Visitor door control system based on Wechat and visitor door opening method
A visitor access control and access control technology, which is applied in the visitor access control system and the field of visitor opening, can solve the problems of difficult management of visitor identities, achieve real-time data transmission and management, improve convenience, and avoid inconvenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
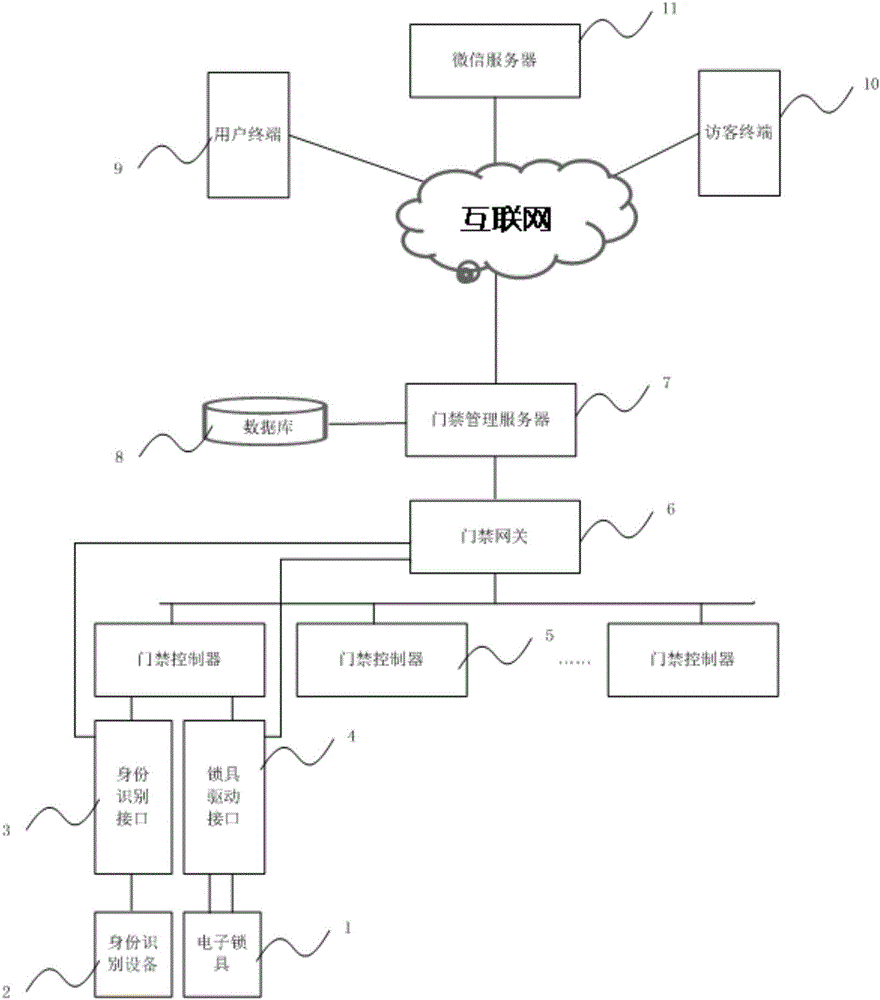
[0036] The present invention provides a visitor access control system based on WeChat, such as figure 1 As shown, a preferred embodiment of the present invention is shown therein. The visitor access control system of the present invention comprises:
[0037] At least one set of electronic lock 1 arranged on the door, a lock drive interface 4 and an access controller 5 connected to the electronic lock 1 through the lock drive interface 4 .
[0038] An access control gateway 6 for receiving, analyzing and sending control instructions, the access control gateway 6 is connected with the access control controller 5 through a network.
[0039] An access control management server 7 for managing access control information and user information, the access control management server 7 is connected to the access control gateway 6 through a network.
[0040] A visitor terminal 10 for receiving or sending instruction information, the visitor terminal 10 is connected with the access contro...
