Terminal permission control method and system
A technology of authority control and control method, which is applied in the field of terminal authority control method and system, can solve problems such as inability to adjust adaptively, and achieve the effect of improving security and usability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
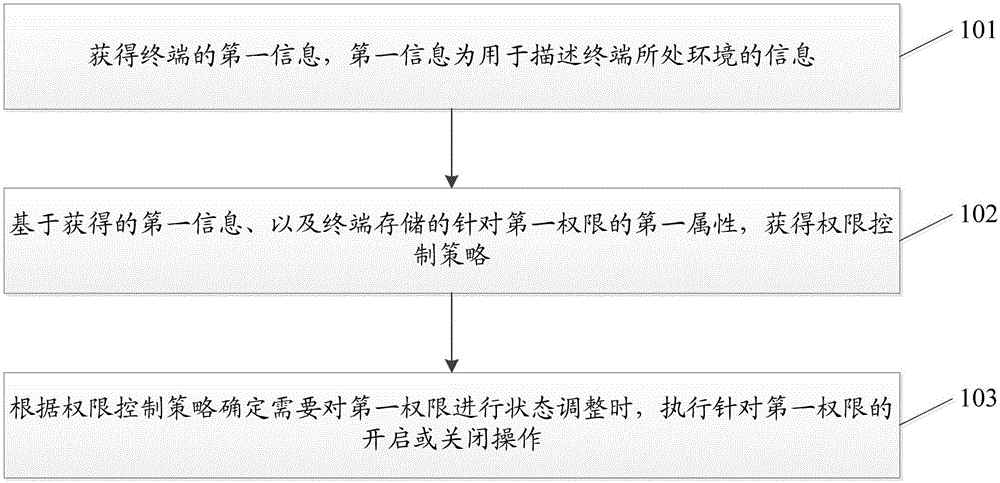
[0046] Embodiment 1 of the present invention provides a method for controlling terminal authority, such as figure 1 As shown, wherein, the first attribute for the first permission is stored in the terminal, the first permission includes at least the system permission and / or application permission of the terminal, and the first attribute is used to describe the first permission Opening and closing conditions of a permission; the method mainly includes:
[0047] Step 101, obtain first information of the terminal, where the first information is information used to describe the environment where the terminal is located.
[0048]In the embodiment of the present invention, the system authority refers to the operation and use authority of various functions of the operating system (such as Android system, Apple's IOS operating system, windows operating system, etc.) of the intelligent terminal, such as the wireless local area network (wifi) of the intelligent terminal. authority, mob...
Embodiment 2
[0074] Corresponding to the terminal authority control method in the embodiment of the present invention, Embodiment 2 of the present invention also provides a terminal authority control system, such as Figure 5 As shown, the system includes: an initialization unit 10, a first information obtaining unit 20, a policy control unit 30 and an authority control unit 40; wherein,
[0075] The initialization unit 10 is configured to store a first attribute for a first permission, the first permission includes at least the system permission and / or application permission of the terminal, and the first attribute is used to describe the first permission opening and closing conditions;
[0076] The first information obtaining unit 20 is configured to obtain first information of the terminal, where the first information is information describing the environment in which the terminal is located;
[0077] The policy control unit 30 is configured to obtain a permission control policy based ...
Embodiment 3
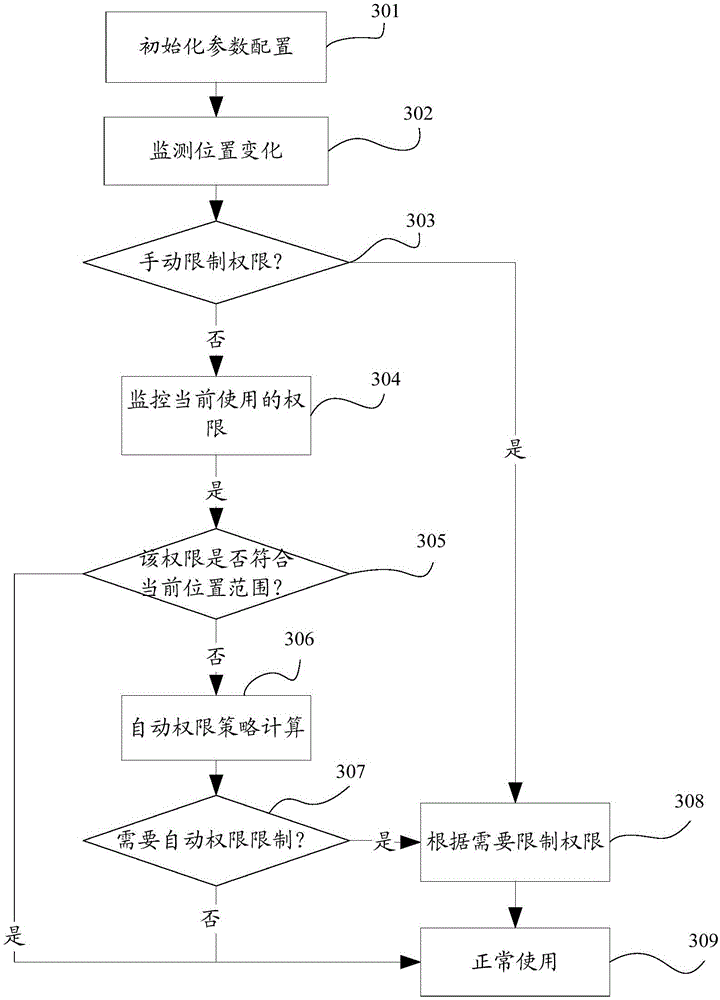
[0098] Considering that in practical applications, end users have different requirements for opening and / or closing system permissions and / or application permissions in the terminal in different geographical locations, such as workplaces, home places or unfamiliar locations; and , end users have certain rules to follow for the opening and / or closing habits of terminal system permissions and / or application permissions, that is, end users usually have the same habit of opening and / or closing permissions in the same location area; then according to the Regularly and adaptively adjust the operation and use rights of applications and systems, which can save users a lot of manual operations, save users time, and improve the operation experience.
[0099] According to the third embodiment of the present invention, the method for controlling the terminal authority based on the change of geographic location, such as image 3 As shown, the method mainly includes:
[0100] Step 301, ini...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com