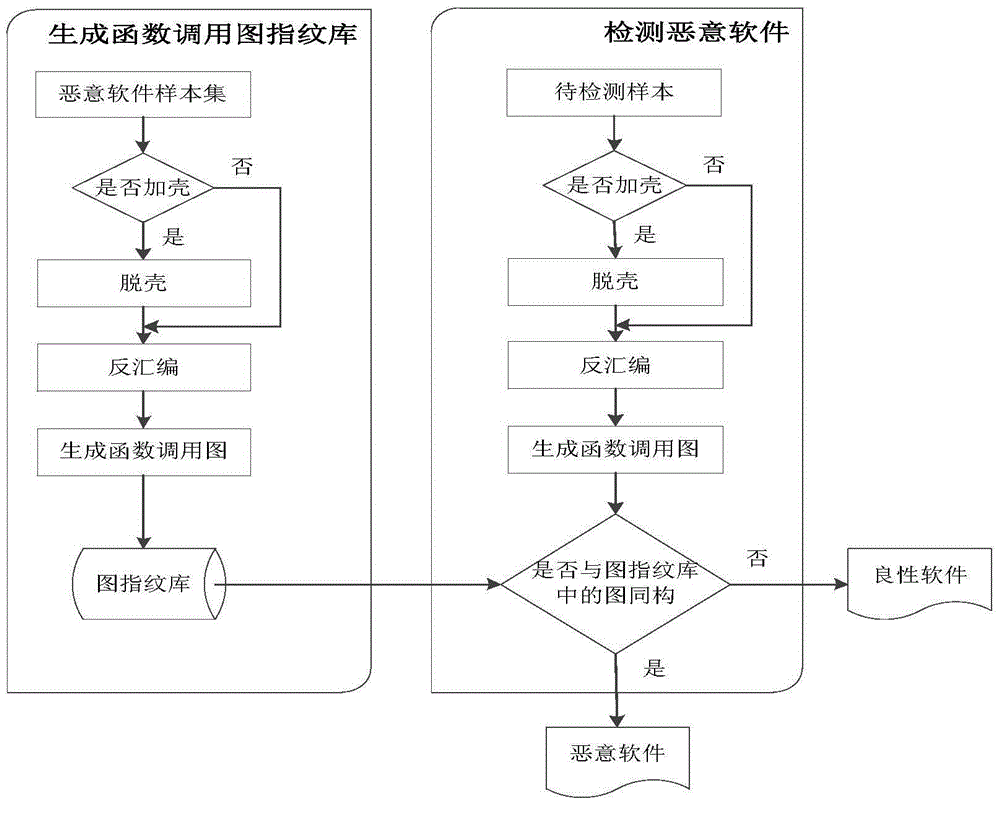
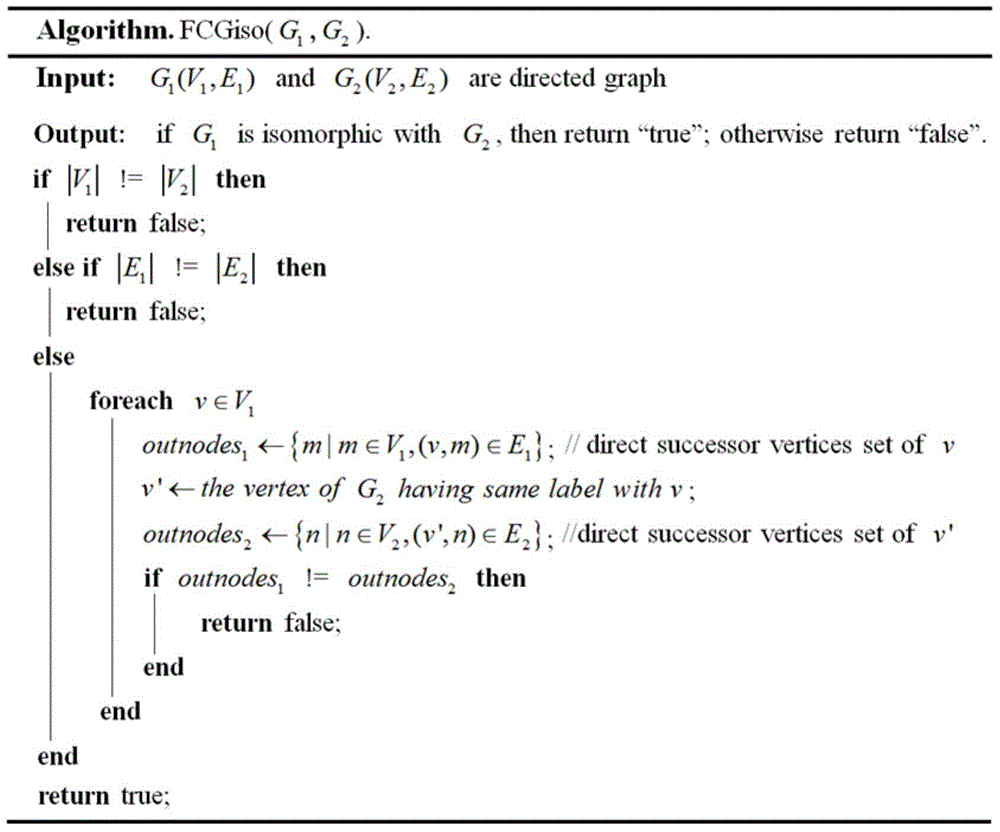
Function call graph fingerprint based malicious software detection method
A function call graph and malicious software technology, applied in the direction of electrical digital data processing, instrumentation, platform integrity maintenance, etc., can solve problems such as incompleteness, high scale and complexity, fine granularity, etc., and achieve scale reduction and high recognition rate , the effect of strong unique identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0053] This embodiment mainly evaluates whether the method of the present invention can effectively detect known malicious software. This embodiment uses 4985 benign software samples and 5340 malicious software samples, uses all malicious software samples to generate the function call graph fingerprint library, and all benign software and malicious software are used as test samples to evaluate the detection rate and false alarm rate of the detection method ,Accuracy. In order to compare with the graph isomorphism method FCGiso proposed by the present invention, the classic graph isomorphism method VF2 is also used for graph isomorphism judgment. The experimental results are shown in Table 1, and the detection time using the FCGiso graph isomorphism judgment method is as follows: Figure 5 , Figure 6 As shown, the detection time of the VF2 graph isomorphism judgment method is as follows Figure 7 , Figure 8 shown.
[0054] Table 1 Detection results of known malware
[0...
Embodiment 2
[0060] This example mainly evaluates whether the method of the present invention can effectively detect packed known samples. First, use 9 packing tools to pack the samples notepad.exe and calc.exe, use the original two samples to generate a function call graph fingerprint library, and use the packed 18 samples as test samples, the experimental results are shown in Table 2 shown.
[0061] Table 2. Packed variant detection results
[0062]
[0063] As can be seen from Table 2, the method of the present invention can detect most of the packed variants. The packed samples of ASProtect cannot be detected, mainly because the tool uses compression, encryption, anti-debugging, and disassembly technologies, which makes the common unpacking tools unable to unpack successfully. In addition, the size of the original sample file, the packed file, and the unpacked file are different, so it can be judged that the method based on the hash signature is invalid for the packed sample. The...
Embodiment 3
[0065] This embodiment mainly evaluates whether the method of the present invention can effectively detect malware variants. In this embodiment, four malicious software families are selected, and some samples are variants produced by confusion, and some are variants after modification or function expansion of known malicious software. First, a sample of each family is selected to generate a function call graph fingerprint library, and other samples of each family are used as test samples. The test results are shown in Table 3.
[0066] Table 3 Malware variant detection results
[0067]
[0068] It can be seen from Table 3 that the method of the present invention can detect most of the variants of the same family. Commonly used obfuscation techniques mainly include garbage instruction insertion, equivalent instruction replacement, register replacement, instruction sequence replacement, and instruction control flow transformation. The first four techniques will not change th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com