Compression method and device based on cryptographic hash algorithm
A technology of hash algorithm and compression method, which is applied in the field of communication, can solve the problems of low circuit clock frequency and throughput, long circuit critical path, and large adder delay, etc., to reduce delay, shorten critical path, and improve throughput Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
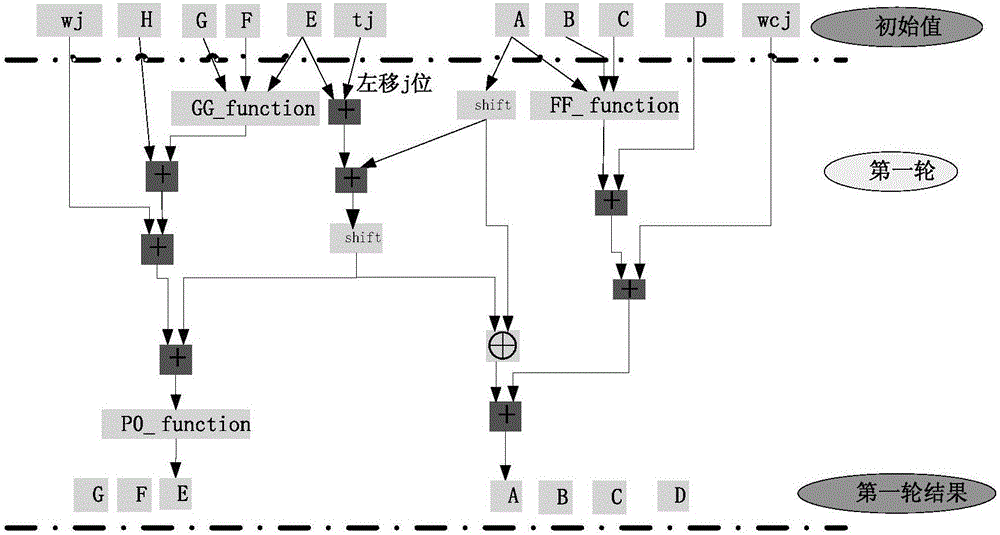
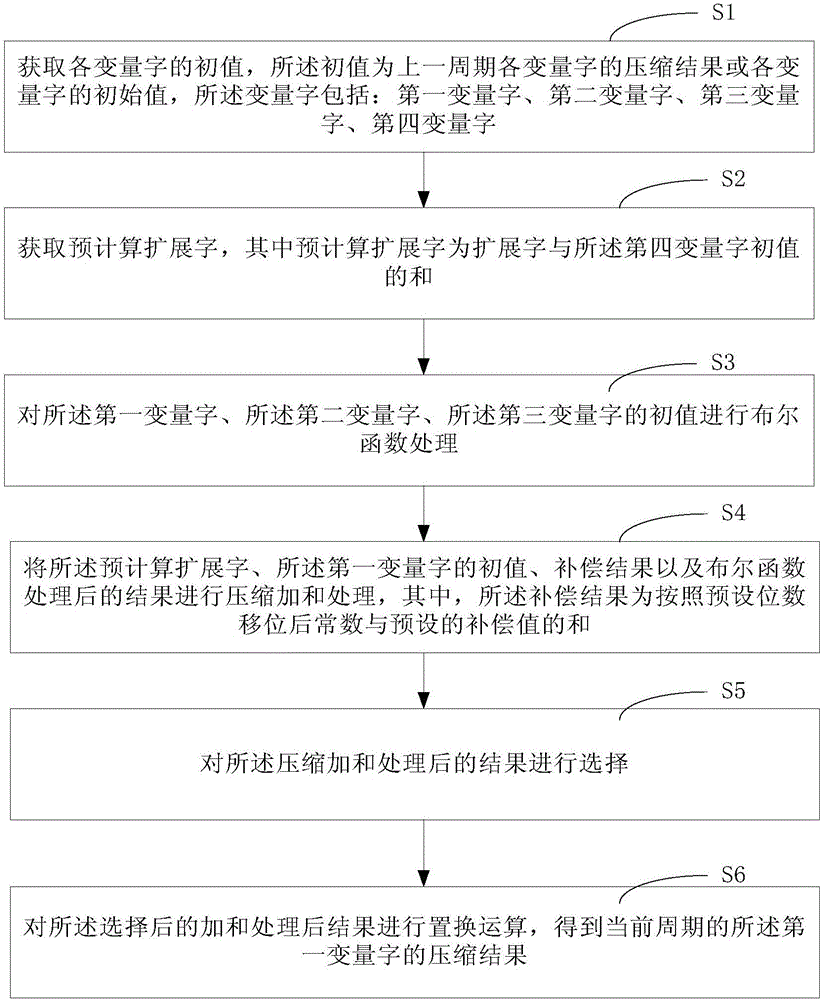
[0112] image 3 A flow chart of a cryptographic hash algorithm-based compression method provided in Embodiment 1 of the present invention, Figure 4 A schematic structural diagram of a compression circuit based on a cryptographic hash algorithm provided in Embodiment 1 of the present invention, as shown in image 3 , Figure 4 As shown, the method includes:
[0113] Step S1, obtain the initial value of each variable word, the initial value is the compression result of each variable word in the previous cycle or the initial value of each variable word, and the variable word includes: the first variable word, the second variable word, the second variable word The third variable word, the fourth variable word.
