Method and device for unlocking terminal
A technology for unlocking devices and terminals, applied in the fields of instruments, digital data authentication, electrical digital data processing, etc., can solve the problems of easy observation and identification, high cost, complicated terminal unlocking methods, etc., and meet the requirements of clear and simple unlocking steps and operation accuracy. The effect of low and low learning cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
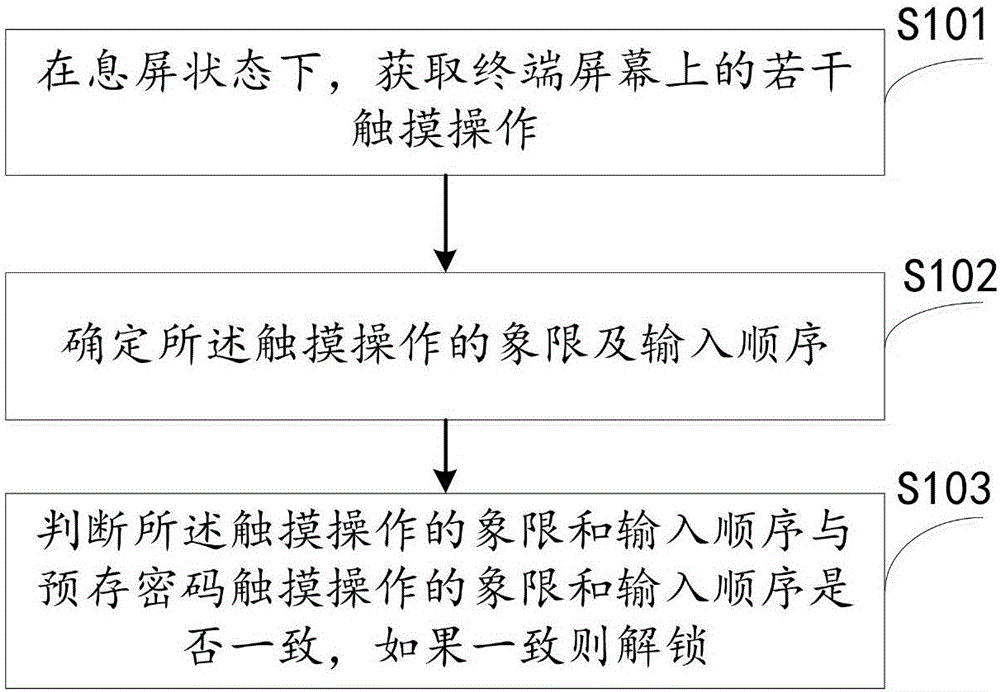
[0080] The first embodiment of the present invention provides a terminal unlocking method, such as image 3 As shown, including the following steps:
[0081] S101: Acquire several touch operations on the terminal screen in the screen rest state;
[0082] Stop screen, that is, the terminal is in a standby state where the screen is not lit. For example, when a specific start key is pressed, the screen can be lit, and some applications can be started in a non-unlocked state. In the rest screen state, the sensors of the terminal are still working, such as gravity sensors and pressure sensors, which provide technical conditions for unlocking the rest screen.
[0083] Monitor the user's touch operation when the terminal is on the screen. The touch operation includes the most basic single click, and may also include other touch operation actions, such as double-clicking, sliding, and sliding in a specific direction and a specific length. In the present invention, it is preferable to click...
Embodiment 2
[0093] The second embodiment of the present invention provides a terminal unlocking method, such as Figure 4 As shown, including the following steps:
[0094] S201: In the screen rest state, obtain a continuous touch point on the screen, divide the four quadrants of the screen with the horizontal and vertical coordinate lines of the continuous touch point, and obtain several touch operations in the four quadrants;
[0095] Compared with the first embodiment, this embodiment provides a new quadrant division method, such as Picture 10 As shown, the upper left vertex of the definition screen is the origin of coordinates (0,0), the upper right vertex coordinates (a,0), the lower left vertex coordinates are (0,b), the lower right vertex coordinates are (a,b), when the screen is on When there is a continuous touch point that lasts longer than the set time, it is assumed that the user wants to switch the terminal to the use state, then the coordinates (c, d) of the point are obtained, wh...
Embodiment 3
[0109] The third embodiment of the present invention provides a terminal unlocking method, such as Figure 5 As shown, including the following steps:
[0110] S301, preset the input sequence and quadrants of a number of touch operations in the four quadrants of the screen as the unlocking password;
[0111] When the touch operation password is preset, the terminal screen is the default four quadrants divided by the horizontal axis and the vertical axis where the midpoint of the diagonal is located. The user clicks on the quadrants in a certain order within the four quadrants according to their own wishes and chooses to save, then the inputted quadrants and sequence corresponding to the quadrants are used as the preset unlock password. This step can also be set in the technical solutions provided in the first and second embodiments.
[0112] S302. In the screen rest state, obtain the first touch point and the second touch point on the screen, and divide the four quadrants of the scre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com