Method and device for detecting hidden channel communication
A covert channel and covert communication technology, applied in the database field, can solve the problems of lowering system efficiency, high misjudgment rate and missed detection of covert channel detection technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
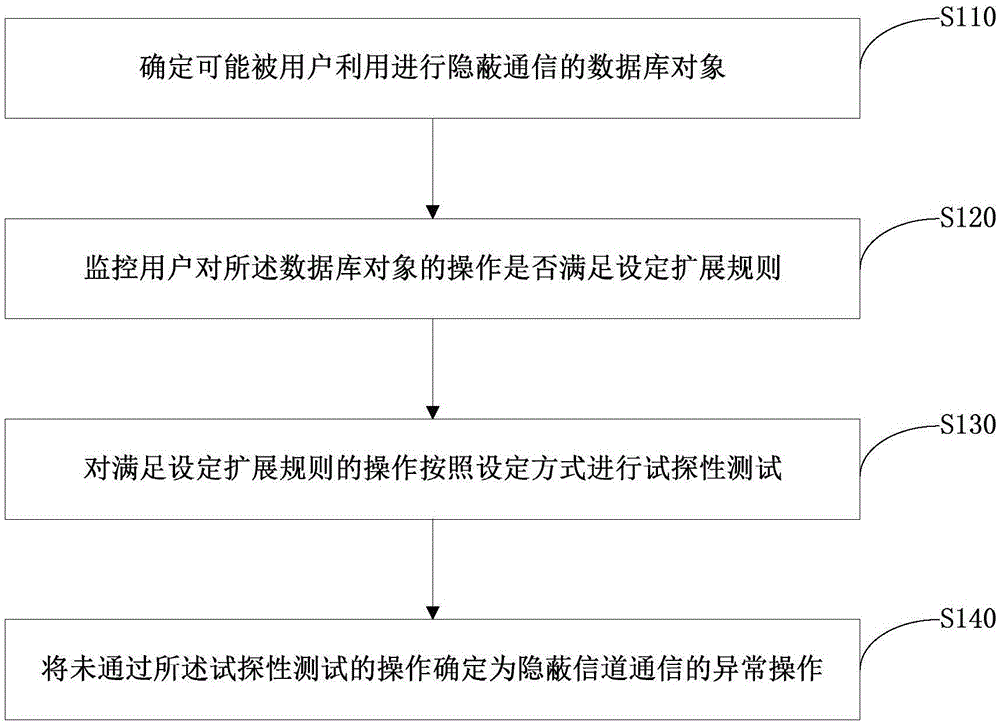
[0021] figure 1 It is a flow chart of the detection method for covert channel communication provided by Embodiment 1 of the present invention. This embodiment can be applied to monitor and record the related operations of potential covert channels, and detect the actual operation of the intruder on the channel by analyzing the records. In the case of , the method may be performed by a detection device for covert channel communication, and specifically includes the following steps:
[0022] Step 110, determine the database objects that may be used by the user for covert communication.
[0023] Among them, the database objects include shared database resources that may be utilized by users for covert communication.
[0024] The terminal obtains the user's operation on the database object, and determines the shared resource that the user can operate according to the database object; builds a shared resource matrix based on the shared resource, and determines the database object ...
Embodiment 2
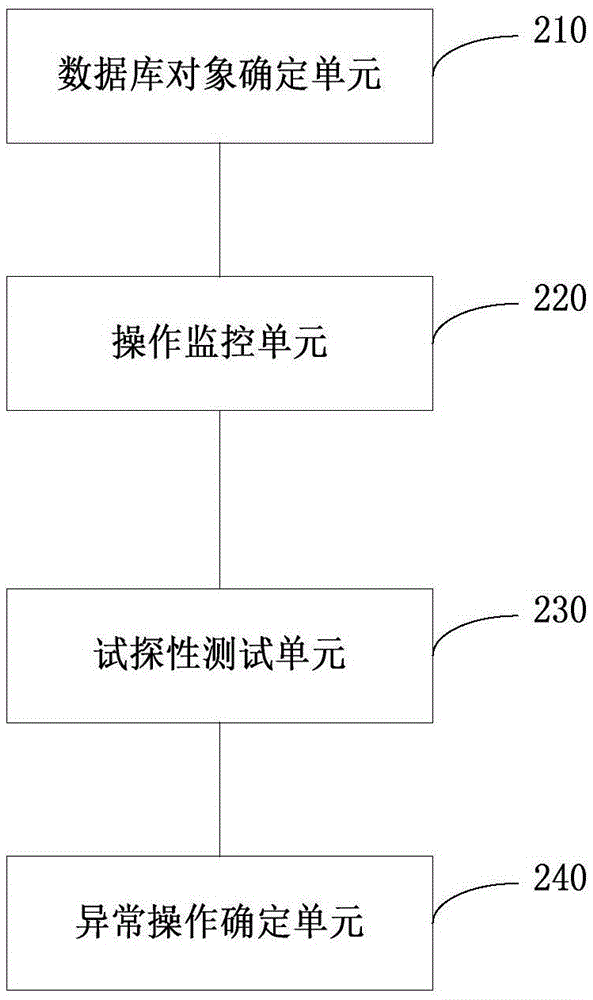
[0036] figure 2 It is a schematic structural diagram of a detection device for covert channel communication in Embodiment 2 of the present invention. The detection device for covert channel communication includes:
[0037] A database object determination unit 210, configured to determine database objects that may be used by users for covert communication;
[0038] An operation monitoring unit 220, configured to monitor whether the user's operation on the database object satisfies the set expansion rule;
[0039] A tentative testing unit 230, configured to perform a tentative test on an operation that satisfies the set extension rule in a set manner;
[0040] The abnormal operation determining unit 240 is configured to determine an operation that fails the tentative test as an abnormal operation of covert channel communication.
[0041] In the technical solution of this embodiment, the database object determination unit 210 is used to determine the database object that may ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com