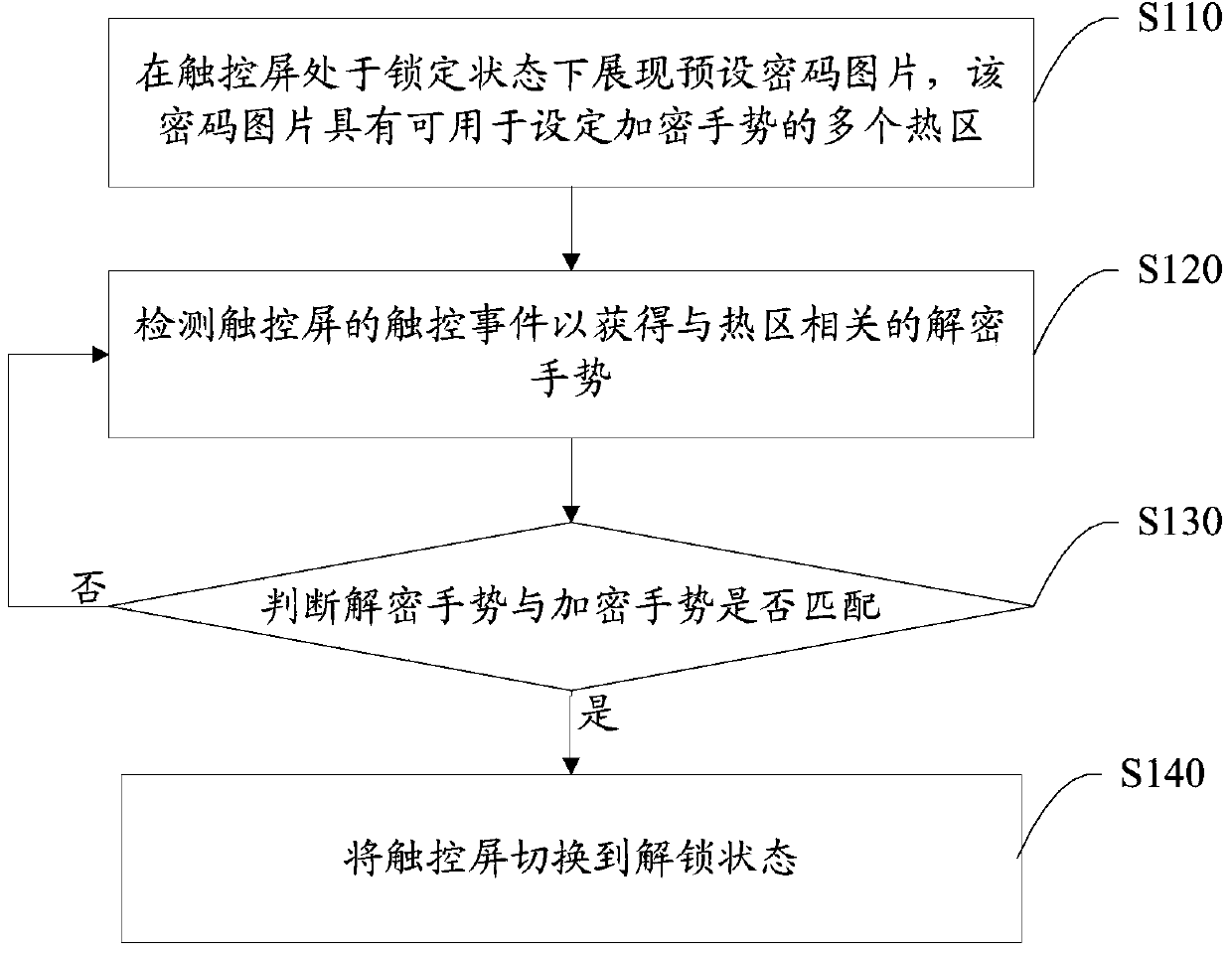
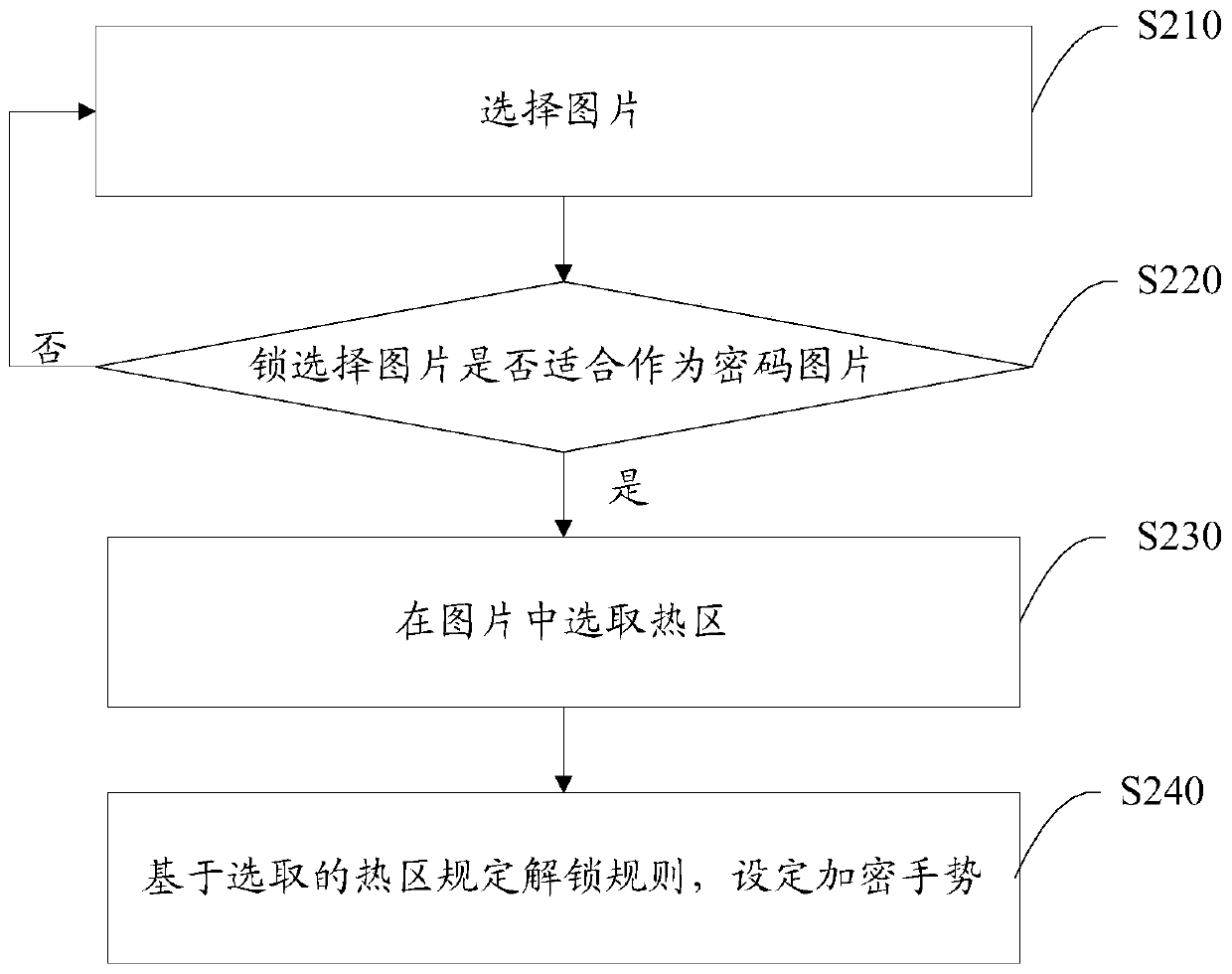
Touch screen unlocking method, device and electronic equipment, display and mobile terminal
A technology for unlocking devices and touch screens, applied in instruments, electrical digital data processing, computing, etc., can solve the problems of limited combination, single mode, and low difficulty of decryption, so as to increase the difficulty of cracking, improve security, increase The effect of diversity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0062] Example 1: Image encryption process with multiple faces
[0063] see Figure 3a and Figure 3b , showing a password image encryption process with multiple faces, which specifically includes the following four steps:
[0064] Step1: The user can select an existing picture in the device as the basis for the password lock. For a device with a camera function, the user can temporarily take a picture to obtain a picture. In this example, the user selects Figure 3a picture shown.
[0065] Step2: Determine whether the selected picture is suitable as a password picture. In this example, the automatic face detection method can be used to select the operation hotspot, and it can be judged that there are 6 faces in the picture, which meet the requirements for setting a password picture. from Figure 3a to Figure 3b , the outer frame of the face is detected by automatic face detection technology, and the content in the frame is the hot spot. The automatic face recognition he...
example 2
[0071] Example 2: Image encryption process with multiple scenes
[0072] see Figure 4a and Figure 4b , showing a password image encryption process with multiple scenes, which specifically includes the following four steps:
[0073] Step1: The user selects a picture, such as Figure 4a shown.
[0074] Step2: The picture has a variety of scenes, which meet the requirements.
[0075] Step3: Use the scene area segmentation technology to divide the image area into 5 parts, such as Figure 4b shown. For technical information on scene segmentation, refer to known technologies, for example, refer to the following papers:
[0076] [2] Zhuowen Tu, Xiangrong Chen, Alan L. Yuille, Song-Chun Zhu, "ImageParsing: Unifying Segmentation, Detection, and Recognition," International Journal of Computer Vision, Volume63, Number2, pp.113-140July2005
[0077] Step4: The user can define an encrypted gesture according to the segmentation result. For example, a user clicks: tree->beach->mountain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com