IO sequence-based virtual machine abnormal behavior detection method and system
A detection method and virtual machine technology, applied in the field of virtualization security, can solve the problems of performance loss, complex security threats, frequent read and write operations, etc., and achieve the effect of reducing performance loss and protecting security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described in detail below with reference to the drawings and specific embodiments.
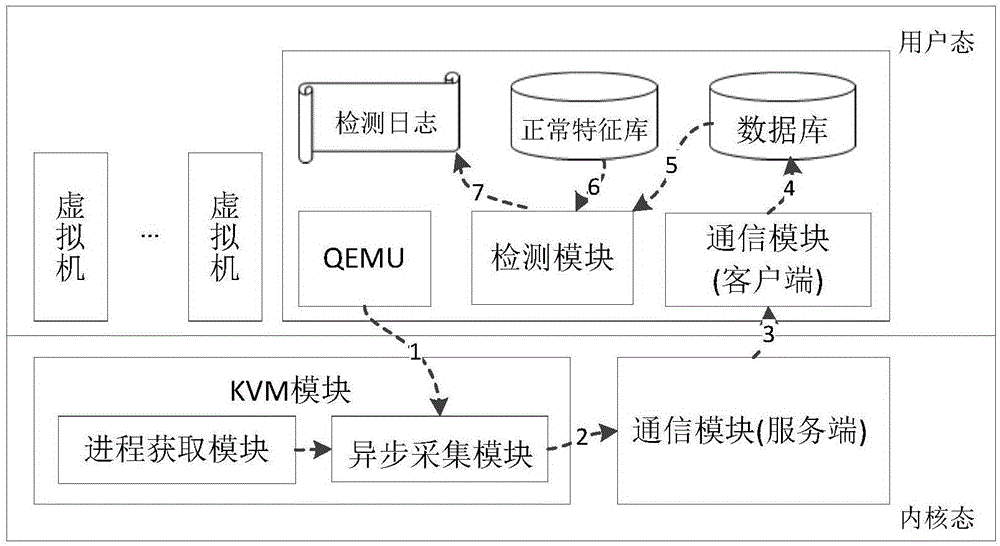
[0030] Attached figure 1 The overall architecture diagram of the KVM (Kernel-based Virtual Machine) virtual machine abnormal behavior detection system based on the IO sequence in the present invention is given. Such as figure 1 As