Automatic defense system and method of ddos attack
An automatic defense and automatic technology, applied in the field of network security, can solve problems such as timeliness cannot meet the high service level, and achieve the effect of rapid identification and automatic defense, fast automatic recovery, and avoid manual operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention is further illustrated below by means of examples, but the present invention is not limited to the scope of the examples.
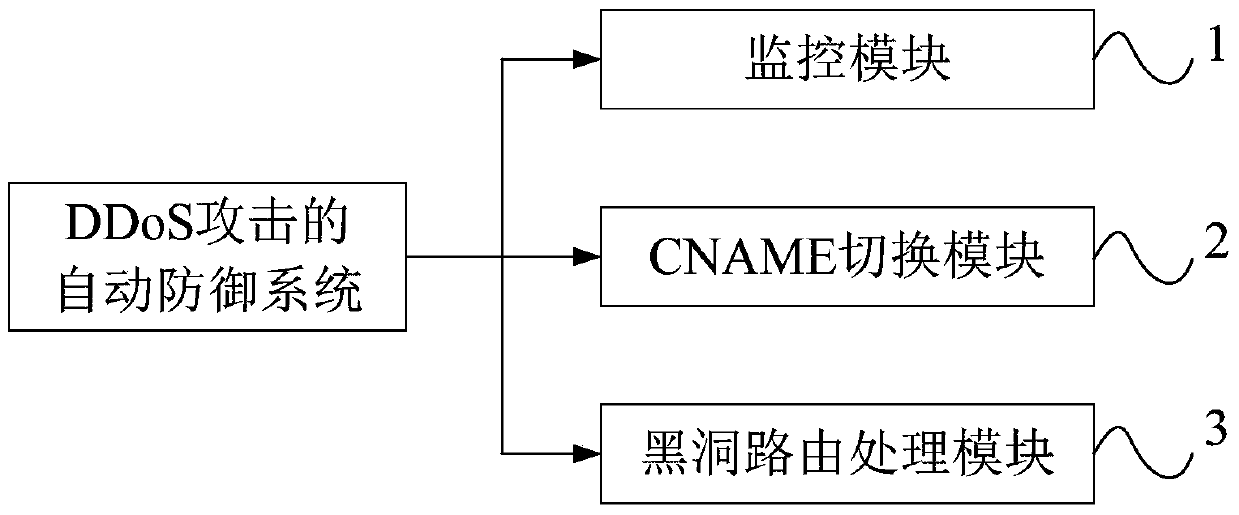
[0026] Such as figure 1 As shown, the DDoS attack automatic defense system of the present invention includes a monitoring module 1 , a CNAME switching module 2 and a black hole routing processing module 3 .
[0027] Wherein, the monitoring module 1 receives the message of the network security analysis system in real time, collects the data in the network system in real time, and resolves the site and the IP address of the website attacked by DDoS from the network system data;
[0028] Preferably, the monitoring module 1 also analyzes the attack type, attack magnitude and attack time of the DDoS attack at the same time, and displays it through a webpage, and can also send it to relevant staff such as security engineers by email or SMS.
[0029] The monitoring module 1 also sends the site and IP address, DDoS attack attack type...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com