FPGA optimization implementation method and system for SM4 cryptographic algorithm and application
A technology for implementing systems and cryptographic algorithms, applied in the field of FPGA optimization and implementation of SM4 cryptographic algorithms, can solve problems such as large resource consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
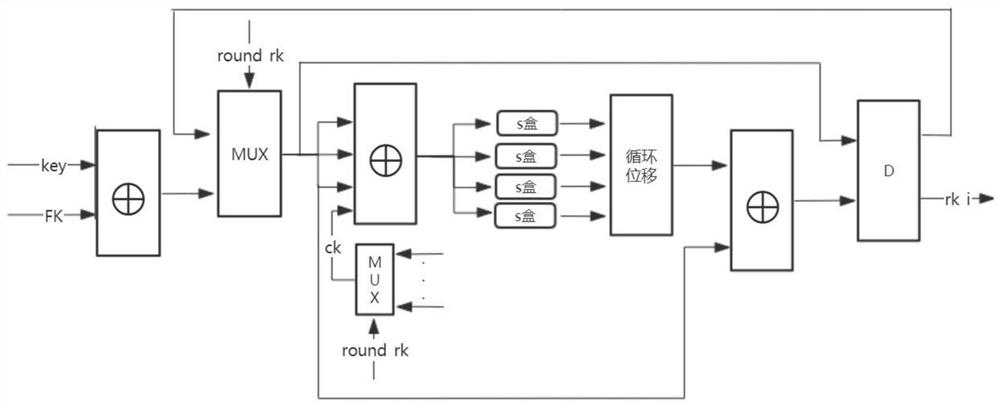
[0099] The SM4 algorithm is a group encryption algorithm, the length of the message group and the key are both 128 bits, mainly including the key expansion algorithm, encryption algorithm, and decryption algorithm. The algorithm adopts a 32-round nonlinear iterative structure, and the encryption and decryption algorithm structures are the same, but the order of using the round keys is reversed.
[0100] The following is a brief introduction to the principle of the SM4 algorithm. represents the vector set of bits e, The elements in are called words, The elements in are called bytes. Sbox(·) represents an S-box with 8 inputs and 8 outputs, which is used for nonlinear permutation. Represents a 32-bit XOR operation. i (i=0,···,31) represents a round key with a length of 32 bits. ck i (i=0,···,31) represents a system parameter with a length of 32 bits. The round function F is expressed as The nonlinear transformation τ is expressed as τ(A)=(Sbox(a 0 ),Sbox(a 1 ),Sbox(a...
Embodiment 2
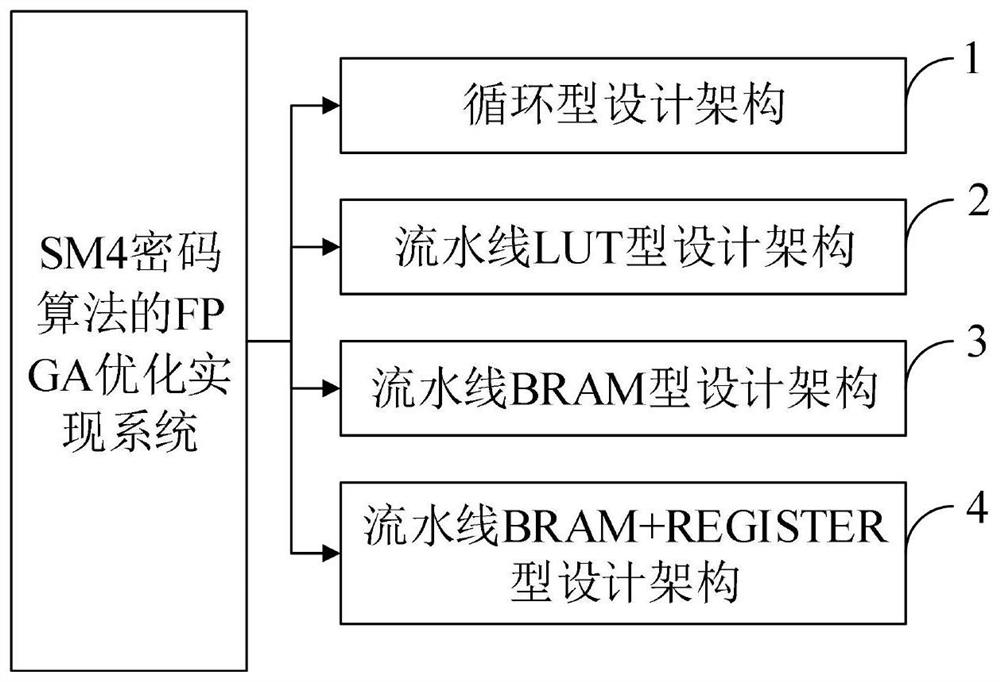
[0113] The FPGA optimization implementation system of the SM4 cryptographic algorithm provided by the embodiments of the present invention includes: a circular design architecture, a pipeline LUT type design architecture, a pipeline BRAM type design architecture, and a pipeline BRAM+REGISTER type design architecture.
