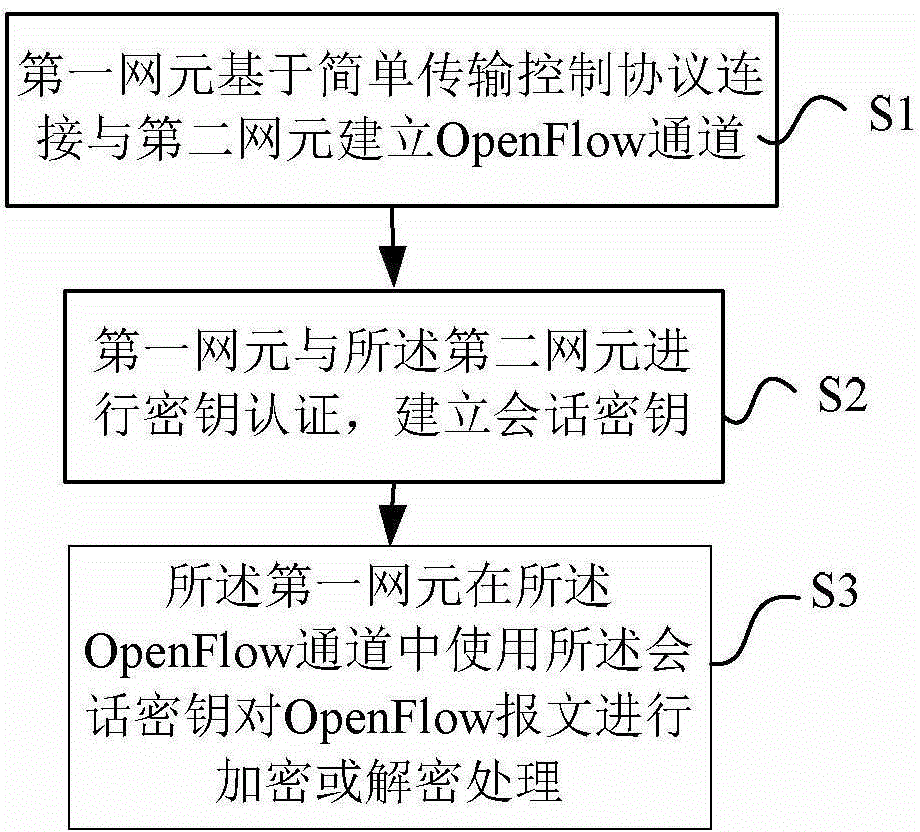
OpenFlow message processing method and network element
A processing method and network element technology, applied in electrical components, data exchange networks, digital transmission systems, etc., can solve problems such as unspecified, and achieve the effect of ensuring integrity and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
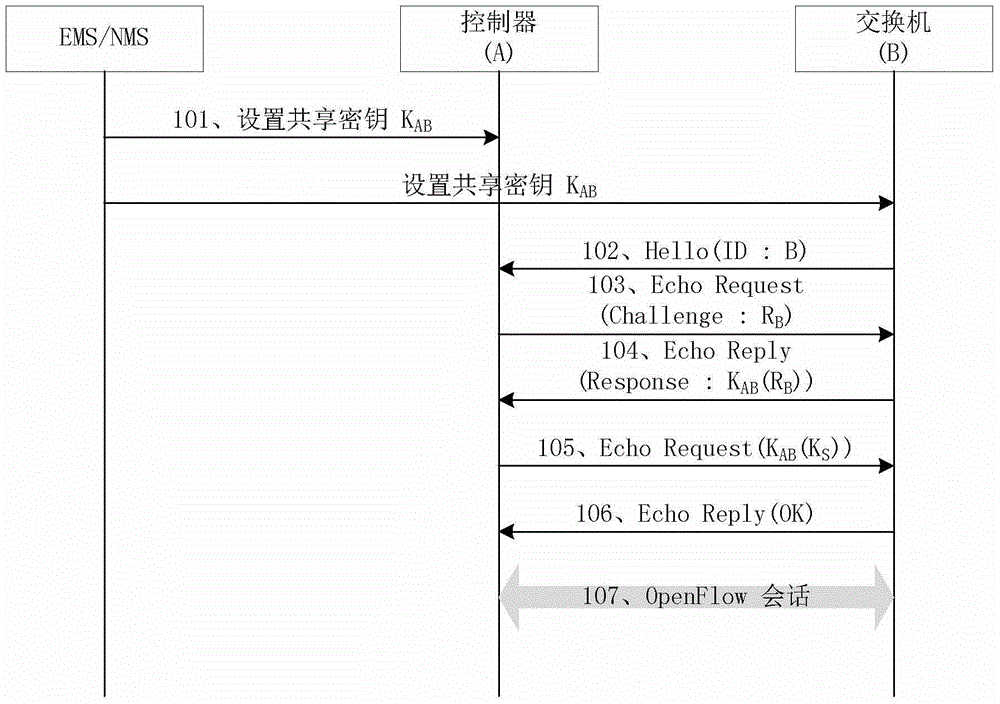
[0059] Embodiment 1: Use a shared key for authentication.
