Identity identification and voice interaction operating method and device
A voice interaction and identity recognition technology, applied in voice analysis, voice recognition, secure communication devices, etc., can solve the problems of low usage rate of voice recognition technology, and achieve the effect of improving user experience, convenient operation, simple, convenient and fast operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0024] figure 1 It is a flowchart of a method for identity recognition and voice interaction in the embodiment of the present invention, combined with figure 1 , an embodiment of the present invention provides an identity recognition and voice interaction operation method, including:
[0025] Step S101: Acquire a user's voice command, extract acoustic feature information of the voice command, and perform user identity verification according to the acoustic feature information;
[0026] The production of human speech is a complex physiological and physical process between the human language center and the vocal organs. The vocal organs that people use when speaking—the tongue, teeth, larynx, lungs, and nasal cavity are very different in size and shape. , so the voiceprints of any two people are different. Since each person's vocal organs are different, according to the differences in the voiceprints in human speech, extracting the acoustic features in them can distinguish the ...
Embodiment 2
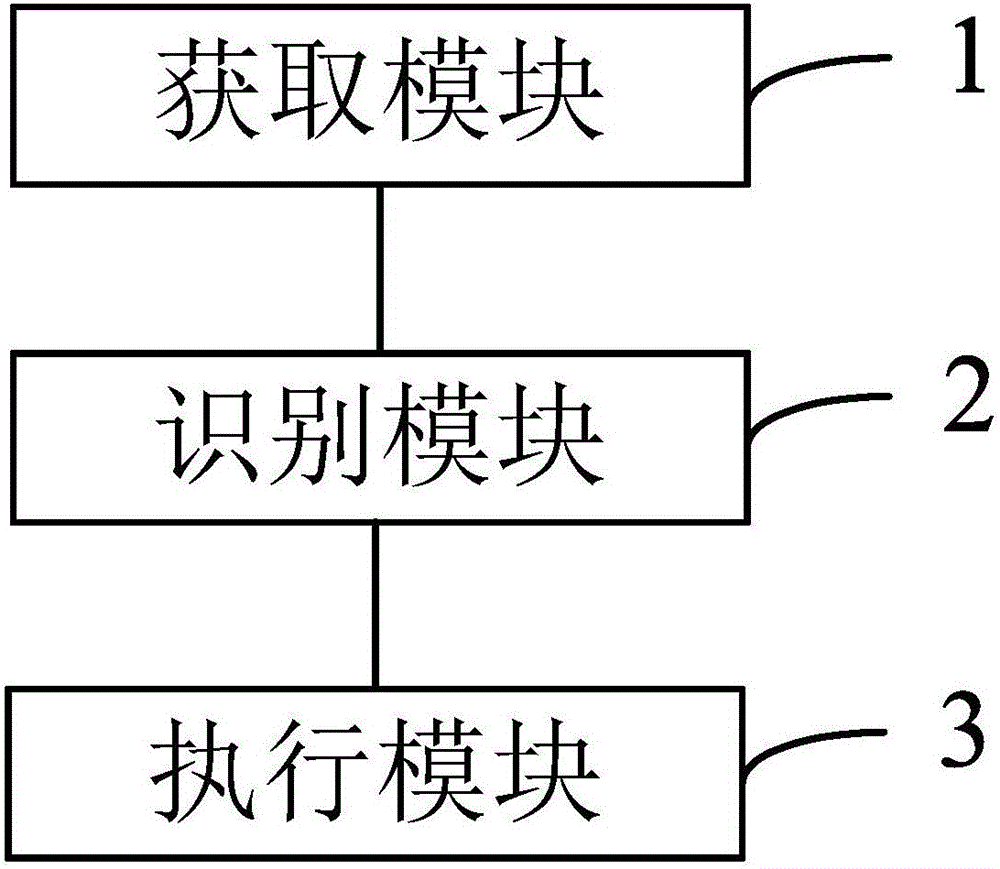
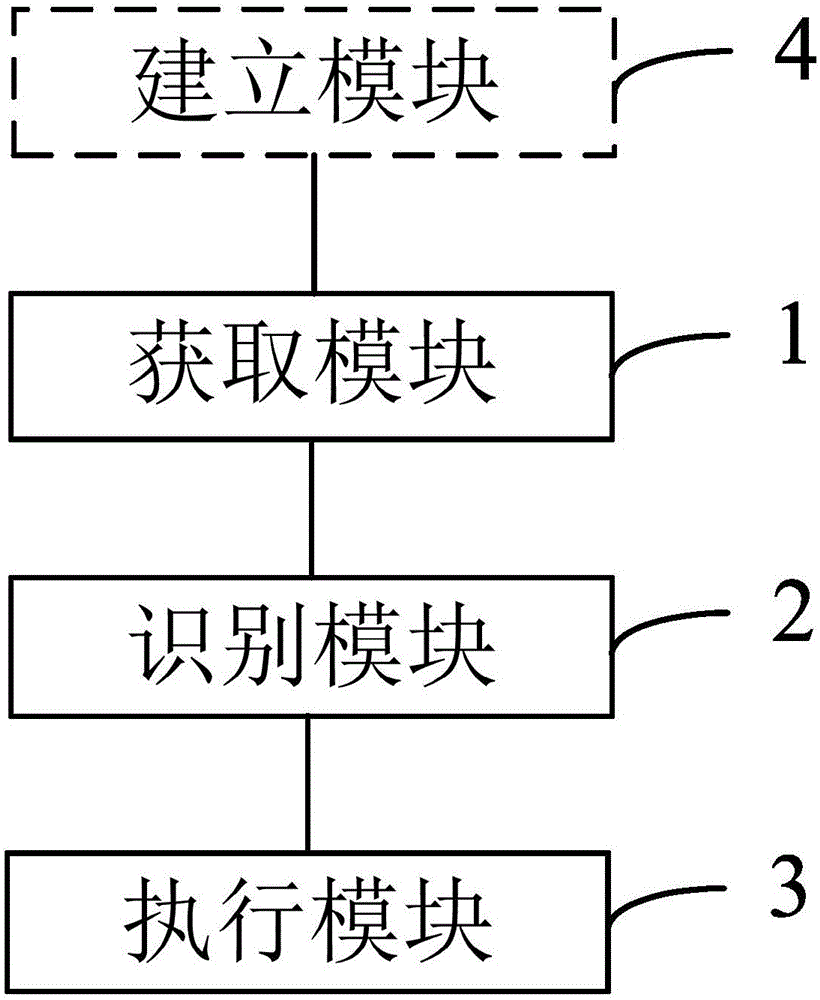
[0052] figure 2 It is a schematic structural diagram of an apparatus for interactive operation of identity recognition and voice in an embodiment of the present invention, such as figure 2 shown:
[0053] Correspondingly, the embodiment of the present invention also provides an identity recognition and voice interactive operation device, including:
[0054] The acquisition module 1 is used for acquiring the user's voice command, extracting the acoustic feature information of the voice command, and performing user identity verification according to the acoustic feature information;
[0055] The identification module 2 is used for recognizing the voice command after the user identity verification is passed, and judging whether the voice command corresponds to the preset operation command according to the correspondence between the voice command and the preset operation command;
[0056] The identification module 2 is coupled with the acquisition module 1, the acquisition mod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com