Method for implementing CMS based system for grouped security management of files
An implementation method and technology for a management system, which are applied in the field of organization confidential information files and personal privacy information file grouping confidentiality management systems, can solve the problems of poor security, non-compliant files and one-to-many, many-to-many relationships between visitors and visitors. Cloud mode is vulnerable to attacks, etc., to achieve the effect of flexible settings and good confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0109] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
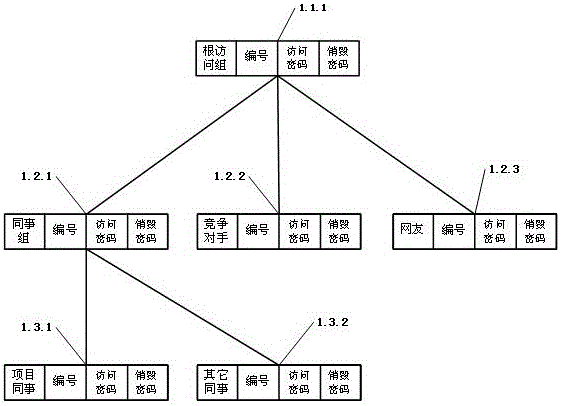
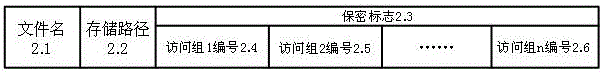
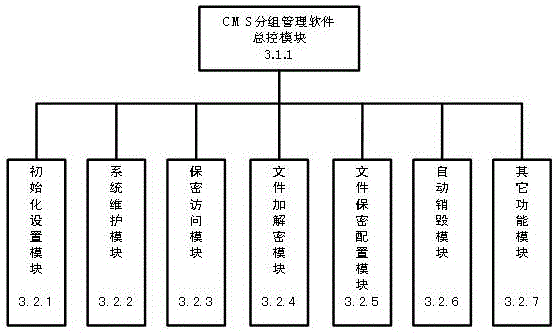
[0110] The present invention relates to a kind of realization method based on CMS file grouping security management system, such as Figure 5 As shown, the security management system includes two parts: storage and access group. In the storage, all files are stored, including some files that need to be kept secret, such as file 1, file 2 and file n. In the access group, Contains the root access group, and also contains access group 1, access group 2, and access group n.
[0111] figure 1 It is a group structure diagram of the CMS access group in the present invention. Among them, 1.1.1 is the root access group. Under the root access group, there are three secondary access groups, namely: colleague access group 1.2.1, competitor access group 1.2.2, colleague access group 1.2.3, and , under the colleague visit group, there are two third-level...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com