A method for locating intrusion infected areas based on computer timing dependent network
A technology for computers and computer objects, applied in computer security devices, computing, instruments, etc., can solve problems such as information dependency explosion, information dependency false positives, and difficulty in locating intrusion sources, achieving high accuracy and applicability. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] Below in conjunction with specific embodiment and appended Figures 1 to 4 The present invention is further described:
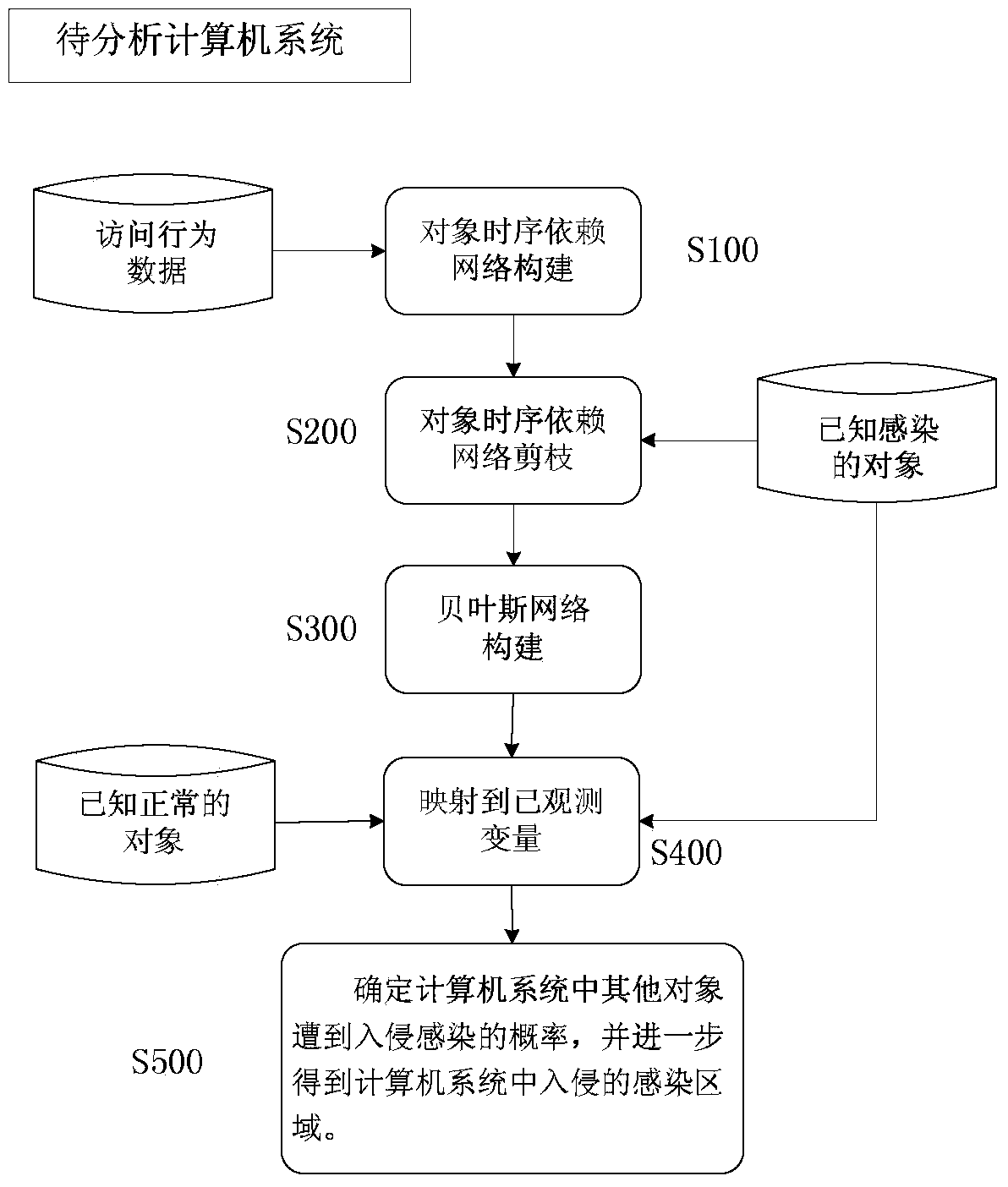
[0039] In one embodiment, such as figure 1 As shown: the present invention discloses a method for locating an intrusion infection area based on computer timing dependent network, and the method includes the following steps:
