Secret key safety protection equipment and working method thereof
A security protection and key technology, applied in the field of information security passwords, can solve problems affecting information security, and achieve the effect of preventing accidental loss and ensuring reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
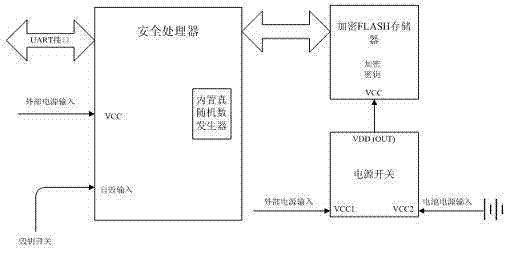
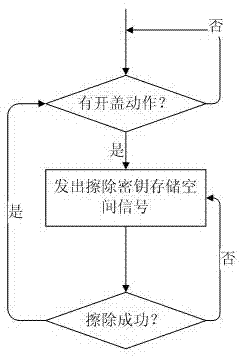
[0022] The purpose of the present invention is to provide a key security protection device, if any attempt is made to open the machine cover, the private key will be automatically destroyed, thereby preventing the private key from being obtained illegally and ensuring the security of the key.
[0023] Such as figure 1 As shown, the key security protection device of the present invention is composed of a body, a machine cover, a security processor disposed in the body, an encrypted FLASH memory, and a power management unit.
[0024] A key-killing switch is arranged on the machine cover.
[0025] The security processor is bidirectionally connected to the encrypted FLASH memory; the input end of the power management unit is connected to the external power supply and the battery power supply, and the output end is connected to the encrypted FLASH memory.
[0026] The safety processor includes a self-destruction input terminal and a safety password module, and a key destruction pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com