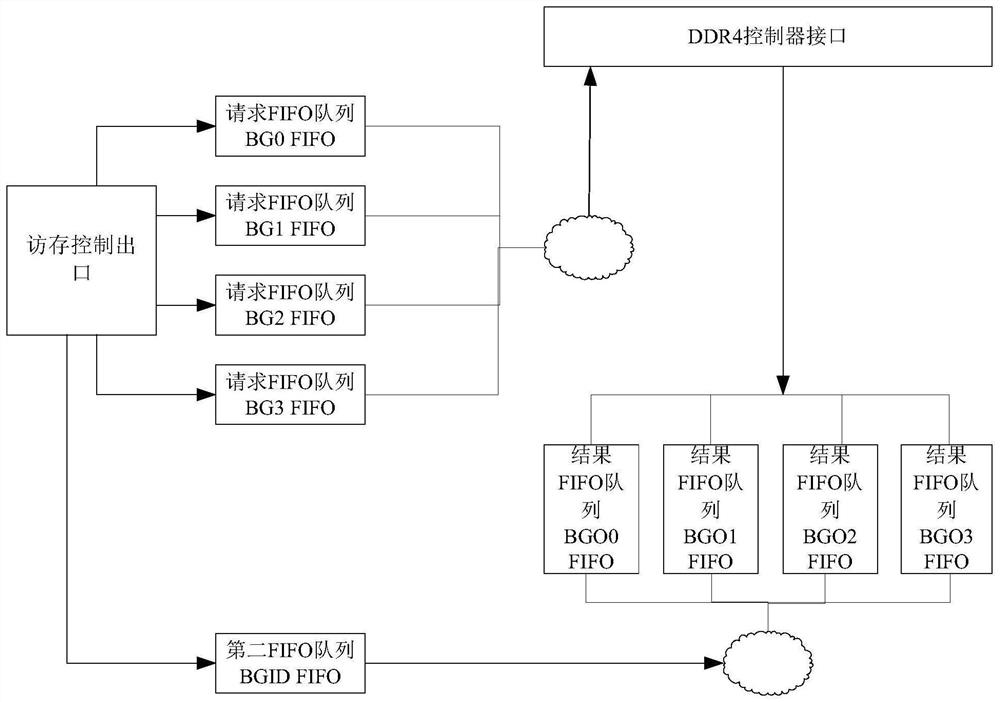
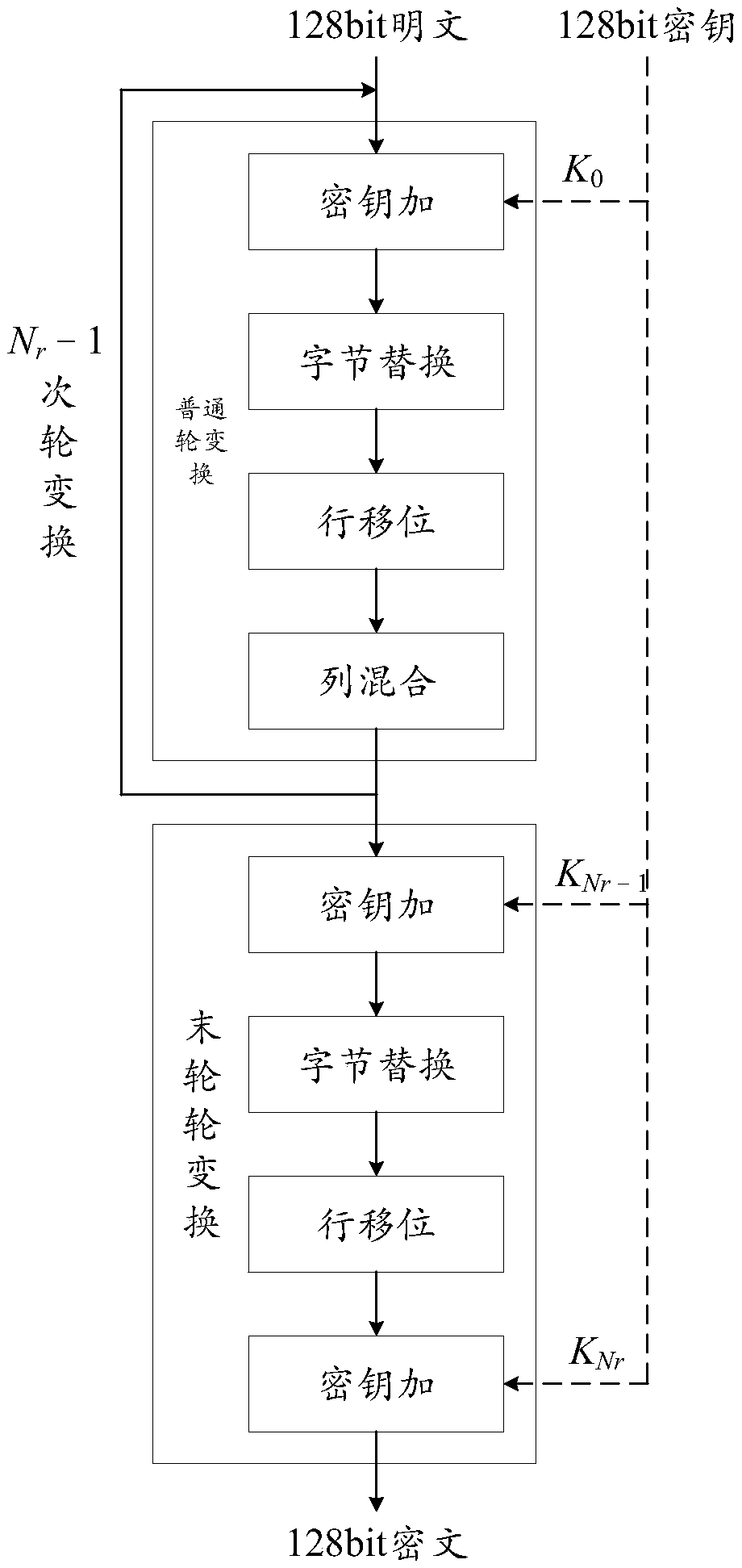
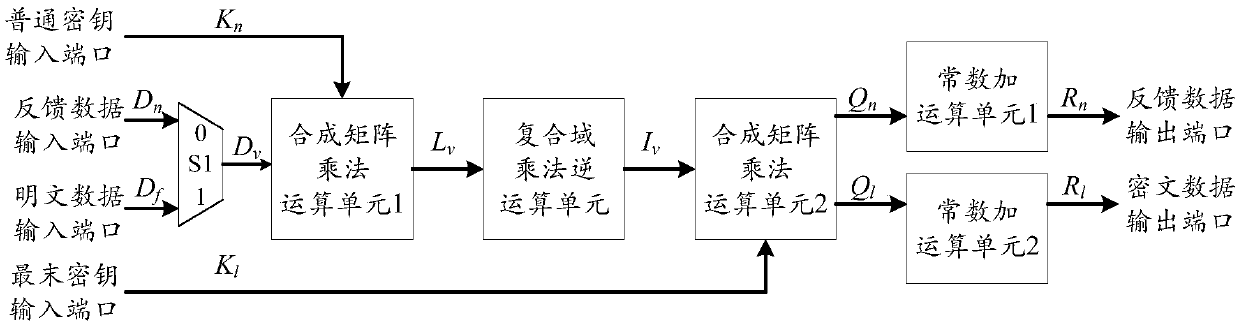
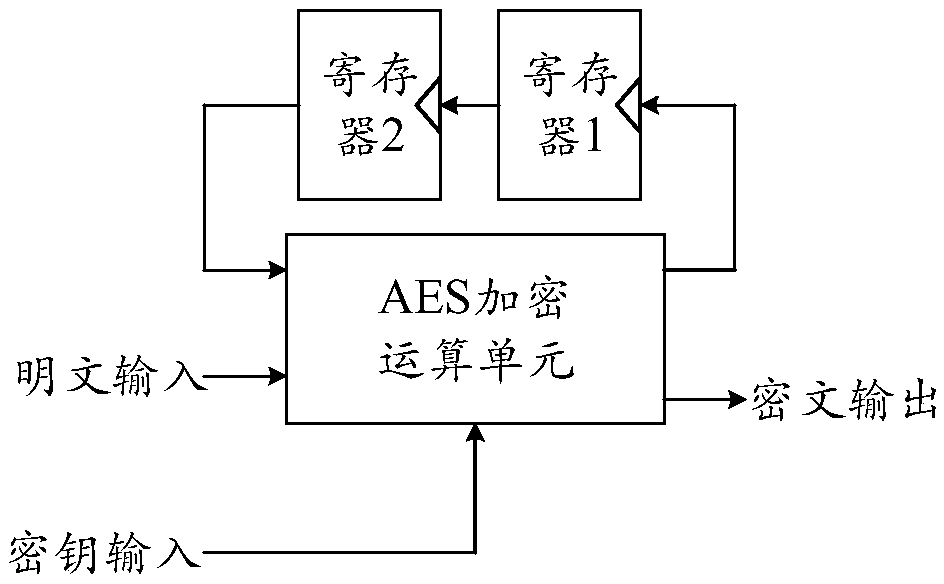
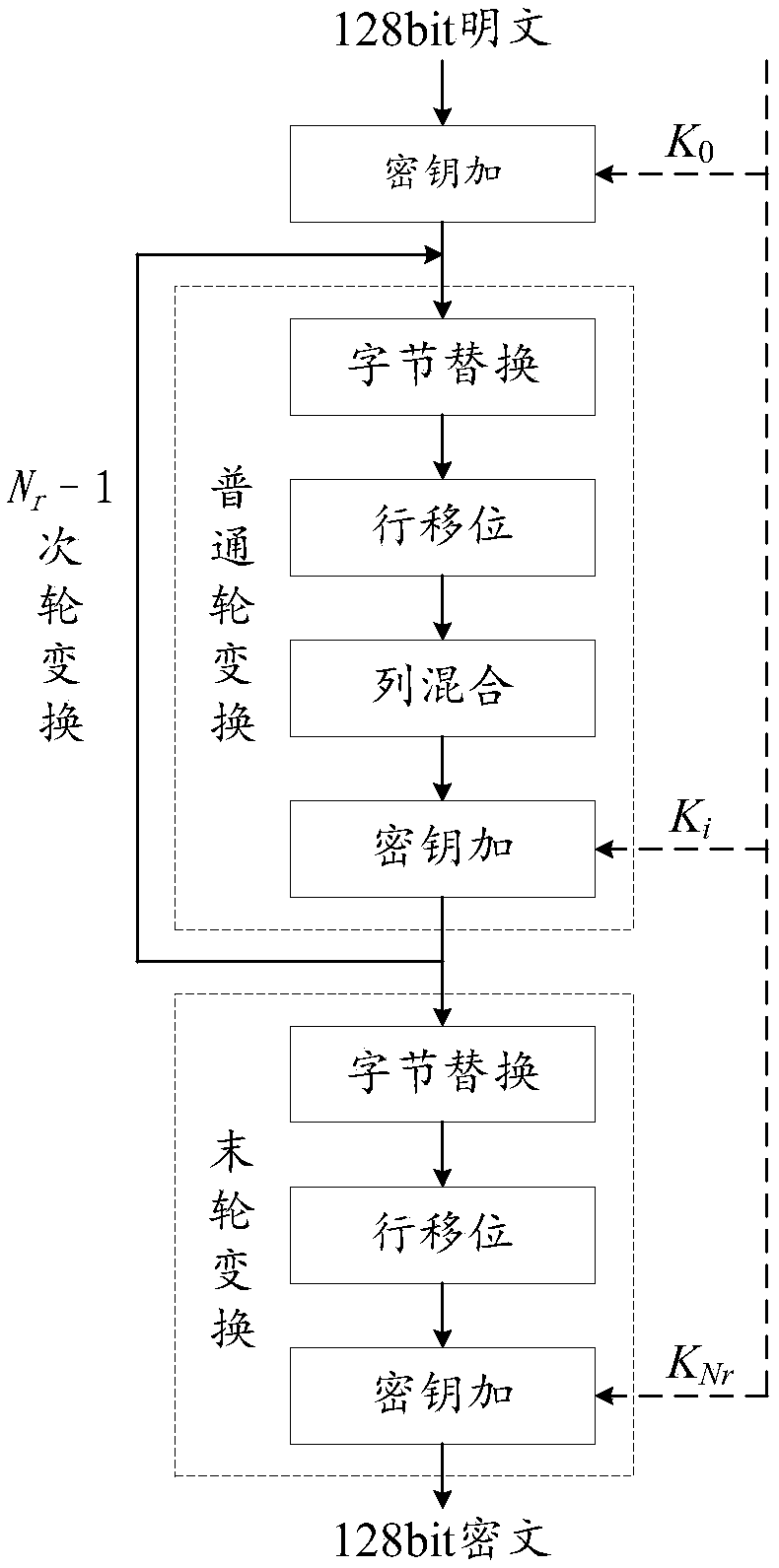
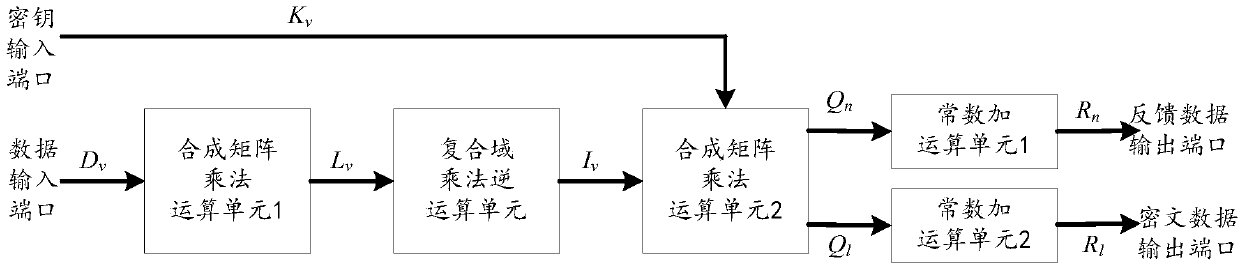
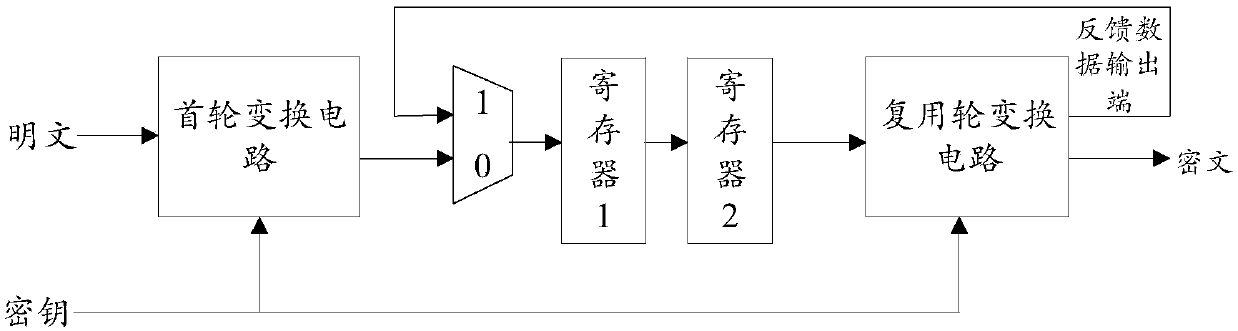
Patents
Literature
85results about How to "Shorten the critical path" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
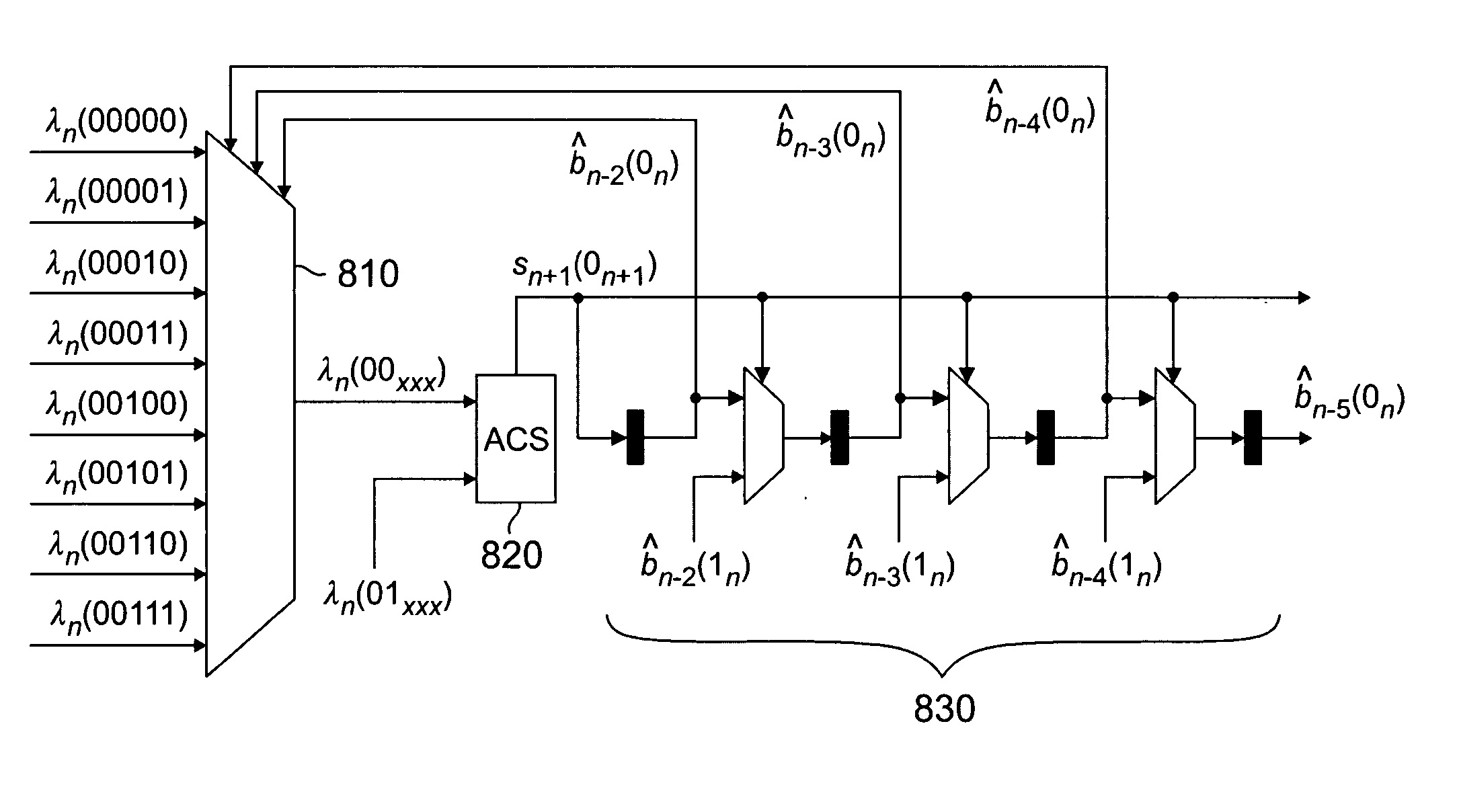
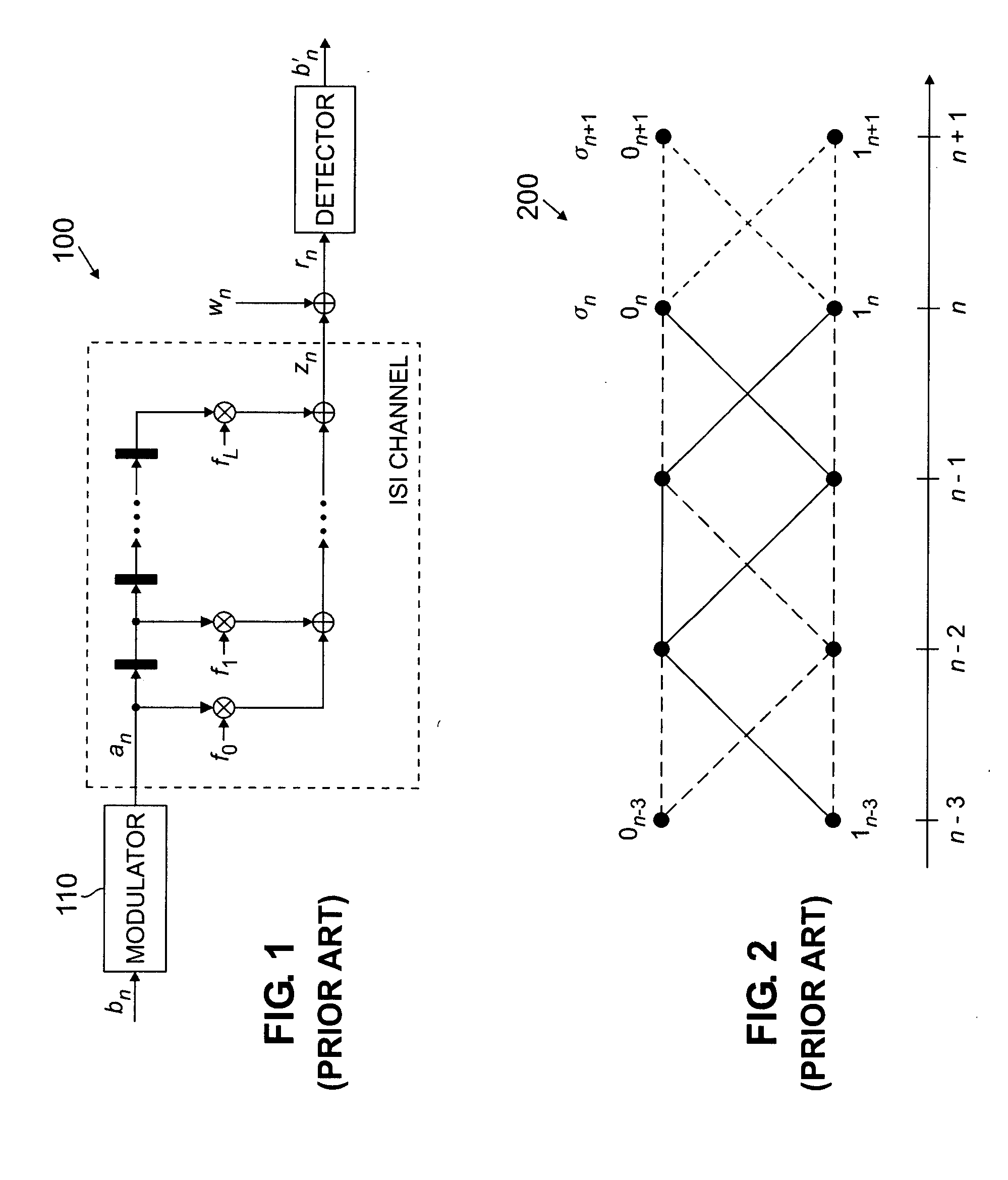
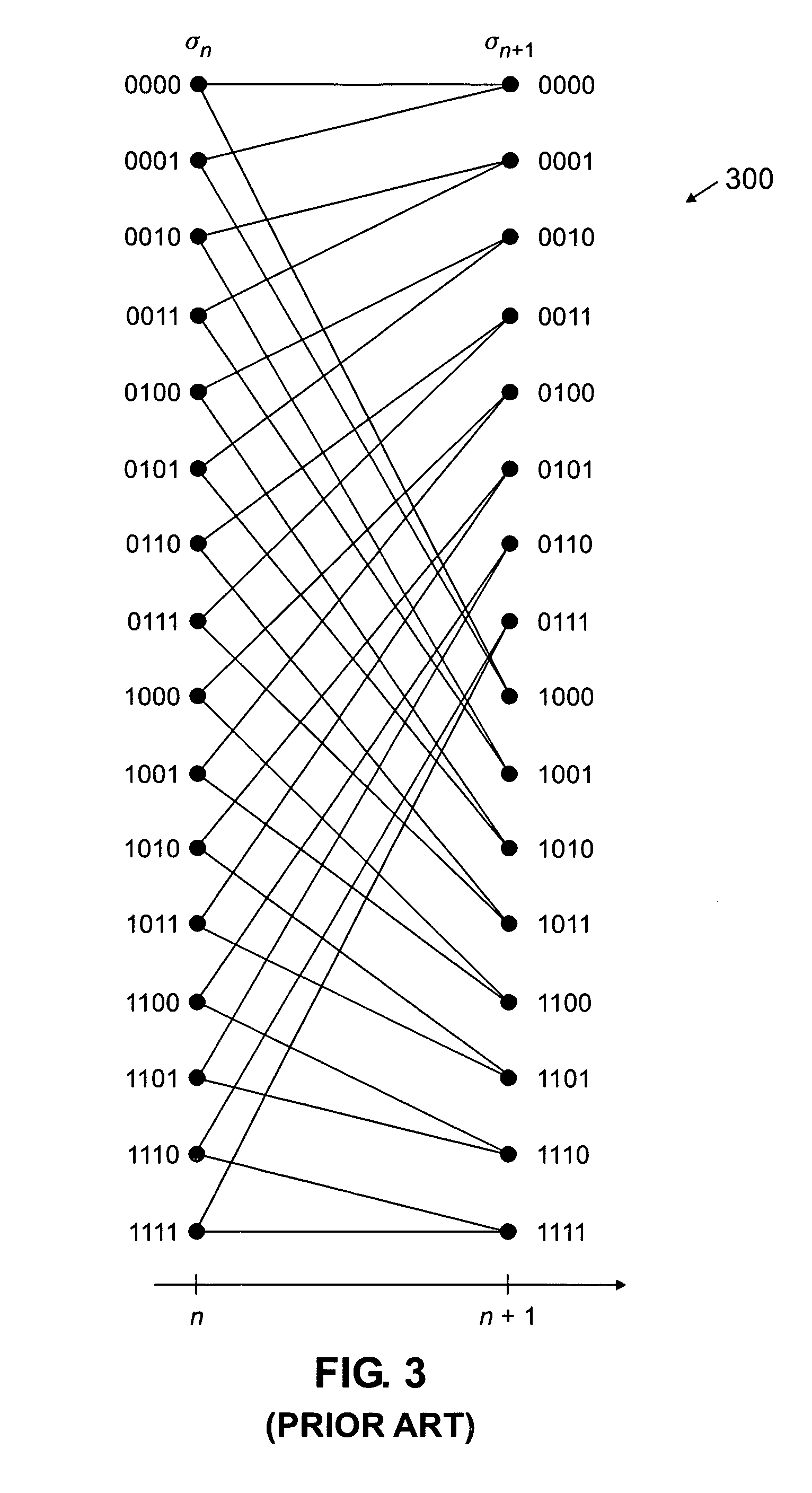
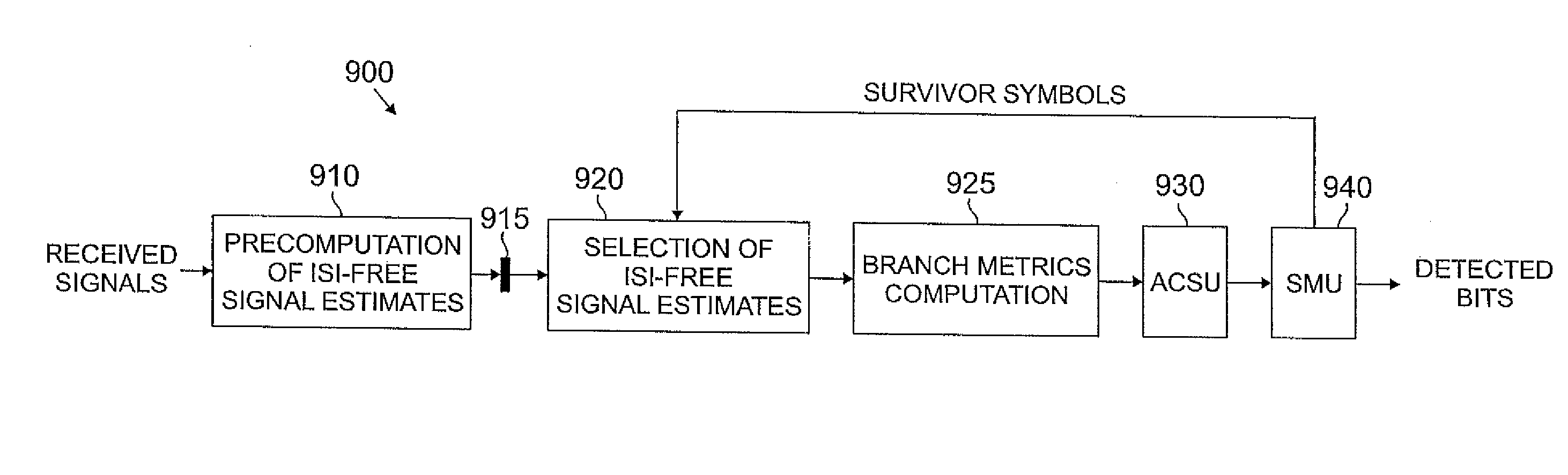
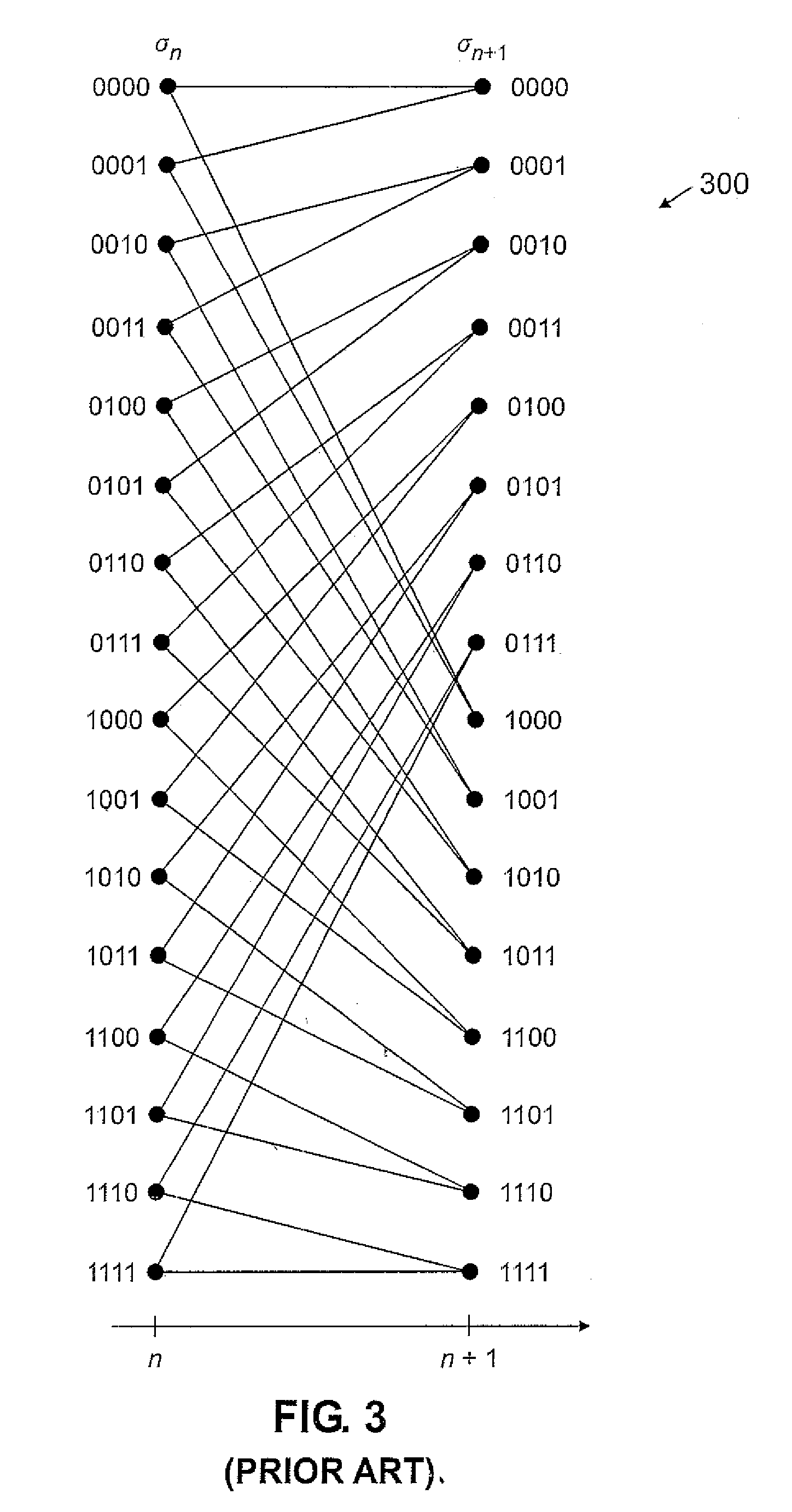
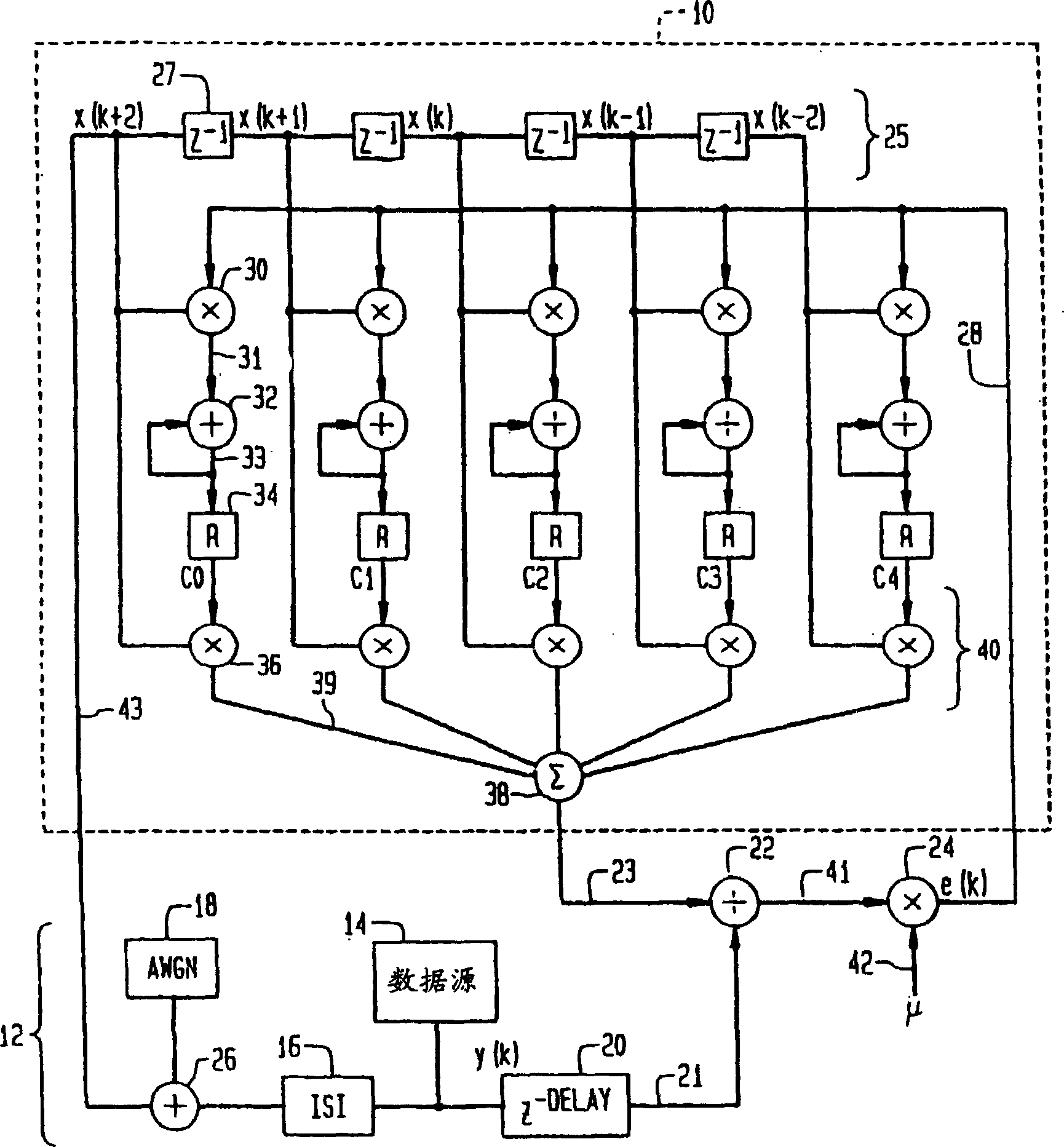
Method and apparatus for reduced-state Viterbi detection in a read channel of a magnetic recording system
InactiveUS20050264906A1Large data-rateShorten the critical pathOther decoding techniquesRecord information storageIntersymbol interferenceBranch Metrics
A method and apparatus are disclosed for improving the maximum data rate of reduced-state Viterbi detectors with local feedback in magnetic recording systems. A read channel signal is processed in a magnetic recording device by precomputing branch metrics, intersymbol interference estimates or intersymbol interference-free signal estimates for speculative sequences of one or more channel symbols; selecting one of the precomputed values based on at least one decision from at least one corresponding state; and selecting a path having a best path metric for a given state.
Owner:AGERE SYST LLC
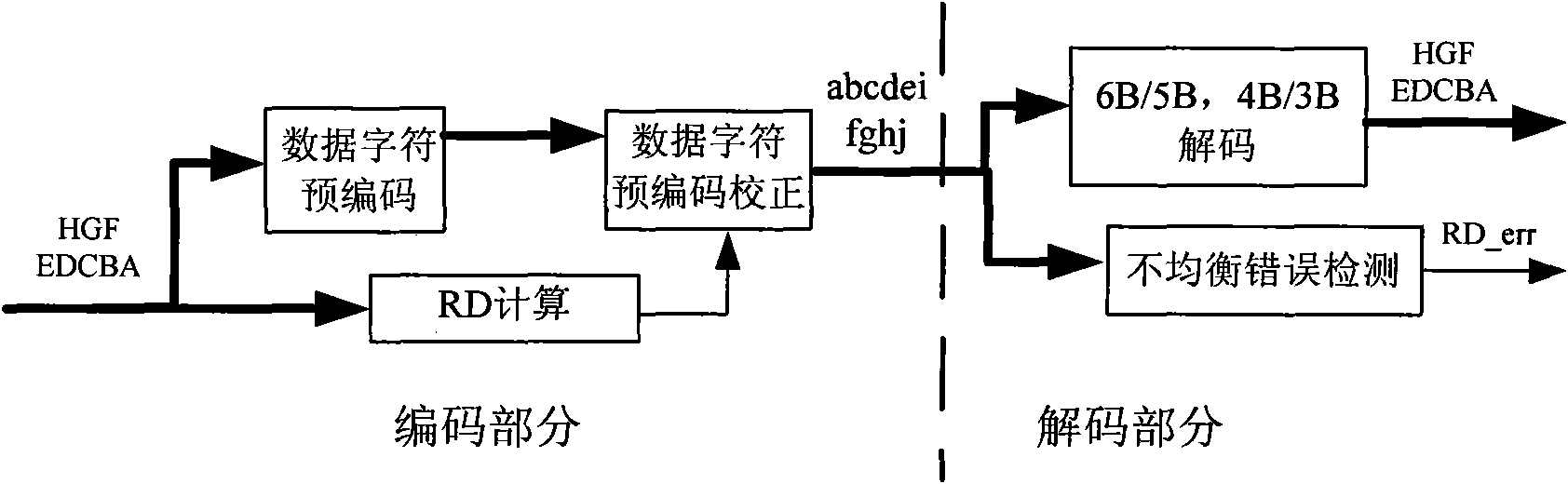
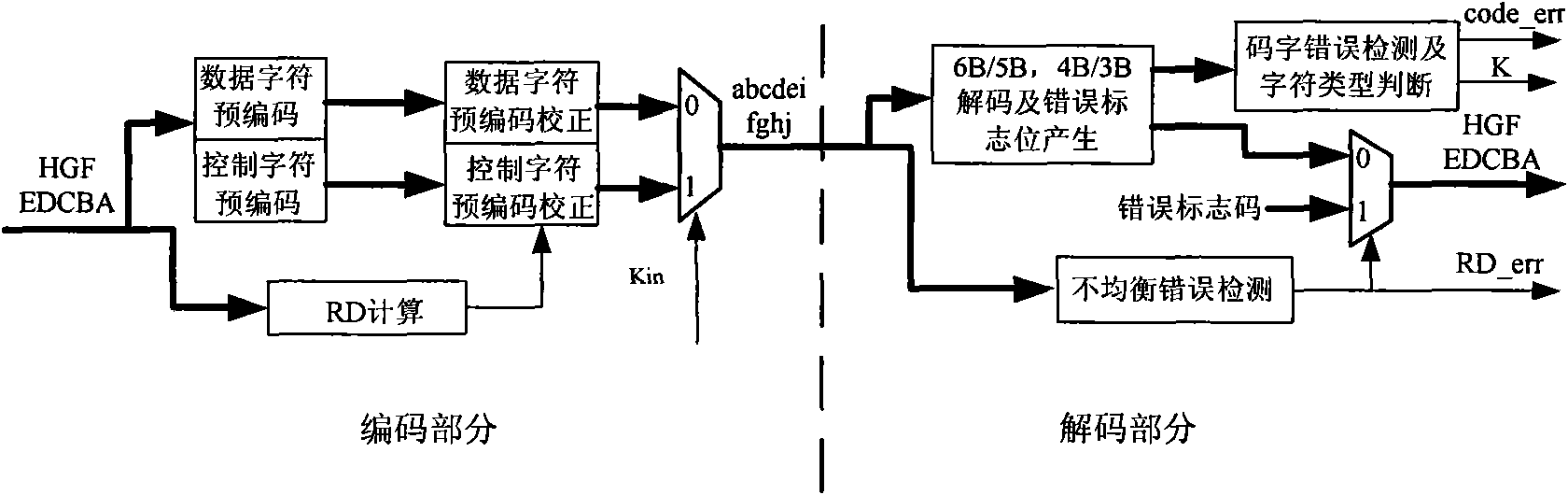
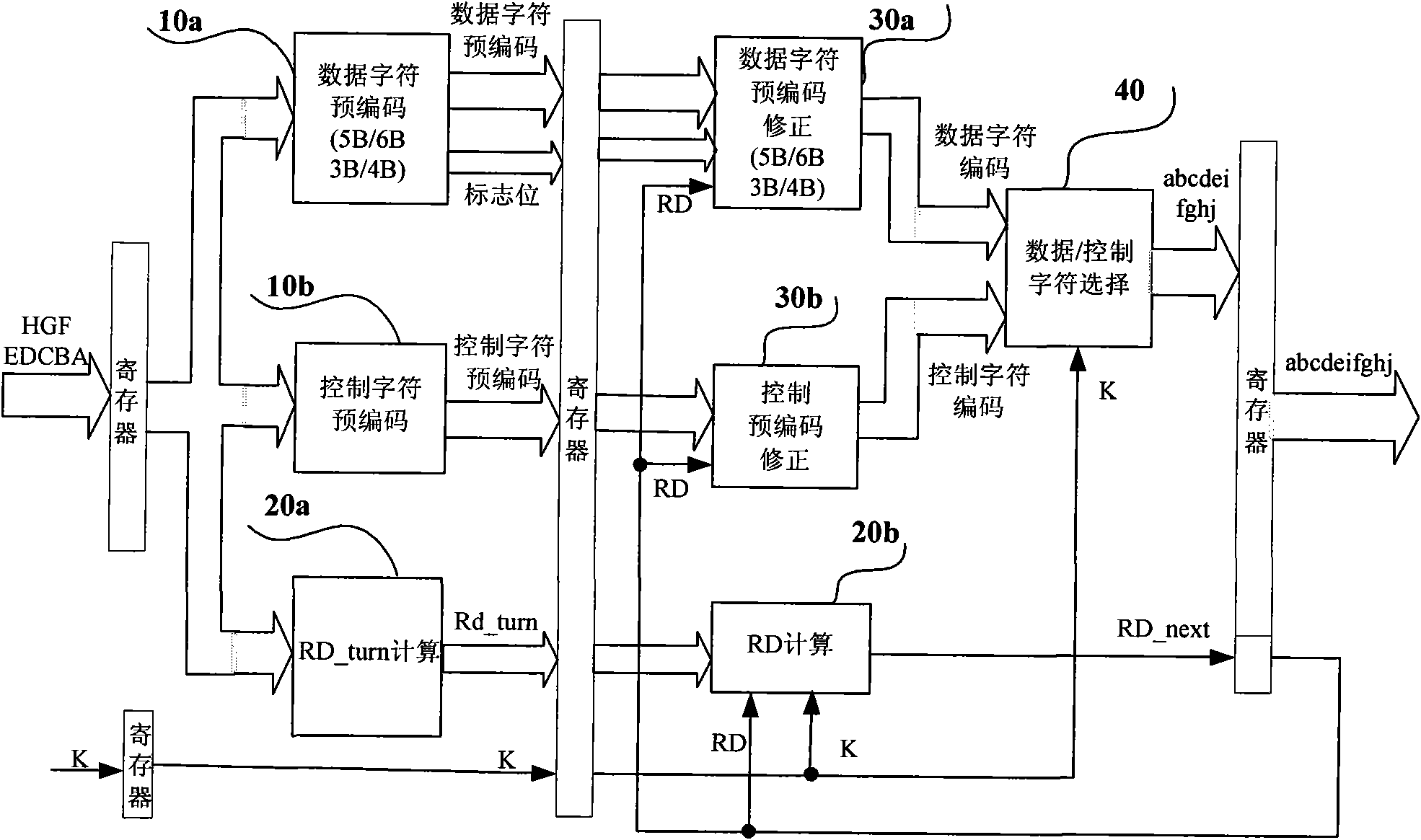
High-speed 8B/10B coder, decoder and processing method thereof for error input
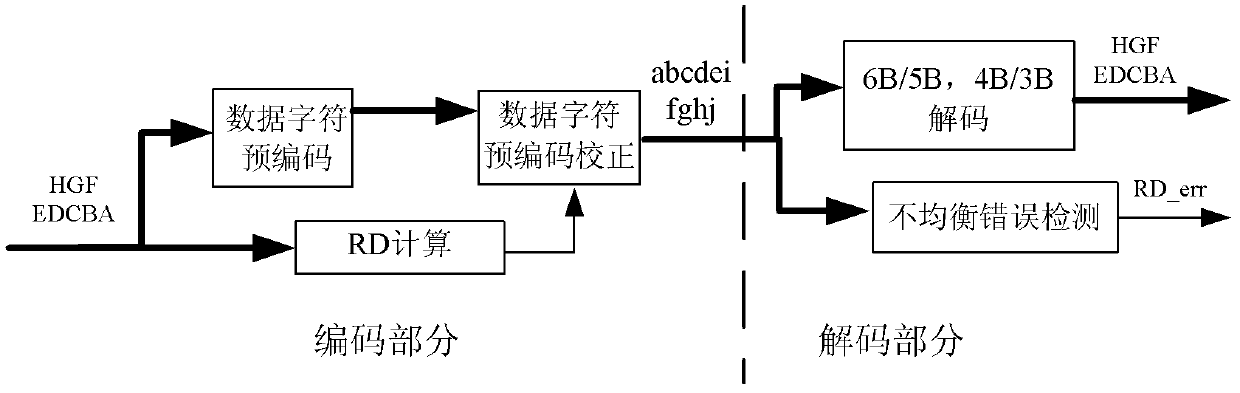
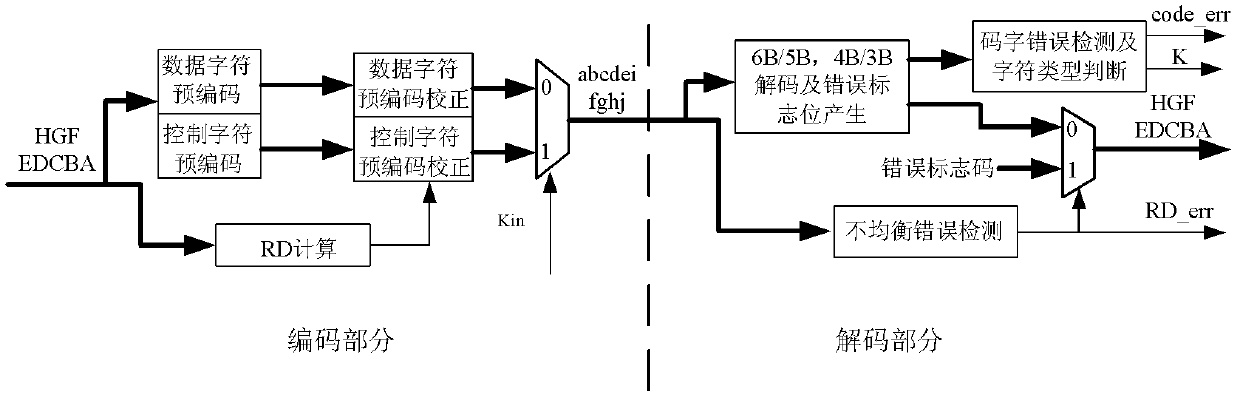
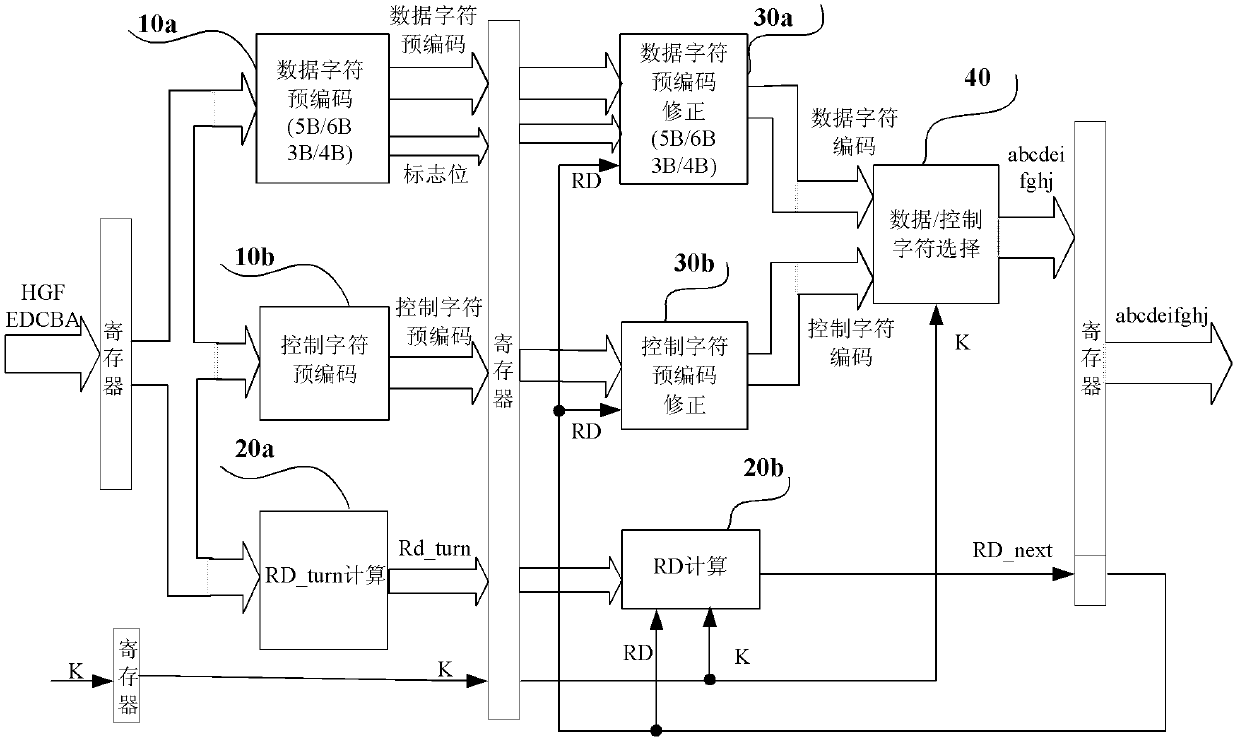
InactiveCN101674089AHigh speedShorten the critical pathIndividual digits conversionPrecodingCritical path method
The invention provides a high-speed 8B / 10B coder, a decoder and a processing method thereof for error input. The coder comprises a data character precoding module, a RD calculating module and a data character precoding correction module, and the coder adopts a pipeline structure and a parallel processing method; the data character precoding module, the data character precoding correction module and the RD calculating module are respectively precoded and then post collected; the data character precoding module precodes input data in first-stage flow water, and calculates whether the current input code