Embodiment 2
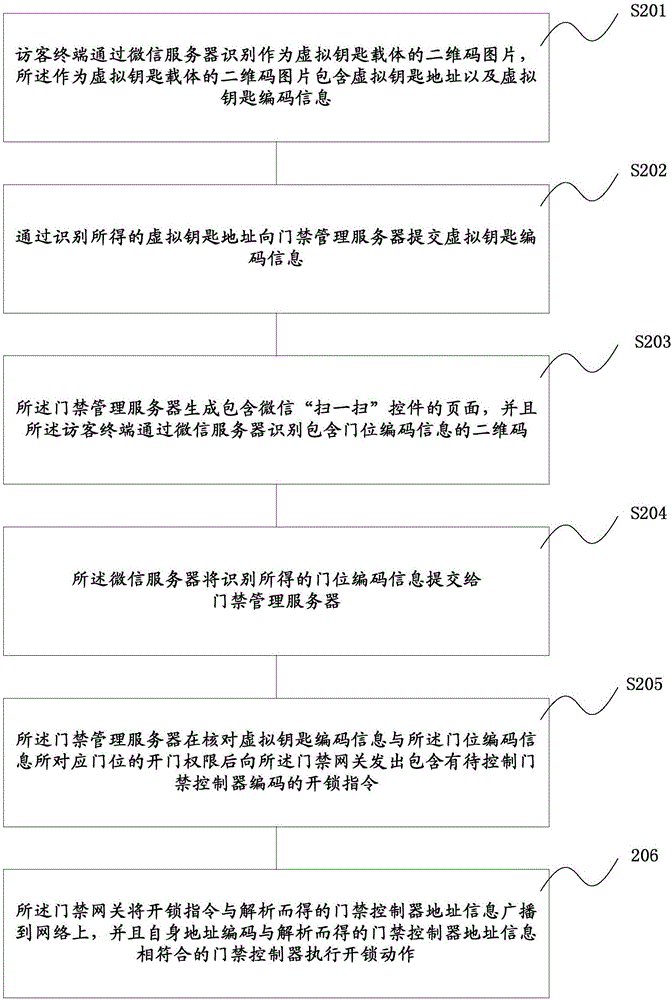
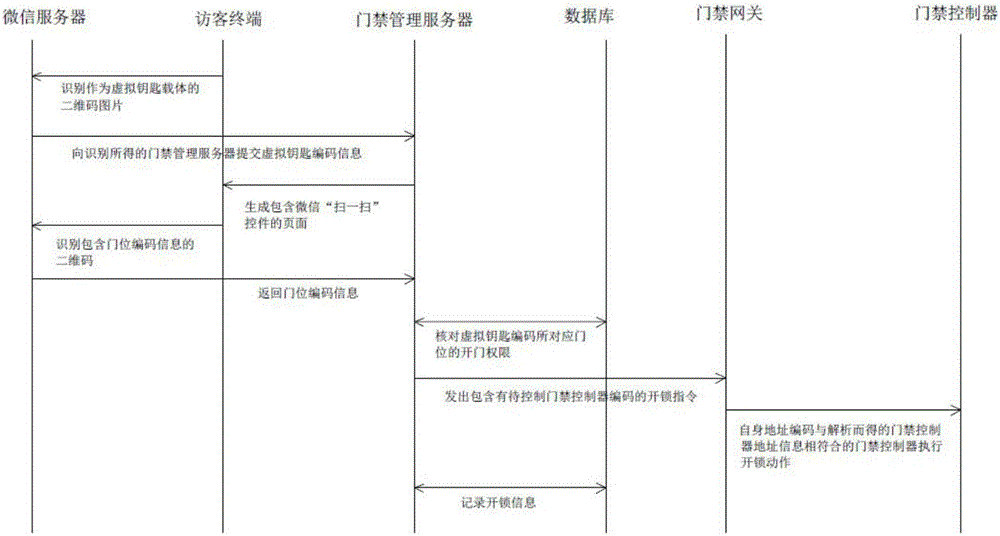
[0074] The present invention also provides a method for opening the door of visitors based on WeChat, such as figure 2 , image 3 As shown, the method for opening the door of the visitor comprises:
[0075] In step S201, the guest terminal 10 identifies the two-dimensional code image as the virtual key carrier through the WeChat server 11, and the two-dimensional code image as the virtual key carrier includes the virtual key address and virtual key code information.
[0076] The access control management server 7 generates the two-dimensional code picture as the virtual key carrier that contains the virtual key address and the virtual key code information according to the user's door opening authority, and then the user passes the two-dimensional code picture generated by the access control management server 7 as the virtual key carrier through The network sends to the visitor terminal 10 to complete the user's authorization to the visitor. Since the visitor access control ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com