Hadoop malicious node detection system based on network behavior analysis
A malicious node and behavior analysis technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as the waste of resources for verification nodes, the inability to effectively detect the framework, and the cache of popular tasks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
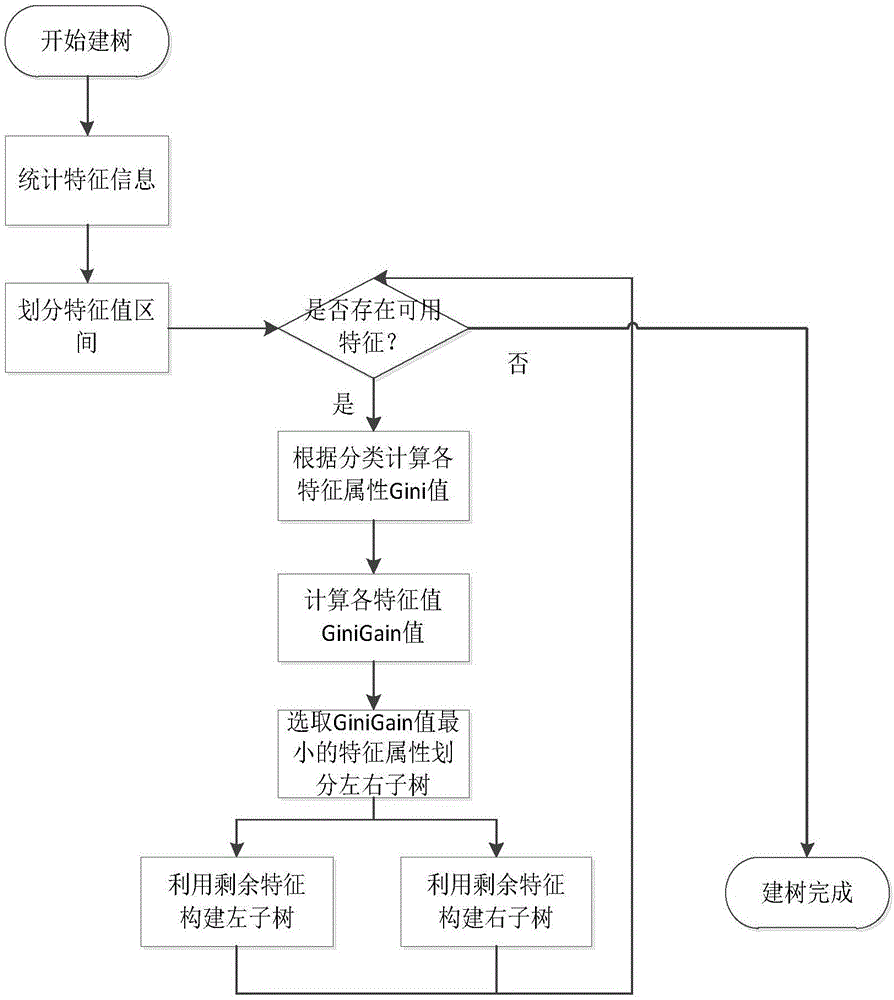
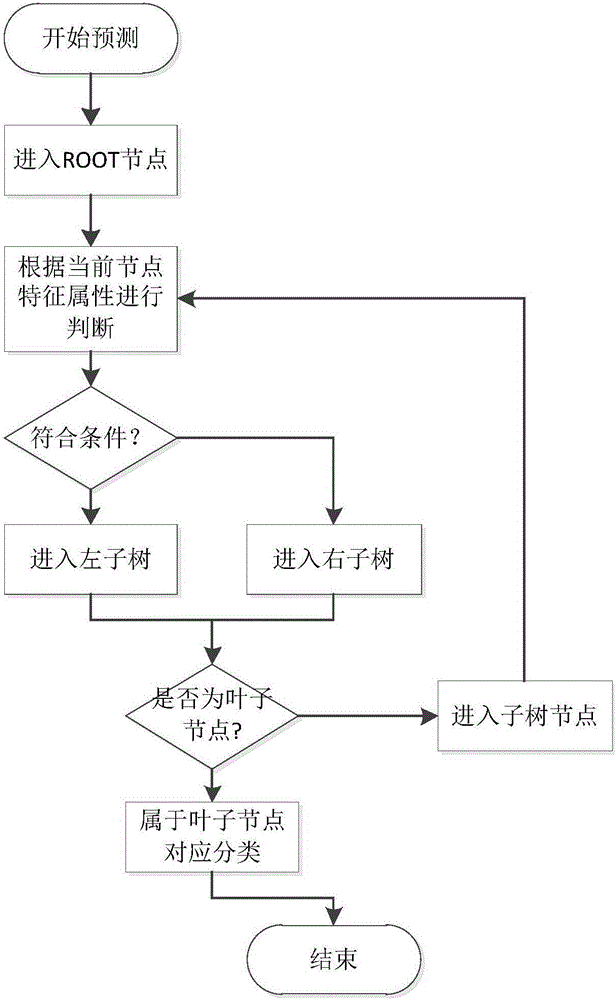
[0023] The Hadoop malicious node detection system based on network behavior analysis of the present invention is specifically implemented as follows:
[0024] (1) Network behavior monitoring module
[0025] Network behavior has different behavior expressions in different network layers. Malicious programs often generate a large number of one or more network requests in the following protocols, such as: DNS, ICMP, HTTP, FTP, SMTP, etc. The present invention simultaneously monitors the network behaviors of the following key protocols:
[0026] ICMP is a sub-protocol of the TCP / IP protocol suite, used to transfer control messages between IP hosts and routers. The control message refers to the message of the network itself, such as the unreachable network, whether the host is reachable, and whether the route is available. One of the usual purposes of this type of behavior is to request a large number of data packets and exhaust server resources. The second purpose is to build communica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com