word can cause RD to turn by a RD_turn module; the RD calculating module calculates a RD value passing through the code word in second-stage flow water, and calculates the obtained RD value by using the former clock period to correct the precoded result of the current code word. The invention respectively adopts the pipeline structure and the parallel processing method when being applied in a high-speed serial interface, thus simplifying the circuit design, shortening the key path and improving speed.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
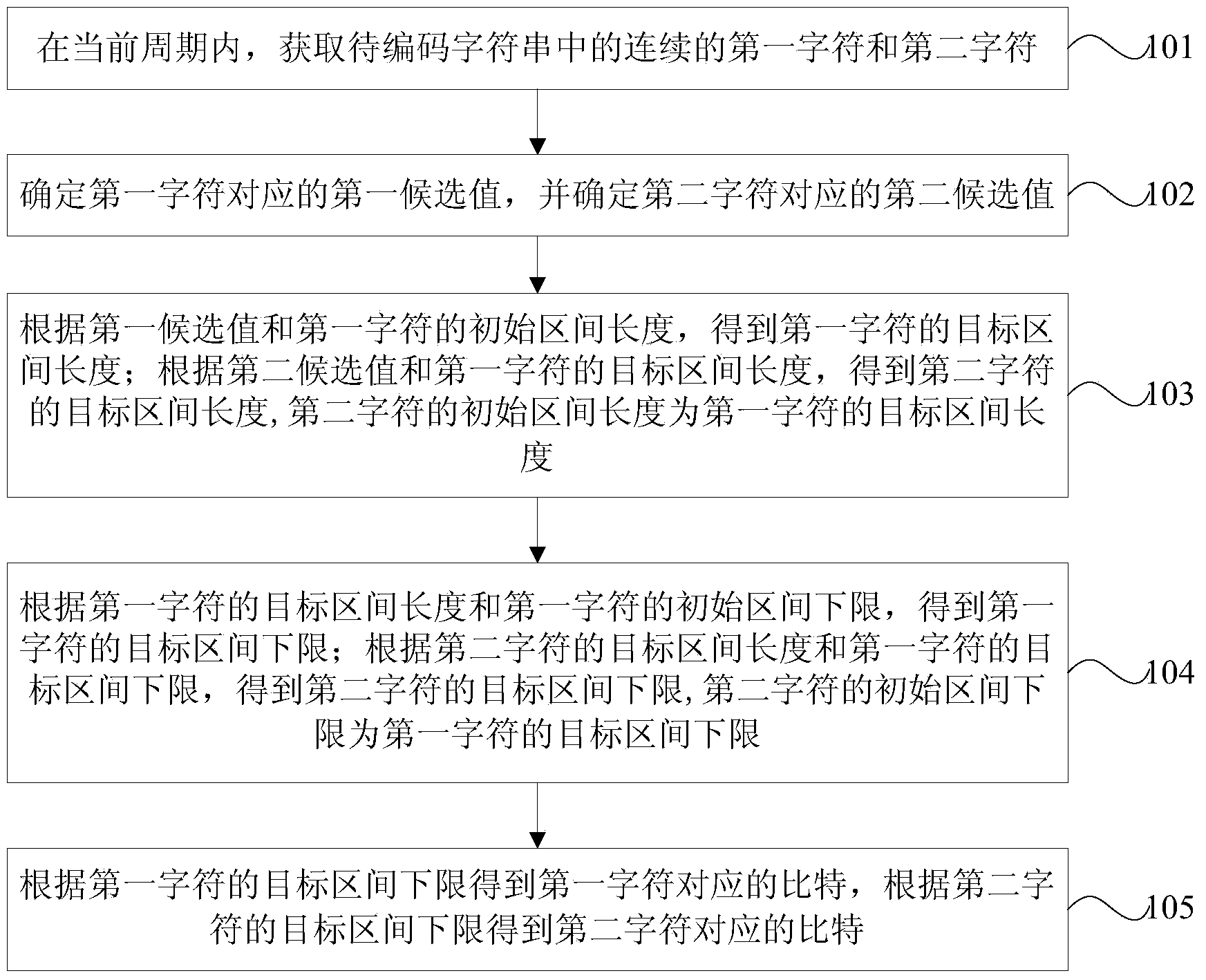
Video coding method and device
ActiveCN103974066AShorten the critical pathImprove data throughputDigital video signal modificationLower limitVideo encoding
The embodiment of the invention provides a video coding method and device. The method comprises the steps that in a current cycle, a first character and a second character which are consecutive in a character string to be coded are obtained; first candidate values corresponding to the first character are determined, and second candidate values corresponding to the second character are determined; the length of a target interval of the first character is obtained according to the first candidate values and the length of an initial interval of the first character; the length of a target interval of the second character is obtained according to the second candidate values and the length of the target interval of the first character; the lower limit of the target interval of the first character is obtained according to the length of the target interval of the first character and the lower limit of the initial interval of the first character; the lower limit of the target interval of the second character is obtained according to the length of the target interval of the second character and the lower limit of the target interval of the first character; a bit corresponding to the first character is obtained according to the lower limit of the target interval of the first character, and a bit corresponding to the second character is obtained according the lower limit of the target interval of the second character.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
Nuclear power plant containment shell pressure test strength monitoring system and monitoring method
ActiveCN107421586AReal-time measurementReduce stayMeasurement devicesNuclear engineeringData reliability
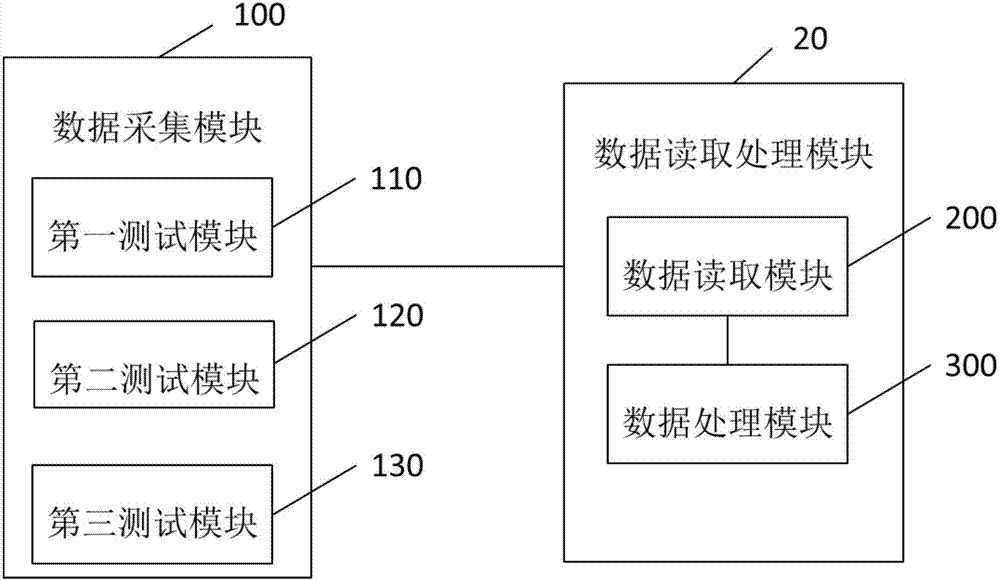
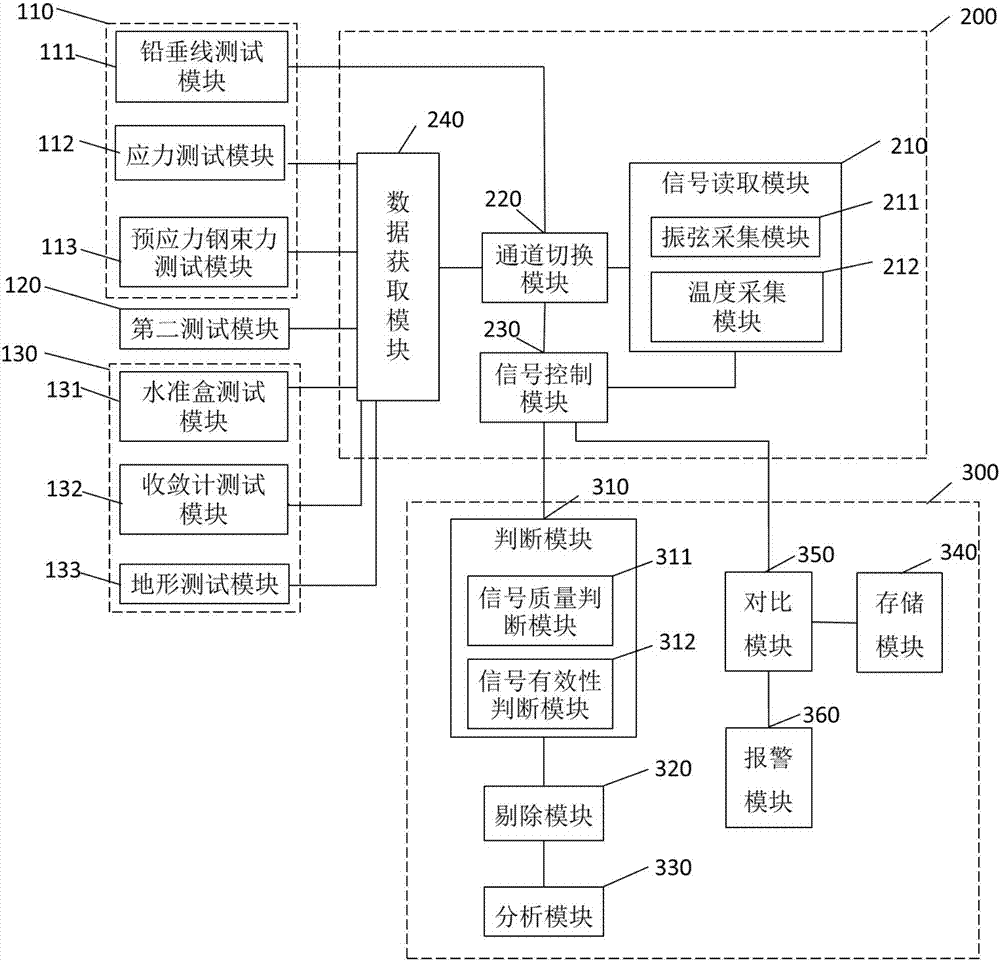
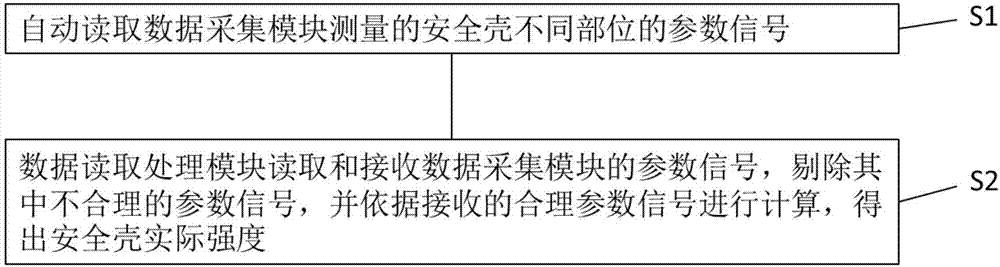
