Identity authentication method based on secret graphic code sharing mechanism
A technology of secret sharing and identity authentication, applied in the field of identity authentication based on the secret sharing mechanism of graphic codes, it can solve the problems of rampant identity tampering and forgery and illegal use of other people's identity documents, technological lag, and large loopholes, and achieves convenient implementation and prevention of being attacked. Tampering, low-cost effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The embodiments of the present invention will be described in detail below with reference to the accompanying drawings, but the present invention can be implemented in many different ways defined and covered by the claims.
[0027] The uniqueness and security of biometric features are the basis of identity authentication. Aiming at technical problems such as collection, storage, conversion and protection of biometric feature information, the present invention proposes an identity real-name authentication method based on a graphic code secret sharing mechanism. Biometric information can be safely and effectively protected, making it unique and secure.
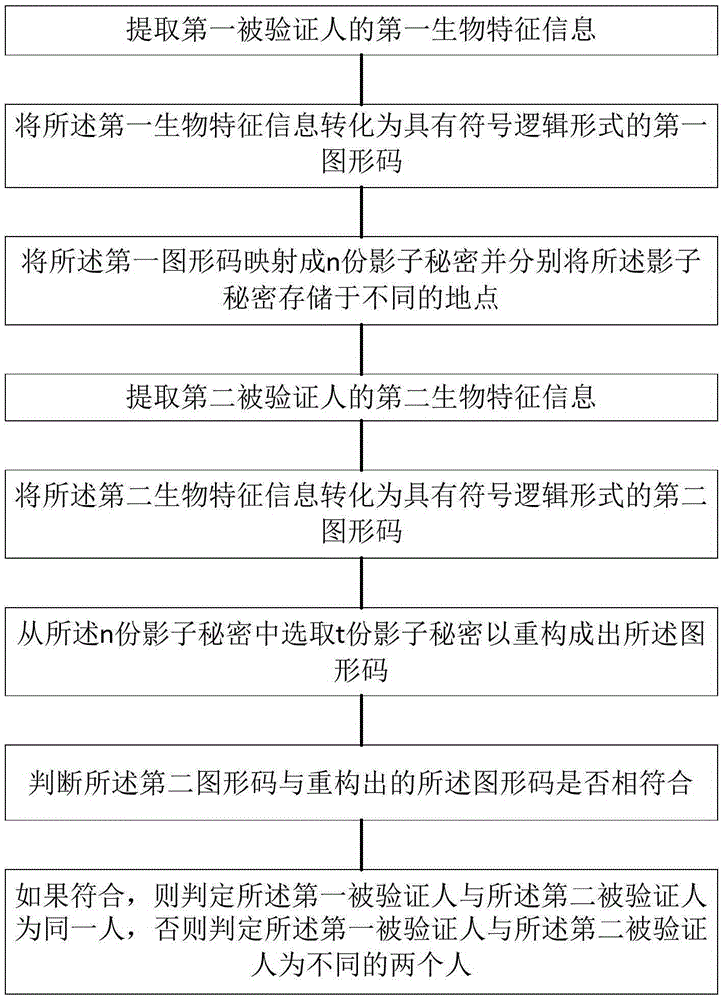
[0028] Please refer to figure 1 , the present invention provides an identity authentication method based on a graphic code secret sharing mechanism, comprising:
[0029] Step 1, extracting the first biometric information of the first verified person;
[0030] Step 2, converting the first biometric information into a fir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com