Security detection method and system based on attack association
A technology of security detection and association relationship, applied in the field of network security, it can solve problems such as interception of hidden attack behavior, inability to know intranet penetration behavior, and difficulty in troubleshooting, and achieve the effect of efficient network management.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
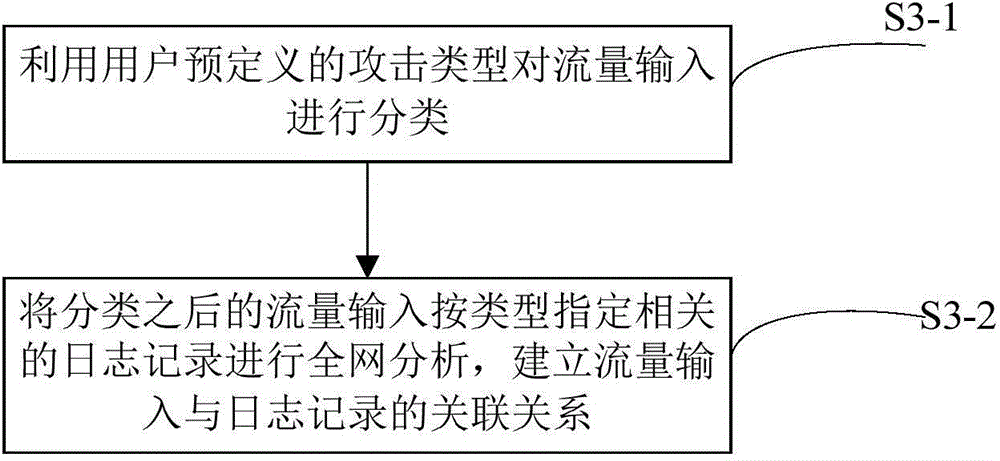
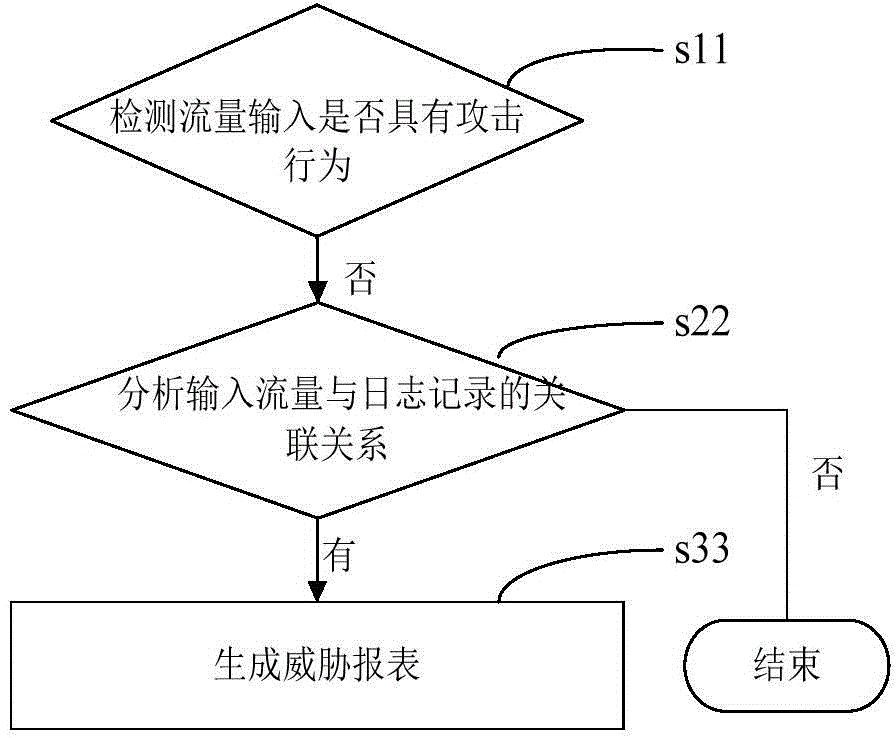
[0041] In order to have a clearer understanding of the technical features, purposes and effects of the present invention, the corresponding specific implementation modes of the present invention when the input traffic has an attack behavior and the corresponding specific implementation modes of the present invention when the input traffic hides the attack behavior are described in detail with reference to the accompanying drawings .
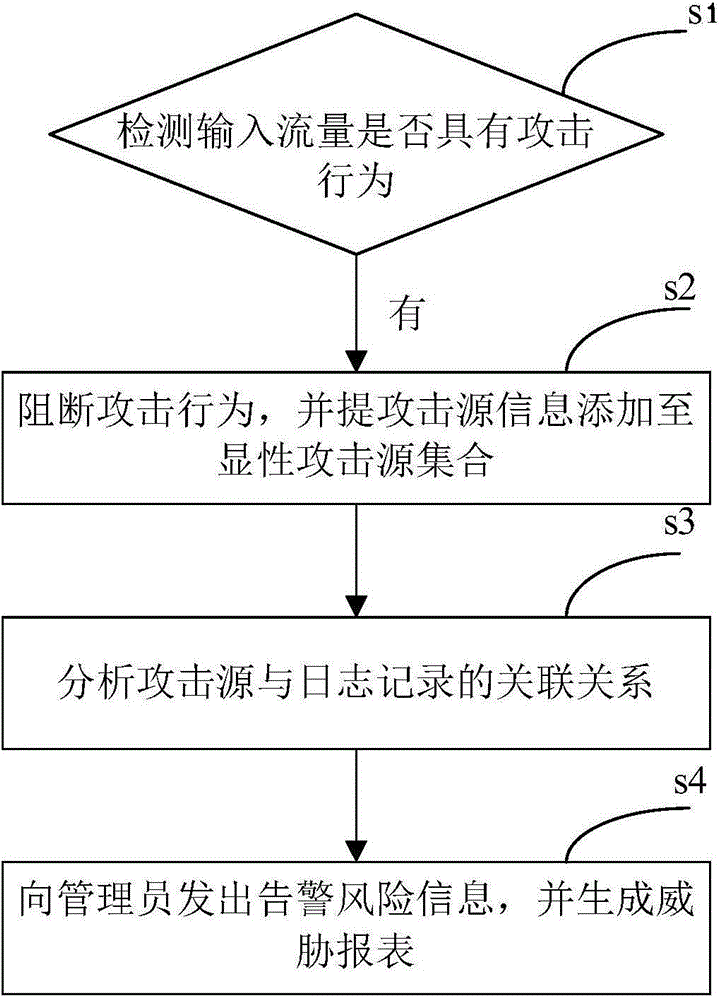
[0042] figure 1 It is a flow chart of the security detection method when the input traffic has an attack behavior according to an embodiment of the present invention. Such as figure 1 As shown, the method includes the following steps:
[0043] Step S1: Detect whether the input traffic has attack behavior. Understandably, the input traffic can be divided into those with attack behavior and those without attack behavior. In this embodiment, assuming that the incoming traffic is detected to have an attack behavior, the following steps are perfor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com