The invention provides a nuclear power plant containment shell pressure test strength monitoring system which includes data acquisition modules and a data reading and processing module. The data acquisition modules are distributed in different parts of a containment shell and used for acquiring parameter signals of different parts of the containment shell, wherein the parameter signals include deformation parameters, stress parameters, temperature parameters and settlement parameters. The data reading and processing module is connected with the data acquisition modules, and is used for reading and receiving the parameter signals from the data acquisition modules, eliminating unreasonable parameter signals, and performing calculation according to the reasonable parameter signals to get containment shell strength analysis data. The invention further provides a nuclear power plant containment shell pressure test strength monitoring method implemented using the nuclear power plant containment shell pressure test strength monitoring system. According to the technical scheme, through optimization of the data reading and analytical processing method of the existing nuclear power plant containment shell pressure test strength monitoring system, the problem that there is a need to read data manually and the data reliability is poor in the prior art is solved.
Owner:中广核工程有限公司 +1
Method and device for realizing finite domain multiplication based on serial and parallel combination
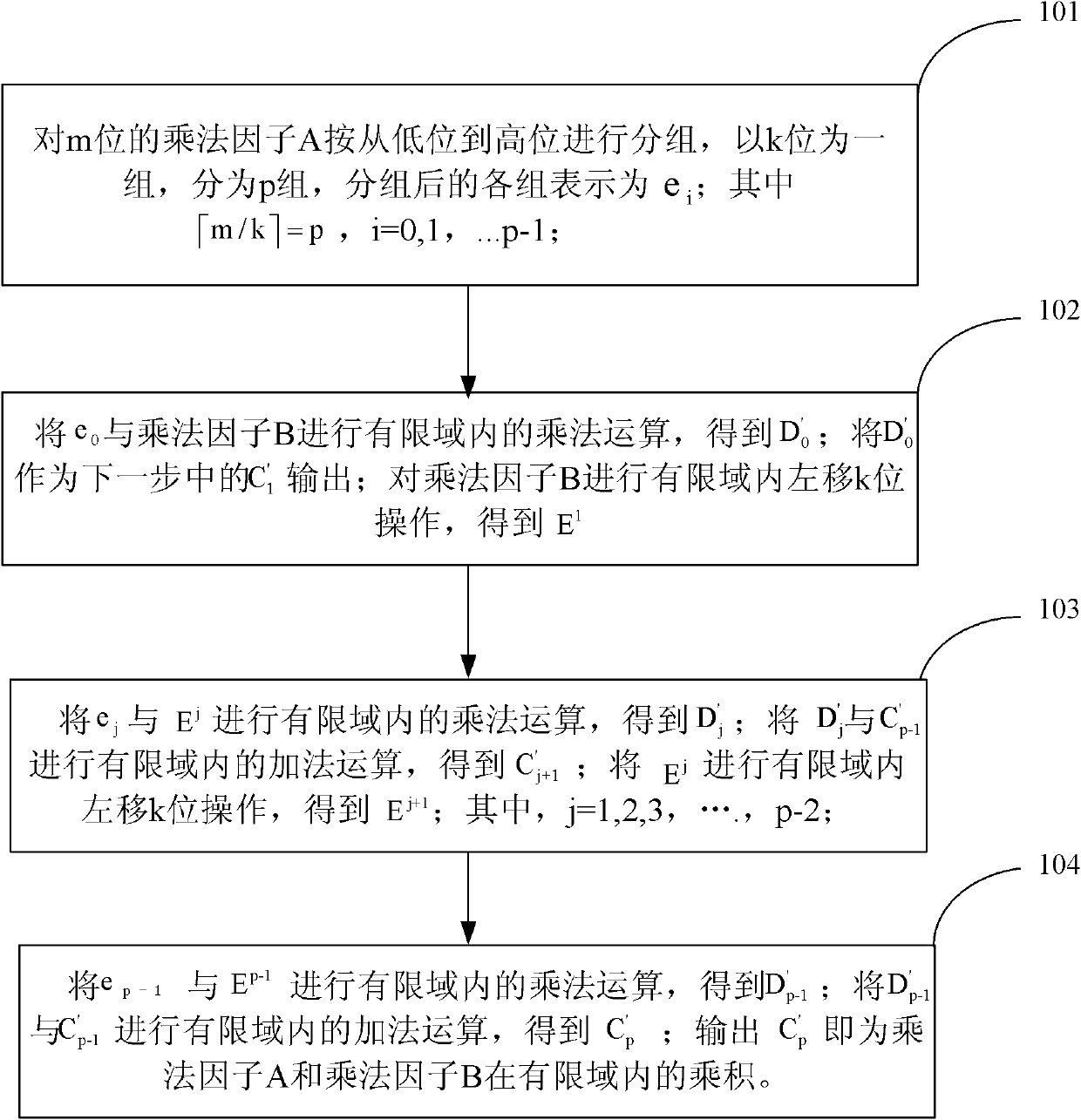
InactiveCN102184088AShorten the critical pathImprove efficiencyComputations using residue arithmeticTheoretical computer scienceLeft shifting
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method and apparatus for reduced-state viterbi detection in a read channel of a magnetic recording system
InactiveUS20070189424A1Large data-rateShorten the critical pathMultiple-port networksDelay line applicationsViterbi detectorData rate
A method and apparatus are disclosed for improving the maximum data rate of reduced-state Viterbi detectors with local feedback in magnetic recording systems. A read channel signal is processed in a magnetic recording device by precomputing branch metrics, intersymbol interference estimates or intersymbol interference-free signal estimates for speculative sequences of one or more channel symbols; selecting one of the precomputed values based on at least one decision from at least one corresponding state; and selecting a path having a best path metric for a given state.
