Security scanning method and system
A technology of security scanning and scanning method, which is applied in the direction of transmission system, electrical components, etc., can solve the problems of opacity, unintuitive user interface and operation, and single content of security scanning, so as to achieve diversified content, intuitive user interface and operation, and improve The effect of operating efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
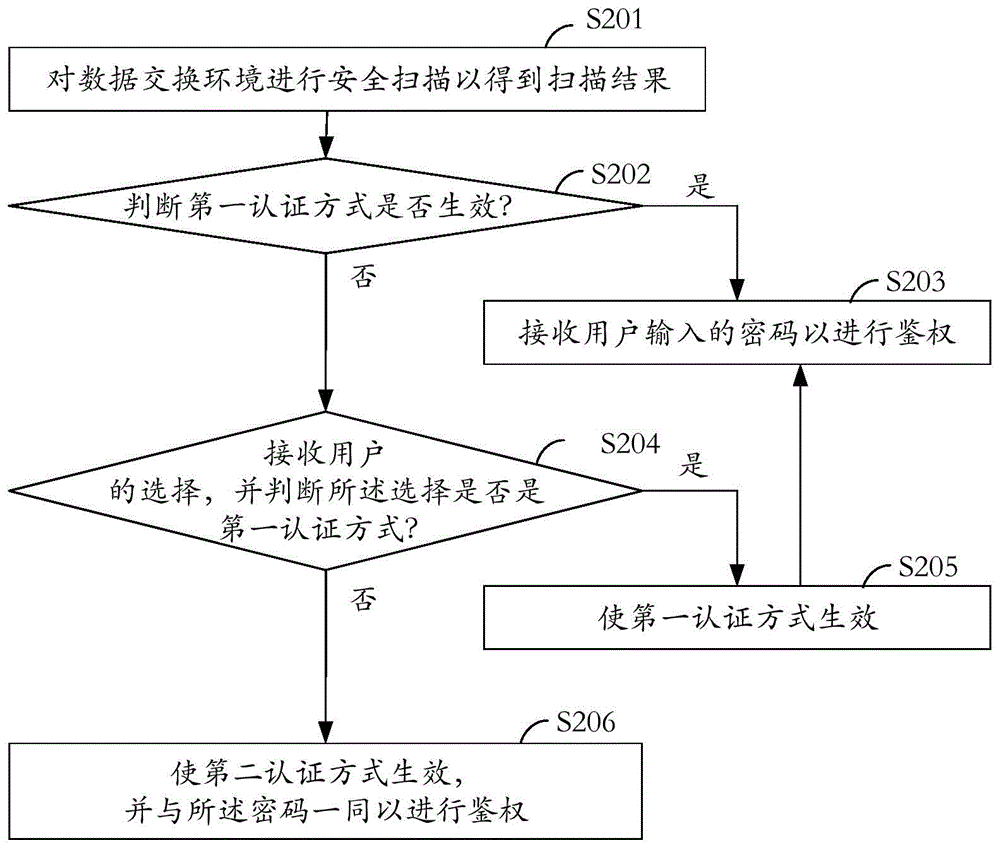
[0035] see figure 2 , which is a schematic workflow diagram of the security scanning method provided by the embodiment of the invention.
[0036] In step S201, a security scan is performed on the data exchange environment to obtain a scan result.
[0037] In step S202, it is judged according to the scanning result whether the first authentication method is valid, wherein if the first authentication method is valid, then step S203 is executed; if the first authentication method is not valid, then step S204 is executed.
[0038] In step S203, the prompt is a security environment, and the password input by the user is received for authentication.
[0039] In step S204, it is prompted that it is an unsafe environment, and the user's selection of the first authentication method and the second authentication method is received.
[0040] This step can also be understood as receiving the user's selection and judging whether the selection is the first authentication method, wherein ...
