Multipoint Hook reversing method for Android reinforcing application
A multi-point, tested application technology, applied in the field of information security, can solve problems such as incorrect function code, empty, and Android application APK cannot be installed, and achieve the effect of ensuring reliability and effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The present invention will be further described in detail below in conjunction with the accompanying drawings.
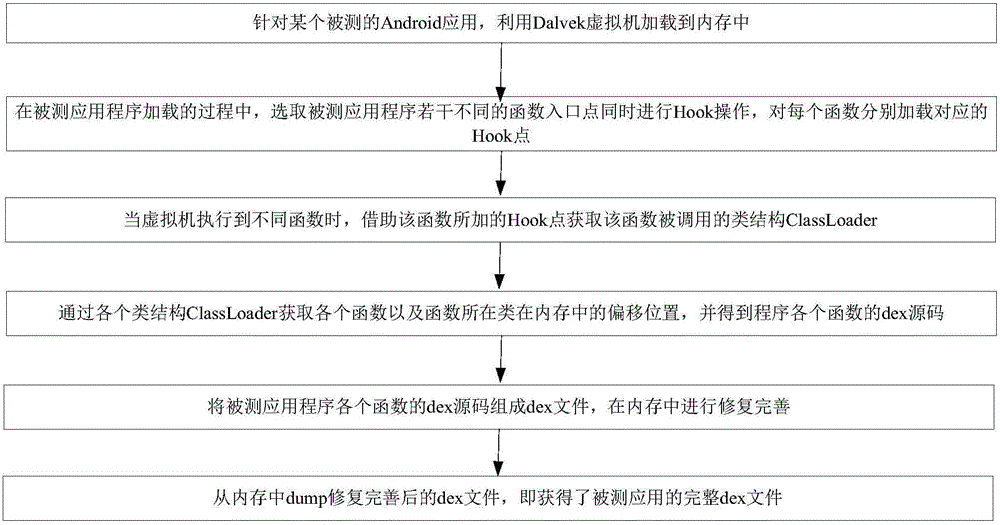
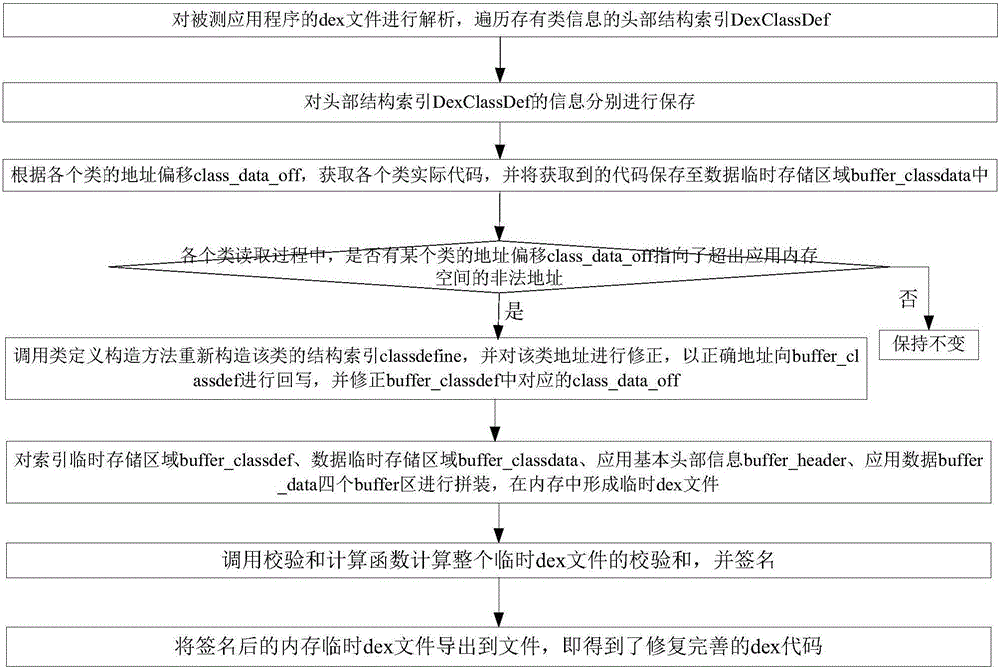
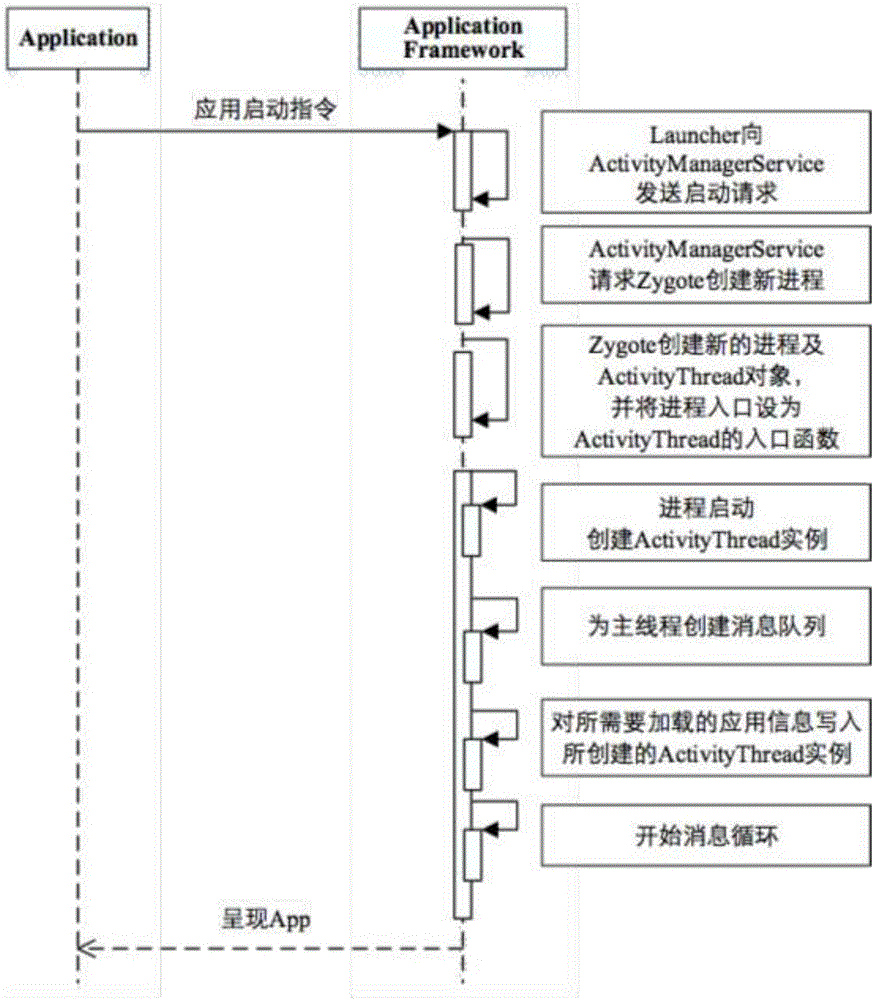
[0048] At present, the method of obtaining app source code is generally static analysis or single-point hook, resulting in incomplete app source code, or cannot be restored to a usable app; although the points selected by multi-point hook are somewhat arbitrary, in order to Each execution branch, function, and class are covered, and the better function entry point is hooked. Through the multi-point Hook reverse method, the hardened Android application is hooked at different locations, and the ClassLoader obtained from different locations is further Obtain the offset position of dex in the memory, obtain the dex source code of each part of the program, and finally organize, combine and repair all the obtained dex, and finally obtain the complete application dex, so that the application surface of Android reverse analysis has been extremely improved. The expans...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com