Method for monitoring suspicious fund transaction based on fund network
A network monitoring and transaction technology, applied in finance, structured data retrieval, instruments, etc., can solve the problems of inability to monitor the fund network, high false alarm rate, and single monitoring dimension, so as to enrich materials and means and improve accuracy Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
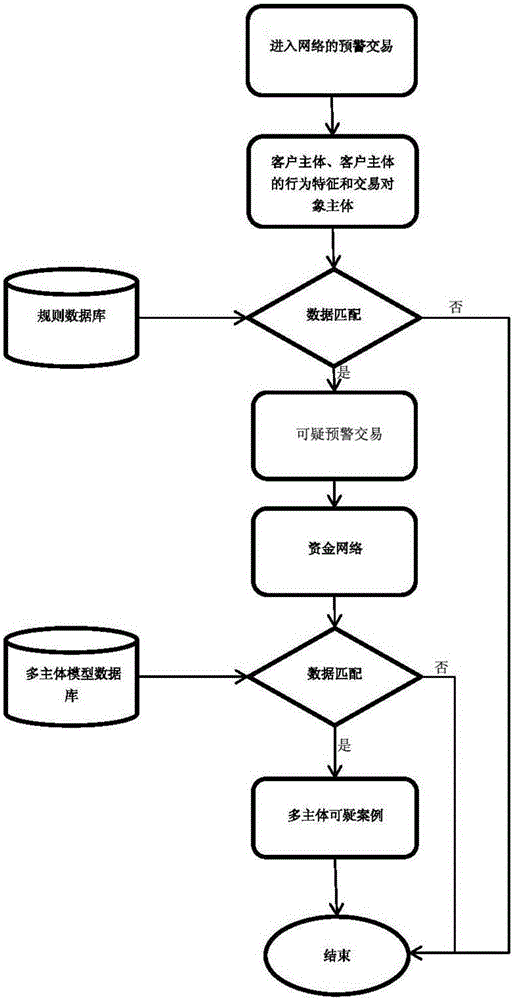
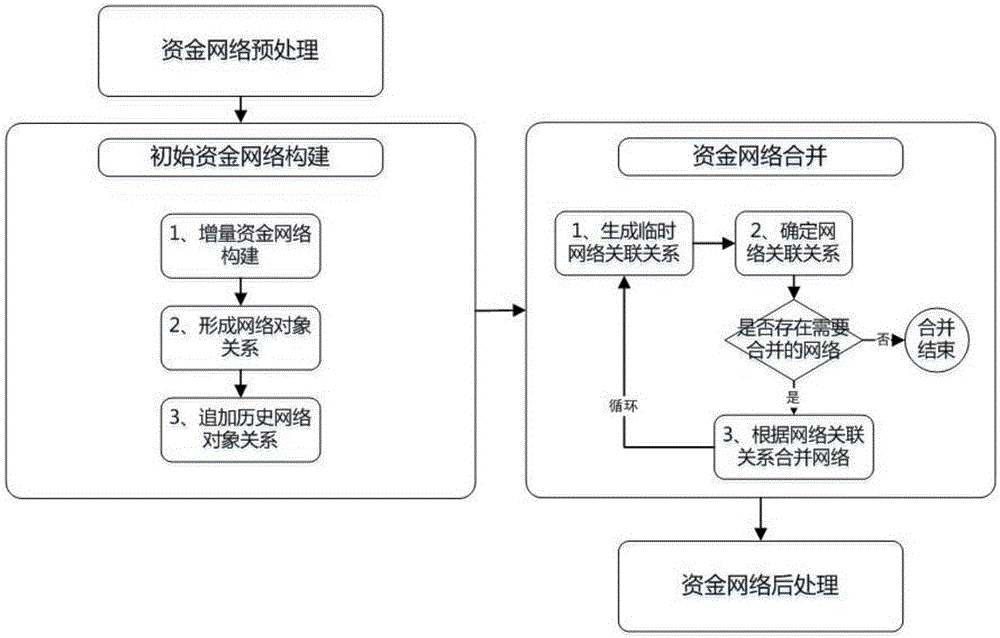
[0026] Attached below figure 1 , figure 2 And embodiment the present invention is described in further detail.
[0027] A method for monitoring suspicious capital transactions based on a capital network, comprising the following steps:
[0028] (1). Establish a rule database and a multi-subject model database. The rule database includes suspicious money laundering rules stipulated in anti-money laundering laws and regulations. The multi-subject model database includes the roles of multiple associated transaction subjects in specific money laundering cases, and each transaction The behavioral characteristics of the subjects and suspected money laundering rules violated by each transaction subject.
[0029] Based on the People's Bank of China's 2006 Order No. 2 "Administrative Measures for Financial Institutions' Large-value and Suspicious Transaction Reports", for 4 large-value and 18 suspicious rules, a rule database can be built by digitizing, based on years of financial i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com