Owner:BROADCOM INT PTE LTD
Memory system based on virtual interface
InactiveCN1761257AShorten the critical pathIncrease profitTransmissionMemory systemsZero-copyNetwork module
The invention includes M pieces of node machines for storage service, one node machine of metadata and N pieces of client node machines, which are connected to each other through VIA communication network. Running on the node machines for storage service, the modules include system initiation module, module for monitoring request, and module for processing request. Running on the node machine of metadata, the modules include metadata initiation module, monitoring module for request from metadata, and state detection module. Running on the client node machine, the modules include one or more device drive modules of network module based on VIA. The invention realizes zero copy of data transmission, shortened path of network stored data, as well as solves main issues of network storage: network bandwidth, storage access speed and interoperability.
Owner:HUAZHONG UNIV OF SCI & TECH
Ciphering unit being suitable for compacting instruction set processor
ActiveCN101304312AImprove scalabilityLow costPublic key for secure communicationMachine execution arrangementsComputer hardwareHash function
The invention belongs to the design technical field of integrated circuits, in particular to an encryption unit which is suitable for RISC processors, comprising a RSA encryption unit, an SHA encryption unit and a RSA / SHA reusable encryption unit. The encryption function units can be integrated into the RISC processor to accelerate the calculation of public-key algorithm and hash functions and obviously lower the cost of hardware; particularly the RSA / SHA reusable encryption unit fulfills the complex cryptography calculation through hardware, and adopts the software for finishing and configuring upper-layer RSA algorithm so as to realize the scalability of data width. The RSA / SHA reusable encryption unit being used for dealing with the most complex calculation of the cryptographic algorithm greatly accelerates the execution efficiency of the cryptographic algorithm, brings no influence on the pipeline structure of the RISC processor and increases no complexity of the hardware, thus having great compatibility with the RISC structure, and having better application prospect in information security field.
Owner:FUDAN UNIV
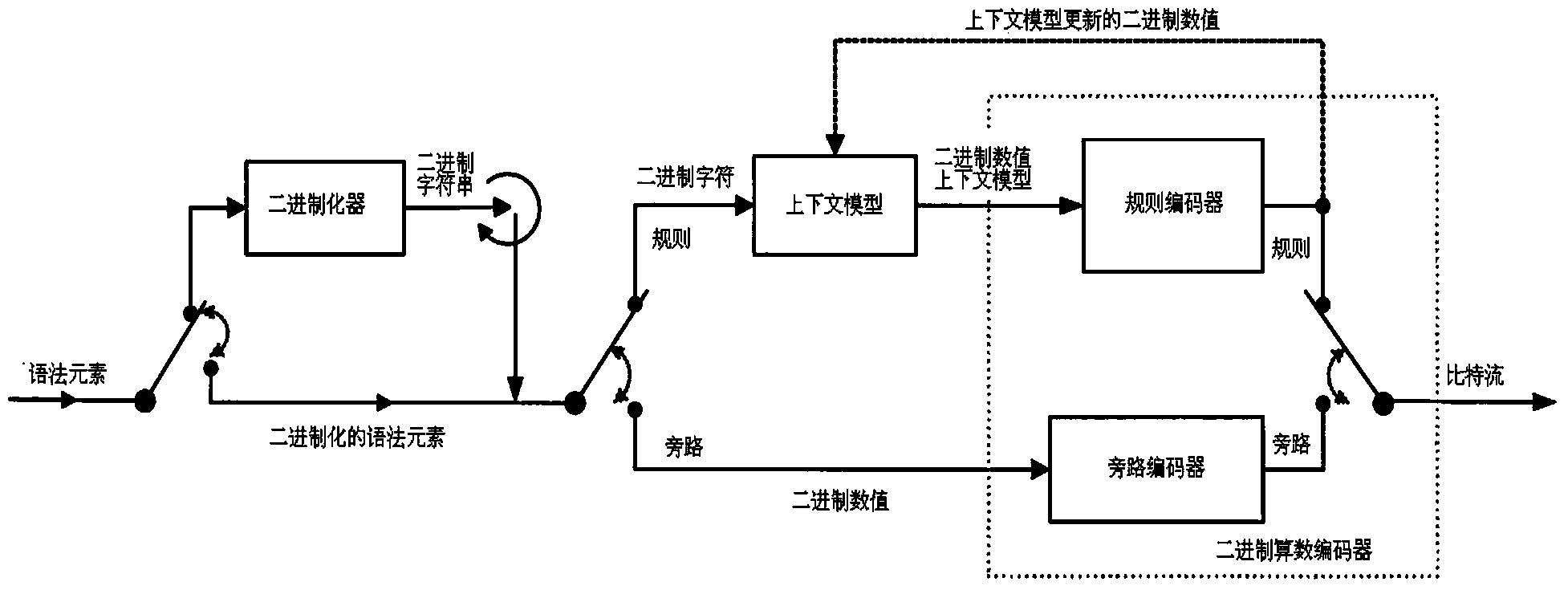
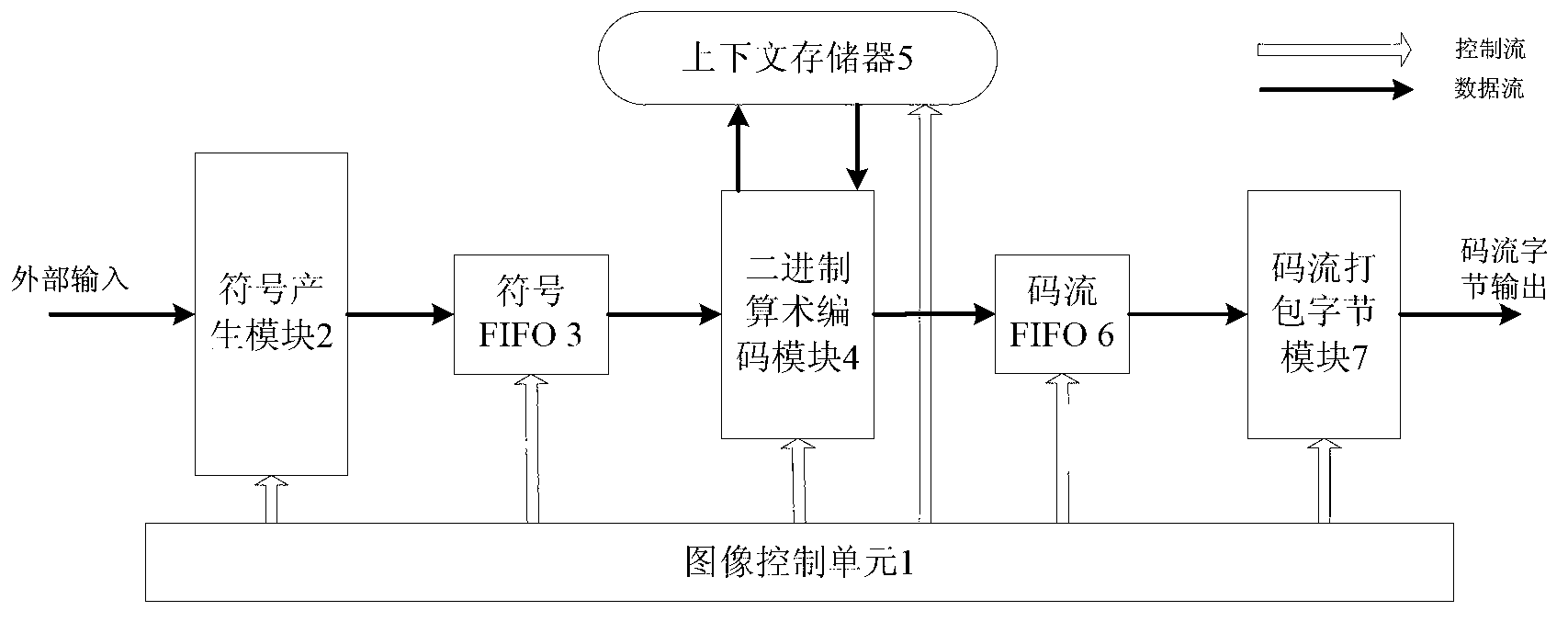
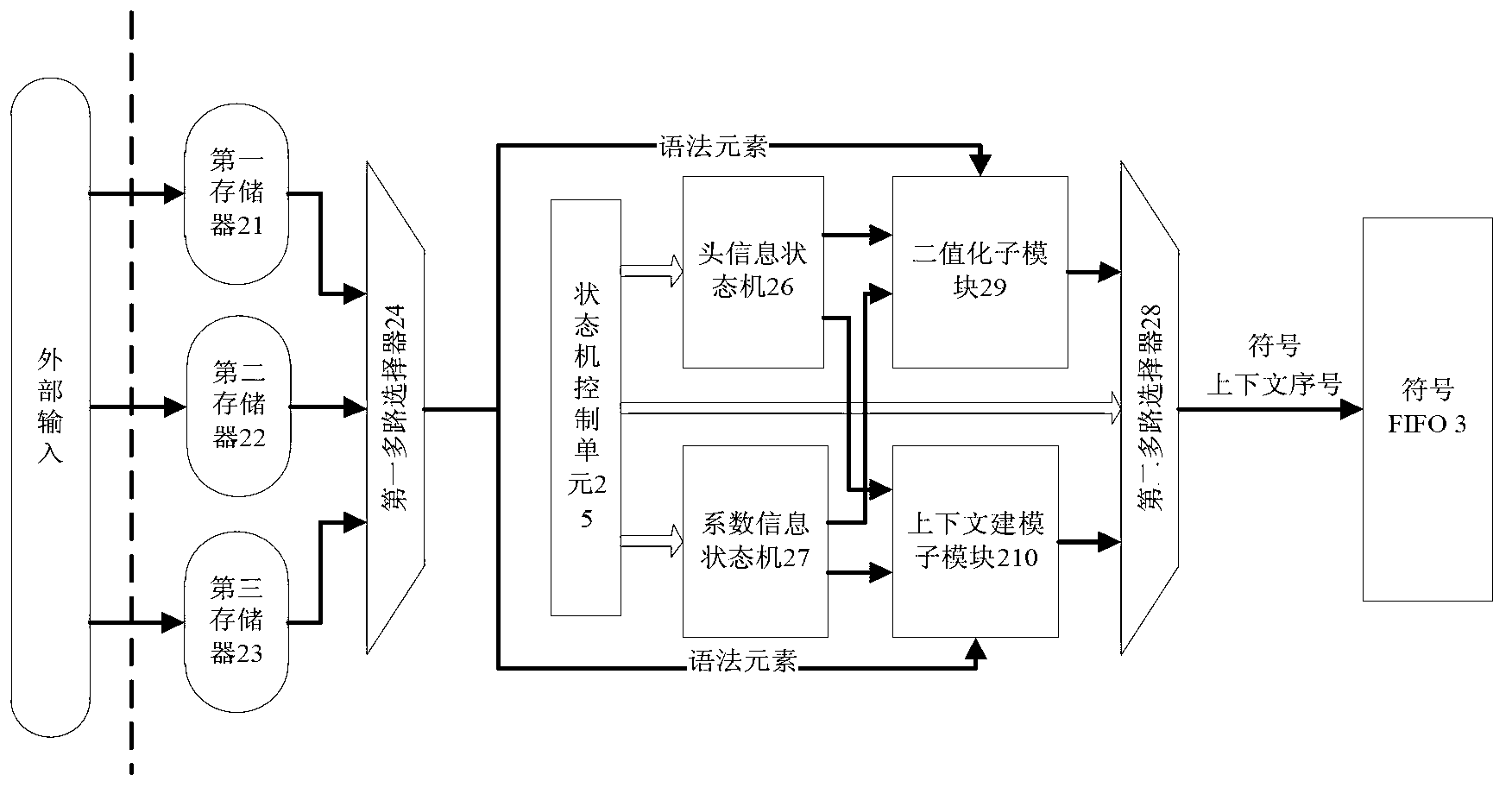
Image compression and entropy coder based on CABAC (Context-Based Adaptive Binary Arithmetic Coding)
InactiveCN102801974AAvoid stagnationImprove throughputTelevision systemsDigital video signal modificationStreaming dataCode module
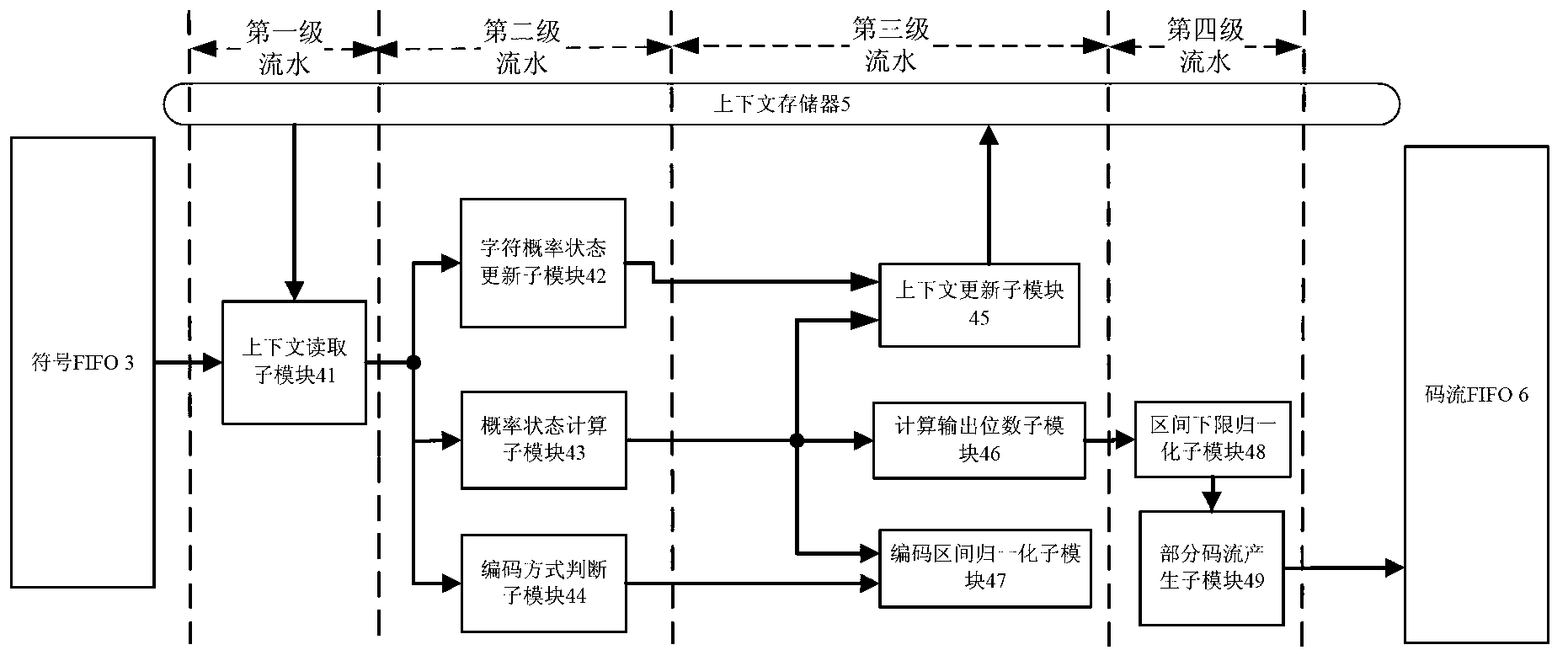
The invention discloses an image compression and entropy coder based on CABAC (Context-Based Adaptive Binary Arithmetic Coding), and the coder is mainly used for solving the problems that the coding efficiency is not high, and data overflows when a code stream is rapidly packaged in the prior art. The image compression and entropy coder comprises an image control unit (1), a symbol generation module (2), symbol FIFO (First In, First Out) (3), a binary arithmetic coding module (4), a context memory (5), code stream FIFO (6) and a code stream packaging byte module (7), wherein the image control unit is used for controlling the resetting of each module and the generation of an enabling signal, the symbol generation module is used for reading data from the external and finishing binarization and context modeling, the symbol FIFO is used for storing a binary symbol and a context model, the context memory is used for storing context information, the binary arithmetic coding module is used for acquiring a middle code stream according to the binary symbol, the code stream FIFO is used for storing middle code stream data, and the code stream packaging byte module is used for generating a final code stream according to the middle code stream. The image compression and entropy coder has the advantages that the throughput is high, the circuit scale is small, a key path is short, a flow line is prevented from stagnating, and the data is avoided overflowing; and the image compression and entropy coder is used for realizing arithmetic entropy coding with high throughput.
Owner:XIDIAN UNIV
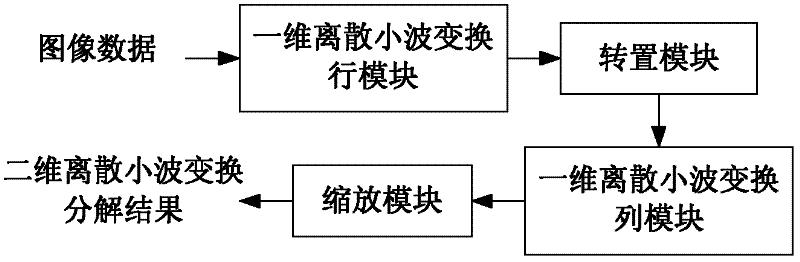
Hardware framework for two-dimensional discrete wavelet transformation
ActiveCN102572429AReduce the numberShorten the critical pathTelevision systemsDigital video signal modificationInternal memoryProduction line
The invention provides a hardware framework for two-dimensional discrete wavelet transformation, which comprises a one-dimensional discrete wavelet transformation row module, a transposition module, a one-dimensional discrete wavelet transformation column module and a zoom module which are respectively connected in serial, image data are connected with the input end of the one-dimensional discrete wavelet transformation row module, and the zoom module outputs two-dimensional discrete wavelet transformation decomposing results. The framework has the advantages of high performance and low storage, and is suitable for realization of discrete wavelet transformation in JPEG2000 static image coding standards. By adopting the folding technology and the production line technology, the hardware framework provided by the invention reduces the number of operation units, shortens a key path of a system, and improves system performances. The one-dimensional discrete wavelet transformation row module and the one-dimensional discrete wavelet transformation column module in the hardware framework are scheduled by adopting row-based data flow, so that required middle caches can be greatly reduced, and further the area of an internal memory and the hardware area of the two-dimensional discrete wavelet transformation framework are reduced.
Owner:SOUTHEAST UNIV
Construction method for steel plate concrete wall of primary loop cabin of high temperature gas cooled reactor
ActiveCN102605951AShorten the critical pathEnsure correct executionWallsBuilding material handlingSteel platesNuclear reactor
The invention relates to a construction method for a steel plate concrete wall of a primary loop cabin of a high temperature gas cooled reactor, which belongs to the technical field of reactor structures. The method includes: arranging inner bearing steel posts, outer bearing steel posts, bearing crossbeams and connecting beams according to design requirements, sequentially arranging shielding cooling water pipes, outer steel plates, inner steel plates and a plurality of transverse shearing nails to form a wall framework module, hoisting the module to the position of the primary loop cabin ofthe high temperature gas cooled reactor, concreting to form a lower-layer steel plate concrete wall module, hoisting an upper-layer module on the lower-layer steel plate concrete wall module, and cycling so to form the wall of the primary loop cabin of the high temperature gas cooled reactor. By the construction method, time of constructional critical paths can be shortened, cross workload on a construction site can be reduced, and work intensity on the construction site is relieved. Further, accurate execution of construction schedule can be guaranteed while construction quality is improved and construction period is shortened.
