Method and system for preventing structured query language (SQL) implantation
A technology of abstracting and requesting parameters, applied in the fields of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve problems such as low processing efficiency, and achieve the effect of reducing requirements, improving security, and high processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] In order to describe the technical content, achieved goals and effects of the present invention in detail, the following descriptions will be made in conjunction with the embodiments and accompanying drawings.
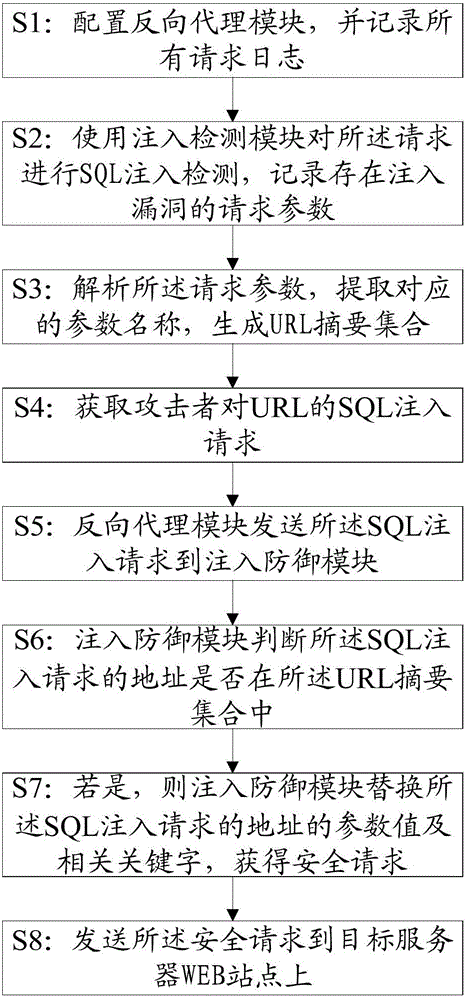
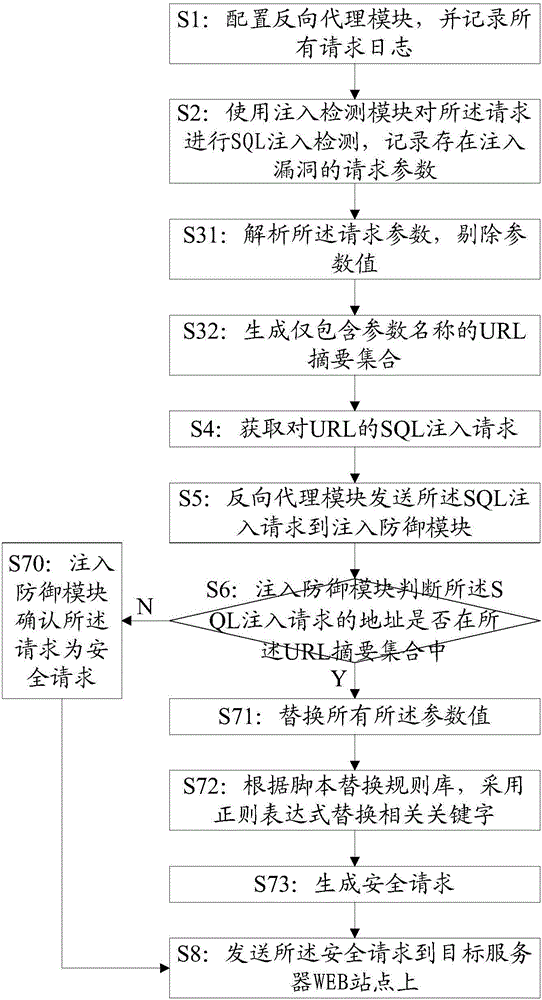
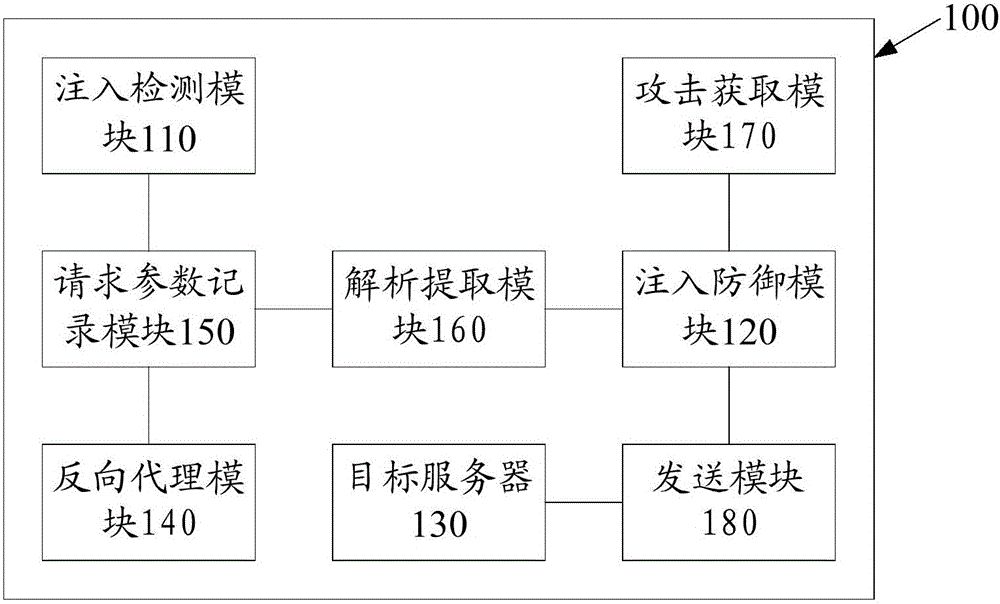
[0029] The most critical idea of the present invention is: through SQL injection detection, obtain the request parameter that needs defense, generate URL summary set, analyze, parameter value or key word replacement process to the acquired SQL injection, prevent SQL from injecting into the system.
[0030] Please refer to figure 1 , Embodiment 1 of the present invention provides a method for preventing SQL injection, including the following steps:
[0031] S1: Configure the reverse proxy module and record all request logs; such as the known nginx, use the logging function to record all request logs. Optionally, the reverse proxy module can also be, for example, IIS under the windows system;
[0032] S2: Use the injection detection module to perform SQL injec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com