Security domain-based traffic network security evaluation method
A technology of traffic network and safety evaluation, applied in the direction of road vehicle traffic control system, traffic control system, traffic flow detection, etc., can solve the problem of lack of failure probability prediction and preventive control.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0029] A safety domain-based transportation network security evaluation method, see figure 1 , the transportation network security evaluation method includes the following steps:
[0030] 101: Calculate the transportation network security domain under the N-1 constraint, and obtain the boundary equation group of the transportation network security domain through the transportation network security domain;
[0031] 102: After calculating the blockage of a certain road section, the safety boundary distance of the remaining road sections;
[0032] 103: Carry out safety evaluation on traffic network through safety boundary distance, and visualize safety evaluation results.
[0033] Among them, the transportation network security domain is specifically:
[0034] For a transportation network with a certain topology and capacity during operation, all road sections satisfy the set of N-1 safety operating points, which has a uniquely determined boundary in the multidimensional space,...
Embodiment 2
[0041] The scheme in embodiment 1 is described in detail below in conjunction with specific calculation formula, see below for details:
[0042] 201: Calculate the transportation network security domain under the N-1 constraint, and obtain the boundary equation group of the transportation network security domain through the transportation network security domain;
[0043] Among them, the security domain of the transportation network can be defined as: for the transportation network with a certain topology and capacity in the operation process, all the road sections meet the set of N-1 security working points, and this set has a uniquely determined boundary in the multi-dimensional space . All work points within the boundary are safe, and work points outside the boundary are unsafe.
[0044] The embodiment of the present invention adopts the following flow distribution mode considering user balance:
[0045] t ...
Embodiment 3
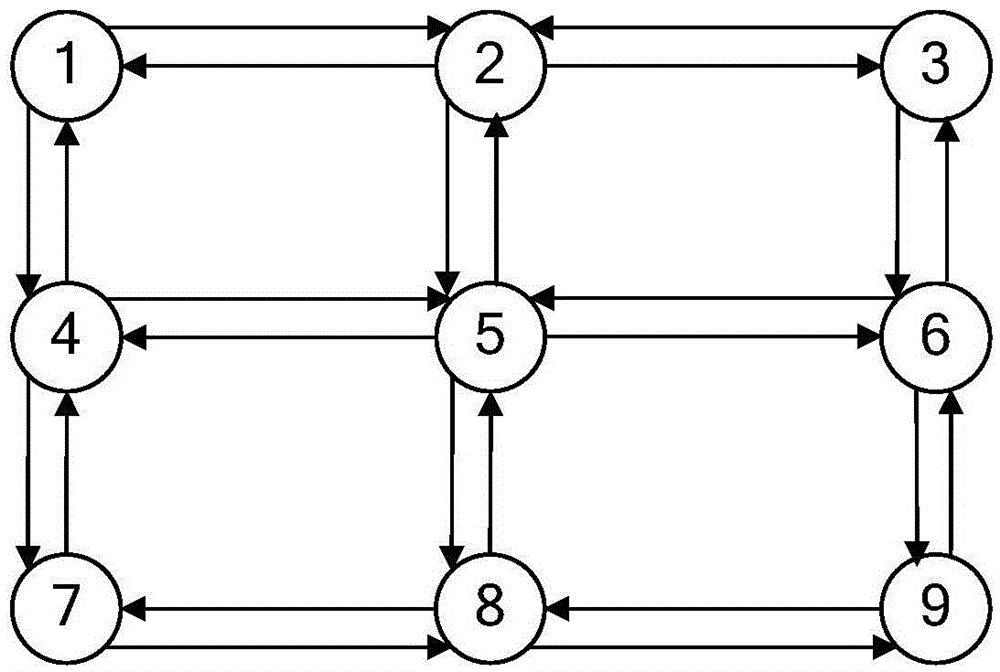
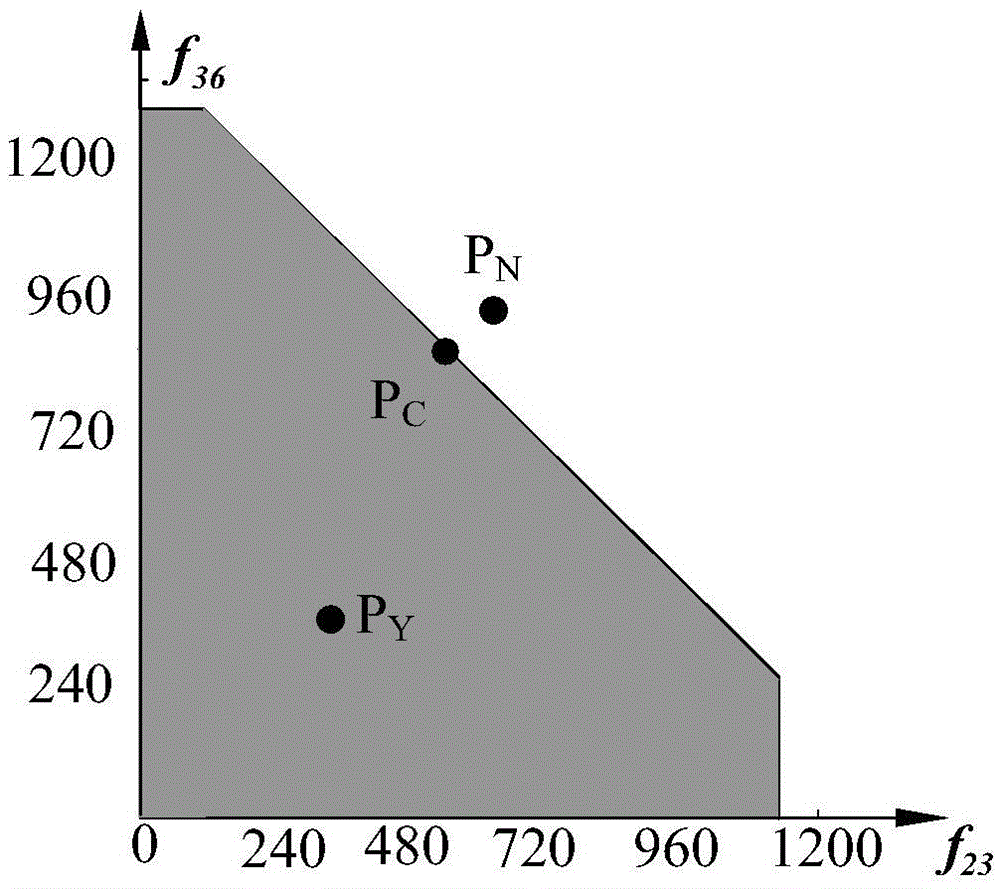
[0062] Combined with specific calculation examples, figure 2 and image 3 Carry out feasibility verification to the scheme in embodiment 1 and 2, see the following description for details;
[0063] In the embodiment of the present invention, 1.25 times the capacity (that is, the value of Q is 1.25) is taken as the upper limit, and if the upper limit is exceeded, the road section is regarded as oversaturated.
[0064] A simple example of commonly used Jiugongge topology is used to verify the method. There are 12 road sections in the calculation example, all road sections are two-way four-lane, and the width of the lanes is equal. The network topology is shown in figure 2 , the parameters are shown in Table 1.
[0065] Table 1 The parameters of the simple example network
[0066]
[0067]
[0068] From Table 1, we can know the length, capacity and the shortest path after congestion of any road section. For example, the length of road section (1,2) is 20km, the capac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com