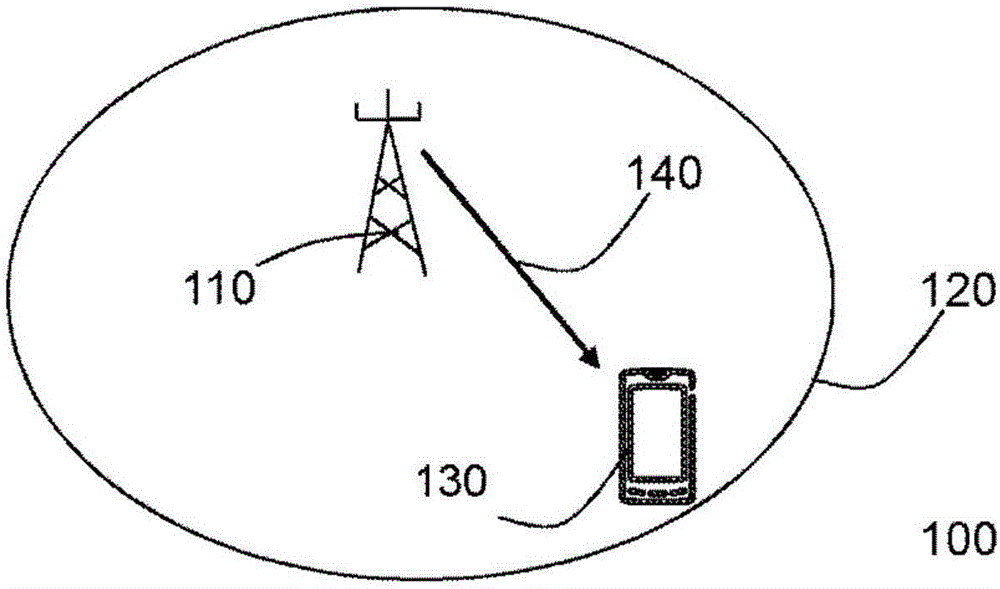
Wireless device, network node, and methods therein for sending message comprising indication of restriction of the wireless device
A technology for wireless devices and network nodes, applied to computer-readable storage media, to determine the restricted areas of the first device, and to solve problems such as communication failures and inability to handle authorization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0103] Embodiment 1: The T type field is introduced into the sub-header of the CCCH SDU in Msg3.
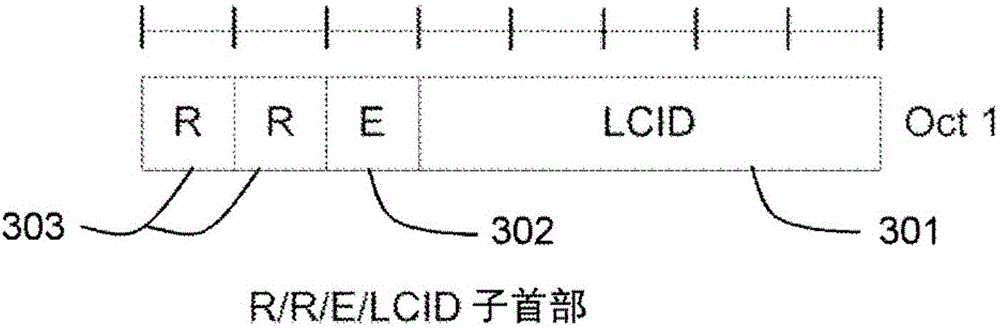
[0104] In the first embodiment, one or both of the two reserved bits R in the MAC PDU subheader of the CCCH SDU in Msg3 may be used to send an indication of TBS restriction. In this embodiment, LCID=00000 for UL-SCH can be used, which explicitly indicates CCCH on UL-SCH. Figure 7 It is a schematic diagram showing the minimum possible Msg3 authorization using two examples a) and b) of the first embodiment. Example a) is an RRC connection request, and example b) is an RRC connection reestablishment request.
[0105] The MAC subheader corresponding to the CCCH SDU in Msg3 of the first embodiment may include the following fields:
[0106] LCID: logical channel ID field 701, LCID=00000 can identify the logical channel CCCH.
[0107] -E: Extension field 702, may be set to "0", indicating that there are no more fields in the MAC header. MAC SDU 703 corresponding to CCCH may start a...
Embodiment 2
[0115] Embodiment 2: Using the LCID value indicating the BSR in Msg3 for CCCH access
[0116]In the second embodiment, the normal LCID field currently available to indicate the CCCH content in Msg3 for CCCH access may not be used. Alternatively, in this embodiment, any one of the BSR LCIDs for UL-SCH, ie, LCID=11100, 11101 or 11110, may be used, thereby also indicating one of the truncated BSR, short BSR or long BSR. In the specific case of Embodiment 2, Msg3 may be sent as part of RRC connection establishment, that is, when buffers or logical channel groups may not yet be defined. Therefore, the normal meaning of BSR may not be valid, and instead it may be used by low-complexity UEs to simultaneously indicate CCCH on UL-SCH as well as TBS restriction. The MAC control element may not be required, and the actual buffer status report may not be valid. Also, no more bytes from the MAC control element may be needed as this may increase the message size. Therefore, in some embod...
Embodiment 3
[0125] Example 3: New LCID
[0126] In a third embodiment, a new LCID for UL-SCH may be allocated with respect to an existing LCID. The new LCID can be used by low-complexity UEs to indicate both CCCH on UL-SCH and TBS restriction. Figure 9 is a schematic diagram showing the case of the smallest possible Msg3 grant according to Embodiment 3 using LCID values in the range of Msg3 for CCCH access. The smallest possible Msg3 authorization is 7 bytes. Figure 9 Two non-limiting examples a) and b) are shown, but the embodiments here apply to Msg3 of any available size. Example a) is an RRC connection request, and example b) is an RRC connection reestablishment request. as in Figure 9 It can be understood from the example in the example that the MAC header of Msg3 for CCCH access corresponding to the third embodiment may include the following fields:
[0127] - LCID: Logical Channel ID field 901, some LCIDs are in the range of 00001 to 11001, can be used to indicate that th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com