A double chaotic image encryption method based on the characteristics of plaintext itself
An encryption method and technology of plaintext images, applied in image data processing, image data processing, instruments, etc., can solve problems such as inability to effectively resist differential attacks, statistical characteristic analysis, and inability of image encryption to effectively resist attacks, and achieve encryption effects. Good, improve security, resist differential attack effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
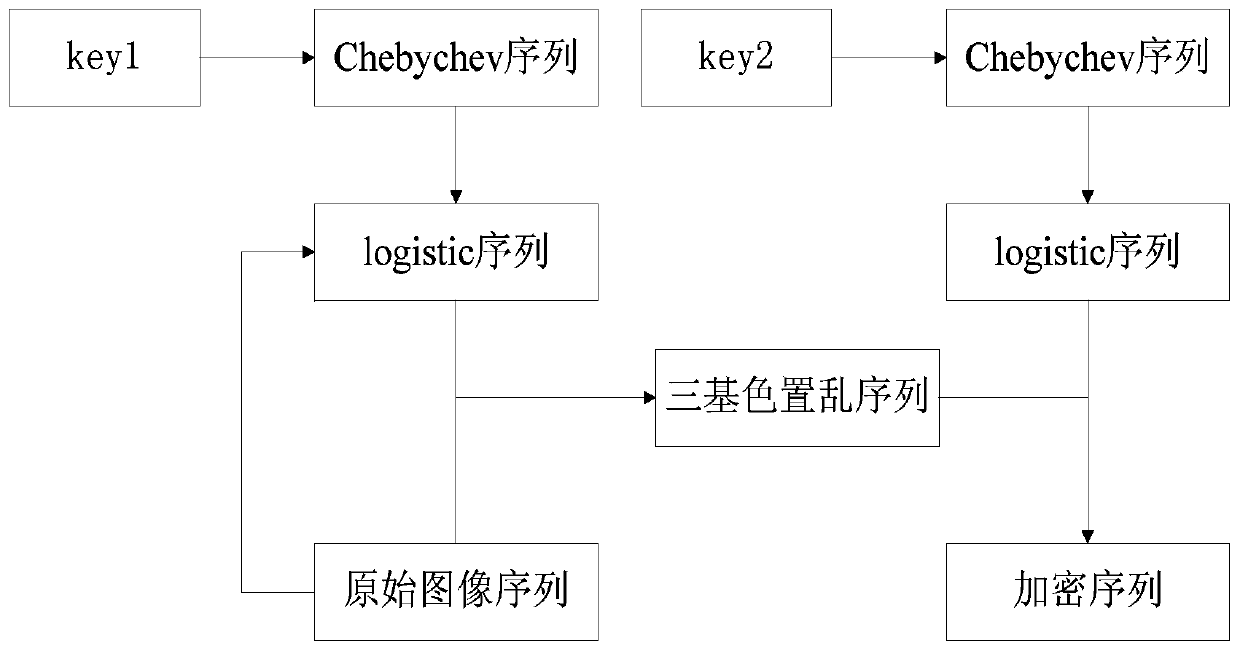
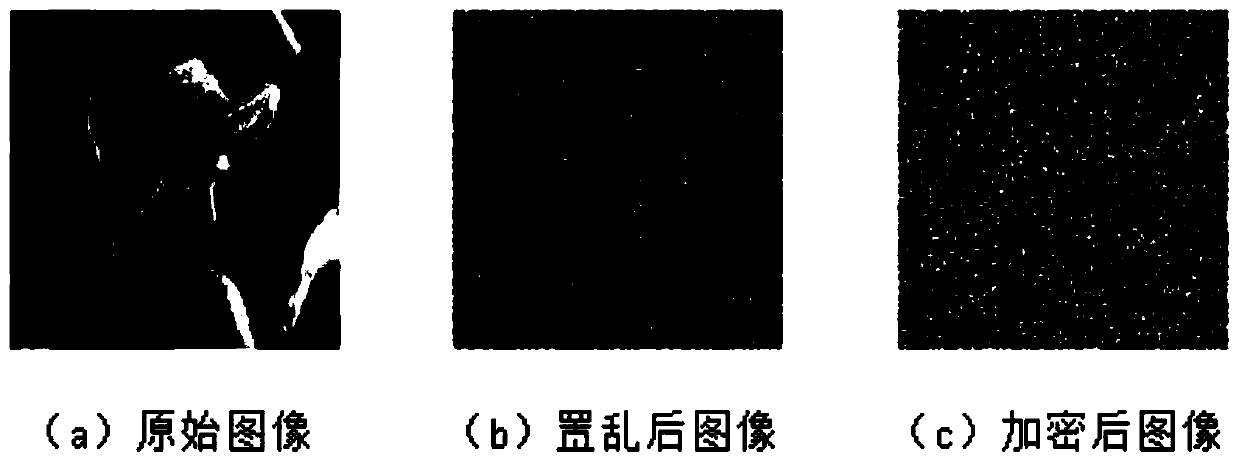
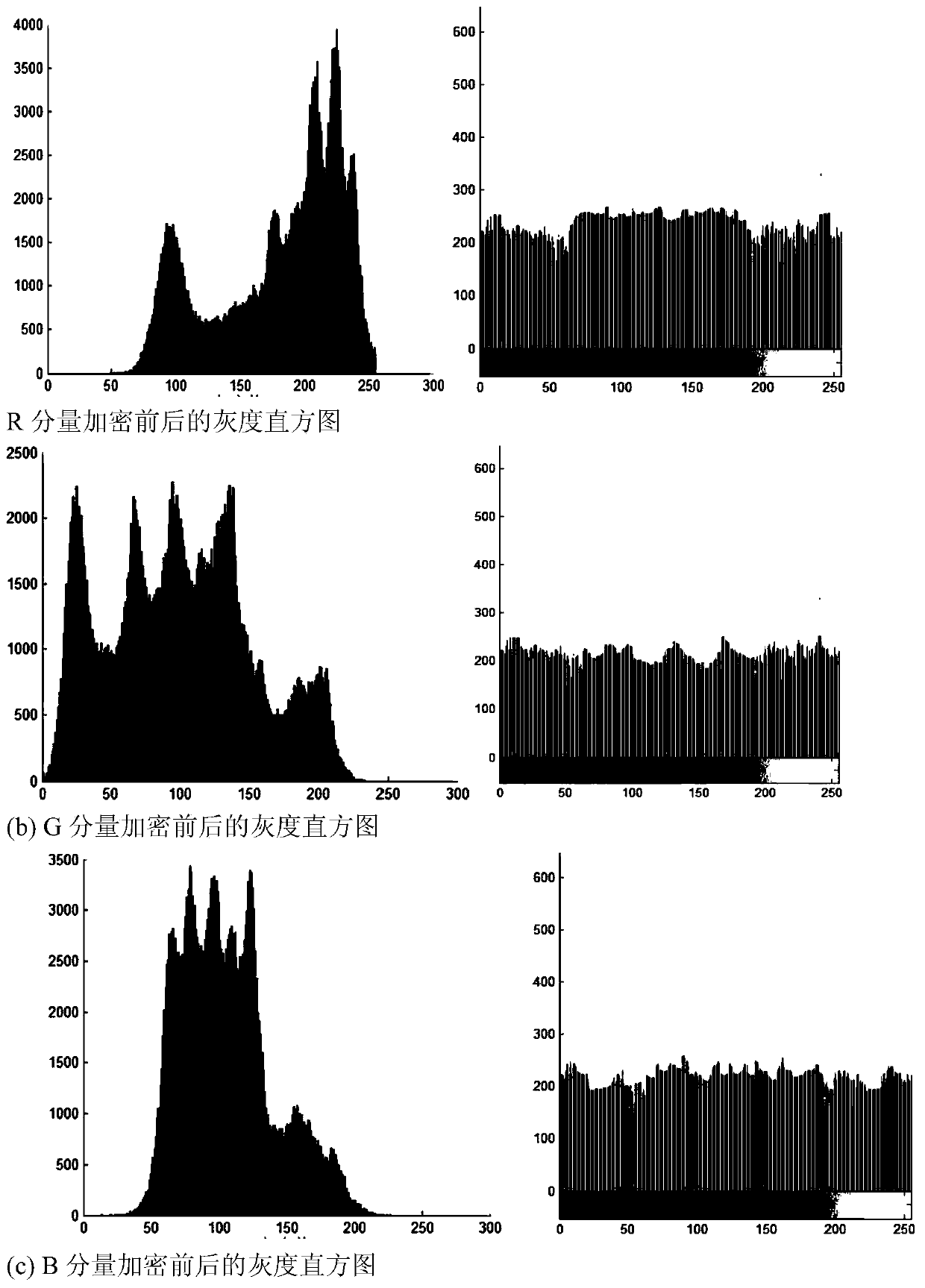
[0013] The double-chaotic image encryption method based on the characteristics of the plaintext itself in this embodiment can process the plaintext image into a ciphertext image, and the encryption method includes scrambling the image pixel positions of the plaintext image and bit bits of the image pixel values scramble.
[0014] Wherein the scrambling of the image pixel position and the bit scrambling of the image pixel value include:
[0015] Step1 separates the three primary colors of the plaintext image, and stores the pixel values of the RGB three primary colors into three two-dimensional arrays of R[m][n], G[m][n], and B[m][n] respectively Inside, the number of iterations N is calculated using the sum of all color components of the original graphic and m, n:
[0016] N=mod(sum,256)+m+n (3);
[0017] Step2 uses the key key1 as the initial value of the Chebyshev chaotic system to iterate the Chebyshev mapping;
[0018] Step3 takes the value after N iterations as the i...
Embodiment 2
[0028] Through the chaotic system, the global scrambling of the pixel position of the plaintext image is performed, and then the pixel value diffusion operation is performed to change the pixel value, so as to achieve the encryption of the plaintext image. The encryption process can be mainly divided into the following two steps: first, image pixel position scrambling; second, image pixel value bit position scrambling. Specific steps are as follows:
[0029] 1. Image position scrambling
[0030] Step1 separates the three primary colors of the plaintext image A, and stores the pixel values of the RGB three primary colors into the three two-dimensional R[m][n], G[m][n], and B[m][n] respectively. In the array, use the sum of all color components of the original graphics and m, n to calculate the number of iterations N by formula (3).
[0031] N=mod(sum,256)+m+n (3)
[0032] Step2 uses the key key1 as the initial value x of the Chebyshev chaotic system 0 , the parameter k=6 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com