Embodiment 2
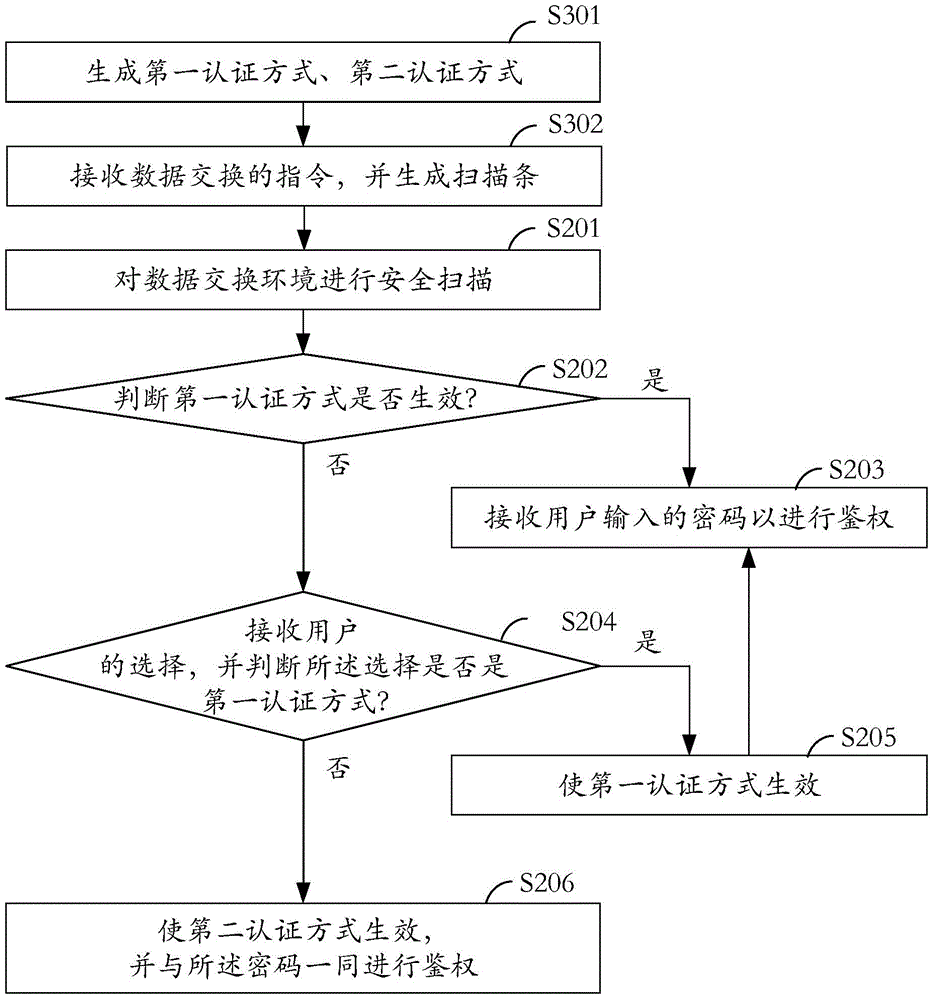
[0055] see image 3 , which is a schematic workflow diagram of the security scanning method provided by the embodiment of the invention. Understandably, figure 2 yes figure 1 Process optimization of the security scanning method shown. Among them, in order to reflect the figure 1 Zhongyuan steps with figure 2 The difference between the optimization steps in , the original step starts with S20, and the optimization step starts with S30. The following steps are performed in the order in which they appear, unless otherwise indicated.
[0056] In step S301, a first authentication method and a second authentication method are generated.
[0057] It can be understood that the step of generating the authentication method specifically includes:
[0058] (1) Select two authentication methods from a variety of preset authentication methods, including but not limited to shields, digital certificates, text messages, secret codes or tokens, and through the above authentication meth...
Embodiment 3
[0076] see Figure 4 , is a block diagram of the security scanning system provided by the embodiment of the invention.
[0077] The security scanning system 100 includes: an authentication generation module 11 , a scanning bar 12 , a scanning module 13 , a judging module 14 , a first authentication module 15 , a selection bar 16 , a receiving module 17 , and a second authentication module 18 .
[0078] The authentication method generating module 11 is configured to generate the first authentication method and the second authentication method. Specifically, the authentication method generation module 11 includes: a selection submodule and a priority submodule.
[0079] It can be understood that the selection sub-module is used to select two authentication methods from preset authentication methods, wherein the preset authentication methods at least include: shield, digital certificate and short message. The priority sub-module is configured to set priorities for the two authe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com