Invasion and perimeter defense method and invasion and perimeter defense device
A perimeter prevention and intrusion detection technology, applied in the direction of anti-theft alarms, instruments, alarms, etc., can solve the problems of poor real-time performance, long processing time of the whole image, large false alarm rate and difficulty in determining the directionality, so as to improve the detection efficiency. rate, meet real-time requirements, and reduce the effect of false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 3
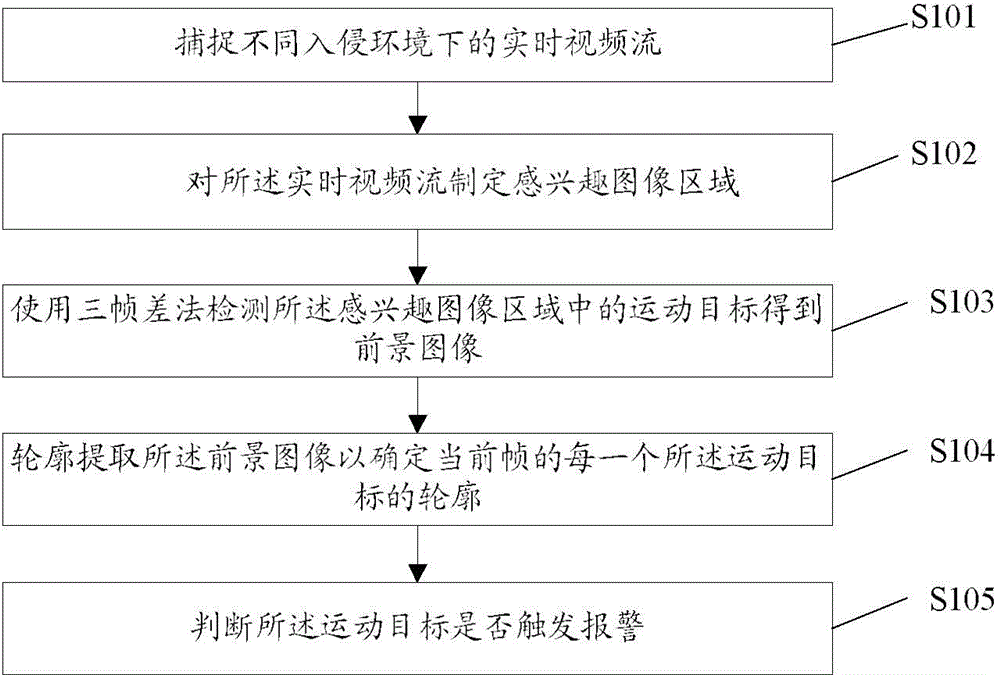
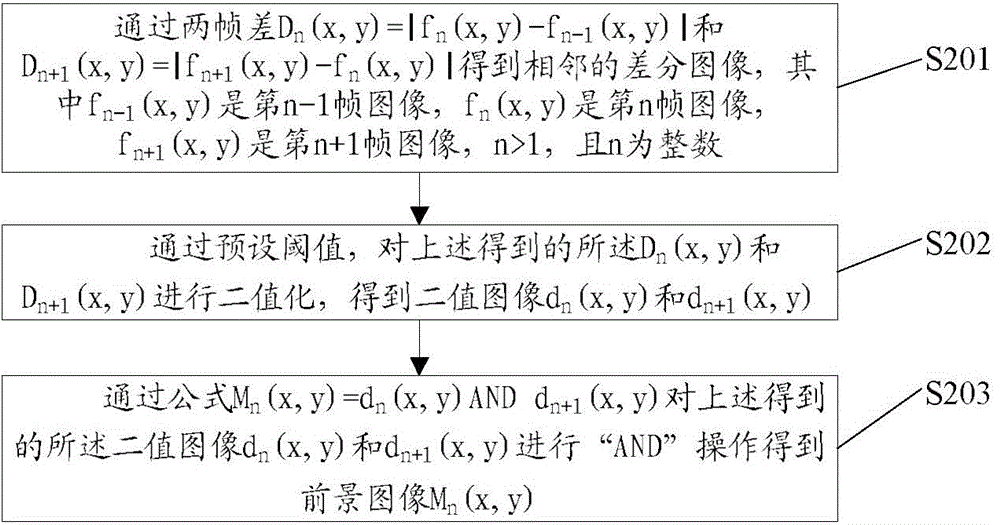
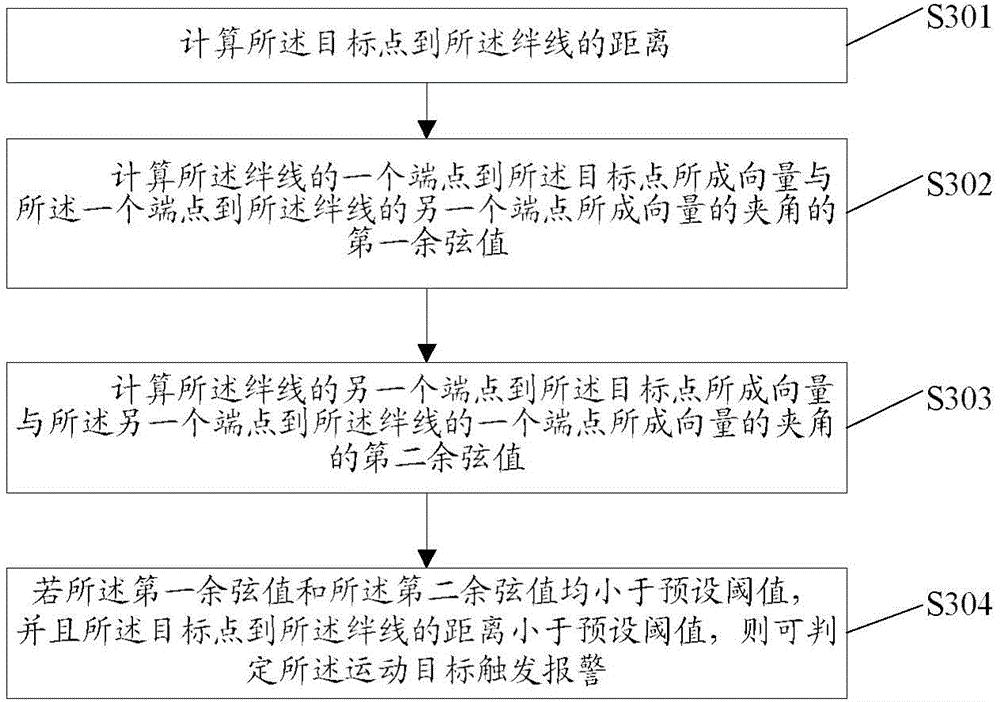
[0078] Correspondingly, the present invention also provides an intrusion and perimeter prevention device, refer to Figure 5 As shown, the present invention provides an embodiment 3 of an intrusion and perimeter prevention device. The device includes: a capture module, a module for formulating an image area of interest, a detection module, a contour extraction module, and a judgment module, wherein the capture module uses It is used to capture real-time video streams under different intrusion environments; the module for formulating an image area of interest is used for formulating an image area of interest for the real-time video stream; The moving object in the image area of interest obtains a foreground image; the contour extraction module is used for contour extraction of the foreground image to determine the contour of each moving object in the current frame; the judging module is used for judging whether the moving object Trigger an alarm.
[0079] Specifically,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com