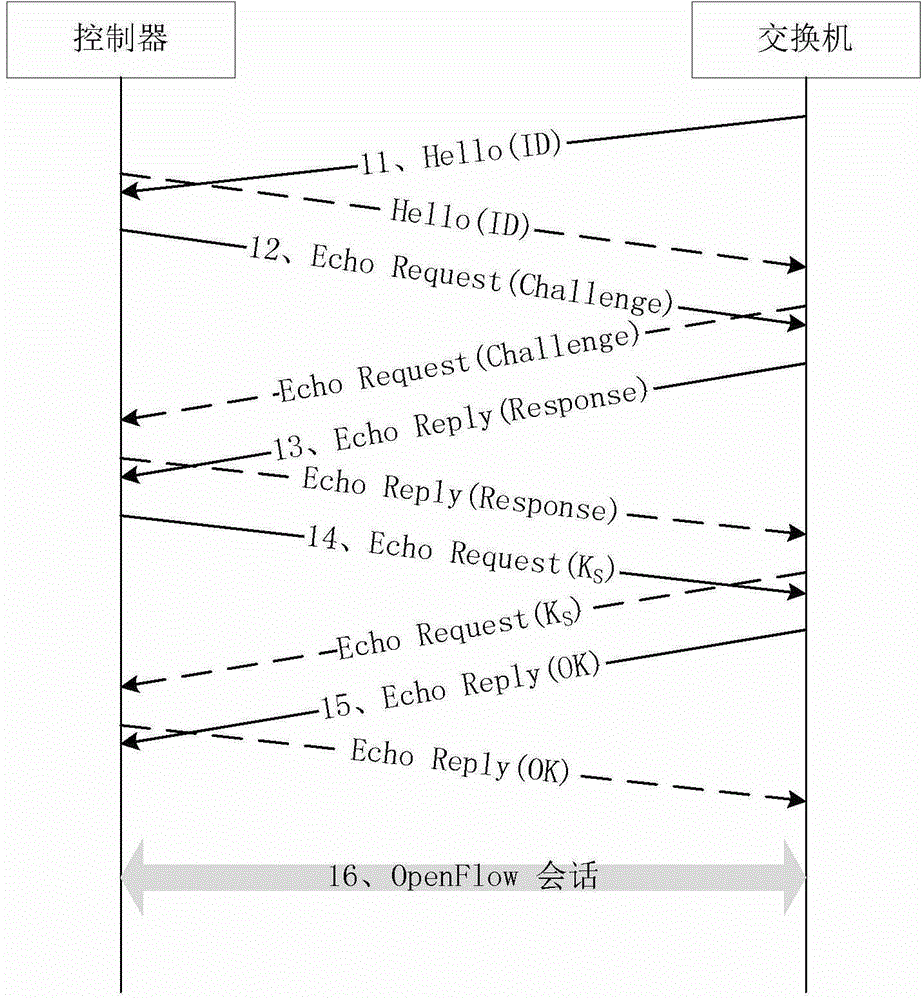
[0060] image 3 The method for authentication between the OpenFlow controller and the OpenFlow switch through the shared key is given in , including the following steps:
[0061] Step 101, share key K by EMS (network element management system) / NMS (Network Management System, network management system) AB Configured for OpenFlow controller and OpenFlow switch respectively;
[0062] Step 102, after the OpenFlow channel is established, the OpenFlow switch carries its own identity (ID: B) in the Hello message and sends it to the OpenFlow controller;
[0063] Step 103, after the OpenFlow controller receives the Hello message sent by the OpenFlow switch, it generates a random number R B As a challenge, carried in the Echo Request message and sent to the OpenFlow switch;
[0064] Step 104: After the OpenFlow switch receives the Echo Request message sent by the OpenFlow controller, it uses the shared key K AB Encrypt R ...
Embodiment 2
[0068] Embodiment 2: query the PKI directory server for the public key, and use the public key for authentication.
[0069] Figure 4 The procedure for obtaining and authenticating a public key through a PKI directory server between an OpenFlow controller and an OpenFlow switch is given in . Wherein, the PKI directory server stores the public key information of the OpenFlow switch and the OpenFlow controller. Include the following steps:
[0070] Step 201, after the OpenFlow channel is established, the OpenFlow controller carries its own identity (ID: A) in the Hello message and sends it to the OpenFlow switch;
[0071] Step 202, after the OpenFlow switch receives the Hello message sent by the OpenFlow controller, it requests the public key E of the OpenFlow controller from the PKI directory server A ;
[0072] Step 203, the PKI directory server sends the public key E of the OpenFlow controller A Send to OpenFlow switch;
[0073] Step 204, the OpenFlow switch sends its o...
Embodiment 3
[0080] Embodiment 3: Authentication is performed through a credible key distribution center.
[0081] Figure 4 A method for authentication between the OpenFlow controller and the OpenFlow switch through the key distribution center is given in , and the key distribution center is trusted for both the OpenFlow controller and the OpenFlow switch. Including the following steps:
[0082] Step 301, after the OpenFlow channel is established, the OpenFlow switch carries its own identity (ID: B) in the Hello message and sends it to the OpenFlow controller;
[0083] Step 302, the OpenFlow controller sends a random number R A , and the identity A of the OpenFlow controller and the identity B of the OpenFlow switch are sent to the key distribution center;
[0084] Step 303, the key distribution center establishes a session key K S , and use the shared key K between the key distribution center and the OpenFlow switch B Put the ID A of the OpenFlow controller and the session key K S ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com