End-to-end hand-held device encryption method based on quantum cryptography and system
A hand-held device and quantum cryptography technology, applied in transmission systems, digital transmission systems, and key distribution, can solve problems such as attacks that cannot resist super-powerful computing power
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
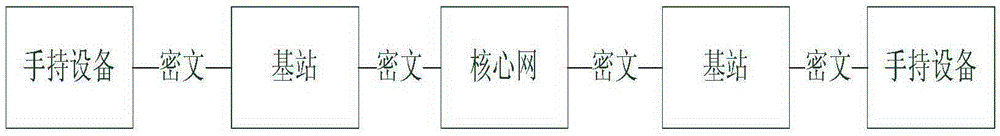
[0048] see figure 1 , figure 2 , image 3 with Figure 4 , this end-to-end handheld device encryption method based on quantum cryptography comprises the following steps:
[0049] Quantum key storage: when the handheld device communicates, the handheld device that initiates the call is the calling terminal, and the called handheld device is the called terminal; the quantum communication key is stored in the handheld device through the key storage module;
[0050] Initiate a call: When encrypted communication is required, the calling end initiates an encrypted communication request to the called end;
[0051] Quantum key synchronization: After receiving the encrypted communication request and confirming the answer, the called terminal sends a key synchronization request message to the calling terminal;
[0052] Synchronization confirmation: After receiving the key synchronization request message, the calling terminal reads the quantum communication key Ksa from its key pool...
Embodiment 2
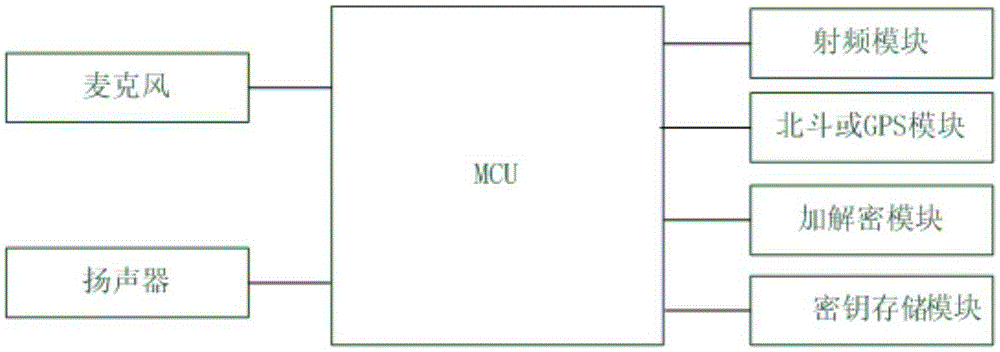
[0064] see figure 2 with Figure 4 , the end-to-end handheld device encryption system based on quantum cryptography includes: radio frequency module, MCU, Beidou or GPS module, encryption and decryption module, key module, microphone, touch screen and speaker; radio frequency module, Beidou or GPS module, The encryption and decryption module, key module, microphone, touch screen and speaker are electrically connected to the MCU; the MCU realizes the air interface function through the handheld device; the microphone is used for voice collection; the speaker is used for voice playback; Beidou or GPS module is used to realize The function of satellite positioning and timing; encryption and decryption module: used to realize the encryption and decryption process of data; the key module is used for the storage and distribution of quantum communication keys; the MCU of the calling terminal uses the quantum communication through the encryption and decryption module of the calling te...
Embodiment 3
[0067] see Figure 5 , both the quantum key distribution terminal QKD1 and the quantum key distribution terminal QKD2 distribute the quantum key through the quantum key distribution channel QL, and generate point-to-point between the two quantum key distribution terminals QKD1 and quantum key distribution terminal QKD2 point of the same key pair. The handheld device TD1 obtains the key from the quantum key distribution terminal QKD1 through the key channel KL1 and stores it in the storage space of the handheld device terminal TD1, and the handheld device terminal TD2 obtains the key from the quantum key distribution terminal QKD2 through the key channel KL2 and stores it In the storage space of the handheld device terminal TD2; the key management center KMC manages key synchronization and update between the handheld device terminal TD1 and the handheld device terminal TD2 through the management channel SL1 and the management channel SL2. As a preferred solution, the specific ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com