Method and system for realizing browser access to intelligent key device
An intelligent key device and browser technology, applied in the field of communications, can solve problems such as hidden dangers, system security, browser crashes, etc., and achieve the effects of high security, good stability, and wide application range.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0031] This embodiment provides a method for implementing a browser to access a smart key device, such as figure 1 shown, including the following steps:
[0032] Step S1: the extension program receives the first data from the browser, and sends the first data to the local application program;
[0033] Step S2: The local application parses the first data to obtain communication parameters, calls the driver interface of the smart key device according to the communication parameters, sends corresponding instructions to the smart key device, and receives the operation result returned by the smart key device;
[0034] Step S3: The local application program organizes the second data according to the received operation result, and sends the second data to the extension program;
[0035] Step S4: the extension program receives the second data, and sends the second data to the browser.
[0036] In the above step S1 of this embodiment, before the extension program sends the first data...
Embodiment 2
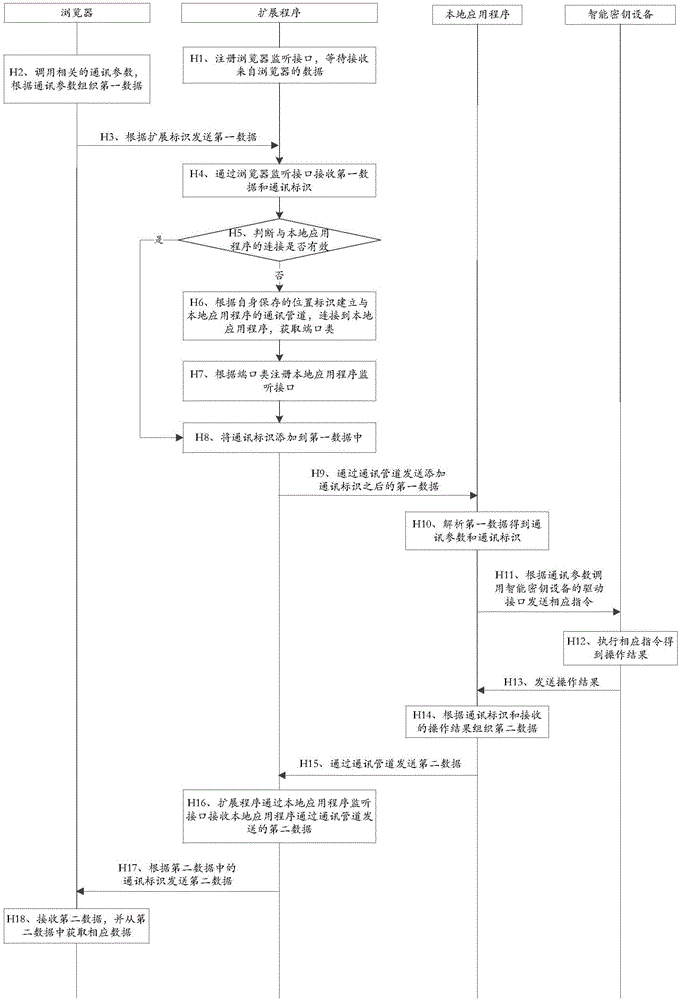
[0075] This embodiment provides a method for implementing a browser to access a smart key device, which is applied to a system including a browser, an extension program, a local application program, and a smart key device. Such as figure 2 shown, including:
[0076] Step H1: The extension program registers the browser monitoring interface and waits to receive data from the browser.
[0077] Specifically, the extension program registers the browser monitoring interface, specifically: when the extension program starts, the extension program registers the first extension function as the browser monitoring interface. More specifically, the extension program registers the first extension function as the browser monitoring interface, specifically: the extension program invokes the first system function to register the first extension function as the browser monitoring interface.
[0078] For example, the first extension function is: function(data, sender, sendResponse);
[0079]...
Embodiment 3
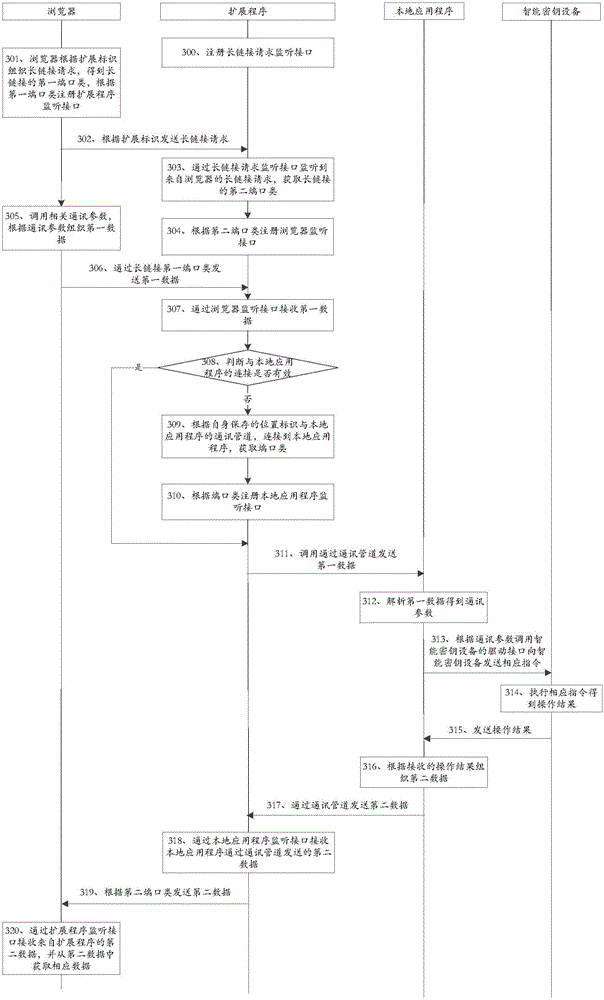
[0231] This embodiment provides a method for implementing a browser to access a smart key device, which is applied to a system including a browser, an extension program, a local application program, and a smart key device. Such as image 3 shown, including:
[0232] Step 300: the extension program registers the long link request monitoring interface;
[0233] Specifically, when the browser is started, the extension program registers the first extension function as the long link request monitoring interface. More specifically, when the browser is started, the extension program calls the first system function to register the first extension function as a long link request monitoring interface.
[0234] For example, the first extension function is: function(port2Web), port2Web;
[0235] The first system function is: chrome.runtime.onConnectExternal.addListener;
[0236] The long link request listener interface registered by the extension program is: chrome.runtime.onConnectEx...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com