Owner:CHINERGY CO LTD
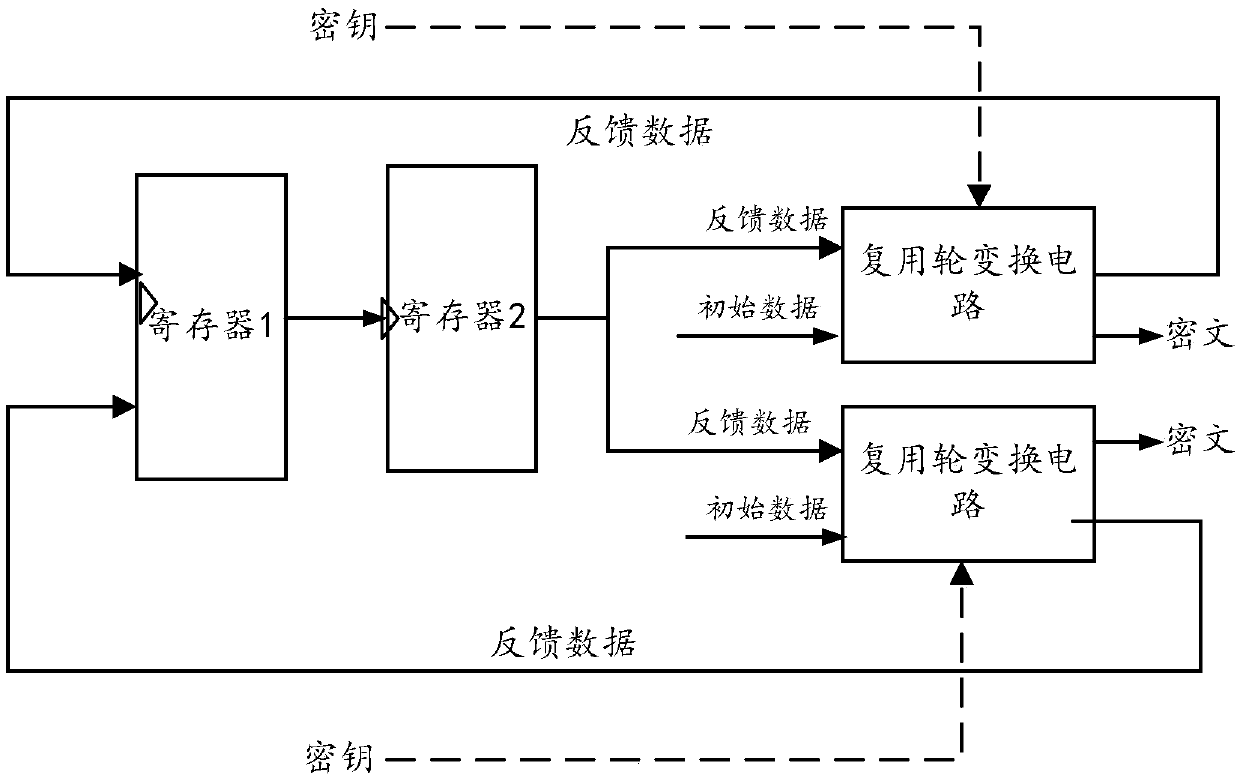
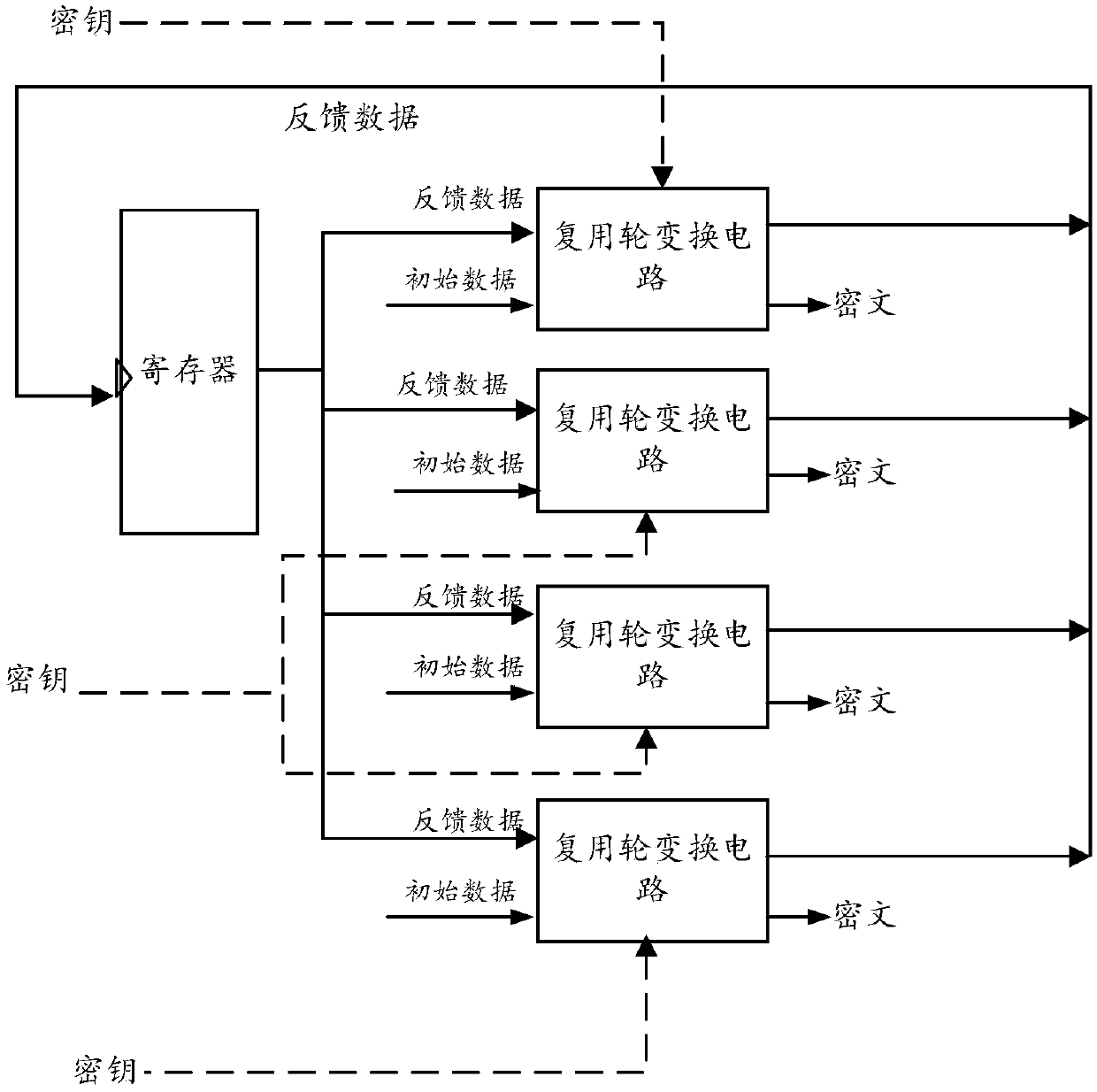
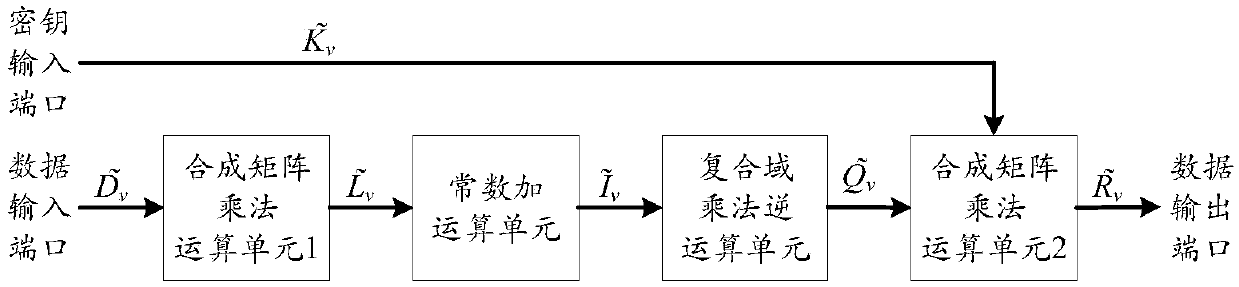
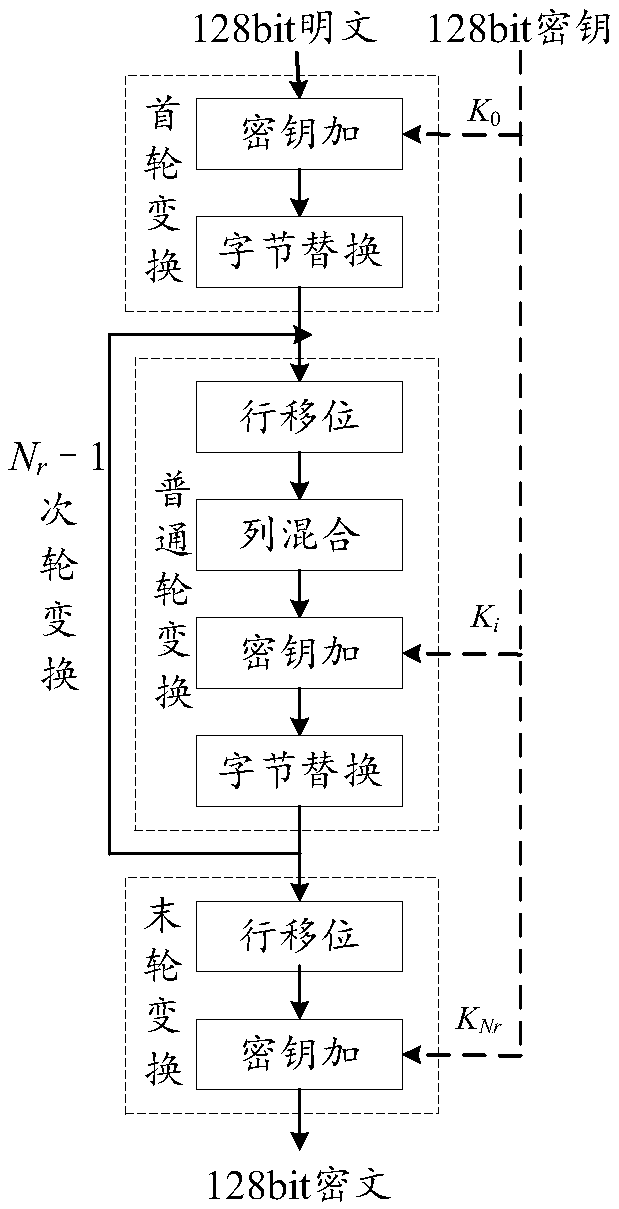
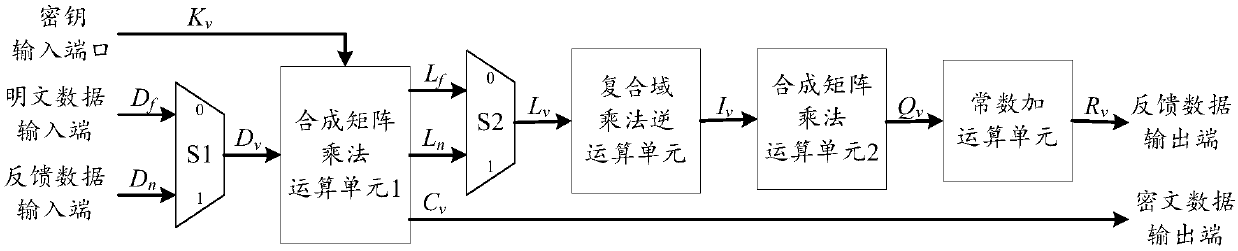
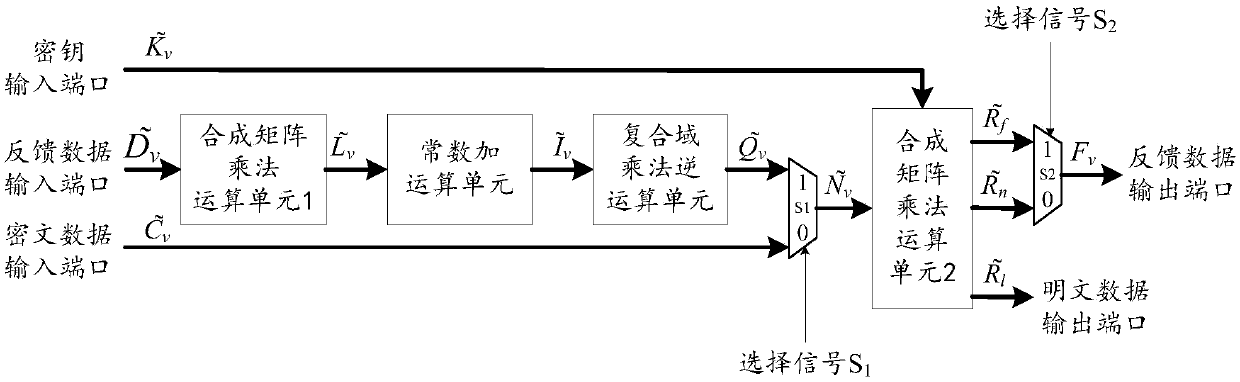
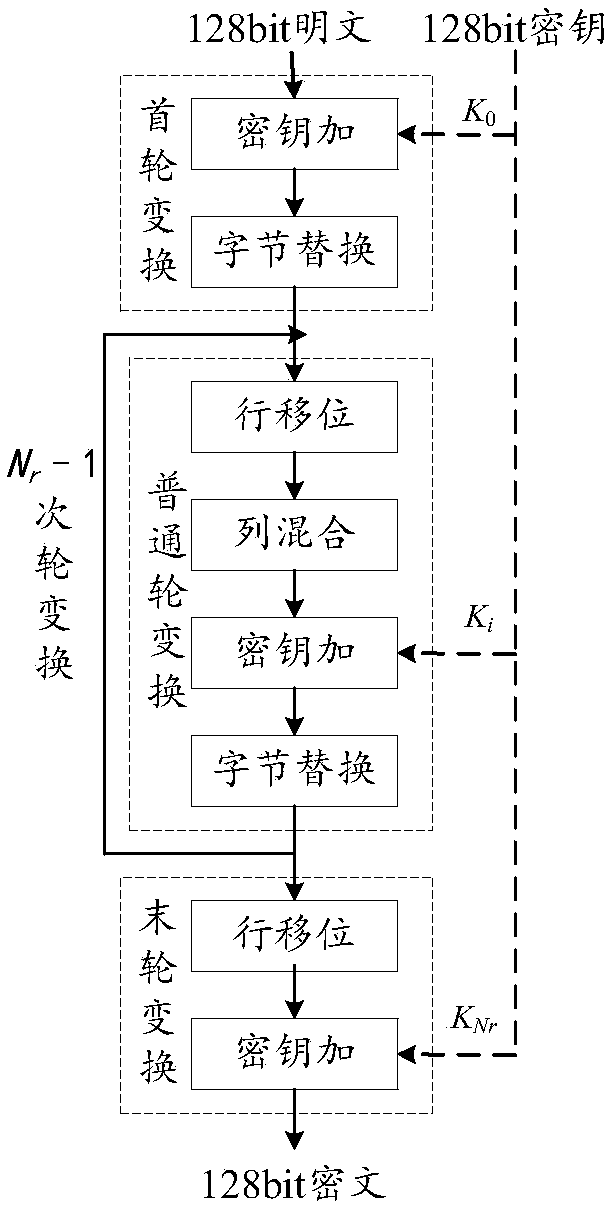
Multiplex wheel conversion circuit, AES encryption circuit and encryption method
ActiveCN109039583ARealize a small areaSave resourcesEncryption apparatus with shift registers/memoriesComputer hardwareMultiplexing
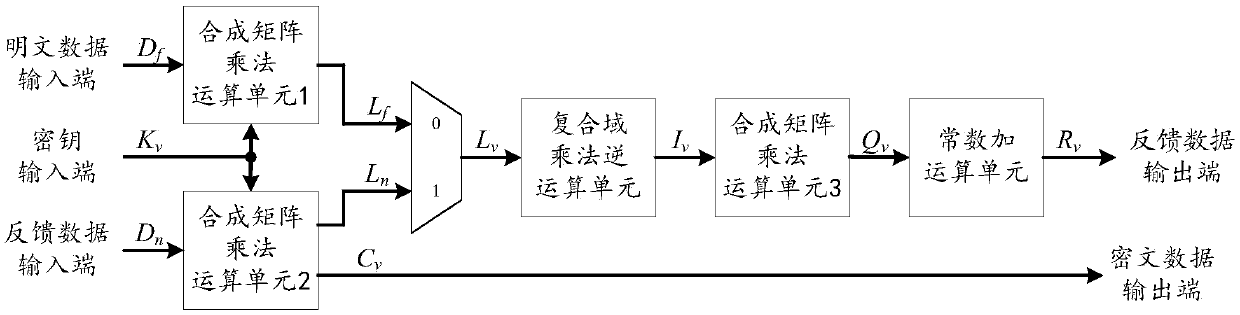
The invention is applicable to the field of encryption technology, provides a multiplex wheel conversion circuit, an AES encryption circuit and an encryption method. The AES encryption wheel transformation multiplexing circuit of the invention combines and synthesizes constant matrices, all the linear transformation operations in AES cryptographic algorithm are combined into two composite matrices, namely the composite matrix delta and the composite matrix lambda, so as to shorten the critical path of the AES encryption wheel conversion circuit, reduce the circuit realization area, and realizethe common wheel conversion and the last round conversion by multiplexing the composite matrix multiplication unit 1, the composite field multiplication inverse operation unit and the composite matrix multiplication operation unit 2, thereby saving a large amount of circuit resources.
Owner:ANHUI UNIVERSITY OF TECHNOLOGY AND SCIENCE
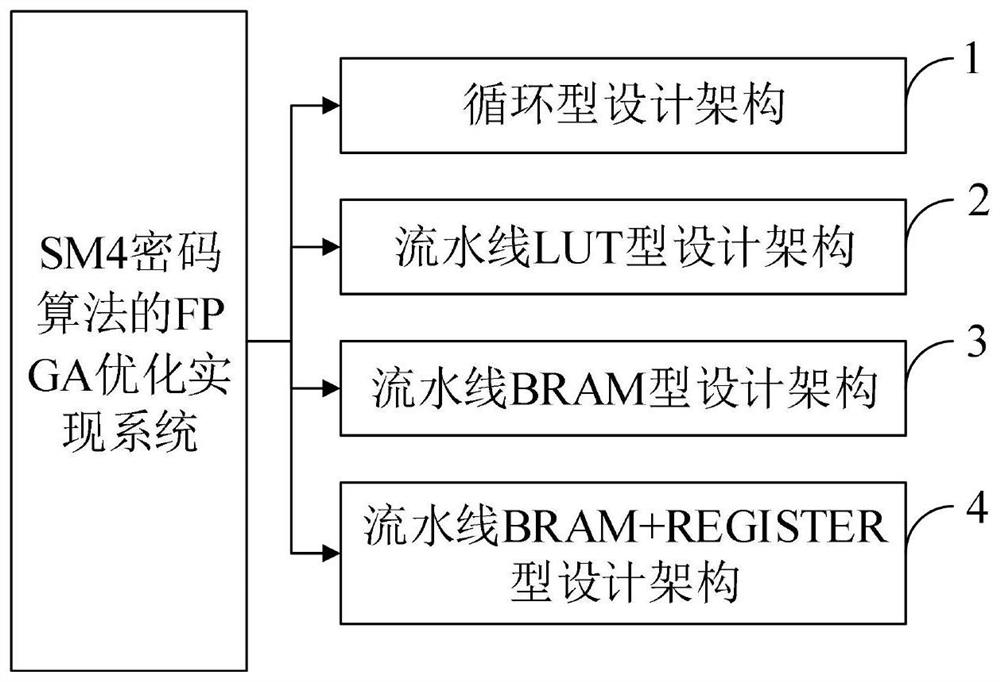
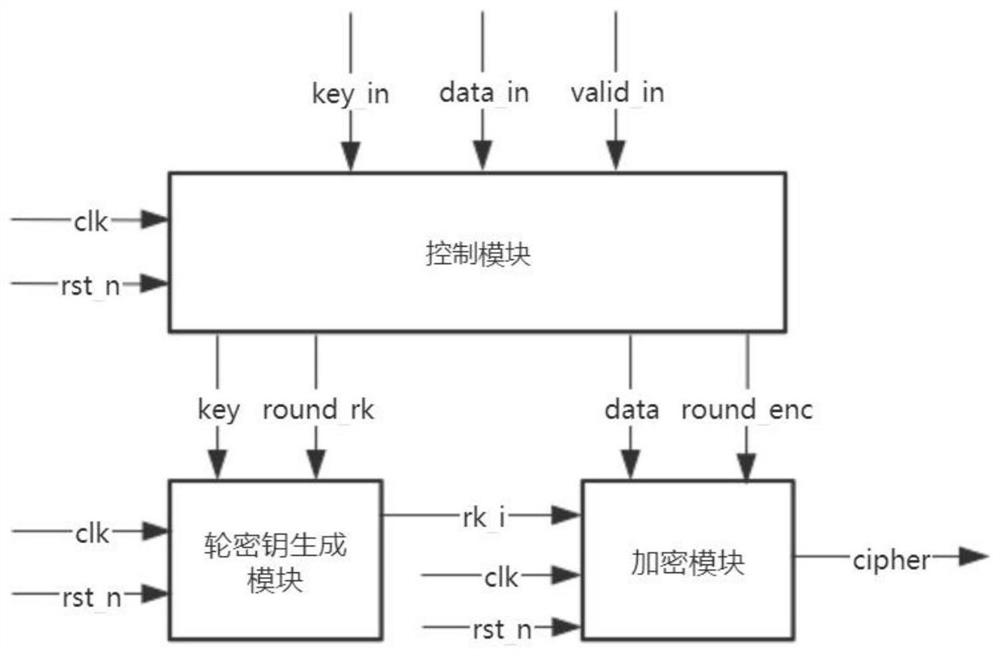
FPGA optimization implementation method and system for SM4 cryptographic algorithm and application
ActiveCN113078996ASave resourcesResist attackEncryption apparatus with shift registers/memoriesKey (cryptography)Parallel computing
The invention belongs to the technical field of cryptography, and discloses an FPGA optimization implementation method and system for an SM4 cryptographic algorithm and application, and the FPGA optimization implementation system for the SM4 cryptographic algorithm comprises a circulation type design architecture, a pipeline LUT type design architecture, a pipeline BRAM type design architecture and a pipeline BRAM + REGISTER type design architecture. The circular design architecture comprises a control module, a round key generation module and an encryption module; the assembly line LUT type design architecture comprises a control module, a round key generation module and an assembly line encryption module; the assembly line BRAM type design architecture comprises a control module, a round key generation module and an assembly line encryption module; the assembly line BRAM + REGISTER type design architecture comprises a control module, a round key generation module and an assembly line encryption module. According to the invention, side channel attacks can be effectively resisted, and the encryption performance is improved.
