Quantum secrete key dynamic distribution management method and system
A quantum key distribution and quantum key technology, applied in the field of management methods and systems for the dynamic distribution of quantum keys, can solve the problems of different use speeds, inability to meet systems and methods, etc., and achieve good practicability and high management efficiency. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
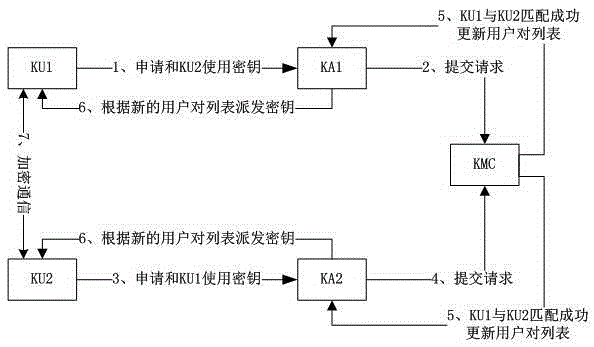
[0035] see figure 1 , image 3 with Figure 4 , the management method for the dynamic distribution of quantum keys, including KMC and two security controlled areas, when one security controlled area is the local end, the other security controlled area is the opposite end; KMC is connected through the key control channel Between two security controlled areas; the local end includes quantum key distribution terminal QKD1, key service agent KA1, and key user KU1; the opposite end includes quantum key distribution terminal QKD2, key service agent KA2 , the user KU2 of the key; including the following steps:
[0036] (1) KU1 sends a request to KA1 to apply for communication with KU2 using a key;
[0037] (2) KA1 submits KU1's request to KMC;
[0038] (3) KU2 sends a request to KA2 to apply for communication with KU1 using a key;
[0039] (4) KA2 submits KU2's request to KMC;
[0040] (5) KMC makes KU1 and KU2 match successfully through the request, forms a user pair and puts ...
Embodiment 2
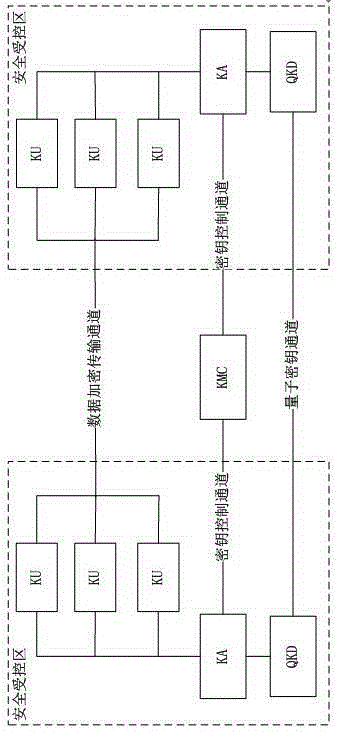
[0047] see figure 2 , the management system for the dynamic distribution of quantum keys includes KMC and two security controlled areas, KMC is connected between the two security controlled areas through the key control channel; when one security controlled area is the local end, the other The security-controlled area is the opposite end; the communication between users in the security-controlled area does not need to be encrypted, and the user communication between two different security-controlled areas uses quantum keys for encryption protection; the security-controlled area includes QKD, KA, KU; QKD is a quantum key distribution terminal, which is used to generate a symmetrical quantum key between the local end and the peer end; KA is a key service agent, which is used to store the quantum key generated by the local QKD , distribution and management; KU is the user of the key, and is used to read the quantum key from the KA at the local end; KMC is the key management cent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com