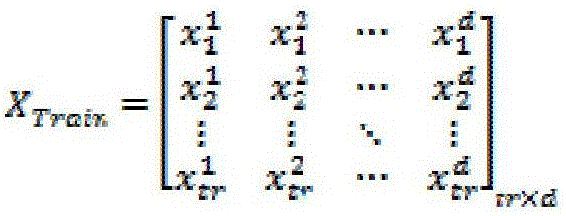Dynamic self-adapting wireless sensor network invasion detection intelligence algorithm
A network intrusion detection, wireless sensor technology, applied in network topology, wireless communication, transmission system and other directions, can solve problems such as difficulty in adapting to different network structures, limiting the application scope of detection modes, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
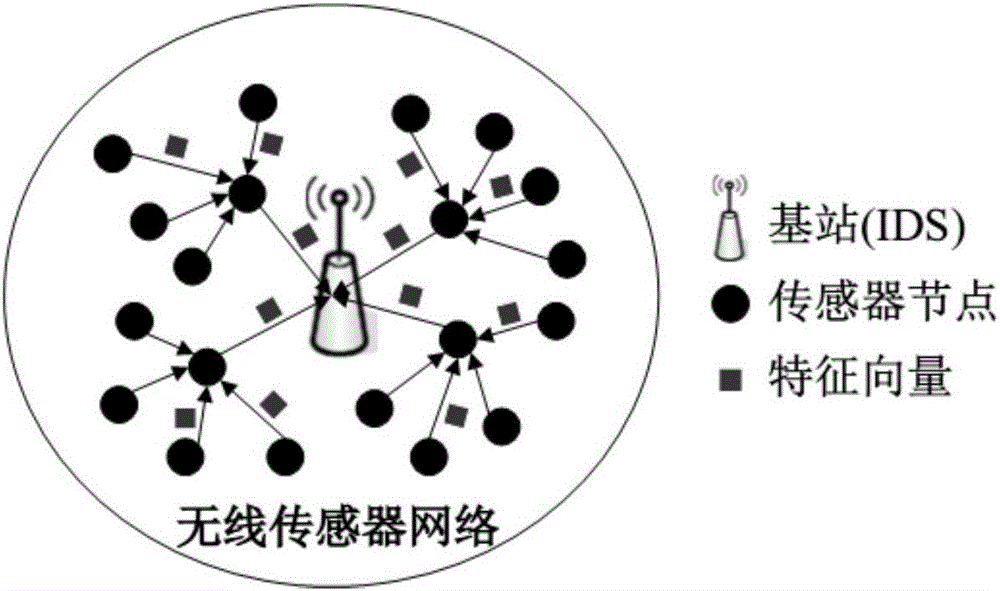
[0064] figure 1 is the structure diagram of the wireless sensor network of the present invention, the network node sends its status information (feature vector) to the base station every other time gap Δt, and the base station divides the received feature vector set into training data and test data at time point m, time The set of feature vectors in [0,n] is normal data.
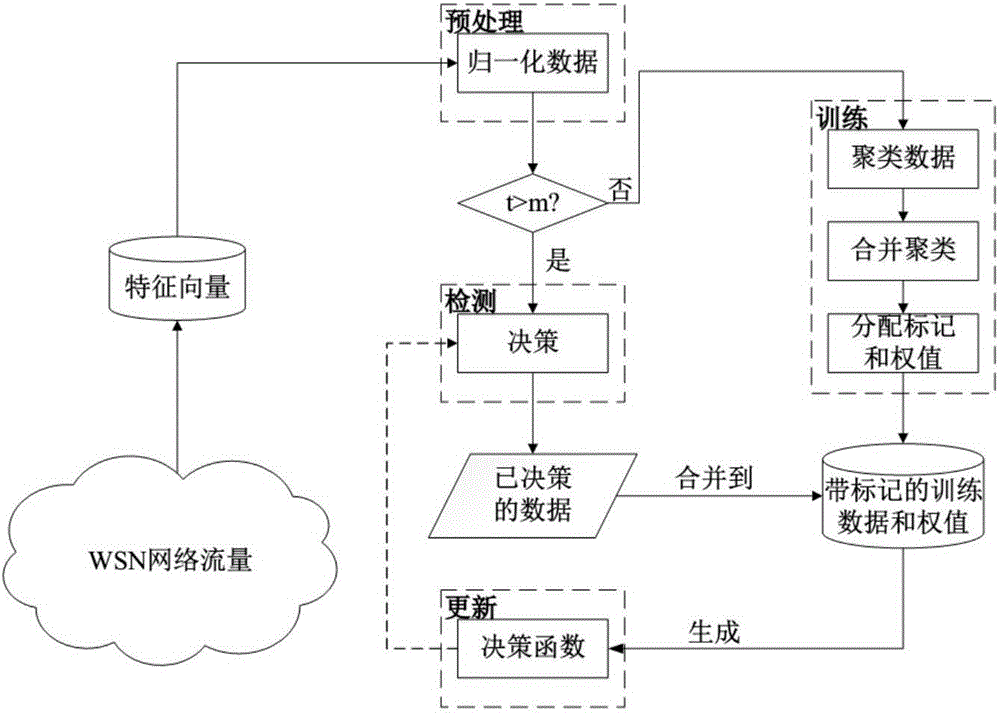
[0065] figure 2 Be the algorithm flowchart of the present invention, as shown in the figure, mainly comprise the following steps:
[0066] Preprocessing: The min-max normalization method is used to normalize the network features.
[0067] Training: The training data is clustered into multiple clusters by the mean shift algorithm, and merged into two clusters according to the relative distance between the cluster centers. Mark these two clusters as normal or abnormal ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com