Intrusion detection method and intrusion detection system based on cloud computing
An intrusion detection and cloud computing technology, applied in transmission systems, electrical components, etc., can solve the problems of large host resource consumption, difficult maintenance and update, high complexity, etc., and achieve the effects of rapid analysis, rapid processing, and rapid discovery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
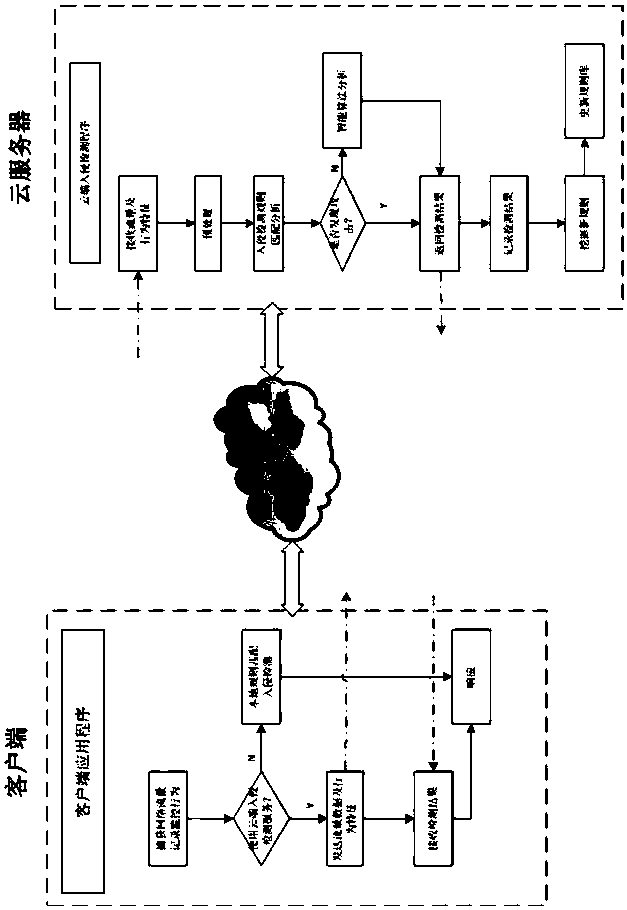
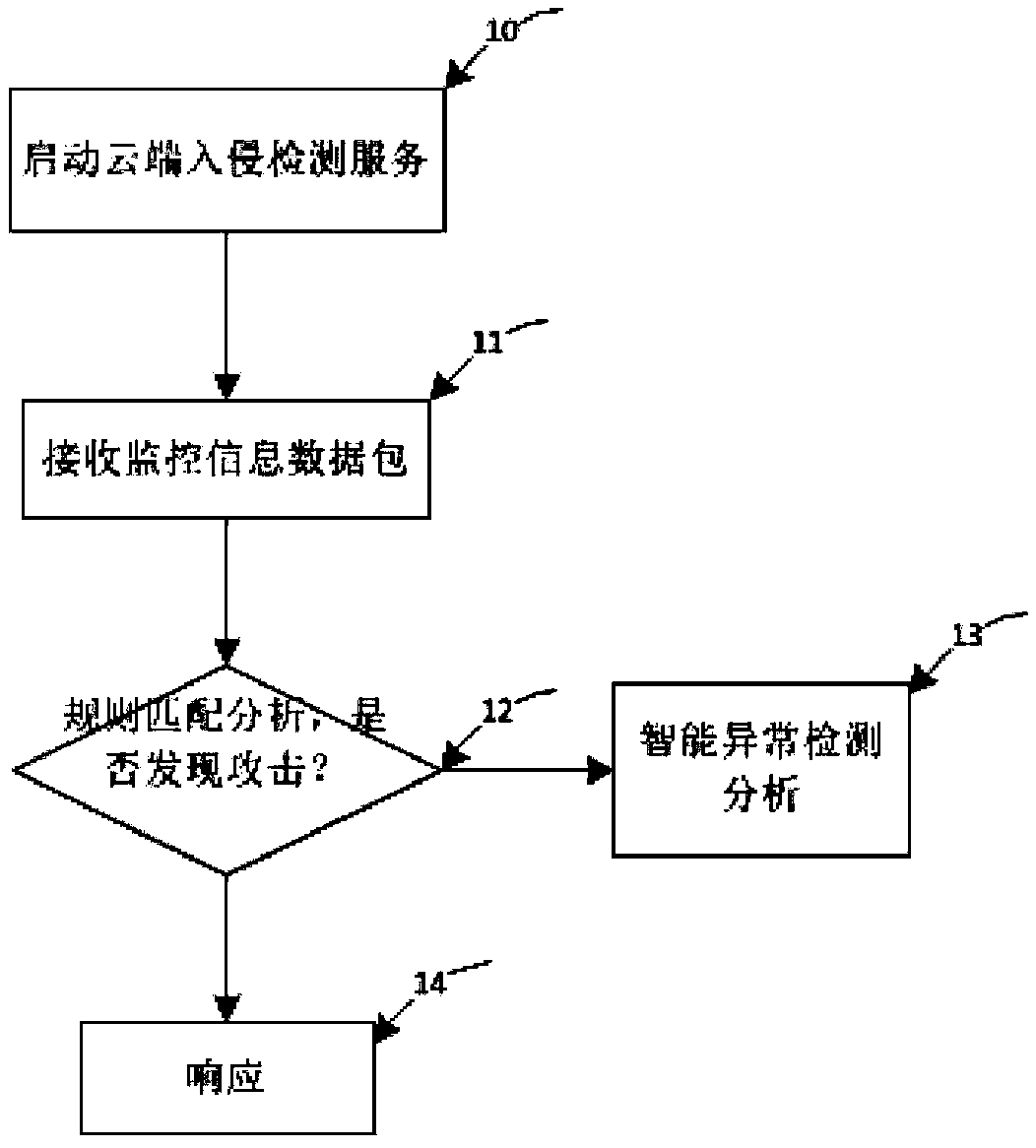
[0038] In order to solve the problems of high complexity, high cost, difficult maintenance and update, and large consumption of host resources in the intrusion detection system deployment and application mode in the prior art, the present invention provides an intrusion detection system based on cloud computing, and a cloud computing-based intrusion detection system Intrusion detection method.
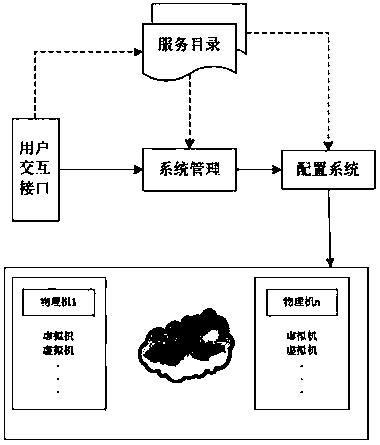
[0039] The cloud computing-based intrusion detection system is implemented by a cloud server and a client. The cloud server includes a number of computing nodes for combining multiple common computers, servers and storage devices through the network through cloud computing technology, wherein the common computers and The server acts as a computing node. Clients are some common web servers that need to use the intrusion detection function.
[0040] Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com