Owner:XIDIAN UNIV
Compression method and device based on cryptographic hash algorithm
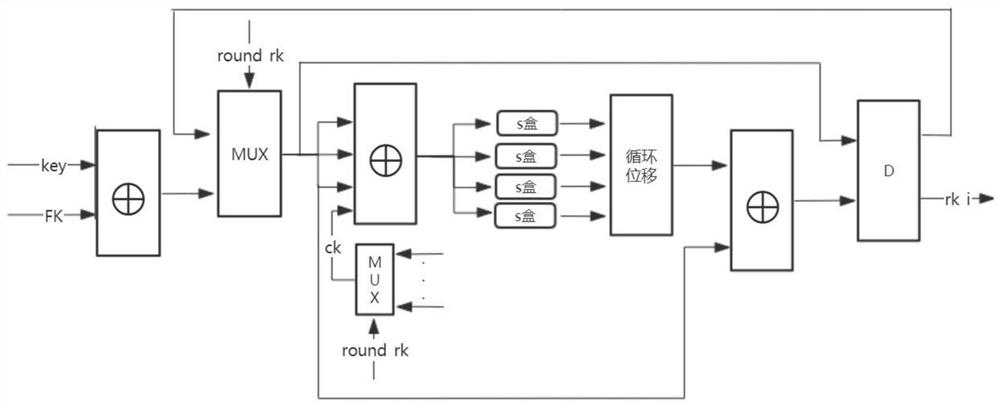
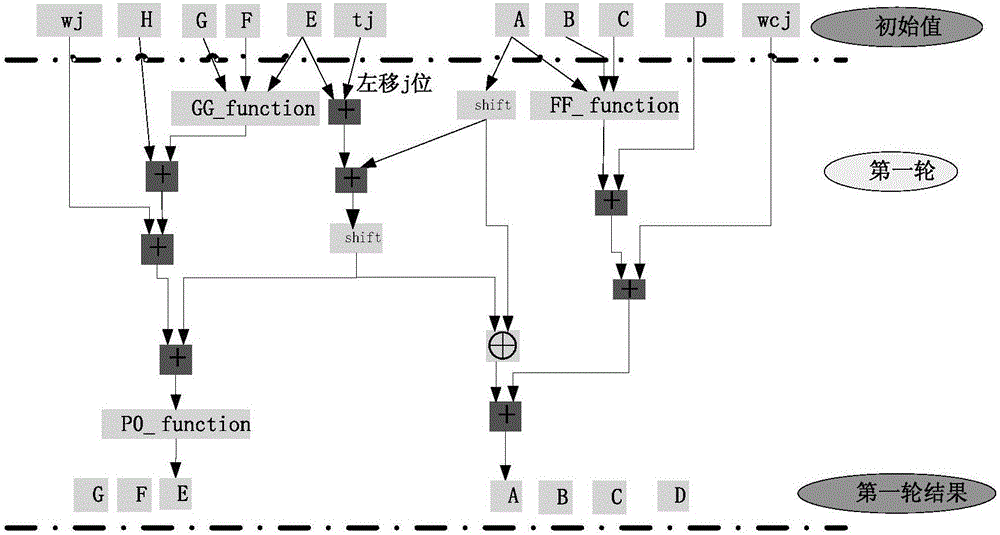
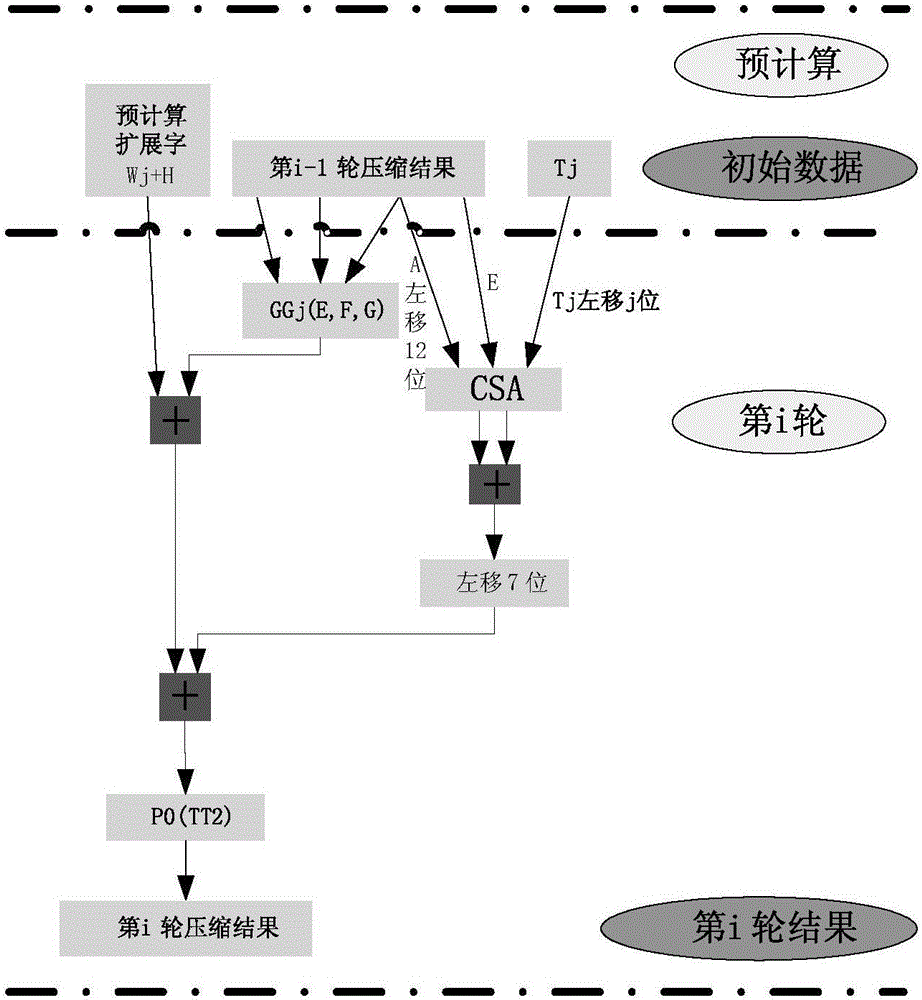
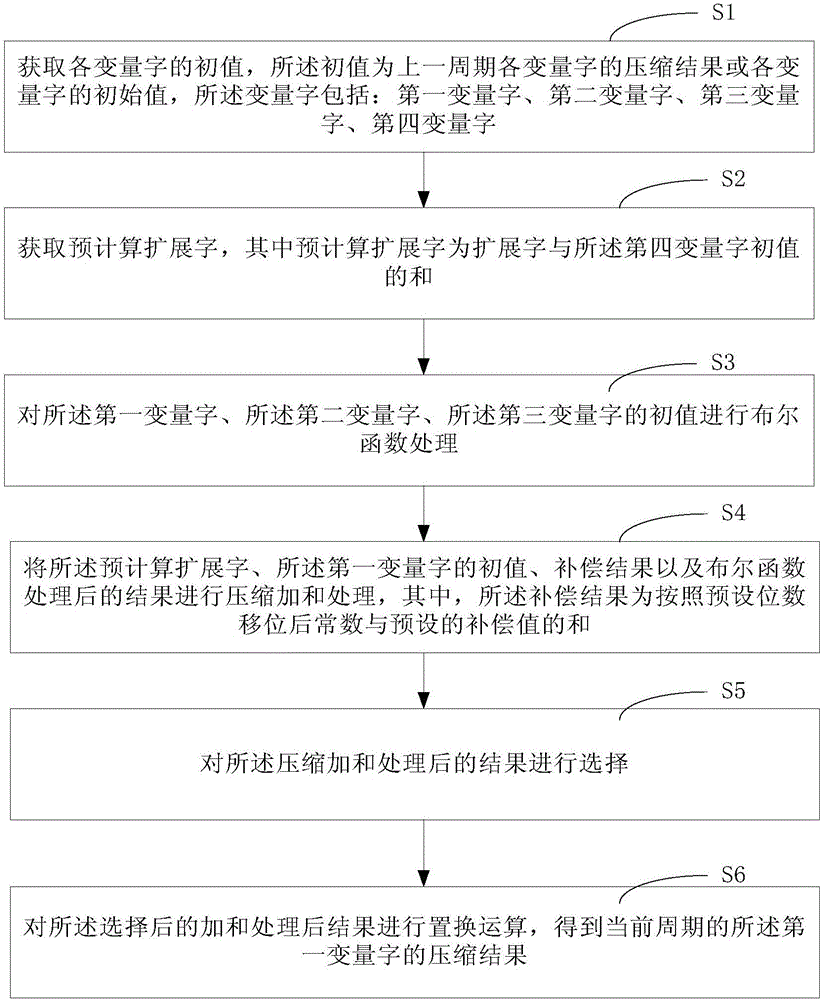
ActiveCN106301761AShorten the critical pathReduce latencyEncryption apparatus with shift registers/memoriesTime delaysBoolean function
Owner:BEIJING SMARTCHIP SEMICON TECH CO LTD +2
A hardware detector for image LSB built-in hiding information
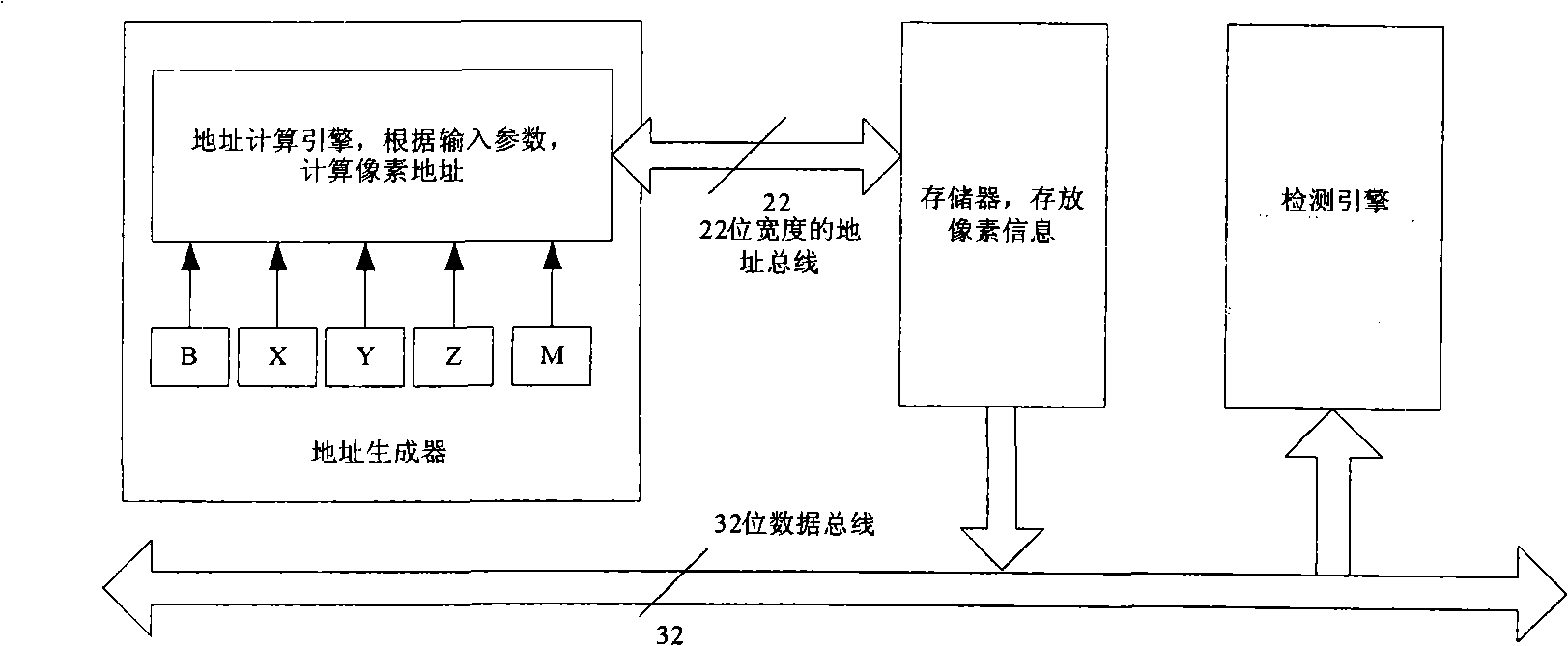
InactiveCN101266682AEasy to handleProcessing speedImage data processing detailsMemory addressAddress generator
The invention discloses a hardware detector aiming to insert hidden information into an LSB image, which comprises an address generator, a memory, and a detection engine. Wherein, the address generator connects with the memory through an address bus of 22 bits, and the memory connects with the detection engine through a data bus of 32 bits. The detector maps the RS hidden detection algorithm to hardware to be realized, which adopts a 3-level pipeline structure, thus improves data processing efficiency; the width of the data bus of the detector is 32 bits, which possesses a strong parallel processing capability and can parallel process 4 image pixels of 8 bits at the same time; the value of image pixels is saved in the memory, and the data saved in the memory is output to the detector through a memory address generated by the address generator which supports 2 scanning modes. The invention has a very strong data processing capability and the data processing speed is much higher than the current program realized by software.
Owner:ZHEJIANG UNIV
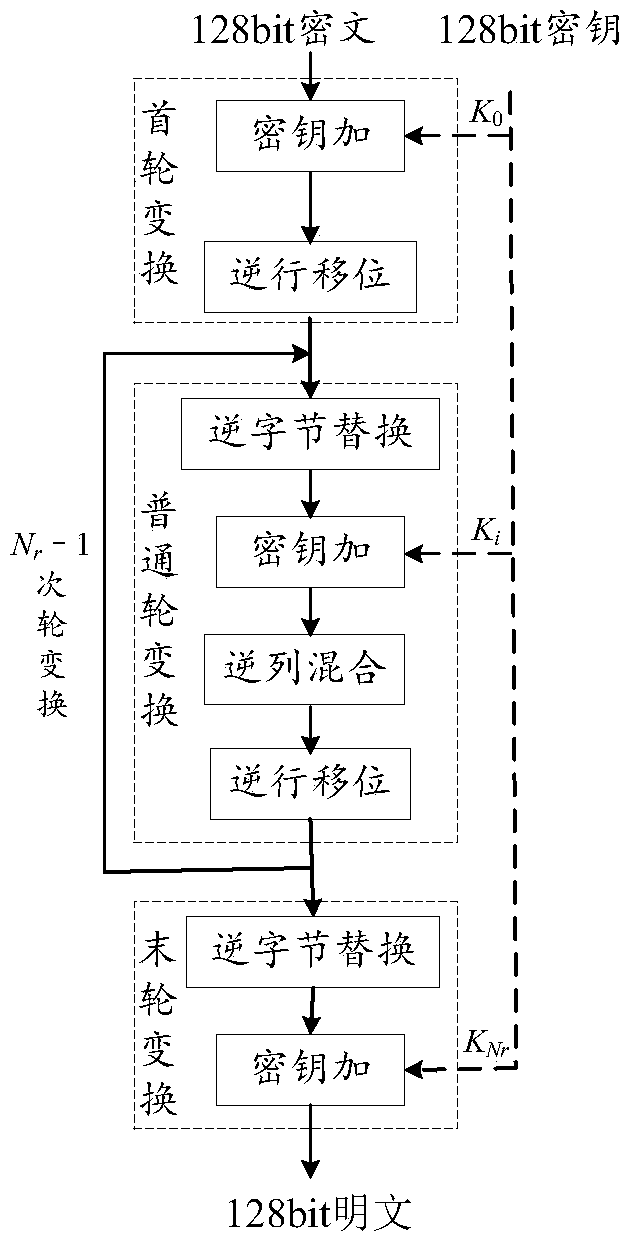
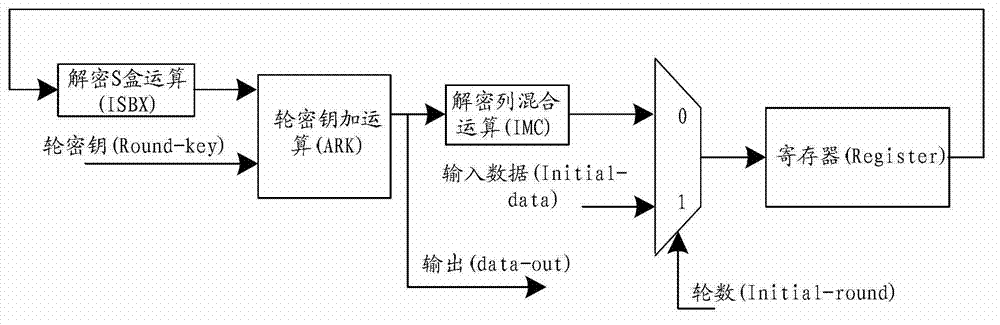
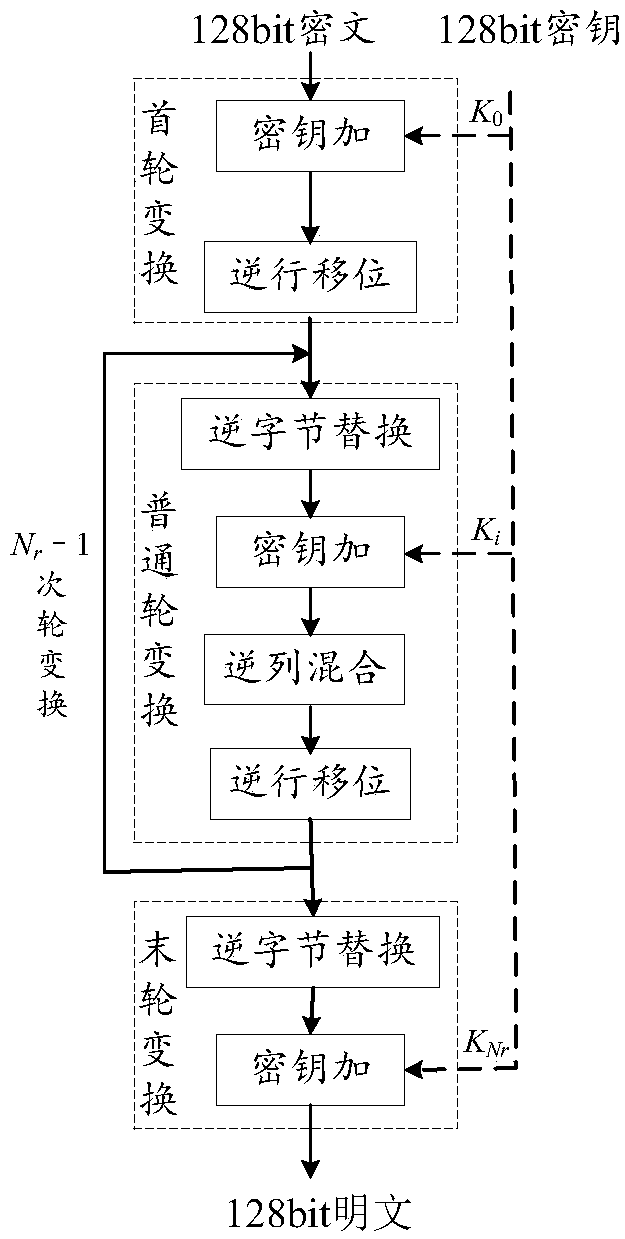
Common round transformation operation unit, common round transformation circuit and AES decryption circuit
ActiveCN108933652AShorten the critical pathRealize a small areaEncryption apparatus with shift registers/memoriesComputer hardwareTransformation unit
The invention relates to the technical field of cryptographic circuits, in particular to a common round transformation operation unit, a common round transformation circuit and an AES (Advanced Encryption Standard) decryption circuit. In the common round transformation unit used for AES decryption, all linear transformation operations in common round transformation in an AES decryption algorithm are combined into two composite matrixes through combination of constant matrixes and compositional operation, and the composite matrixes are shown in the description. A circuit critical path can be shortened and the circuit implementation area can be reduced.