shown, the system can be used to detect malicious behaviors in virtual machines and prevent known virtual machine escape attacks in time, including an asynchronous collection module, a process acquisition module, a communication module, and a detection module.
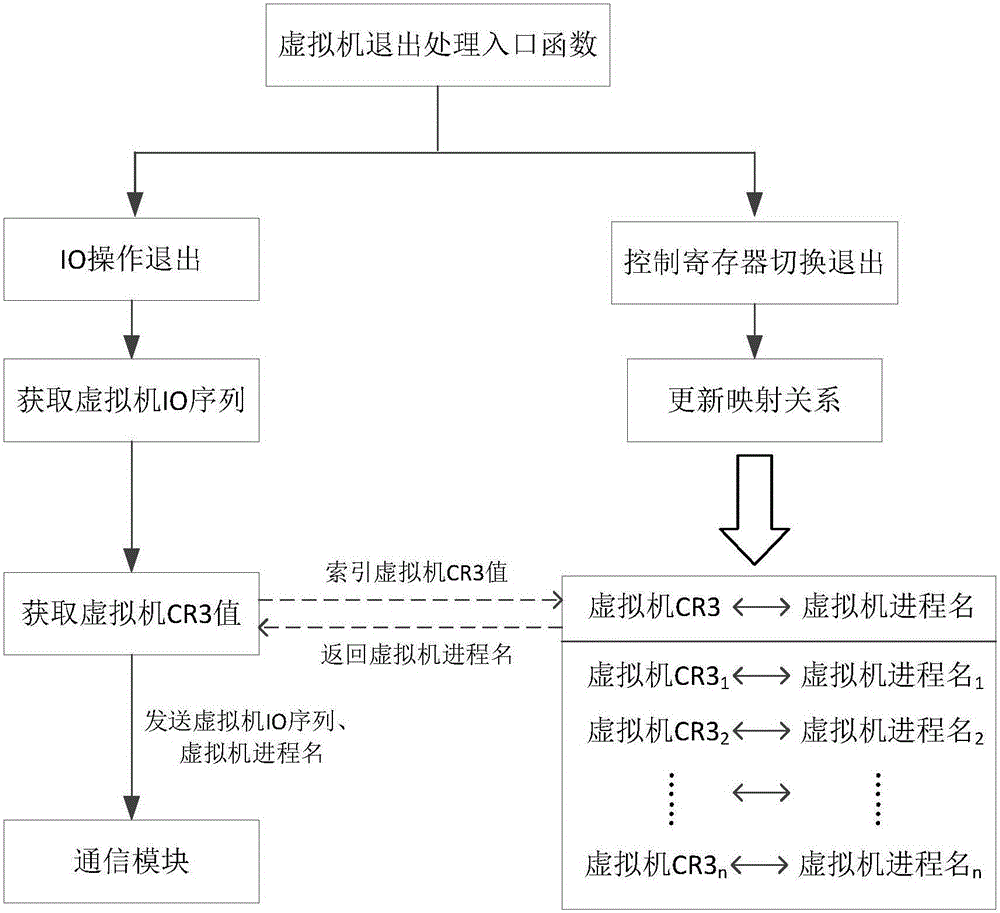
[0031] The asynchronous acquisition module intercepts the virtual machine I / O simulation operation, extracts the required virtual machine IO sequence and saves it in the data buffer area, wakes up the custom kernel thread located in the communication module, and restores the normal execution flow of the VMM.
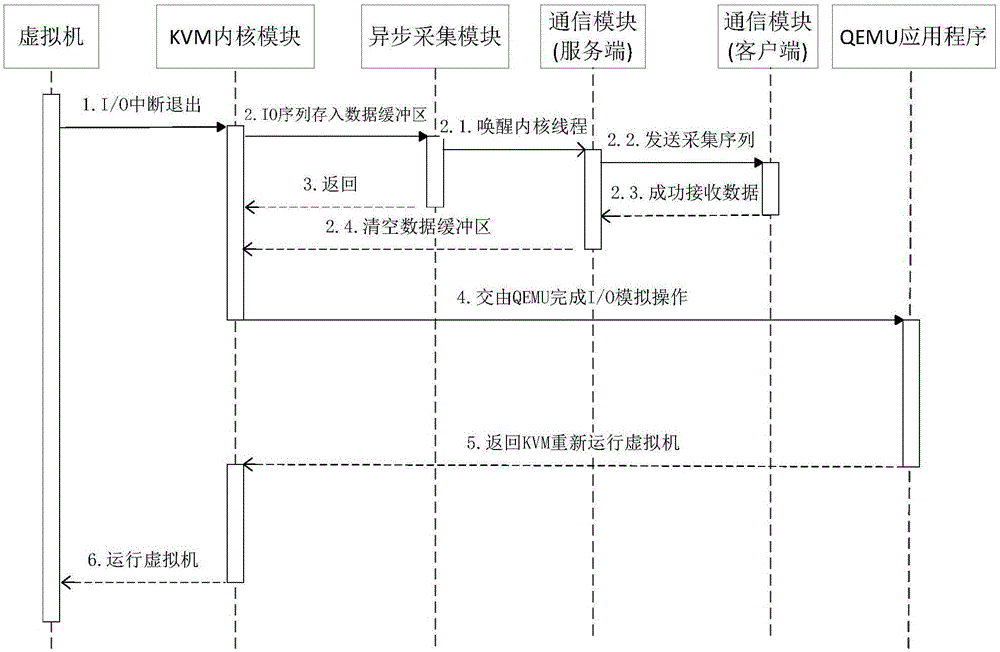
[0032] Attached figure 2 The timing diagram of the asynchrono...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com