Method and device for detecting baleful programs
A malicious program and program technology, applied in the computer field, can solve problems such as the inability to detect and exploit unknown privilege escalation security vulnerabilities, and inability to solve advanced threats, etc., to achieve the effect of improving the detection success rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
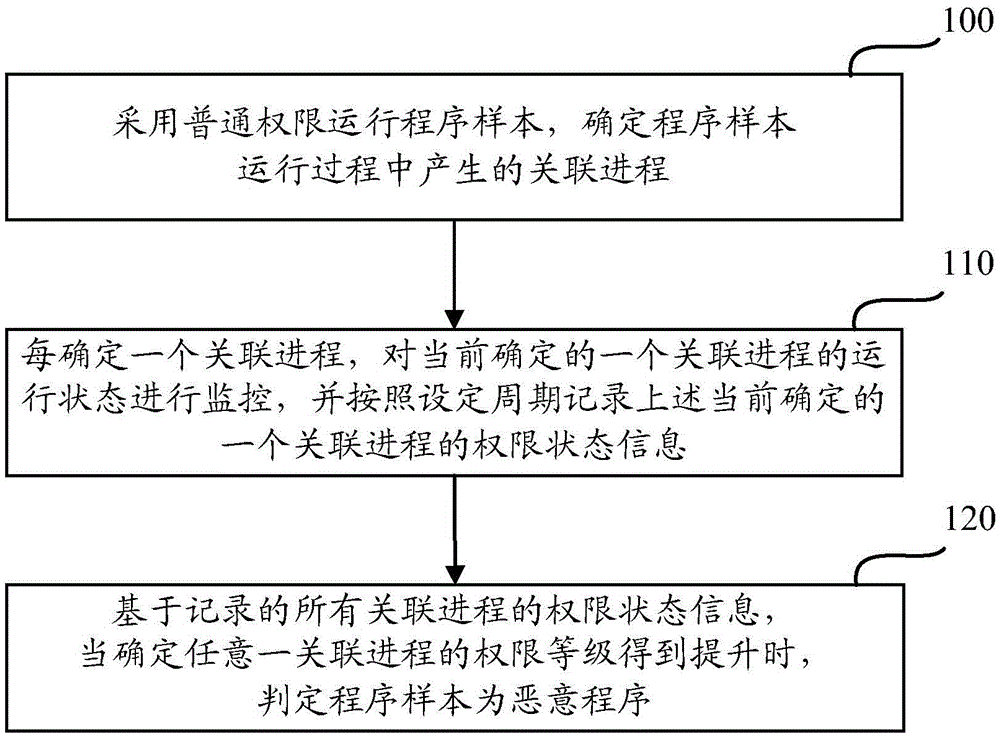
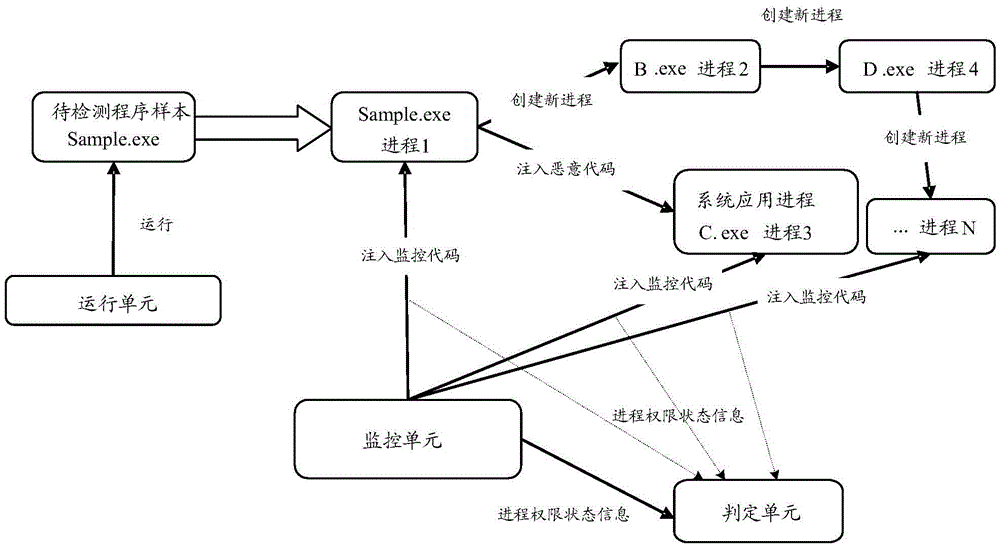
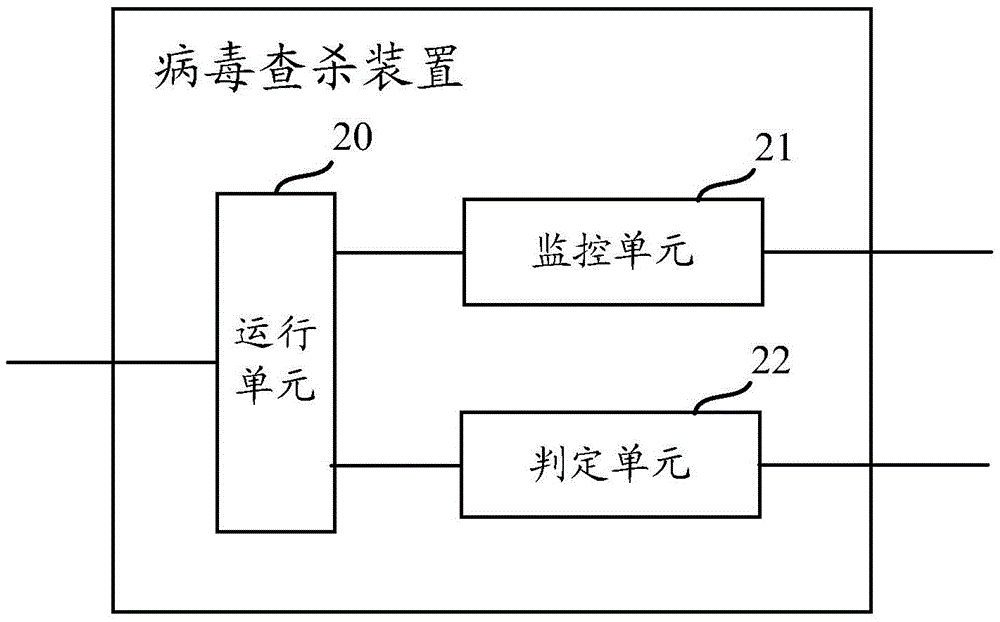
[0042] Preferred embodiments of the present application will be described in detail below with reference to the accompanying drawings.
[0043] Currently, the latest operating systems such as windows, linux, etc., implement the permission division mechanism, and ordinary users can only use the default permissions (usually ordinary permissions, not high permissions), which can meet the daily use needs, and the running program needs When the authority is high, the user is required to confirm or enter a password, so as to ensure that the computer system is not damaged by malicious programs. For example, in Windows 7, by default, ordinary users do not have administrator privileges. When running a program that requires administrator or System privileges, a User Account Control (UAC) prompt box will pop up, prompting the user to enter a password or perform a confirmation operation. The same is true for the Linux system. It is recommended that general users use non-root privileges an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com