Intrusion detection and analysis method based on modbus/tcp
A technology of intrusion detection and analysis method, applied in transmission systems, electrical components, etc., can solve the problems of low false alarm rate, abnormal equipment operation, false alarm, etc., to achieve fewer missed and false alarms, and faster intrusion identification. Effect
Active Publication Date: 2019-01-22
BEIJING UNIV OF TECH
View PDF5 Cites 0 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
With the transformation of industrialization and automation towards networking and informatization, more and more industrial control systems adopt standard and general-purpose communication protocols and software and hardware systems; in this context, the original encapsulation of industrial control systems is Breaking, various unsafe factors, such as viruses, Trojan horses, intrusions, etc., will enter the industrial control network along with the normal information flow, leading to the instability of enterprise production, especially those related to power transmission, transportation, oil and gas extraction, water treatment, etc. Important industries and fields of national security, facing increasingly serious security threats
At present, traditional firewalls, gatekeepers and other devices are mostly used for security protection in industrial control networks; the basic principle of these devices is to provide better identity authentication and access control, detect and isolate abnormal information flows passing through the protection devices, and prevent known Invasion of viruses and attacks; but this method cannot prevent attacks from inside the firewall, cannot guard against the latest threats, and cannot prevent attacks that bypass the firewall. Intruders use legitimate data packets with dangerous operation control commands to attack, It will cause abnormal or even damage to the operation of the equipment; for example, in recent years, the Stuxnet virus targeting Iran's industrial infrastructure has caused serious damage to Iran's nuclear facilities by tampering with the parameters of normal industrial control protocols
