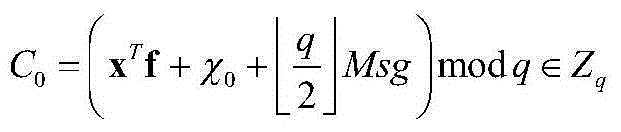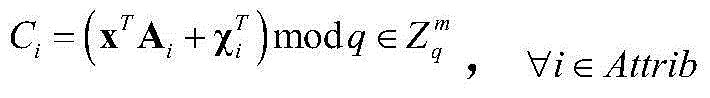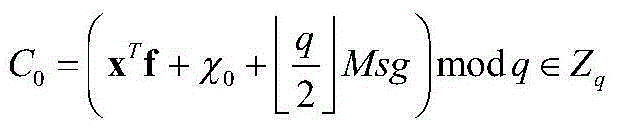Attribute-based encryption method for lattice multi-authority key strategy
An encryption method and attribute technology, which is applied in the field of information security, can solve the problems that the encryption method cannot be realized, different organizations cooperate and the workload is low, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
[0102] Example: Suppose challenger B randomly selects (lm+1) vectors And visit the oracle machine O to obtain (lm+1) LWE oracle machine samples and mark them as follows:
[0103]
[0104] Target: Adversary A announces the list of target attributes that it wants to attack, denoted as Attrib * , that is, the target to be challenged,
[0105] Setting: B Construct public attribute public key Apk as follows:
[0106] 1 vector is obtained from sampling with index 0, that is, s=w 0 ;
[0107] 2 For each i ∈ [l] and such that the attribute i ∈ Attrib * The corresponding public key matrix of is constructed from the LWE oracle to the sample with index i, namely
[0108] 3 For each i∈[l] and the attribute The corresponding matrix A i It is constructed according to the TrapGen algorithm in the real scheme, where the TrapGen algorithm is combined with a low-norm full-rank matrix B i makes A i B i = 0, all indexes in the LWE sampling here samples of are not used;
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com