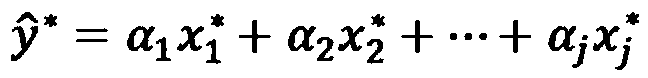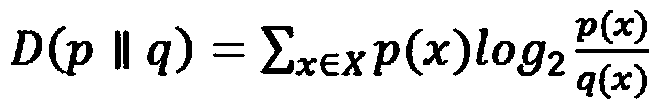Network intrusion detection method and system based on partial least squares
A network intrusion detection, partial least squares technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as insecure open systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
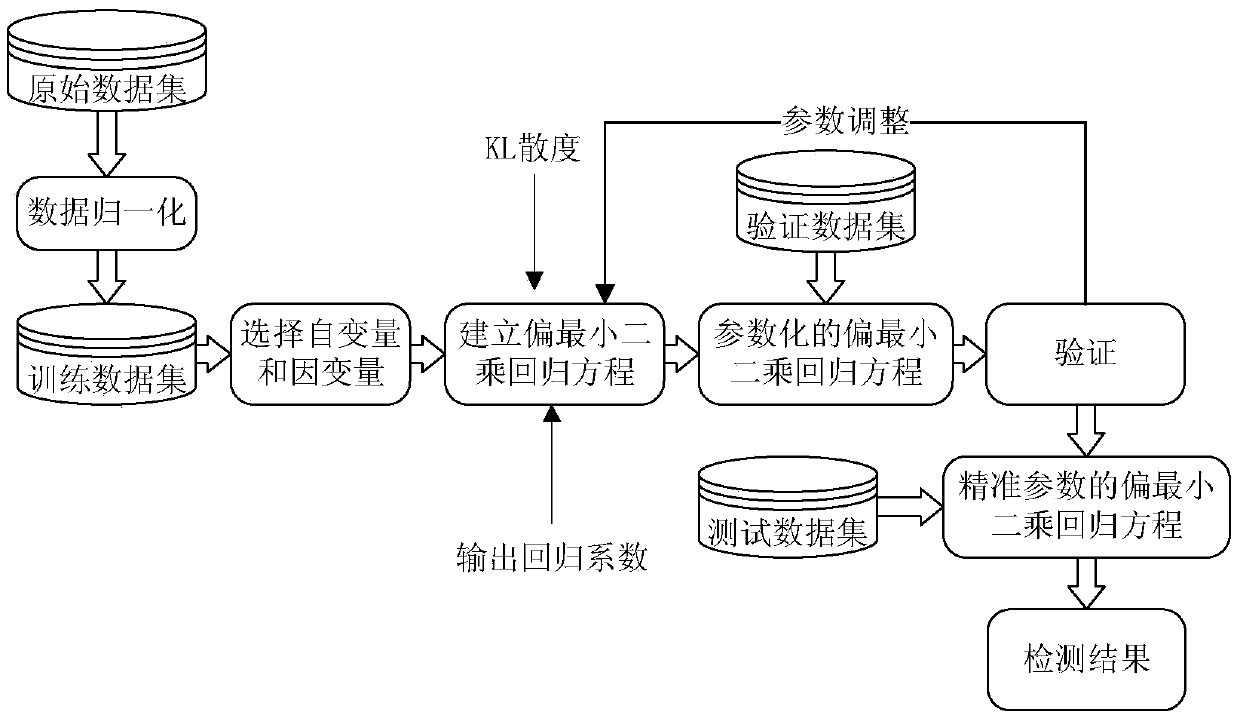
[0039] The present invention will be further described below in conjunction with accompanying drawing and embodiment: figure 1 It is a schematic diagram of the principle of the present invention.
[0040] Such as figure 1 As shown, the network intrusion detection method based on partial least squares in this embodiment includes
[0041] a. Preprocessing the original data set, the preprocessing includes converting each non-numeric attribute into a numerical value and performing normalization processing.
[0042] b. Establish an anomaly detection model of network data according to the partial least squares regression equation;
[0043] c. Perform attribute domain mapping on the unlabeled data set, use the anomaly detection model to classify the data, and obtain different types of access behaviors.
[0044] In this embodiment, when the network suffers from external intrusion, the intrusion data can be regarded as a nonlinear disturbance superimposed on the normal network traff...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com