In recent years, intrusion detection systems generally adopt misuse intrusion detection and abnormal intrusion detection; misuse intrusion detection matches the communication traffic in the network according to known characteristics, and has the characteristics of low false positive rate, but because the attack behavior characteristic database of industrial control system is not It may include all attack behaviors, and the use of misuse detection methods is likely to cause missed alarms; and abnormal intrusion detection is based on the simple and fixed communication mode of the communication flow of the industrial control system itself, and through the establishment of normal behavior rules. Abnormal traffic is identified, but because there is no in-depth analysis of network protocols, the characteristics of industrial control protocols have not been flexibly used, and false alarms are prone to occur
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
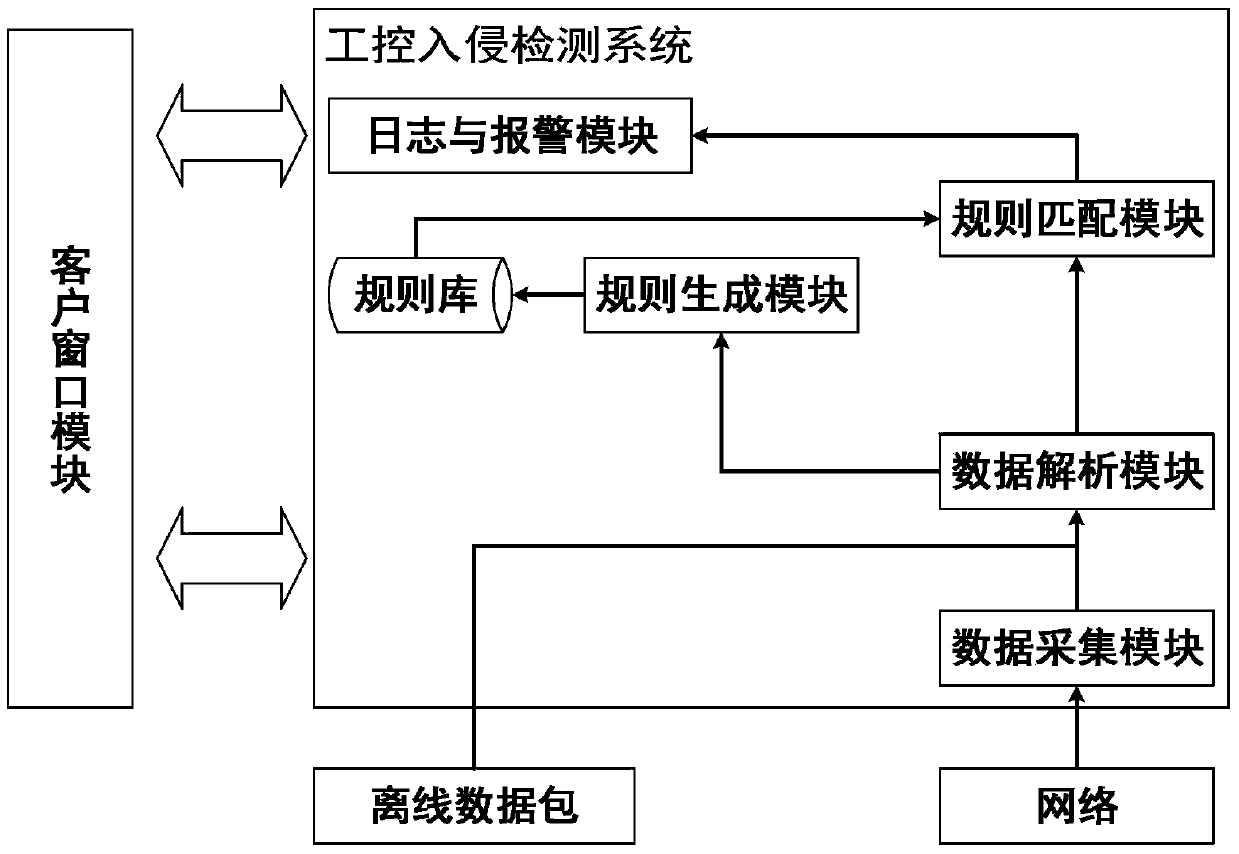
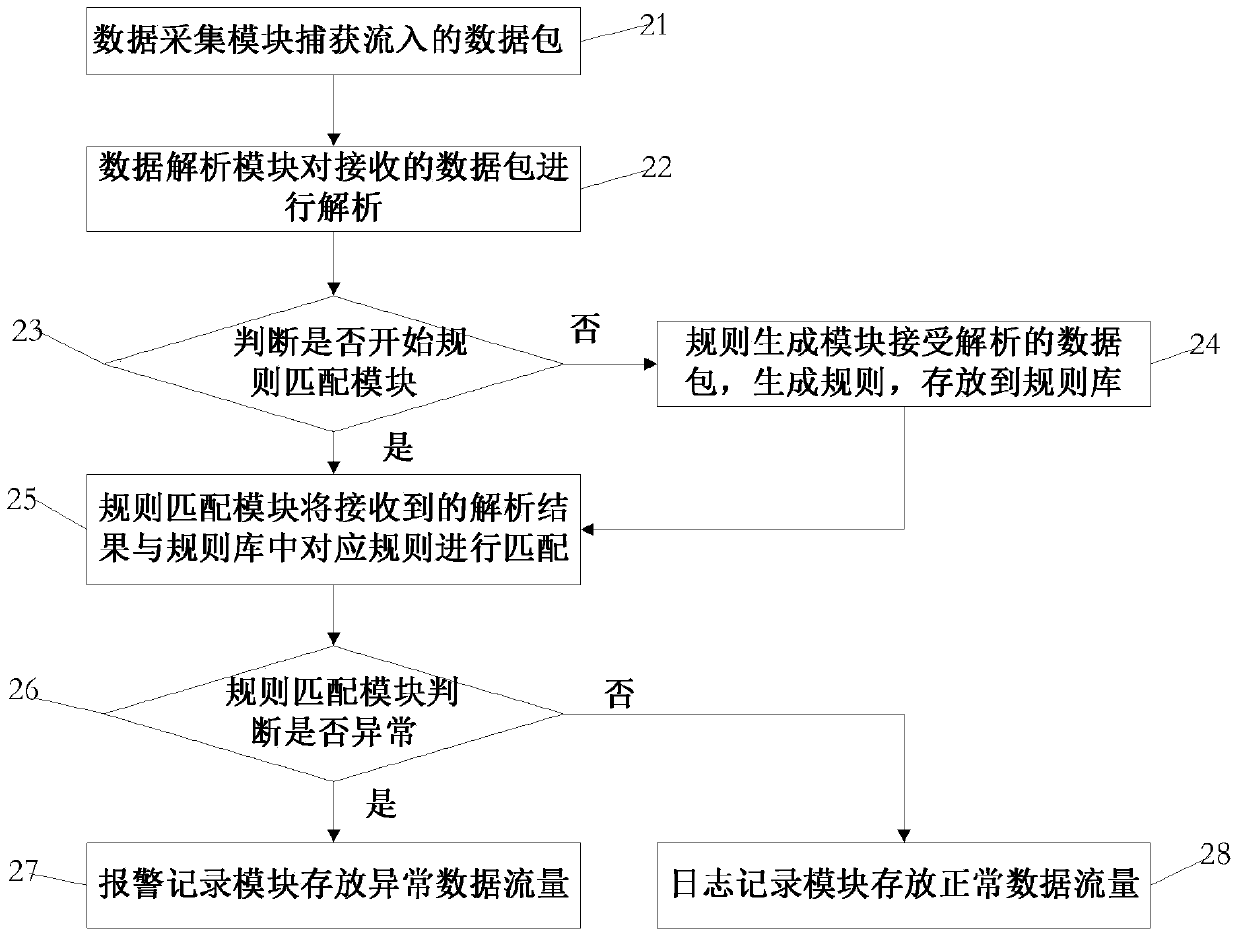
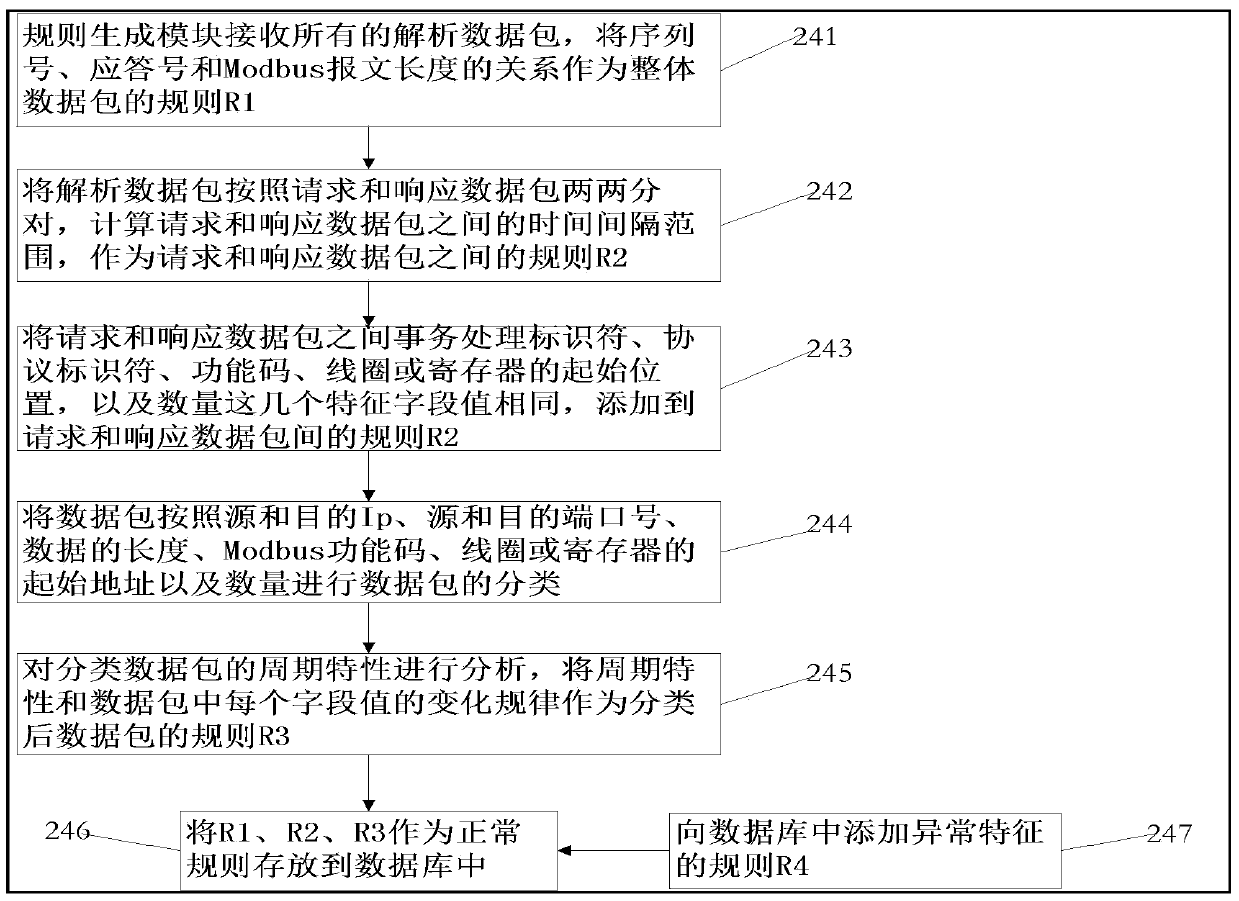
The invention relates to an invasion detection analysis method based on Modbus / Tcp. The method comprises that a data collection module is connected with a network interface, and a data packet is sent to a data parsing module; the data parsing module is connected with a rule generation module and a rule matching module; in the rule self-learning stage, a parsing result of the data packet is sent to the rule generation module; in the rule matching stage, the parsing result of the data packet is sent to the rule matching