A Near Neighbor Detection Method Based on Wireless AP
A detection method and wireless technology, applied in wireless communication, access restrictions, electrical components, etc., can solve problems such as leaking user location information and endangering user privacy, and achieve the effect of ensuring location privacy security and great practical value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
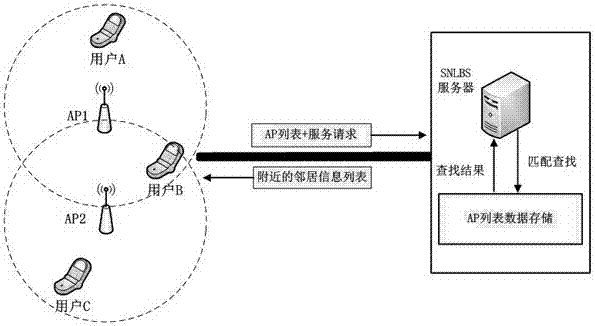
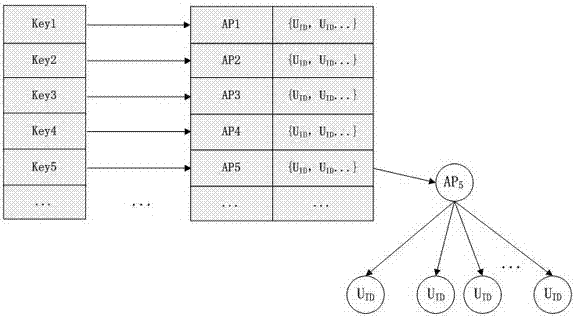
[0014] The present invention proposes a neighbor detection method based on wireless AP, such as figure 1 As shown, the querying user first searches for nearby wireless APs, and sends the MAC address list of the searched APs (that is, the AP list) to the server together with the query request; the server searches and queries the user's AP by searching the AP list submitted by other users. List other users whose intersection exists, and return the search result set as the query result to the query user.
[0015] In this example, the mobile user in the social network can search not only the signal of the AP that he or she accesses, but also the signal sent by other nearby APs. When the user sends a request to find nearby neighbors, he also sends a list consisting of the MAC addresses of each AP that he has found to the server. After the user send...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com