Risk identification and business processing method and device
A technology for risk identification and business processing, applied in the field of network information security, can solve the problem of low risk identification accuracy, and achieve the effect of improving security and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
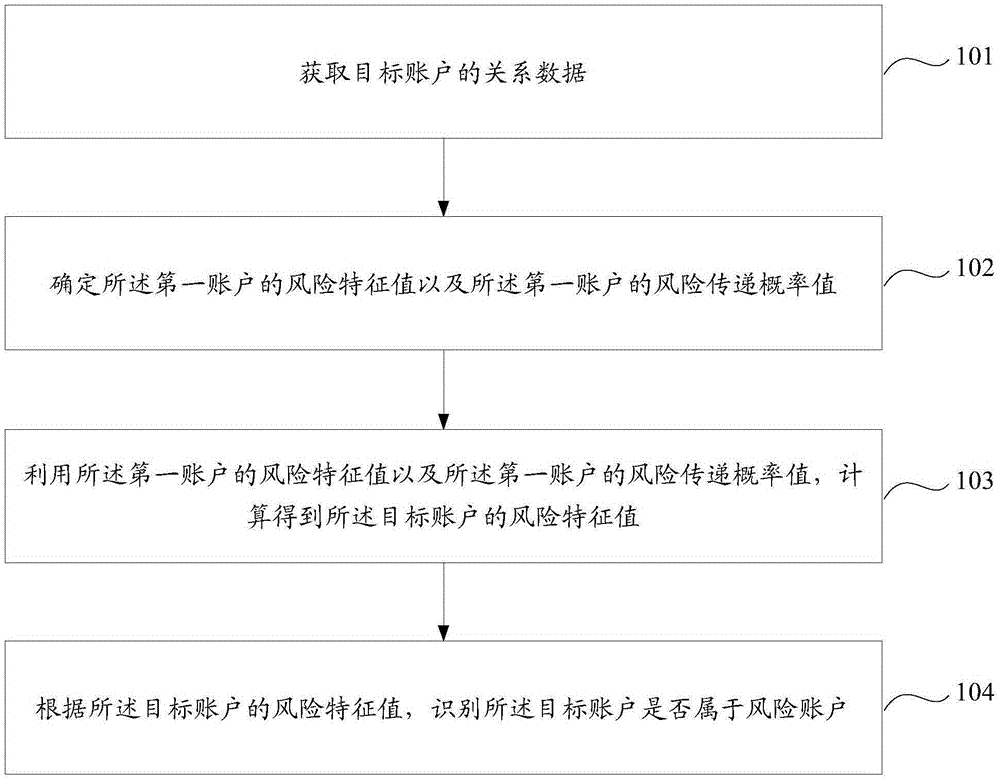
[0038] With the increasing complexity of the Internet network environment, some illegal users use the Internet platform to perform illegal operations to seek illegal benefits, which not only damages the interests of other users, but also brings great inconvenience to network service providers. In order to ensure a safe and orderly network environment, the server uses a blacklist method or a rule method to identify whether the user's account is a risk account.
[0039] For example: an illegal user has performed an illegal operation using an illegal account A, and the server records the illegal account A in the blacklist. Identify illegal account A in time to prevent illegal users from using illegal account A to perform illegal operations.
[0040] However, if an illegal user has a normal account B and a newly registered account C, since the illegal user has not used account C to perform illegal operations, the server will consider account C to be a safe account and there is no ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com