Owner:ANHUI POLYTECHNIC UNIV
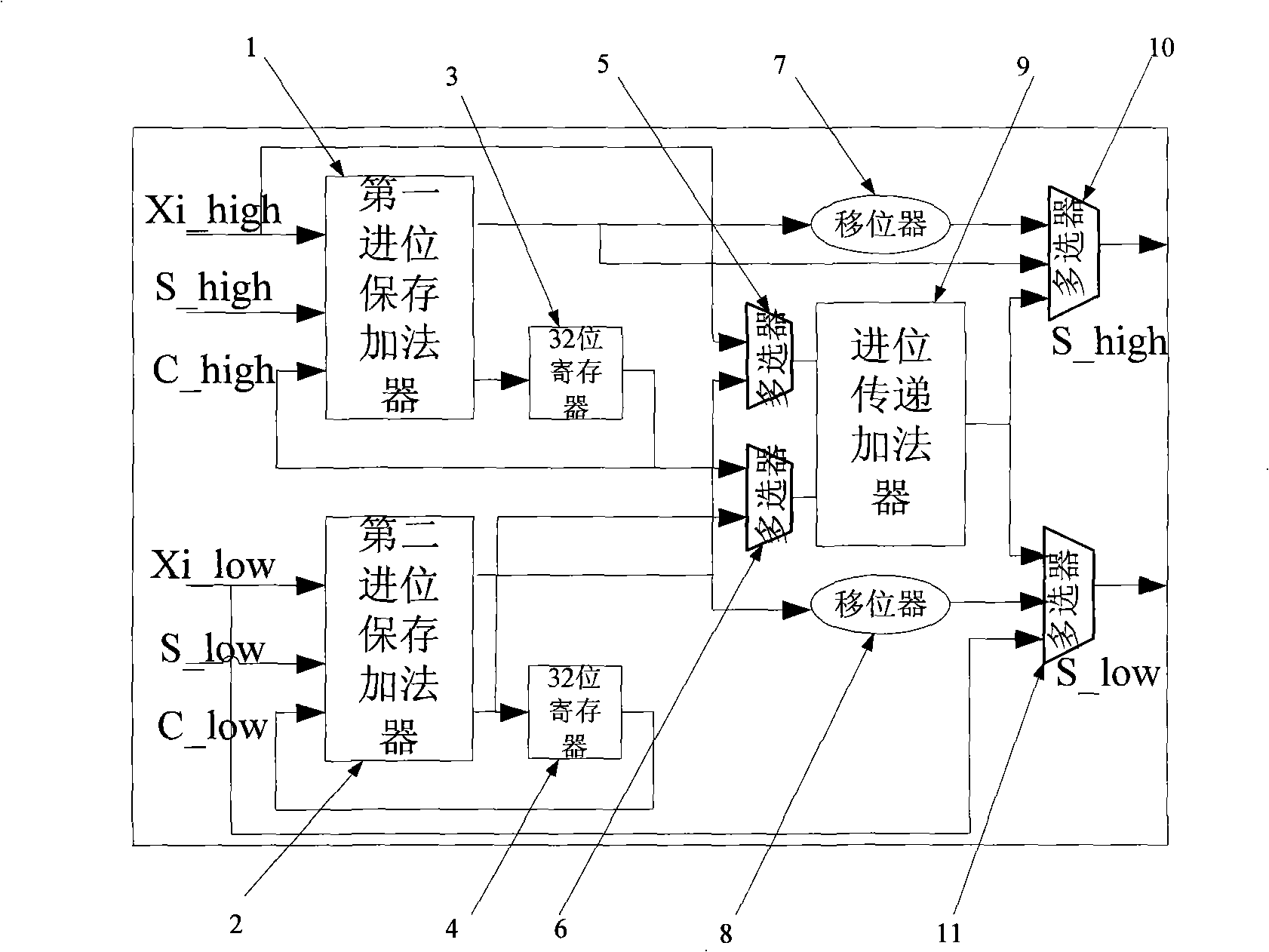
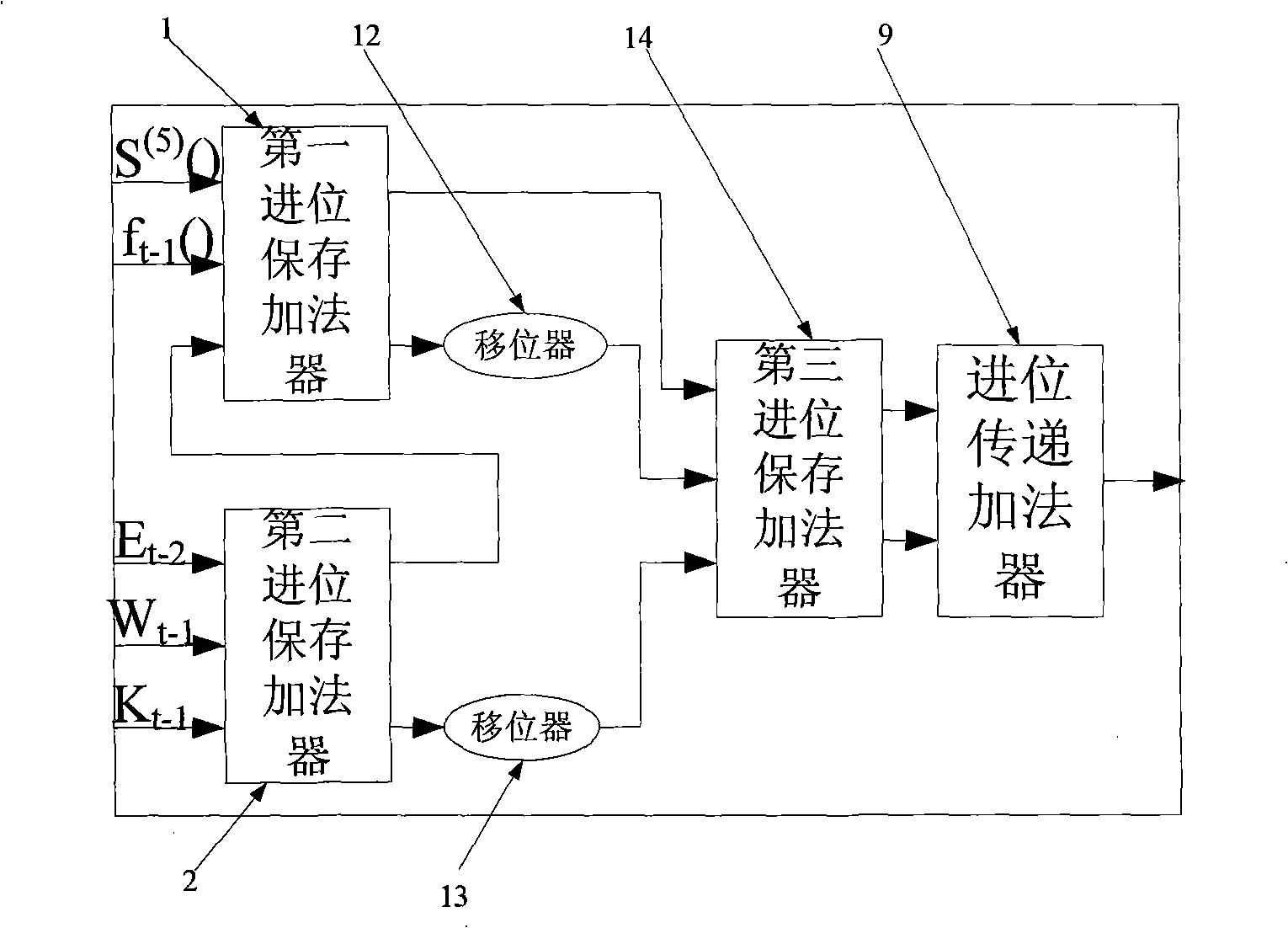
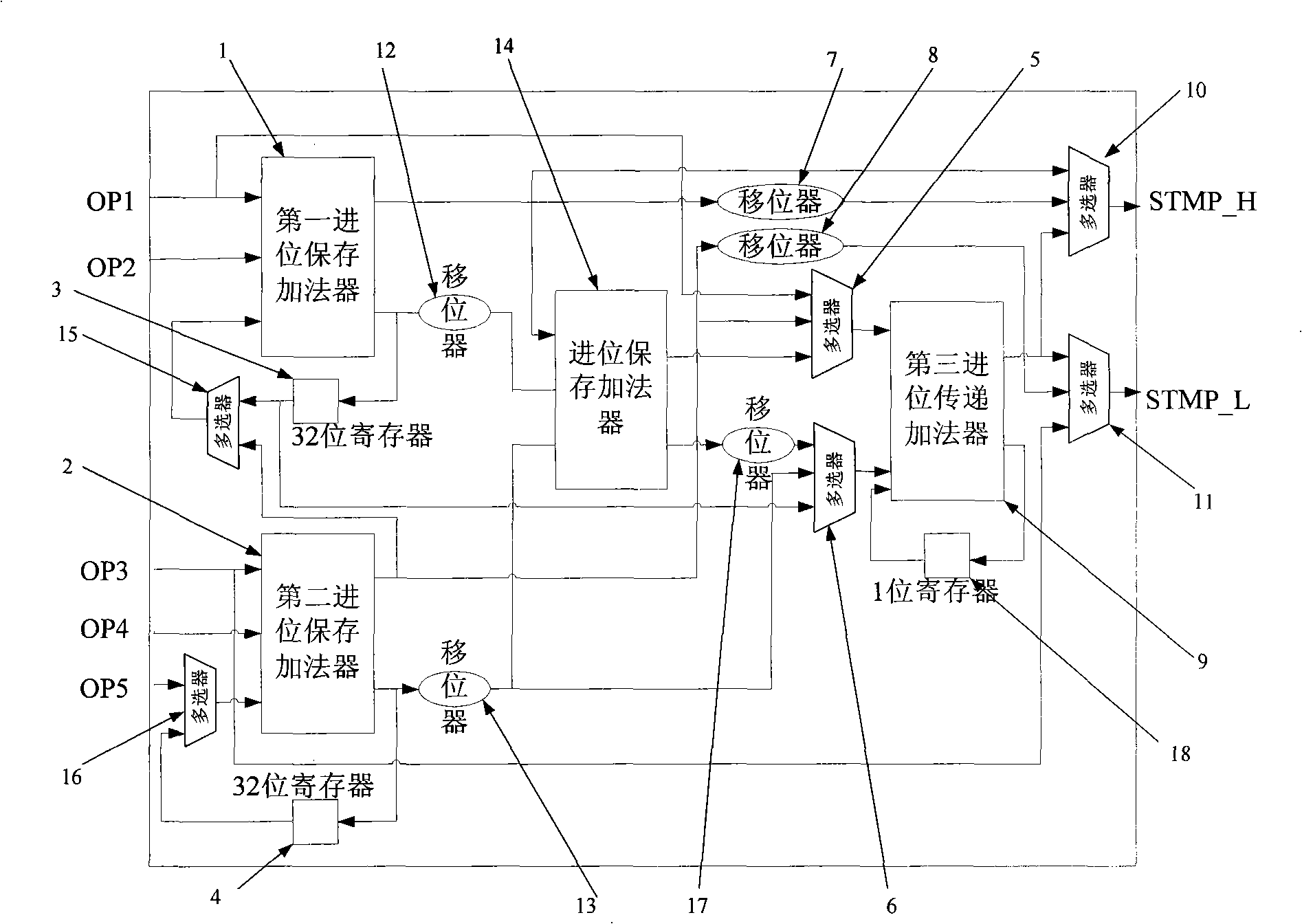
Parallel-serial multiplication-addition device
InactiveCN1529411ATroubleshoot critical path issuesEasy to modularizeAdaptive networkDigital technique networkLeast significant bitCarry-save adder
The multiplying adder comprises a parallel-serial multiplier and a digital serial adder. The parallel-serial multiplier includes following components: a re-coder receives the multiplier, and outputs a ordered sequence re-coded; a partial product generator generates multiple partial products based on multiplicand and the said ordered sequence re-coded; a adder adds multiple partial products in order to synthesize the product. When partial products are carried out summation, the adder outputs least significant digit in intermediate sum of partial product in digital serial format. The digital serial adder includes a carry save adder for receiving product and input of accumulator in order to generate a output. The said output is a sum of the product of input of the accumulator.
Owner:IND TECH RES INST
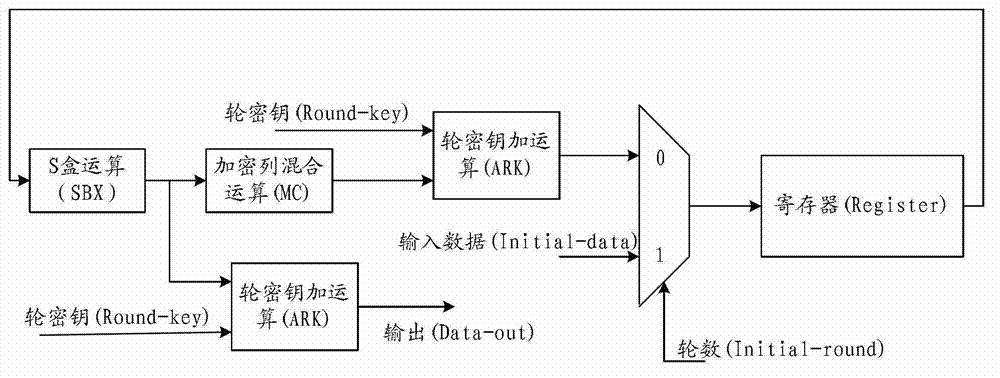
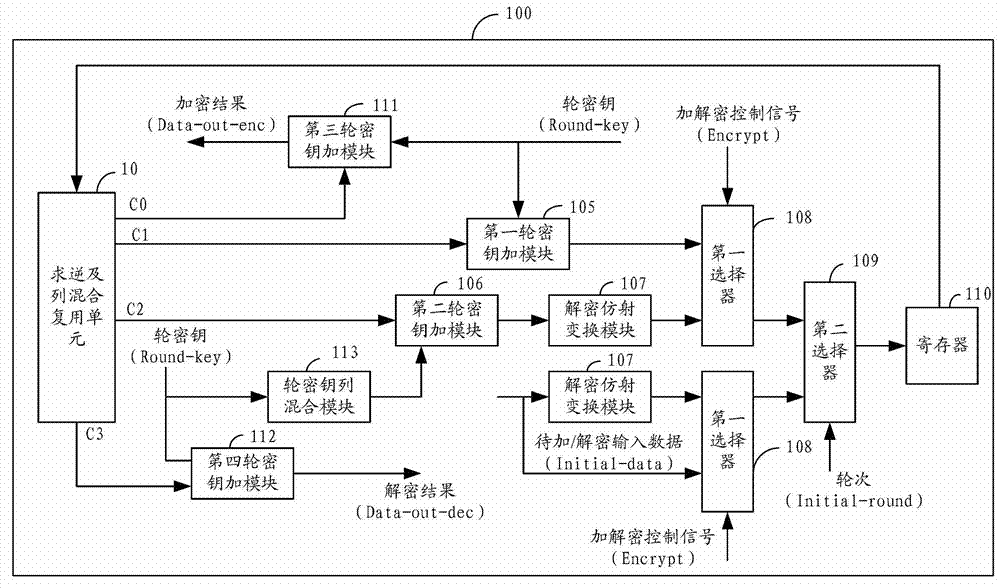
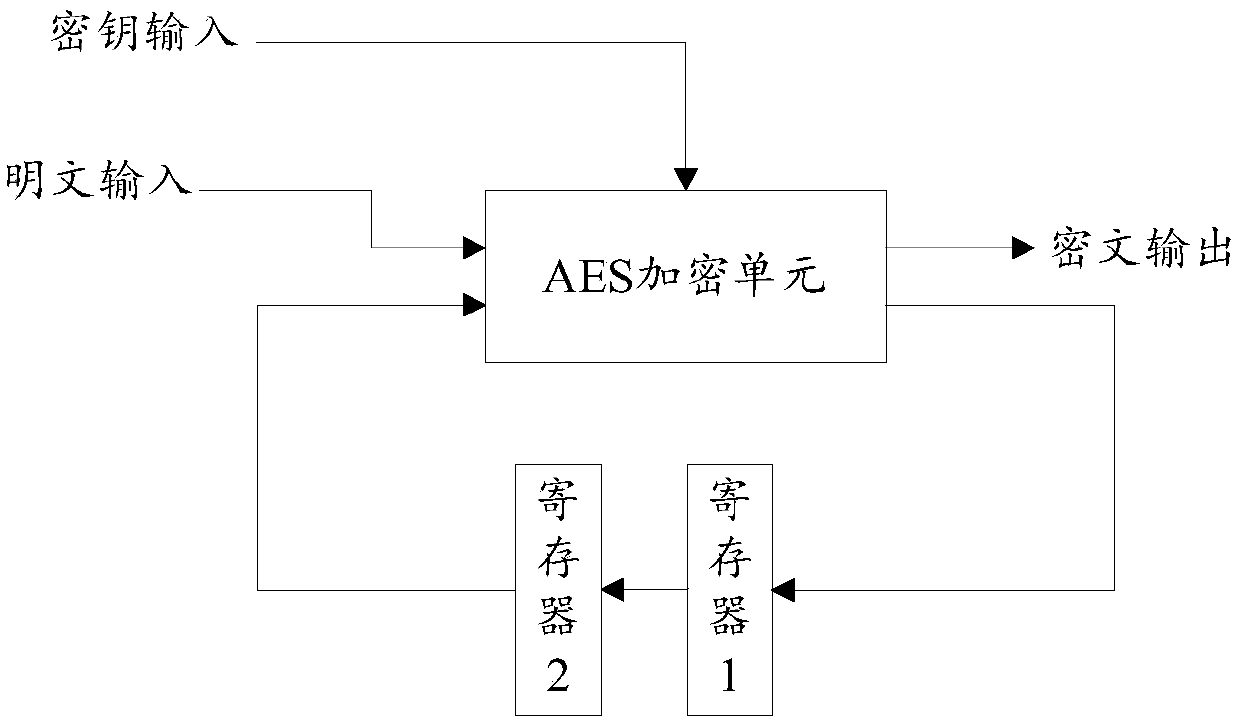
Method and device for realizing AES (advanced encryption standard) encryption and decryption
ActiveCN102857334AOptimizing combinatorial logicReduce areaEncryption apparatus with shift registers/memoriesComputer hardwareMultiplexing
The invention provides an AES (advanced encryption standard) encryption and decryption device which merges an S box with mixcolumns. The AES encryption and decryption device comprises an inversion and mixcolumn multiplexing unit, a first round secret key encryption module, a second round secret key encryption module, a decryption affine transformation module, a first selector, a second selector and a register, wherein the inversion and mixcolumn multiplexing unit comprises an inverse element solving module, an encryption affine transformation module, an encryption mixcolumn module and a decryption mixcolumn module, and the first round secret key encryption module is connected with the encryption mixcolumn module and the first selector; the second round secrete key encryption module is connected with a decryption mixcolumn module; the decryption affine transformation module is connected with the second round secrete key encryption module and the first selector; and the second selector is connected with the first selector and the register. Thus, the AES encryption and decryption device disclosed by the invention can reduce overhead of hardware resources; meanwhile, a critical path is shortened, the chip area is reduced, and operating speed of the AES encryption and decryption device is improved.
Owner:RAMAXEL TECH SHENZHEN
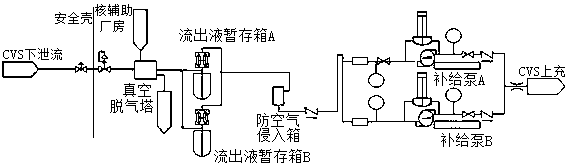
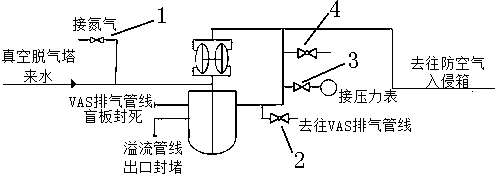
Pressurized water reactor nuclear power plant first circulation starting primary loop deoxidization method based on acid condition
InactiveCN111192702AReduce dissolved oxygenFast deoxygenationNuclear energy generationSteam generator primary sideNuclear plantPressurized water reactor
The invention relates to the technical field of coolant deoxidization, in particular to a pressurized water reactor nuclear power plant first circulation starting primary loop deoxidization method based on an acid condition. The method comprises the following steps: L1, subjecting an effluent temporary storage tank to nitrogen purging; L2, vacuumizing a primary loop coolant system; L3, filling theloop with water; L4, dynamically exhausting the primary loop; L5, establishing nitrogen coverage of the effluent temporary storage tank; L6, establishing degassing circulation between a vacuum degassing tower and the effluent temporary storage tank; L7, starting a main pump to measure the total gas content; L8, calculating the addition amount of hydrazine; L9, adding the hydrazine in a voltage stabilizer main spraying mode; L10, judging the leakage of a check valve to confirm whether the hydrazine is added and uniformly mixed or not, if so, closing the spraying of the pressure stabilizer andentering L11 and otherwise, returning to L9. On the premise that no volume control box or acid condition exists, through combination of an improved physical deoxidization technology and a chemical deoxidization technology, the deoxidization speed is greatly increased, the occupied critical path time is shortened, and the deoxidization difficulty without the volume control box or the acid conditionis relieved.
Owner:SANMEN NUCLEAR POWER CO LTD
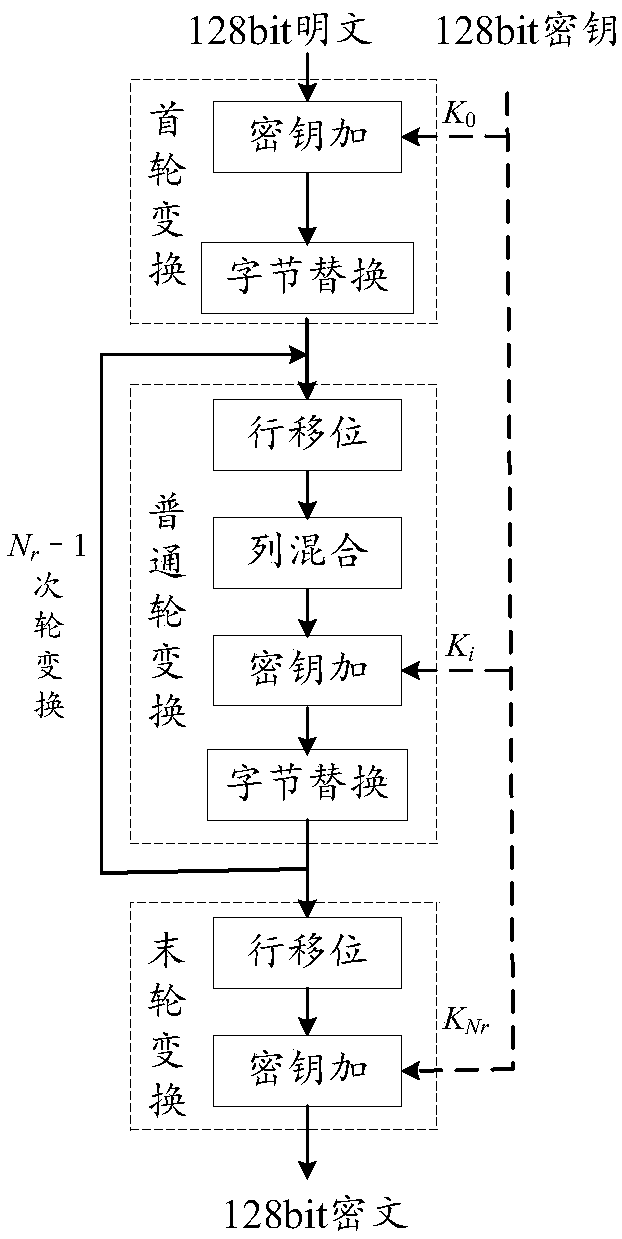
AES encryption unit based on composite matrix, AES encryption circuit and encryption method thereof
ActiveCN109033893AShorten the critical pathRealize a small areaInternal/peripheral component protectionComputations using residue arithmeticByteEncryption
The invention is applicable to the field of encryption technology and provides an AES encryption unit based on a composite matrix is provided, an AES encryption circuit and an encryption method. The AES encryption unit is used to realize 4 bytes AES encryption. By combining and synthesizing the constant matrix, all the linear transformation operations in the round transformation are combined intotwo composite matrices, the composite matrix delta and the composite matrix lambda, so as to shorten the critical path of the AES encryption circuit and reduce the area of the AES encryption circuit.
