Authority adding method, device, and system, and authority addition requesting method and device
A technology for adding requests and authentication requests, applied in the computer field, can solve the problem of complex and single user rights adding process, and achieve the effect of improving efficiency and convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
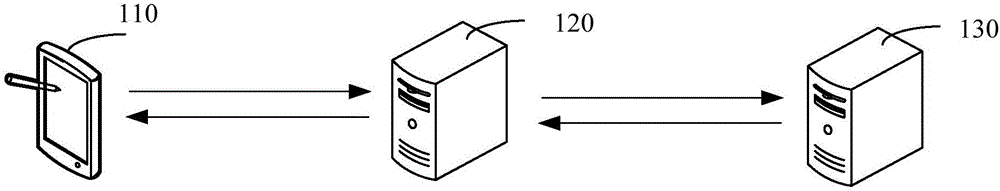
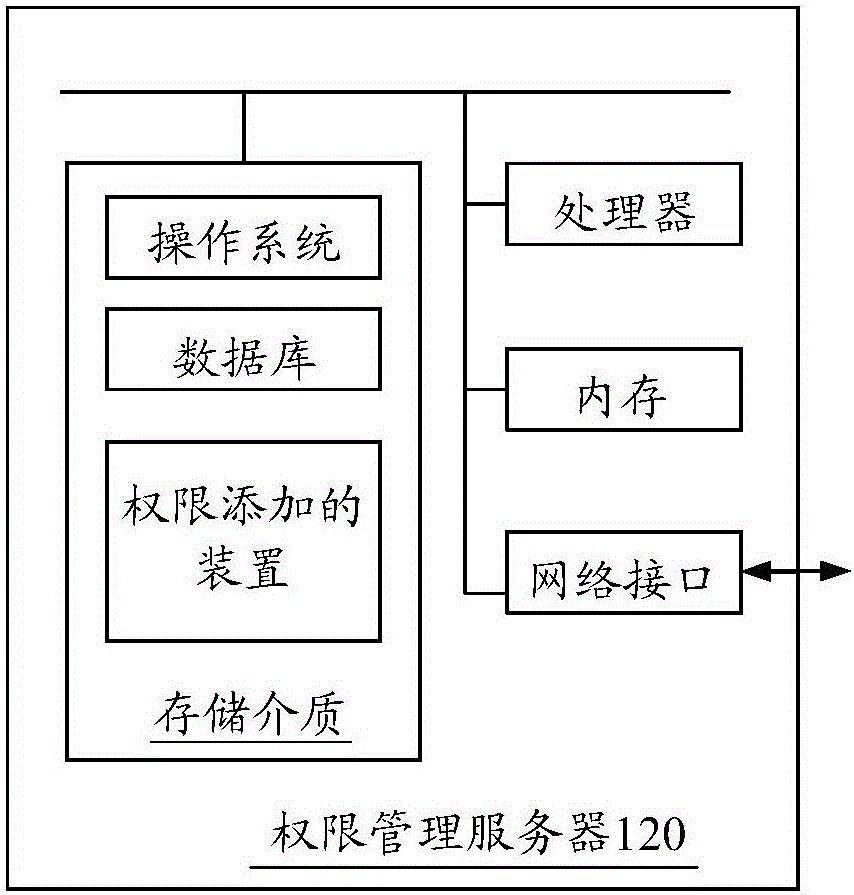
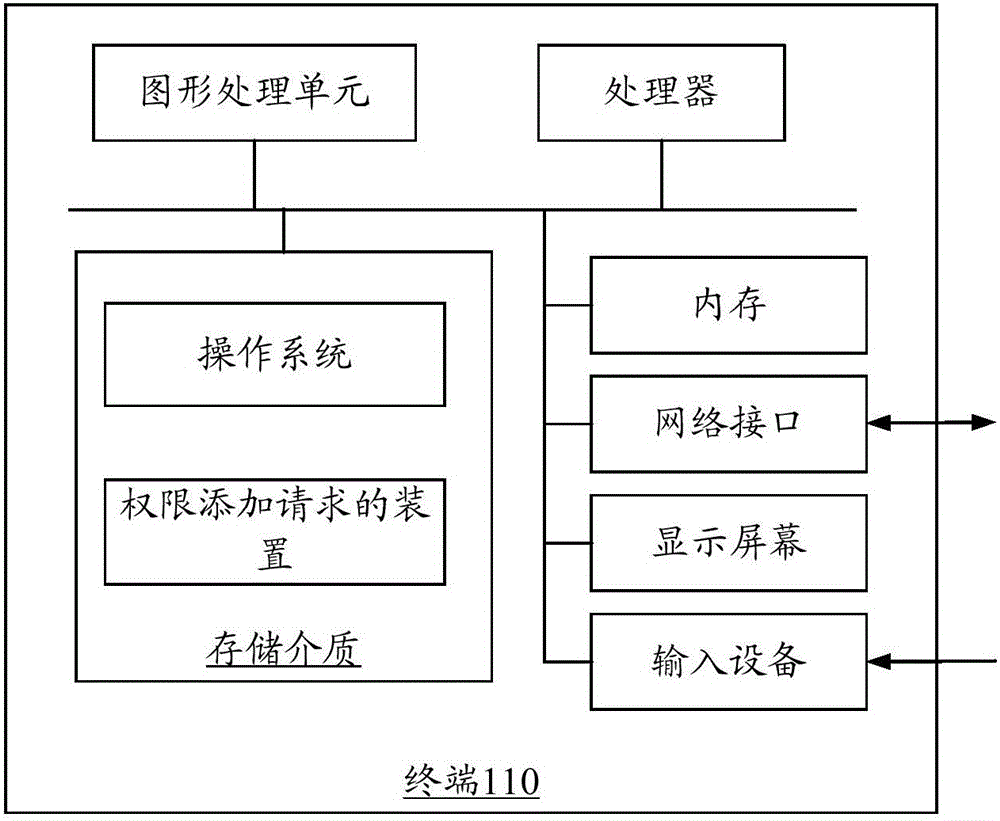
[0047] figure 1 It is an application environment diagram for the operation of the methods of permission addition and permission addition request in an embodiment. Such as figure 1 As shown, the application environment includes a terminal 110, a rights management server 120, and an enterprise background server 130, and they communicate through a network.
[0048] The terminal 110 may be a smart phone, a tablet computer, a notebook computer, a desktop computer, etc., but is not limited thereto. The terminal 110 can send data to the authority management server 120 through the network, such as user information, or data sent by the authority management server 120, etc., and the authority management server 120 can respond to the enterprise group authority authentication request sent by the terminal 110, the enterprise group join request etc. The rights management server 120 performs authentication and verification of user rights, and generates rights addition requests correspondi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com