Method and device for checking weak passwords
A weak password and password technology, applied in the field of information security management, can solve the problems of weak password dictionary update, low efficiency of weak password verification, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
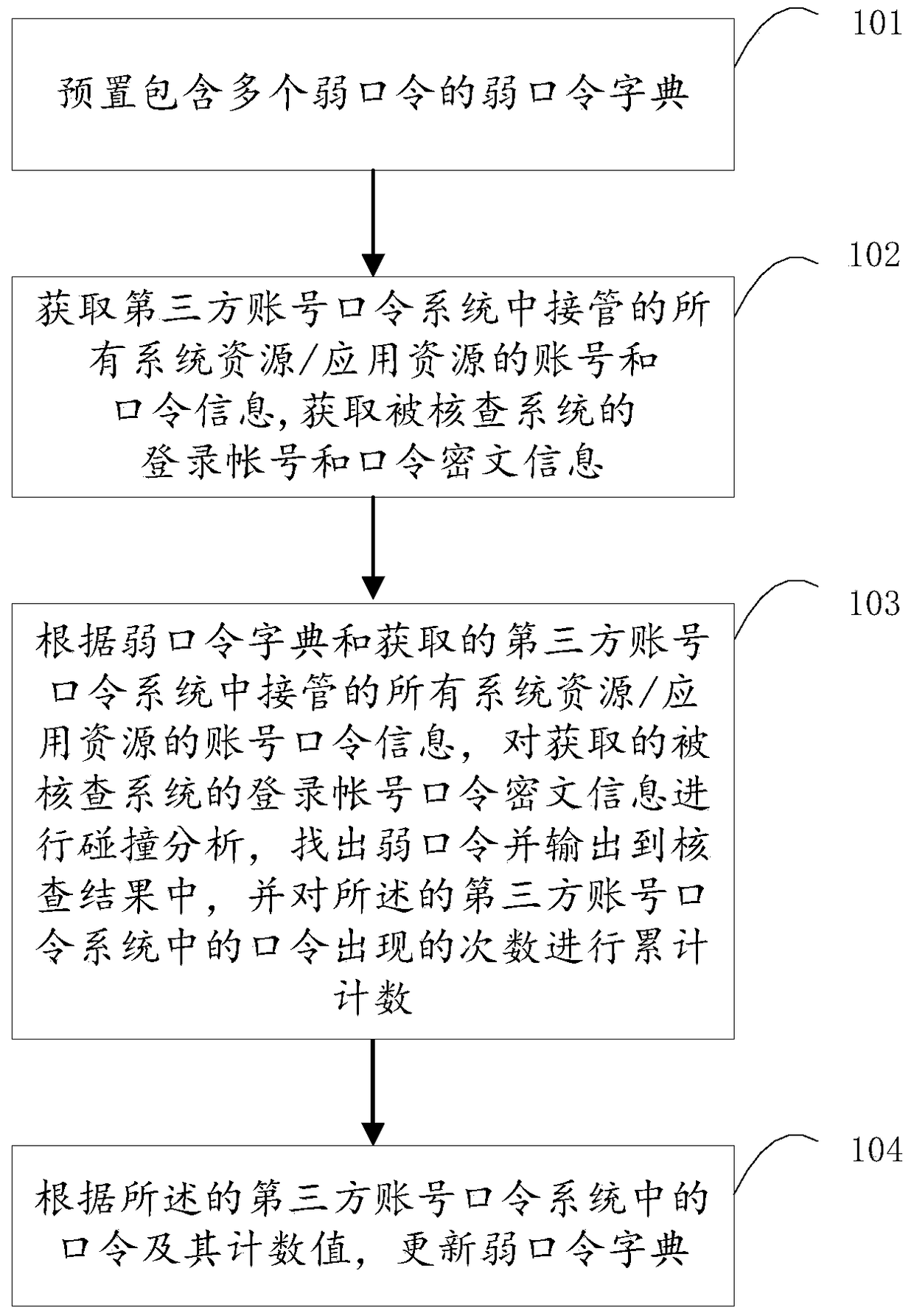
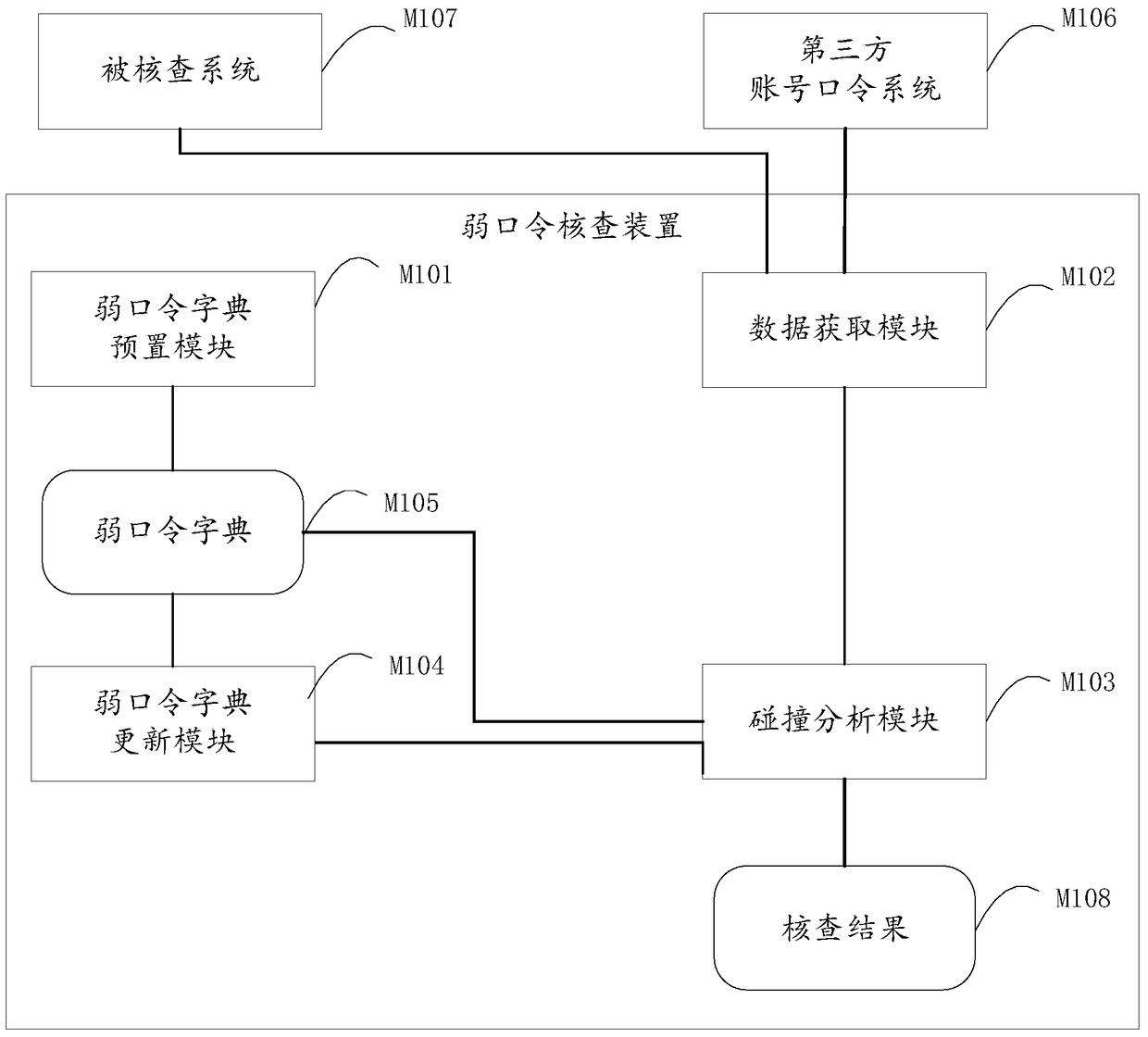
[0042] The embodiment of the present invention provides a weak password verification method, the flow chart is as follows figure 1 shown, including the following steps:
[0043] Step 101, preset a weak password dictionary containing multiple weak passwords.
[0044]In order to be easy to remember, many people use simple and easy-to-remember passwords, such as "88888888", "123456", "a1b2c3", etc., which are easy to crack. Write these commonly used passwords into the weak password dictionary first. The weak password dictionary can be a memory table or string file database composed of multiple weak passwords.
[0045] Step 102, obtaining account and password information of all system resources / application resources taken over by the third-party account password system; obtaining ciphertext information of login account passwords of the checked system.
[0046] For example, to check the weak password status of host A, you can obtain all accounts (such as zhangsan , lisi) and pa...
Embodiment 2
[0053] Based on the technical solution of Embodiment 1, the process of performing collision analysis on the ciphertext of the login account password of the checked system can be specifically as follows:
[0054] According to the weak password dictionary, the login account password ciphertext information of the checked system is collided and matched, if the collision is successful, then it is determined that the matched password is a weak password and output to the verification result; and the third-party account password system The number of occurrences of the password in is cumulatively counted.
[0055] This solution, on the basis of continuing the collision analysis based on the weak password dictionary in the prior art, adds consideration of the password factors in the third-party account password system to prepare for expanding the weak password dictionary.
[0056] For example, there are 30 passwords in the third-party account password system, including five passwords A,...
Embodiment 3
[0058] Based on the technical solution of Embodiment 1, the process of performing collision analysis on the ciphertext information of the login account password of the checked system can also be specifically:
[0059] According to the account and password information of all system resources / application resources taken over by the third-party account password system, the login account password ciphertext information of the checked system is collided and matched. If the collision is successful, it is determined whether the matched password is included in weak password dictionary; if included, the matching password is a weak password and output to the verification result, if not included, the number of occurrences of the matching password is cumulatively counted.
[0060] For example, extract an account number and corresponding ciphertext X1 (such as zhangsan, 14346e3e52c762f3) from the password ciphertext of host A of the checked system; qawsed);
[0061] The password encryptio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com