Method for unlocking hand behavior based three-dimensional password lock
A password lock and behavioral technology, applied in the field of information security, can solve the problems of not being safe enough, not simple enough, easy to be cracked and used, etc., and achieve the effect of improving security and high randomness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
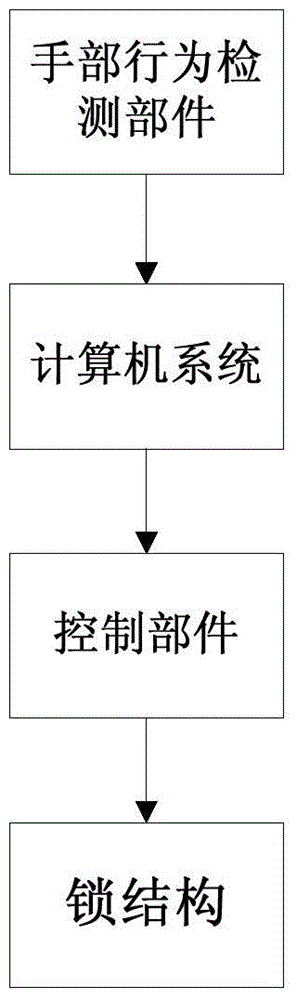
[0041] The hand behavior three-dimensional password lock of the present invention comprises a hand behavior detection component, a computer system, a control component and a lock structure.
[0042] Wherein, the hand behavior detection component is used to detect the hand movement performed by the user and generate a corresponding password. During specific implementation, the hand behavior detection component can use infrared hand detection equipment, such as Lead Motion. Lead Motion is Somatosensory controller A model produced by manufacturing company Leap Somatosensory controller , the Chinese name is "Lidong", which can accurately detect the user's gestures, with high detection accuracy and can even accurately detect one-tenth of the fingertip's movements.
[0043] The computer system is used to detect the hand behavior detection part according to the learned gesture password, and then cooperate with the control part according to the detection result to control the lock...
Embodiment 2
[0046] This embodiment introduces the formation principle of the unlocking method of the hand behavior three-dimensional password of the present invention.
[0047] The position of the hand is in three-dimensional space. Due to the specificity and complexity of hand behavior, it is difficult to locate the position of the hand only by computer. Therefore, there are few researches on gesture unlocking.
[0048] In view of the deficiencies of the above-mentioned prior art, the present invention adopts three-dimensional coordinates and uses hand recognition as the password input object, including the attributes of the hand operation state and hand gestures, and unlocks after comparison by the computer system, thereby providing users with Provides an easy-to-use and safe gesture unlocking method.
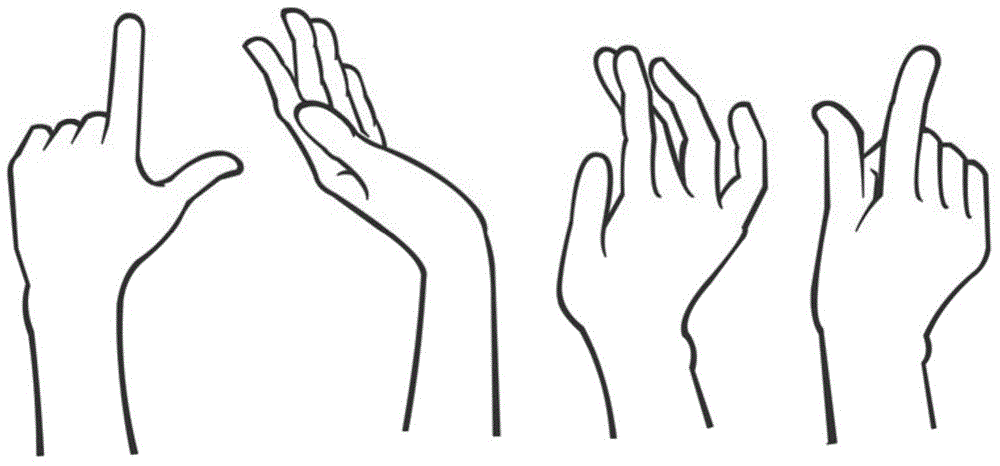
[0049] The hand behavior code of the present invention is composed of three parts, including hand shape code, sequence code and position code.
[0050]The hand shape code means that th...
Embodiment 3
[0055] The present invention is based on the password generated by hand behavior, and is a three-dimensional password lock with gesture action formed by combining a computer system and hand behavior detection components (such as leap motion). The hand behavior three-dimensional combination lock utilizes the hand behavior detection component to detect the hand behavior, so as to decompose the three-dimensional hand behavior into codes.
[0056] In specific implementation, the unlocking process of the combination lock based on hand behavior includes:
[0057] (1) Pre-defined—used to define and store the unlocking gestures of the 3D password lock.
[0058] When the three-dimensional combination lock is activated, the user needs to pre-define a specific gesture in the three-dimensional combination lock to unlock the three-dimensional combination lock (the specific gesture includes the specific shape, specific order and specific position information of the hands). Take the three-d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com