[0040]S100. Construct a timing dependent network of some objects;
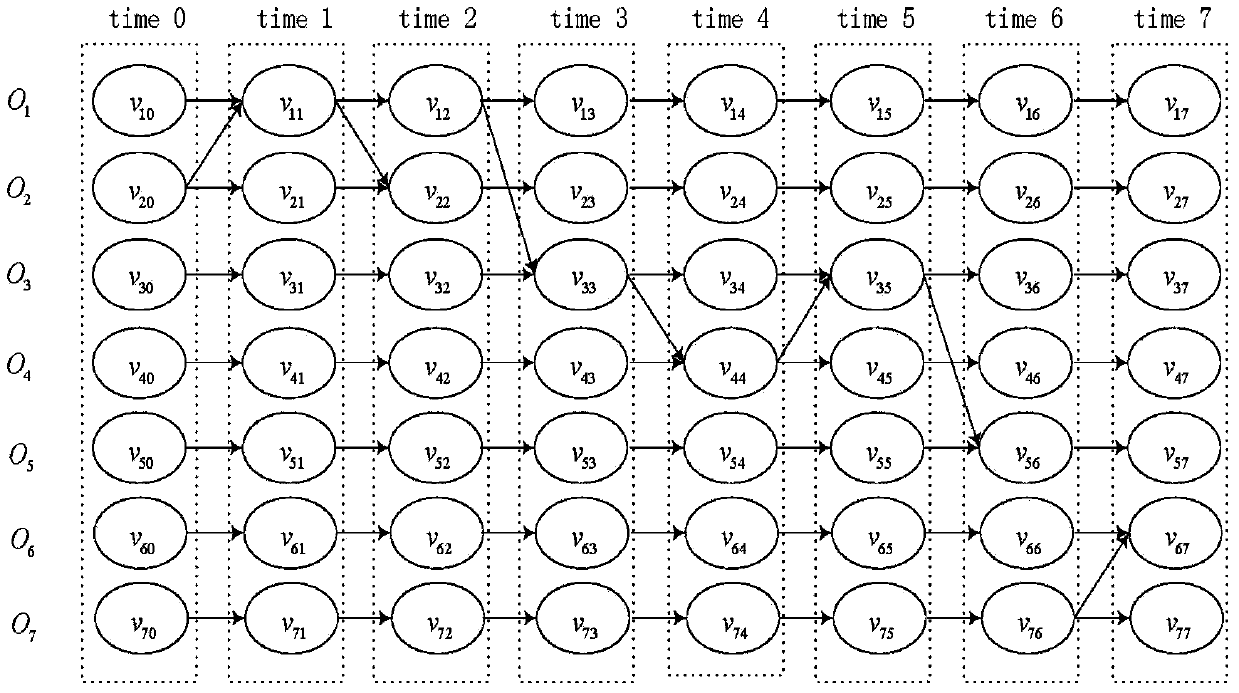
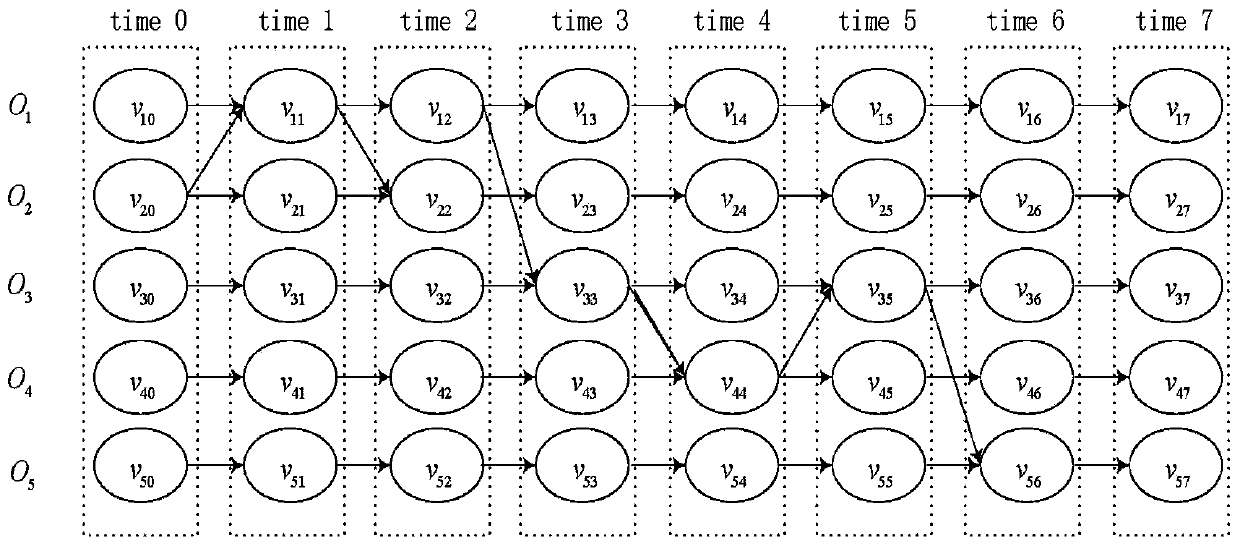
[0041] The time series dependency network of the object is constructed based on the access records of all processes in the computer system to be analyzed;
[0042] The computer system to be analyzed includes: a computer system that was infected by an attacker's intrusion at a certain point in the past and has not detected part of the infected objects until the current moment;
[0043] S200. According to the known infected objects, prune the object time-series dependent network, and extract the object time-series dependent sub-network related to the intrusion i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com