Owner:ANHUI UNIVERSITY OF TECHNOLOGY AND SCIENCE
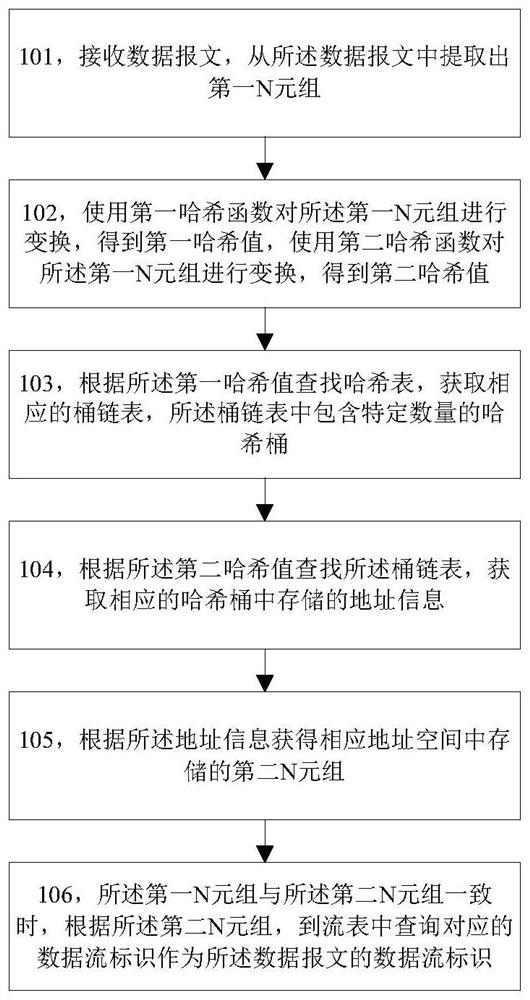
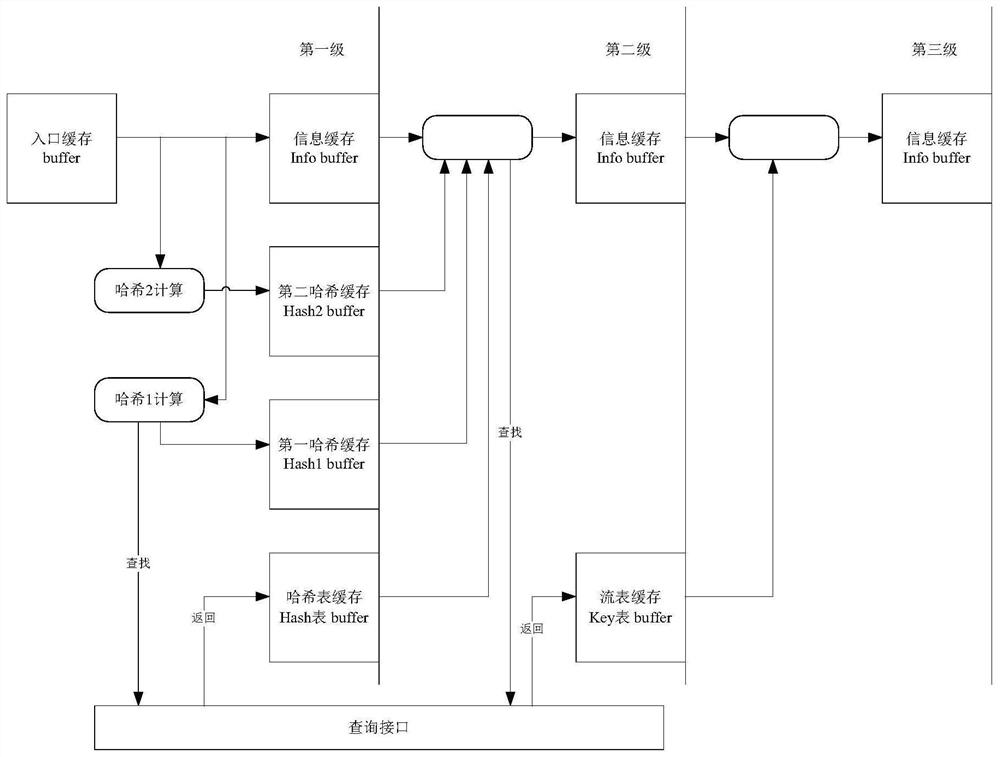
Data flow identifier query method and device
PendingCN112632079AShorten the critical pathImprove query efficiencySpecial data processing applicationsDatabase indexingAddress spaceTheoretical computer science
The invention discloses a data flow identifier query method and device. The method comprises the steps: receiving a data message, and extracting a first N-tuple from the data message; transforming the first N tuple by using a first hash function to obtain a first hash value, and transforming the first N tuple by using a second hash function to obtain a second hash value; searching a hash table according to the first hash value, and obtaining a corresponding bucket chain table, the bucket chain table including a specific number of hash buckets; searching a bucket chain table according to the second hash value, and obtaining address information stored in a corresponding hash bucket; obtaining a second N-tuple stored in the corresponding address space according to the address information; and when the first N tuple is consistent with the second N tuple, querying the corresponding data flow identifier in the flow table as the data flow identifier of the data message according to the second N tuple.
Owner:联想未来通信科技(重庆)有限公司
AES encryption arithmetic unit, AES encryption circuit and encryption method thereof
ActiveCN109033847AShorten the critical pathRealize a small areaDigital data protectionComputer hardwareCritical path method
The invention is applicable to the field of encryption technology and provides an AES encryption arithmetic unit, an AES encryption circuit and an encryption method thereof. The AES encryption operation unit combines all the linear transformation operations in the wheel transformation into two composite matrices, the composite matrix delta and the composite matrix lambda through the combination and synthesis operation of the constant matrices, thereby shortening the critical path of the AES encryption circuit and simultaneously reducing the realization area of the AES encryption circuit.
Owner:ANHUI UNIVERSITY OF TECHNOLOGY AND SCIENCE
Multiplexing round conversion circuit, AES encryption circuit and encryption method thereof
ActiveCN108566271ASave resourcesShorten the critical pathEncryption apparatus with shift registers/memoriesMultiplexingComputer hardware
The invention is applicable to the technical field of encryption and provides a round conversion multiplexing circuit, an AES encryption circuit and an encryption method. The multiplexing round conversion circuit proposed by the invention combines all linear conversion operations in an AES cryptographic algorithm into two composite matrices of a composite matrix delta and a composite matrix lambdaby merging and compositional operation of constant matrices; thereby shortening the critical path of the AES encryption circuit formed by the multiplexing round conversion circuit, reducing the implementation area of the AES encryption circuit, and realizing ordinary round conversion and final multiplexing round conversion through a multiplexing composite matrix multiplication unit 1 and a composite domain inverse-of-multiplication unit, so as to save large amounts of circuit resources.
Owner:ANHUI UNIVERSITY OF TECHNOLOGY AND SCIENCE
Construction method for shielding cooling system and steel lining wall of high temperature gas cooled reactor
ActiveCN102605952AShorten the critical pathShorten the timeBuilding material handlingNuclear reactorEngineering
The invention relates to a construction method for a shielding cooling system and a steel lining wall of a high temperature gas cooled reactor, which belongs to the technical field of reactor structures. The method includes: arranging a steel lining according to design requirements and welding cooling water pipes to the inner surfaces of the steel lining to form a combined structure module, hoisting the module to the position of a primary loop cabin of the high temperature gas cooled reactor, sequentially binding inner main reinforcement bars, auxiliary reinforcement bars and outer main reinforcement bars, erecting a constructional outer mould plate, concreting between the steel lining and the constructional outer mould plate to form a lower-layer combined structural wall module, hoistingan upper-layer module on the lower-layer combined structural wall module, and cycling so to form the wall of the primary loop cabin of the high temperature gas cooled reactor. Using the construction method can shorten time of constructional critical paths, reduce cross workload on a construction site, relieve work intensity on the construction site and guarantee accurate execution of constructionschedule while improve construction quality and shorten construction period.
Owner:CHINERGY CO LTD
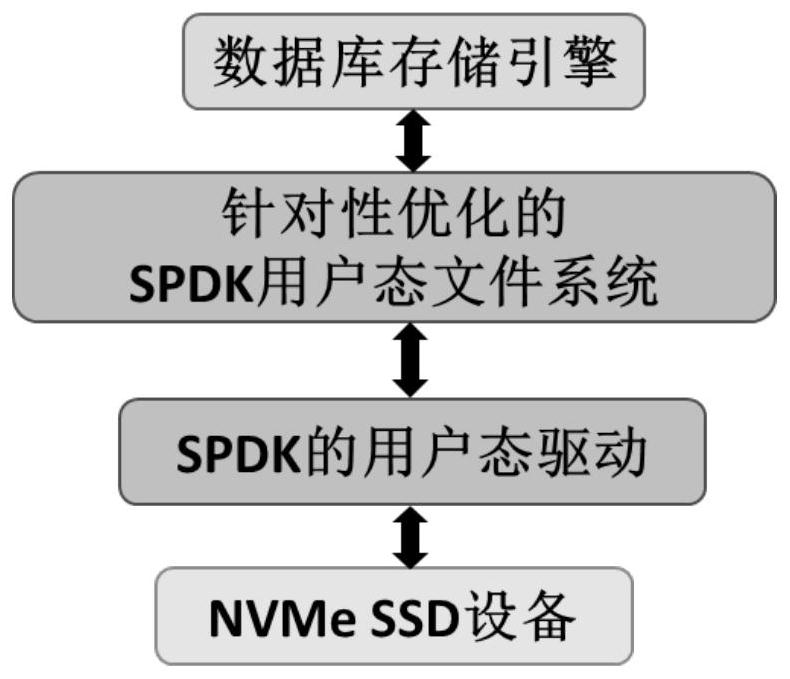
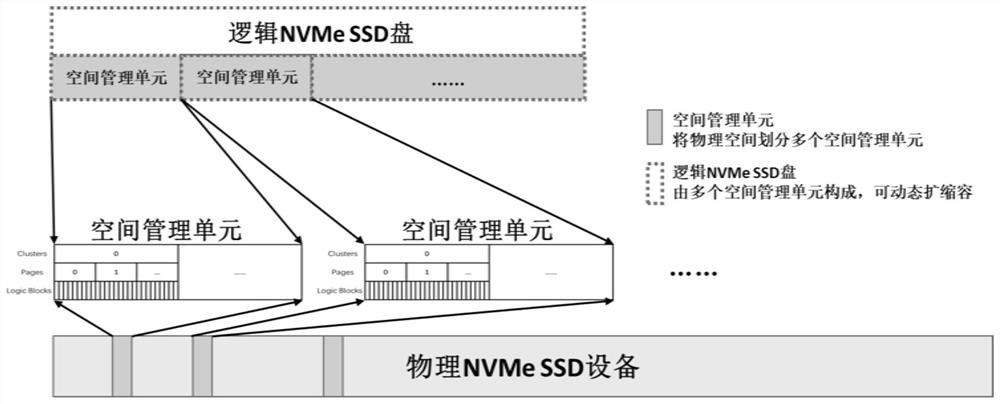
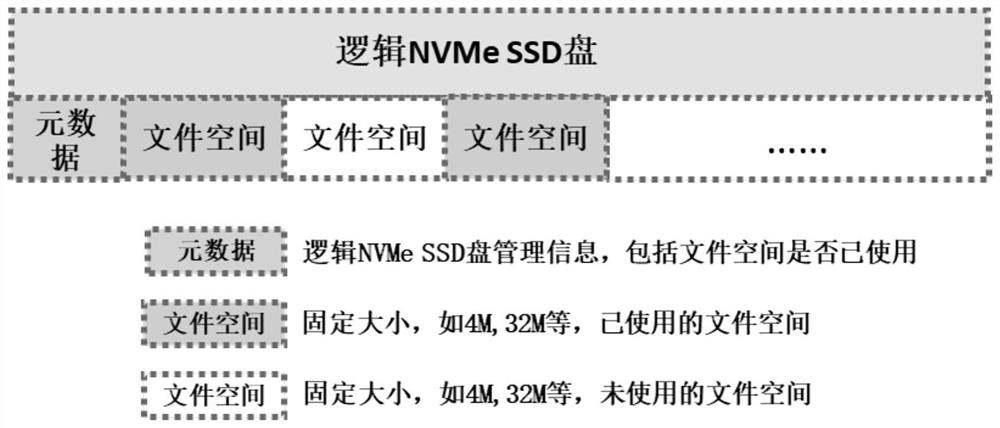
Database storage engine acceleration method and system based on an SPDK
ActiveCN113688099AFit closelyAchieve accelerationInput/output to record carriersProgram synchronisationFile systemEngineering
The invention discloses a database storage engine acceleration method and system based on an SPDK, belongs to the technical field of databases and storage, and aims to solve the technical problems of how to give full play to the original writing advantage of supporting high throughput of a storage engine, optimizing a read service scheduling mechanism, reducing unnecessary mutual exclusion and improving read concurrency, reducing random access of data, and accelerating the overall performance of a database storage engine. According to the technical scheme, the method comprises the following steps that NVMe SSD equipment is bound with a user mode driver of an SPDK; the NVMe SSD equipment is formatted by using a user mode file system lattice disk tool; and the packaging storage engine operates an interface of the user mode file system and performs normal storage access. The system comprises a binding unit, a formatting unit and a packaging unit.
Owner:上海沄熹科技有限公司
Round transformation multiplexing circuit and AES (Advanced Encryption Standard) decryption circuit
ActiveCN108809627ARealize a small areaImprove optimization efficiencyEncryption apparatus with shift registers/memoriesComputer hardwareMultiplexing
The invention relates to the technical field of a password circuit and provides a round transformation multiplexing circuit and an AES (Advanced Encryption Standard) decryption circuit. According to the round transformation multiplexing circuit provided by the invention, through combination and composite calculations of a constant matrix, all linear transformation calculations in an AES decryptionalgorithm are combined into two composite matrixes: a composite matrix delta(-tilde) and a composite matrix inverse-V(-tilde). A key path of the AES decryption circuit is reduced, and moreover, an AES decryption realization area is reduced.
Owner:ANHUI UNIVERSITY OF TECHNOLOGY AND SCIENCE
Zoom device for residue number system
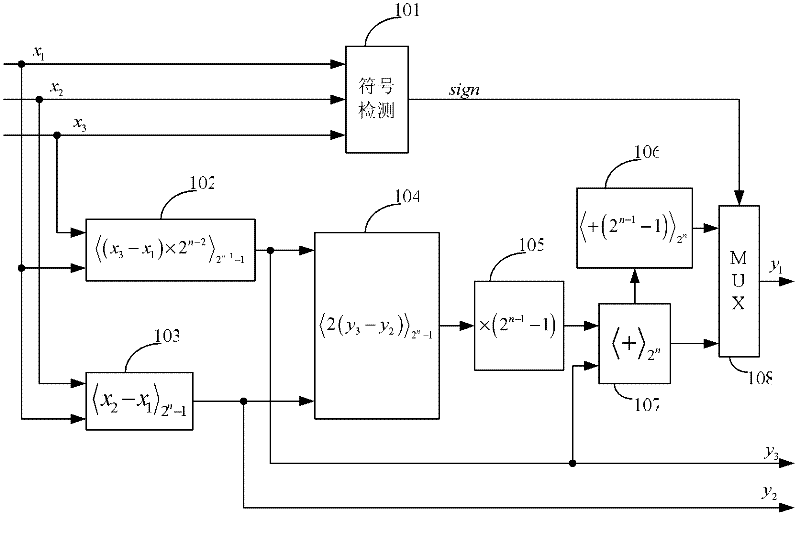
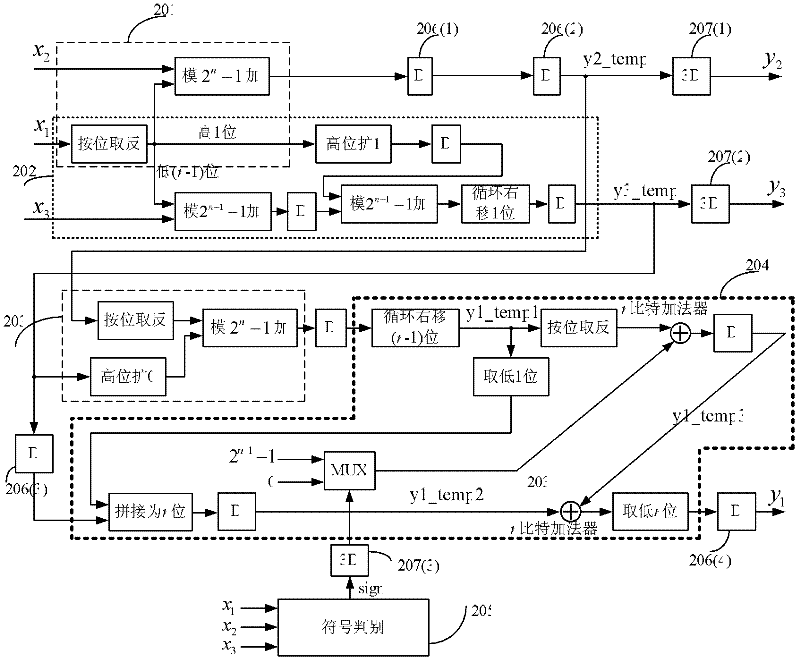
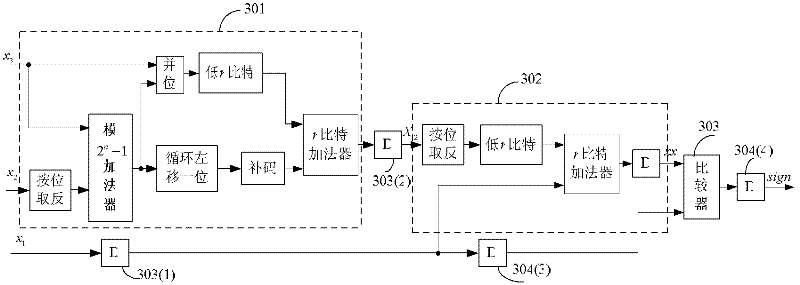
InactiveCN102214082AReduce latencySimple structureComputations using residue arithmeticDigital signal processingNegation
The invention discloses a 2n zoom device for a residue number system (RNS) of which the base is {2<n>, 2<n>-1 and 2<n-1>-1}. The zoom device comprises a modulus 2<n>-1 adder, a modulus 2<n-1>-1 adder, an n-bit common binary adder, a sign detection module, a selector and some simple logic operation such as cyclic shift, bitwise negation and the like. The implementation structure is simple and clear; by adding a pipeline register at a proper position, a key route becomes smaller; therefore, an active effect on reduction of the time delay of the key route of the RNS during application of a digital signal processing system is achieved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
AES encryption unit, AES encryption circuit and encryption method
ActiveCN108989018AShorten the critical pathRealize a small areaKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComposite matrixLinear transform
The invention is applicable to the field of encryption technology. An AES encryption unit, AES encryption circuit and encryption method are provided. An AES encryption unit is proposed. The AES encryption unit realizes 4 bytes AES encryption. The AES encryption unit combines all the linear transformations into two composite matrices by combining and synthesizing the constant matrices, namely the composite matrix delta and the composite matrix lambda, thereby shortening the critical path of the AES encryption circuit and reducing the area of the circuit.
Owner:ANHUI UNIVERSITY OF TECHNOLOGY AND SCIENCE
Rapid unearthing system for top-down ultra-deep foundation pit and construction method of rapid unearthing system
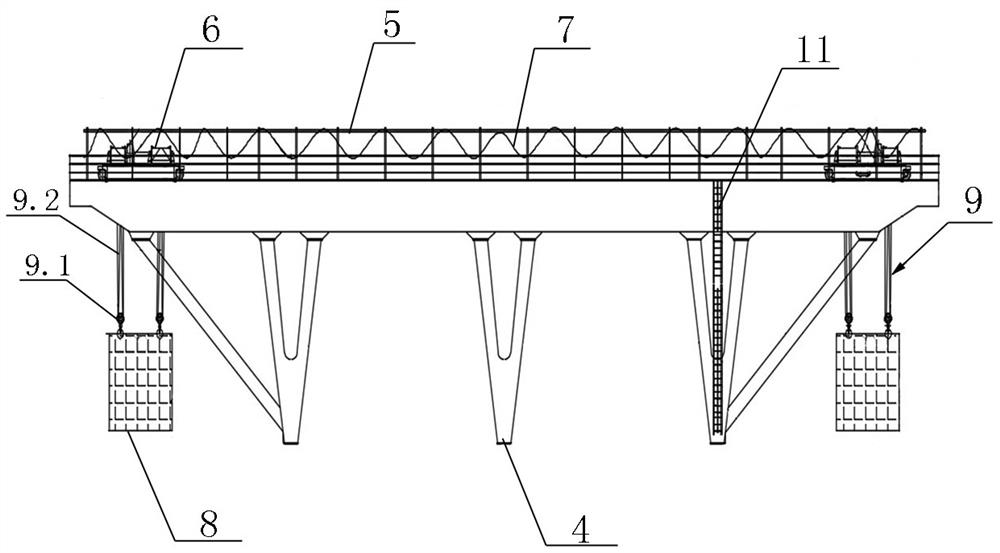
ActiveCN112209252AImprove efficiencySmall footprintLoad-engaging girdersBase supporting structuresArchitectural engineeringWinch
The invention discloses a rapid unearthing system for a top-down ultra-deep foundation pit and a construction method of the rapid unearthing system. The rapid unearthing system comprises supporting legs, an equipment frame, lifting trolleys, hanging boxes, cables, a cab, an earth excavating machine and a dumper. The supporting legs are correspondingly connected to a platform at intervals. The supporting legs are correspondingly connected to a platform at intervals. The equipment frame is arranged on the supporting legs. The two ends of the equipment frame exceed the side faces of the corresponding sides of the platform correspondingly. The equipment frame comprises main beams and secondary beams. The main beams are connected to the supporting legs. The secondary beams are connected betweenthe adjacent main beams. Protective railings are arranged on the equipment frame along the peripheral edges. The lifting trolleys are installed on the main beams correspondingly. Winches are connected to the lifting trolleys. The hanging boxes are hung below the lifting trolleys through hanging tools. The cab is installed on the side faces of the supporting legs. The cables are connected betweenthe cab and the lifting trolleys, between the lifting trolleys, and between the lifting trolleys and the hanging boxes. The earth excavating machine is arranged at the bottom of the foundation pit. The rapid unearthing system solves the problems that in the prior art, the construction efficiency is low, the cost is high, the number of adopted machines is large, and the occupied space of the machines is large.
Owner:CHINA CONSTR FIRST BUILDING GRP CORP LTD +1
High-speed 8B/10B coder, decoder and processing method thereof for error input
InactiveCN101674089BHigh speedShorten the critical pathIndividual digits conversionPathPingAlgorithm
The invention provides a high-speed 8B / 10B coder, a decoder and a processing method thereof for error input. The coder comprises a data character precoding module, a RD calculating module and a data character precoding correction module, and the coder adopts a pipeline structure and a parallel processing method; the data character precoding module, the data character precoding correction module and the RD calculating module are respectively precoded and then post collected; the data character precoding module precodes input data in first-stage flow water, and calculates whether the current input code word can cause RD to turn by a RD_turn module; the RD calculating module calculates a RD value passing through the code word in second-stage flow water, and calculates the obtained RD value by using the former clock period to correct the precoded result of the current code word. The invention respectively adopts the pipeline structure and the parallel processing method when being applied in a high-speed serial interface, thus simplifying the circuit design, shortening the key path and improving speed.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com