module; the rule generation module receives the parsed data packet and generates a rule set; and the rule matching module matches the parsed data packet with the rule in a database. On the premises that the industrial network structure is not changed and daily production is not influenced, the method can provide safety measures for offline rule learning and online real-time detection of users, potential threads are blocked out according to strategy requirements of enterprises, alarm missing and false alarm are fewer, invention can be rapidly identified, and the network safety level of the industrial control system can be greatly improved with lower cost.
Description
technical field The invention relates to the technical field of industrial control networks, in particular to an analysis method and an intrusion detection system for intrusion detection of a control network protocol based on Modbus / Tcp. Background technique With the transformation of industrialization and automation towards networking and informatization, more and more industrial control systems adopt standard and general-purpose communication protocols and software and hardware systems; in this context, the original encapsulation of industrial control systems is Breaking, various unsafe factors, such as viruses, Trojan horses, intrusions, etc., will enter the industrial control network along with the normal information flow, leading to the instability of enterprise production, especially those related to power transmission, transportation, oil and gas extraction, water treatment, etc. Important industries and fields of national security are facing increasingly serious secu...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Patents(China)
IPC IPC(8): H04L29/06
CPCH04L63/1416H04L63/1433
Inventor 赖英旭王宇盛宋站威刘静杨凯翔蔡晓田李亚娟
Owner BEIJING UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com