Processing guest event in hypervisor-controlled system
A technology for managers and customers, applied in the direction of program control design, program control devices, electrical digital data processing, etc., can solve problems such as technical elimination and failure to solve managers, and achieve the effect of preventing unauthorized access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] In the figures, the same elements are referred to with the same reference numerals. The drawings are merely schematic representations, not intended to portray specific parameters of the invention. Moreover, the drawings are intended to depict only typical embodiments of the invention and therefore should not be considered as limiting the scope of the invention.
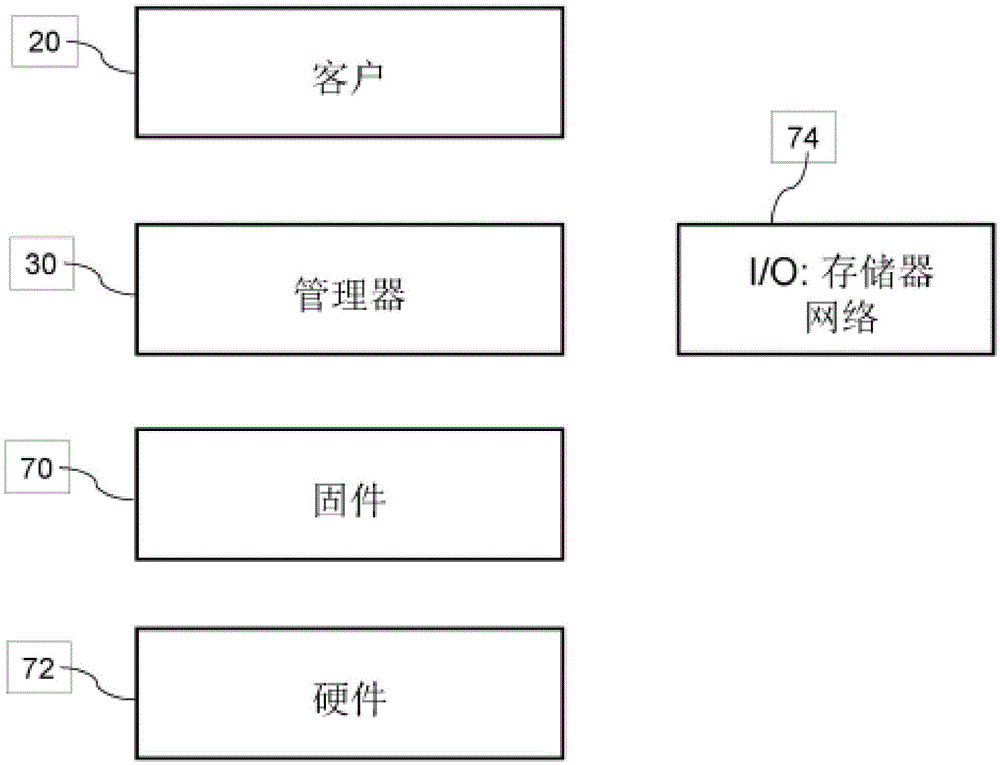
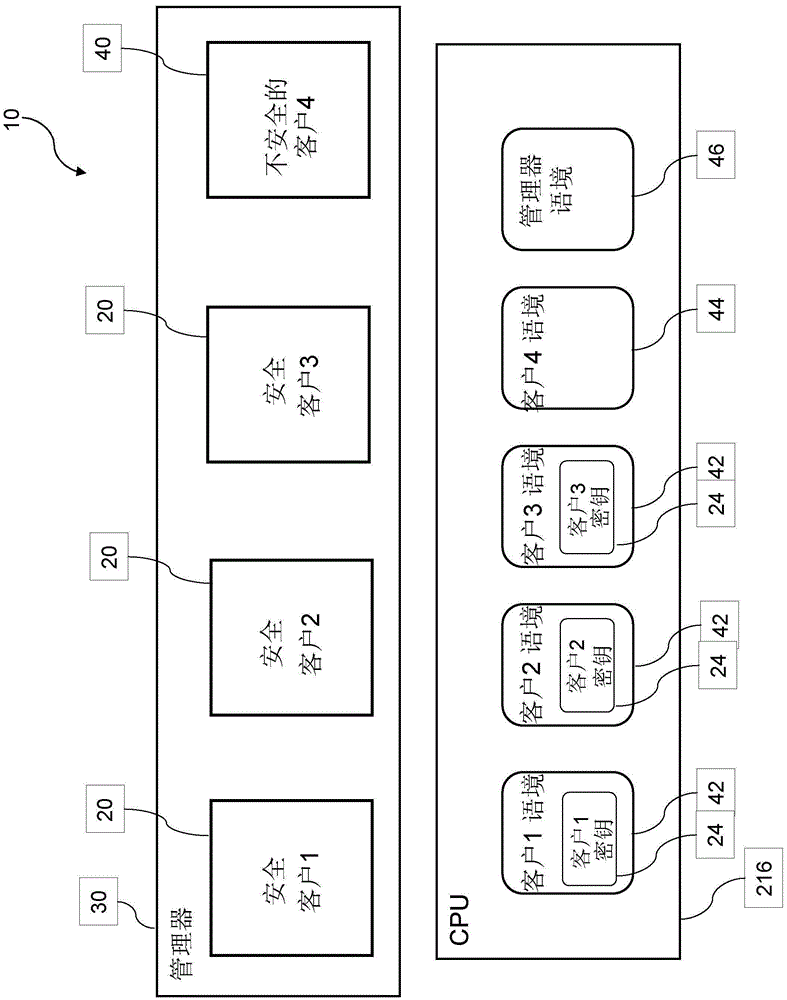
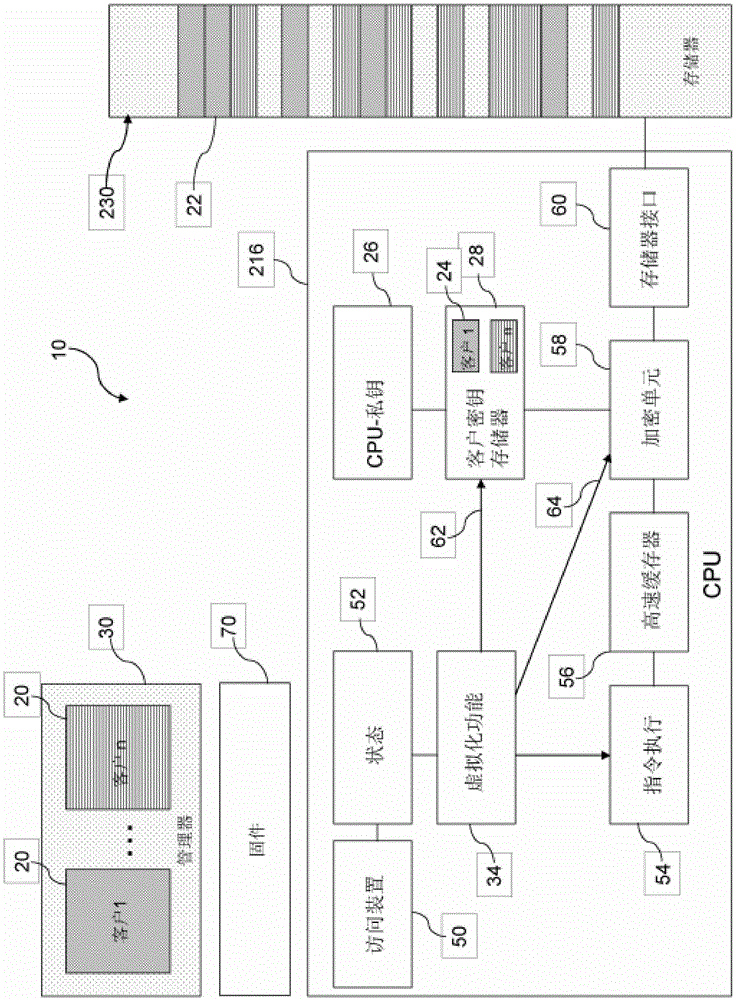
[0048] Figure 1 shows a stack of components in a hypervisor controlled system according to the prior art. The different components include one or more clients 20 implemented as a virtual machine, running as a virtual server system on a system controlled by a hypervisor, including firmware 70, hardware 72 such as one or more CPUs, memory, storage network I / O device74. Manager 30 manages hardware 72 and I / O device 74 resources and allocates appropriate portions of these resources to clients 20 . In a cloud environment, the client virtual machine 20 is operated by the client or client, while the manager 30 is o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com