Ultra-lightweight RFID bidirectional authentication method based on label ID
A two-way authentication, ultra-lightweight technology, applied in the field of radio frequency identification, can solve the problems of increased implementation cost, increased label cost, security defects, etc., to achieve the effect of reducing introduction and storage, reducing storage costs, and reducing label costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
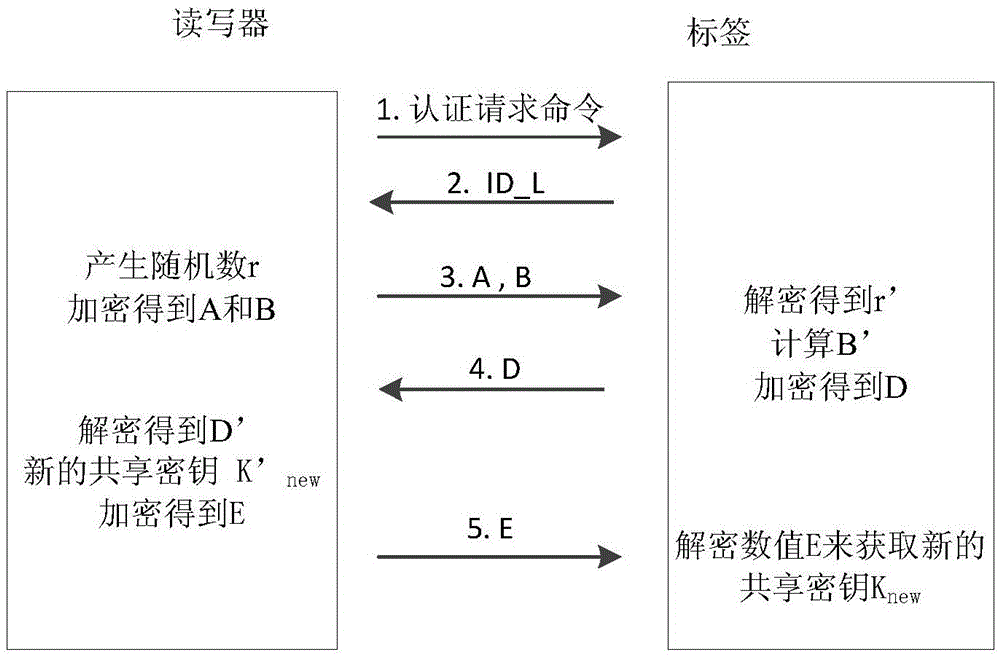
[0042] This embodiment is based on the ultra-lightweight RFID two-way authentication method of tag ID, and its process is as follows figure 1 shown, including the following steps:
[0043] In the first step, the reader sends an authentication request command to the tag; for example, the string "Hello" is sent as the authentication request command;
[0044] In the second step, the tag sends the value ID_L of the first half of the identifier to the reader after receiving the authentication request command; the value ID_L of the first half of the identifier refers to the first half of the identifier ID stored in the tag;
[0045] In the third step, the reader judges whether the first half value ID_L of the received identifier has the same value in the stored data:
[0046] If it does not exist, it is judged that the label is forged, and the authentication ends;
[0047] If it exists, the reader calls the identifier ID' corresponding to the first half of the identifier ID_L, the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com