Authorization authentication method, device and system
An authentication device and digital authentication technology, applied in the electronic field, can solve problems such as user property and information loss, and achieve the effect of ensuring relevance, unity, and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
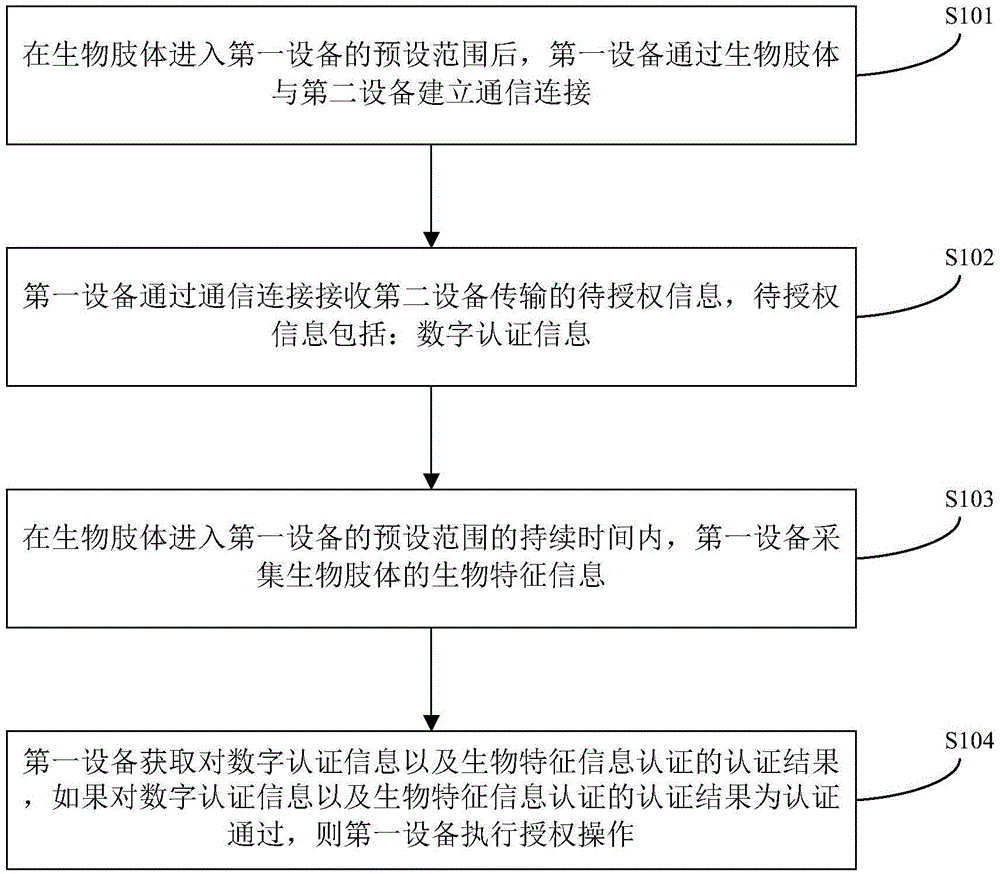
[0039] The present invention provides an authorization authentication method, such as figure 1 shown, including:
[0040] Step S101, after the biological limb enters the preset range of the first device, the first device establishes a communication connection with the second device through the biological limb.
[0041] In a specific implementation manner, the first device has a biological feature collection function, and can communicate with the second device through biological limbs. The first device can be used to manage the access or use rights of places (office areas, confidential areas), website logins, personal items (cars, safes, etc.), dangerous items, etc., and the first device can also be used to execute transactions, For example, it can be access control card reader, smart car lock, safe lock, dangerous goods manager, computer with biometric function, ATM machine and POS machine, etc.
[0042] The second device is placed outside the living body (including the huma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com