Role-based permission control mechanism
A role and mechanism technology, applied in the field of role-based access control, can solve the problems of access and authorization difficulty, database resource management and authorization complexity, etc., to reduce burden and cost, ensure security, and maximize flexibility Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
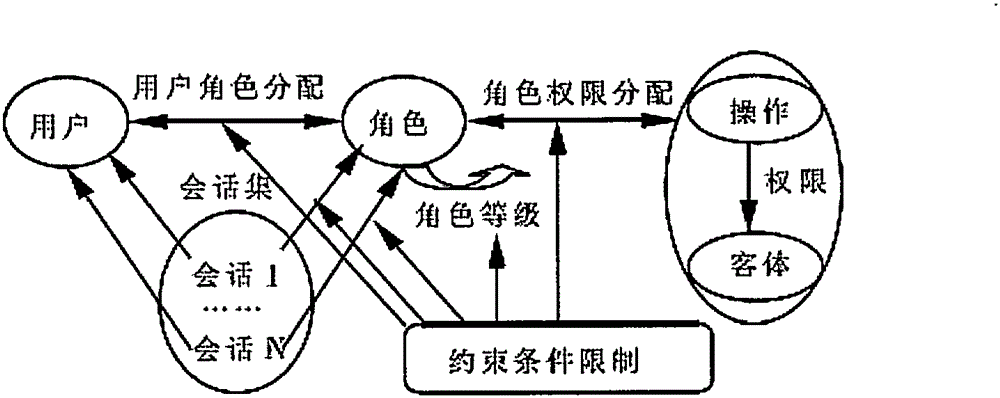
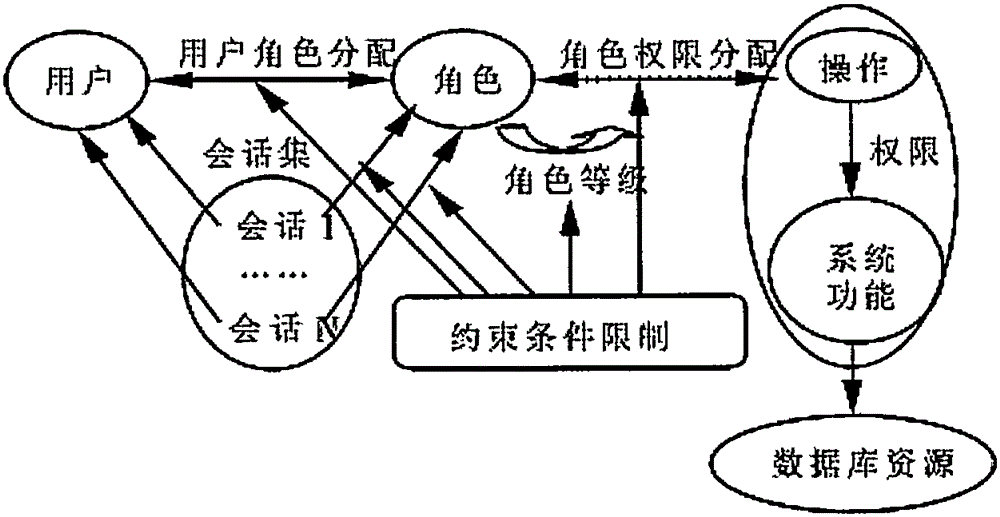
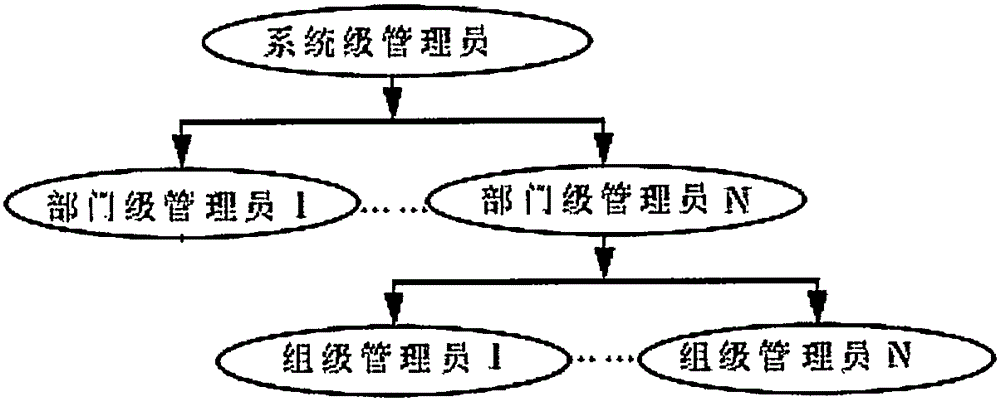
[0015] exist figure 1 In , all entities and steps of the role-based access control model are represented. The role-based access control model sets a new entity-role between users and permissions. Roles serve as an intermediary to connect user collections and authority collections, and users access database resources indirectly through roles. The association between a role and permissions can be regarded as a set of permissions owned by the role, and the association with users can be regarded as a collection of several users with the same identity. A user can be assigned multiple roles, and a role can also be assigned multiple users. There is a many-to-many relationship between users and roles. Similarly, a role can have multiple permissions, and a permission can also be assigned to multiple different roles. There is also a many-to-many relationship between roles and permissions. A user who logs in to the database application system can judge the database resources he can ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com