Method and apparatus for disabling corrupted memory by using BMC
A memory and memory slot technology, applied in the computer field, can solve problems such as server crash and loss of key data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
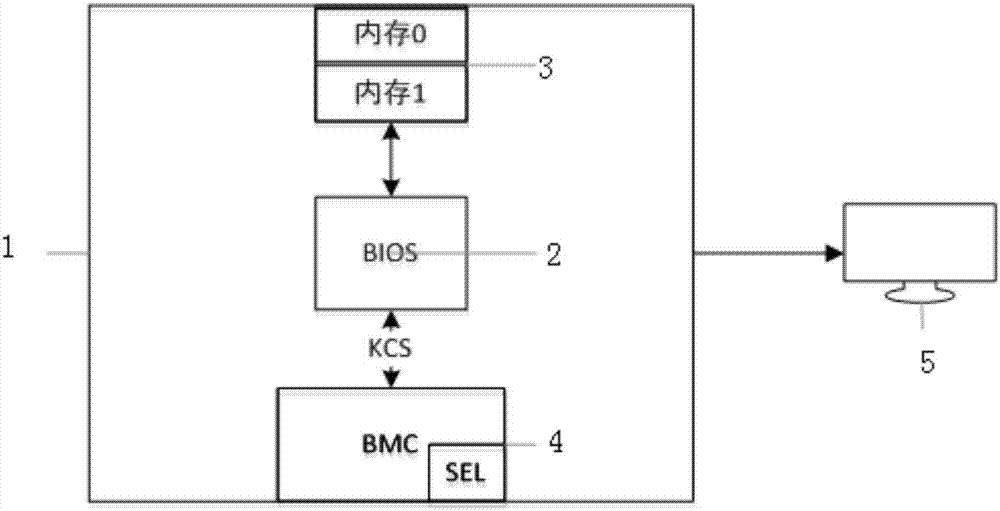
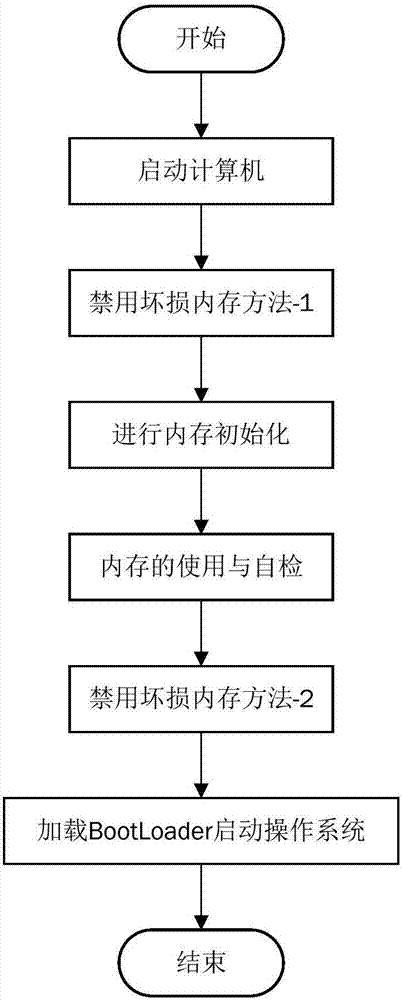
[0038] After the computer is powered on, the first program BIOS is executed. Taking the memory as the research object, the BIOS first initializes the memory, then self-tests and uses the memory, and finally starts the operating system by loading the bootloader (Boot Loader). like figure 2 As shown, this embodiment provides a method of using the BMC to disable the damaged memory. Before the BIOS is ready to initialize the memory, the "method 1 of disabling the damaged memory" is created to analyze whether there is a damaged memory, and if there is, disable it. . Before the boot operating system is started, the present invention creates a "method 2 for disabling damaged memory" to collect the self-test results of the memory by the BIOS and analyze the wrong use of the memory.
[0039] Among them, such as image 3 As shown, method 1 to disable corrupt memory includes:
[0040] (1) After the computer is started, when the BIOS runs to prepare for memory initialization, obtain ...
Embodiment 2
[0052] This embodiment provides a device for disabling damaged memory by using BMC, including:
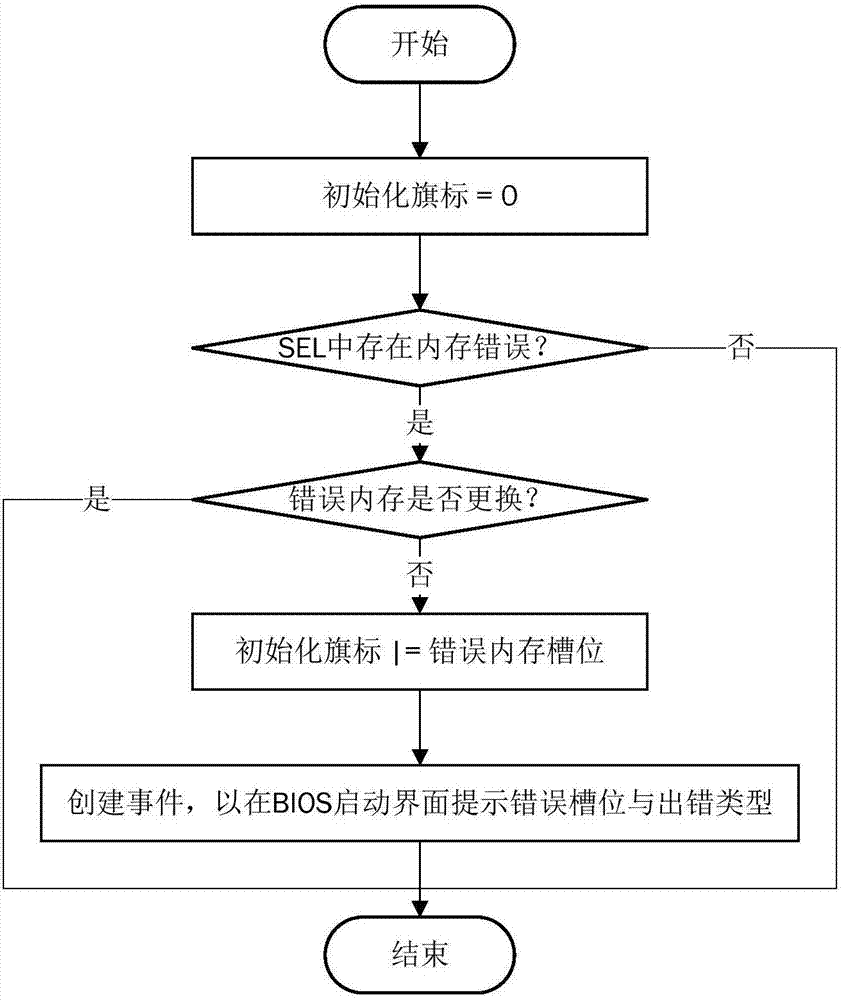
[0053] The initialization flag acquisition module is used to obtain the preset initialization flag value pi for the memory on each memory slot i when the computer is started and the BIOS runs to prepare for memory initialization; wherein, when the memory slot i When the memory on the slot i is damaged, the initialization flag value pi=1 is set, and when the memory on the memory slot i is intact, the initialization flag value pi=0 is set;
[0054] The system event log acquisition module is used to determine whether there is memory error information in the system event log of the BMC when the initialization flag value pi corresponding to the memory on the memory slot i is 0;
[0055] The damaged memory replacement judging module is used to determine whether the damaged memory is replaced by the user based on whether the serial number of the memory is changed when there is memory error ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com