Distributed host vulnerability scanning method
A vulnerability scanning and main scanning technology, which is applied in the field of distributed host vulnerability scanning, can solve the problems of inability to find vulnerabilities in time and low efficiency of vulnerability scanning, and achieve the effects of saving communication time, highlighting scanning efficiency, and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention is further illustrated below by means of examples, but the present invention is not limited to the scope of the examples.
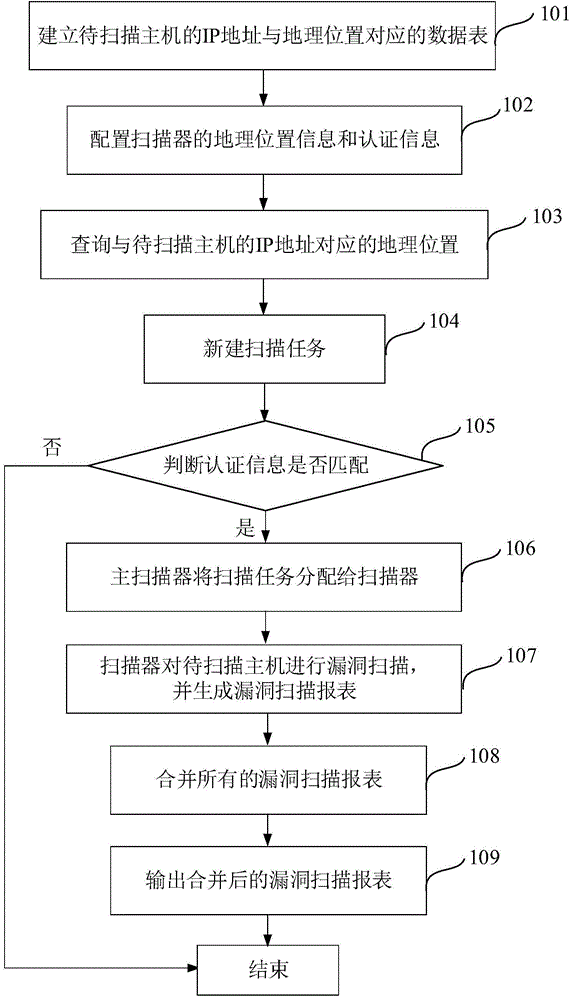
[0030] A distributed host vulnerability scanning method, such as figure 1 shown, including the following steps:
[0031] Step 101, establishing a data table corresponding to the IP address of the host to be scanned and the geographic location;
[0032] Step 102, configure geographic location information and authentication information of multiple scanners, configure one of the scanners as a master scanner, and configure the rest of the scanners as slave scanners;
[0033] Step 103, sequentially query the geographic locations corresponding to the IP addresses of all hosts to be scanned in the data table;
[0034] Step 104, creating multiple scanning tasks in the main scanner, and assigning the IP addresses of hosts to be scanned corresponding to the same geographic location to the same scanning task;
[0035] Step 105, judgin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com