[0114] Specifically, variable words are stored in registers, the first variable word can correspond to E in the algorithm, the second variable word can correspond to F in the algorithm, the third variable word can correspond to G in the algorithm, and the fourth variab...
Embodiment 2
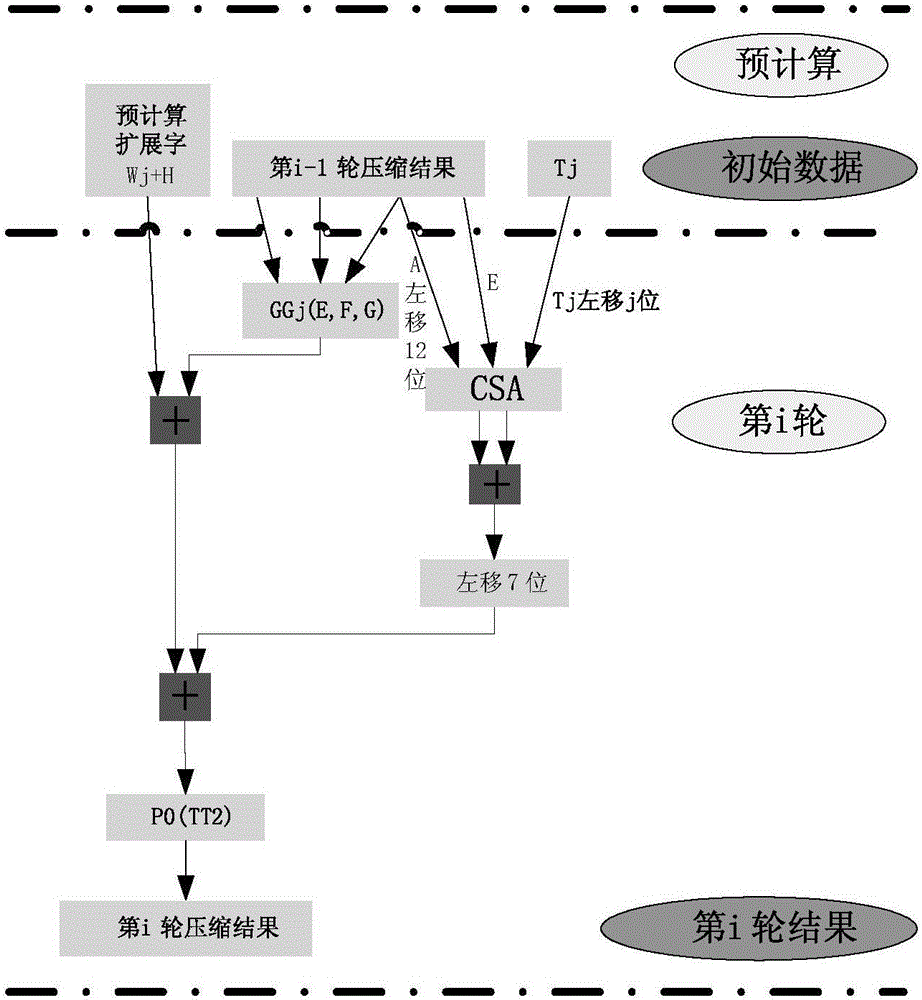
[0132] Figure 5 A flow chart of a cryptographic hash algorithm-based compression method provided in Embodiment 2 of the present invention, Figure 6 A schematic structural diagram of a compression circuit based on a cryptographic hash algorithm provided in Embodiment 2 of the present invention, in Figure 5 neutralize image 3 Steps with the same reference numbers are the same as image 3 The same text descriptions are applicable and will not be repeated here.
[0133] In this embodiment, the variable word may also include: a fifth variable word;
[0134] Step S4 may include:
[0135] Step S401, obtaining the initial value of the fifth variable word, and shifting the initial value of the fifth variable word by a preset number of digits;
[0136] The fifth variable word corresponds to the A variable word in the algorithm.
[0137] Step S402, performing three times the initial value of the shifted fifth variable word, the pre-calculated expansion word, the initial value o...
Embodiment 3
[0163] Figure 8 A schematic diagram showing the structure of the cryptographic hash algorithm-based compression device provided by Embodiment 3 of the present invention, as shown in Figure 8 As shown, the device 10 includes: an acquisition module 110 , a Boolean function processing module 120 , a compression and sum processing module 130 , a selection module 140 , and a replacement operation module 150 .
[0164] Acquisition module 110, is used for obtaining the initial value of each variable word, and described initial value is the compression result of each variable word of last period or the initial value of each variable word, and described variable word comprises: the first variable word, the second variable word word, the third variable word, the fourth variable word;
[0165] The acquiring module 110 is further configured to acquire a pre-calculated extension word, wherein the pre-calculated extension word is the sum of the extension word and the initial value of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com