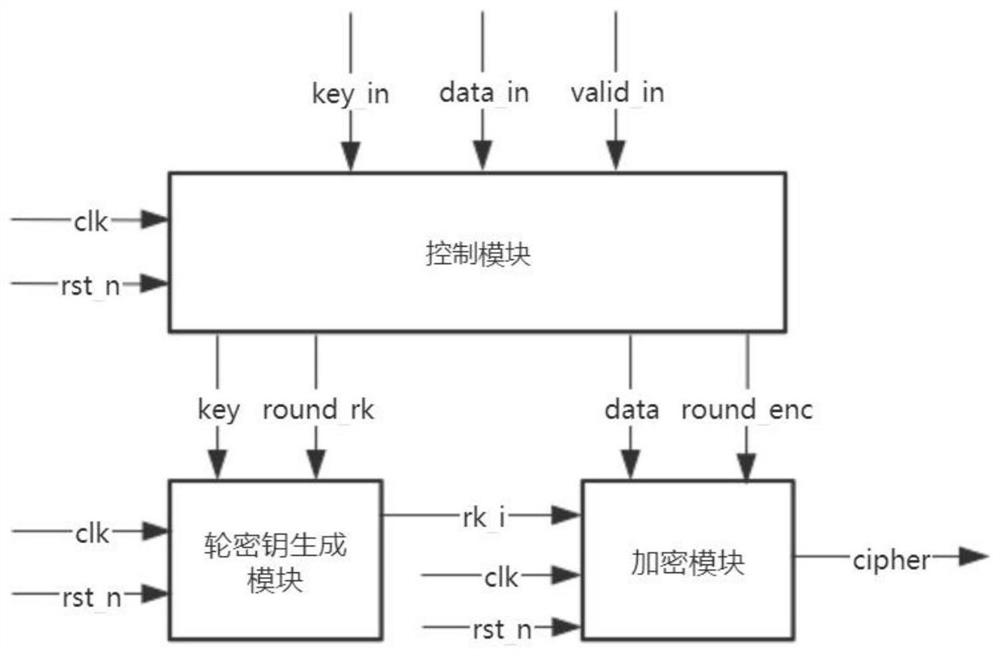
[0114] 1. The circular design architecture includes a control module, a round key generation module, and an encryption module.
[0115] (1) The control module is used to receive keys, messages to be encrypted, valid signals, judge the current state, output keys, messages to be encrypted, current iteration round signals, etc. to the round key generation module and encryption module, and control and coordinate the round The key generation module and encryption module are functioning normally.
[0116] In the above scheme, the control module includes a set of counters, which are used to provide the current iteration round signal for the round key generation module ...
Embodiment 3
[0142] The FPGA optimization implementation method of the national secret SM4 symmetric cipher algorithm provided by the embodiment of the present invention mainly includes a circular architecture design scheme for resource saving optimization and a pipelined architecture design scheme for encryption performance optimization. The pipeline architecture solution is mainly composed of three design ideas based on LUT, BRAM, and BRAM+REGISTER.
[0143] The circular architecture scheme includes a control module, a round key generation module and an encryption module, including:
[0144] (1) The control module is mainly composed of a counter and a Moore state machine. The counter judges the input control signal valid_in to count, and provides the current iteration round signal for the entire loop architecture. The Moore state machine is divided into idle and working states. When the system is in the idle state, the control module receives signals such as the plaintext to be encrypte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com