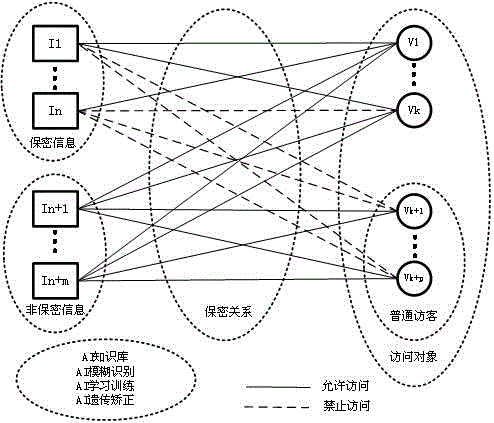
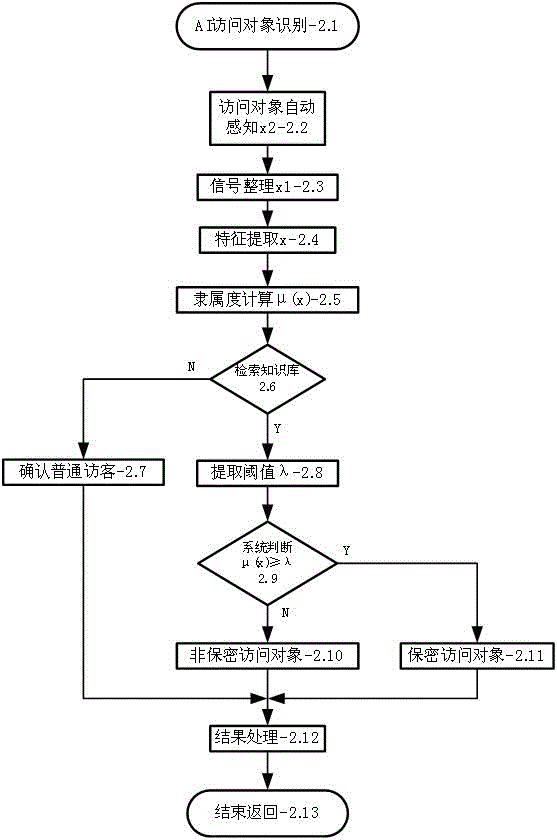
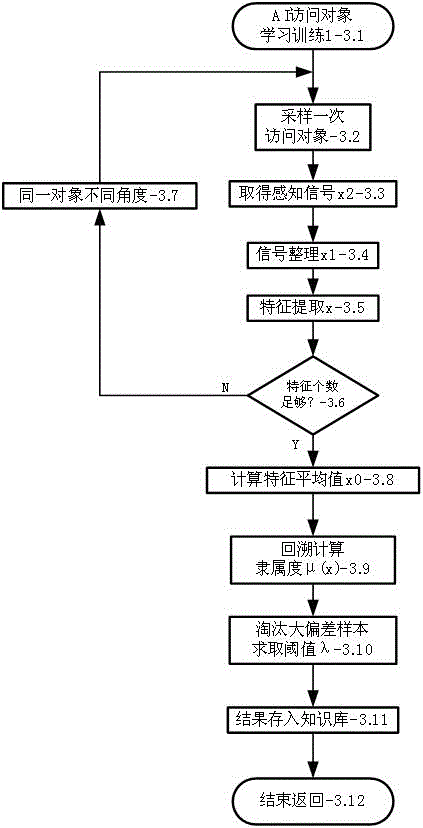
CMS object-oriented artificial intelligence information secrecy system
An artificial intelligence, object-oriented technology, applied in the information field, can solve the problems of not subdividing confidential objects, not adopting automatic identification, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
[0215] Specific embodiment 1, private cloud single-user version
[0216] overview
[0217] This embodiment is an exemplary example of the iPhone-oriented private cloud single-user of the present invention.
[0218] Figure 8 It is a structural diagram of the embodiment, which is composed of a smart phone 8.1, a CMS AIAPP software 8.2 installed on the smart phone and a private cloud storage 8.3. Among them, smartphone 8.1 is a smartphone with mainstream configurations before the filing date of the present invention, such as iPhone 6Plus, SANSUNG Galaxy S7 edg, Huawei P9 plus, Xiaomi Mi 5 Premium Edition, etc. It should be noted that these phones have front And the cameras on both sides of the back, in order to capture the signal that the visiting subject joins. The front camera refers to the camera on the same side as the display screen of the mobile phone, and the rear camera refers to the camera located on the back of the display screen of the mobile phone.
[0219] The f...
specific Embodiment 2
[0248] Specific embodiment two, augmented reality AR version
[0249] overview
[0250] This embodiment is an exemplary example of the present invention oriented to AR augmented virtual reality.
[0251] Figure 10 It is AR glasses, which are used as the host device of this embodiment to design this embodiment. Among them, it includes a front camera facing the front of the glasses, a pupil-capturing rear camera facing oneself, a retinal projection display, and a complete set of sensors and CPU processing information systems.
[0252] System Differentiation Description
[0253] Compared with Embodiment 1, the present embodiment will not repeat the similarities, and the differences are:
[0254] 1. Cancel the private cloud storage and change to the internal storage of the AR glasses.
[0255] 2. Cancel the flashback access and change the alarm prompt. Since the display of this embodiment adopts retinal projection, only the user can see it, so there is no need to worry ab...
specific Embodiment 3
[0258] Specific embodiment three, CMS WeChat special version
[0259] overview
[0260] This embodiment is an illustrative example of the future upgrade of the present invention for WeChat, which is referred to as CMS WeChat for short.
[0261] A smartphone is used as the host device in this embodiment. The camera on the back of the mobile phone is used to identify the access object, and the front camera is used to identify the owner.
[0262] System Differentiation Description
[0263] Compared with Embodiment 1, the present embodiment will not repeat the similarities, and the differences are:
[0264] 1. Cancel the private cloud storage and change it to the internal storage of the smartphone.
[0265] 2. The independently developed CMS AI APP is changed to integrated development with WeChat software, or is authorized by Tencent Technology, the owner of WeChat software.
[0266] 3. Various functions of the present invention are integrated into the chat interface and the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com