Patents
Literature
112 results about "Web presence" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A web presence is a location on the World Wide Web where a person, business, or some other entity is represented (see also web property and point of presence). Examples of a web presence for a person could be a personal website, a blog, a profile page, a wiki page, or a social media point of presence (e.g. a LinkedIn profile, a Facebook account, or a Twitter account). Examples of a web presence for a business or some other entity could be a corporate website, a microsite, a page on a review site, a wiki page, or a social media point of presence (e.g., a LinkedIn company page and/or group, a Facebook business/brand/product page, or a Twitter account).
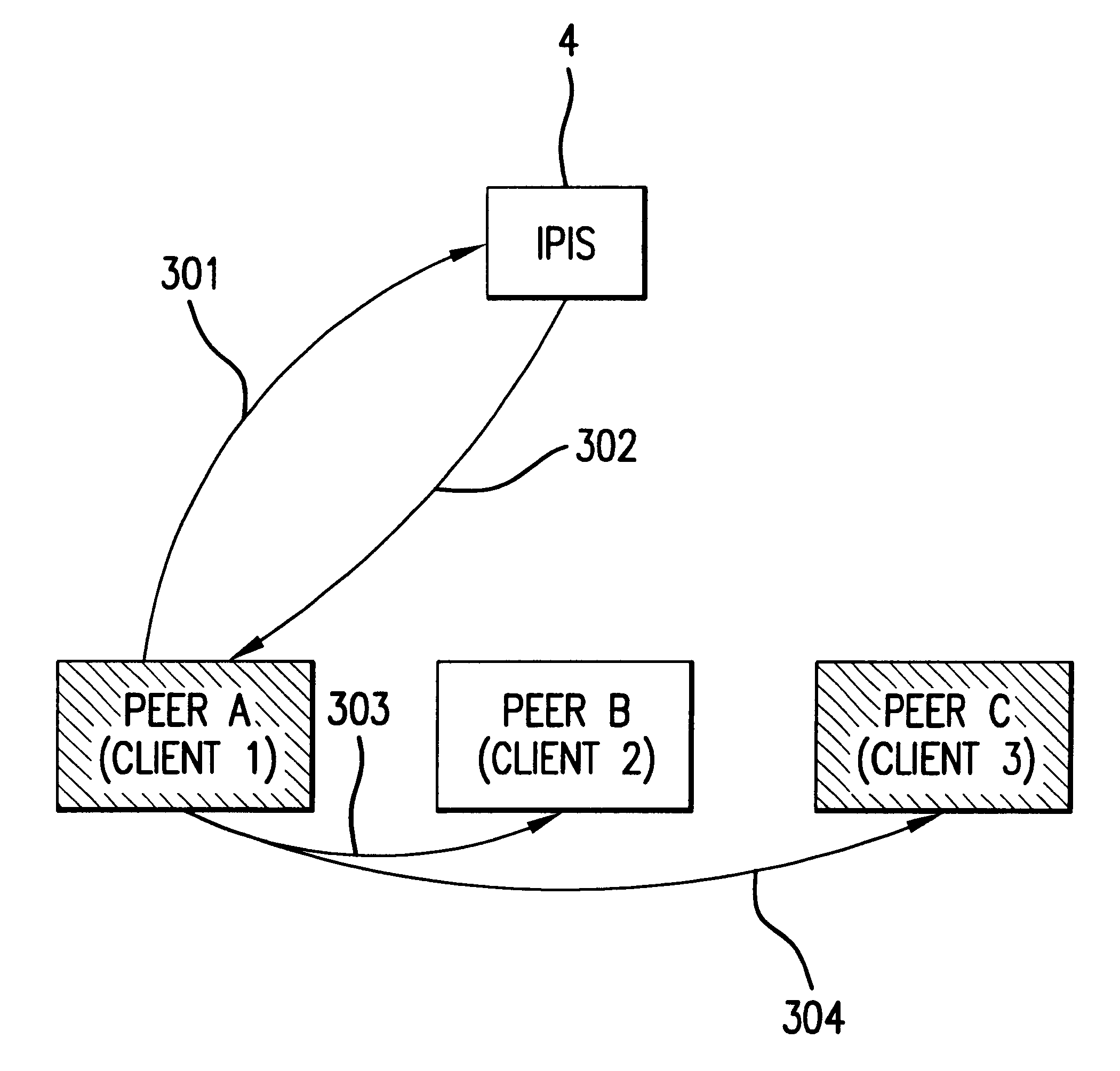
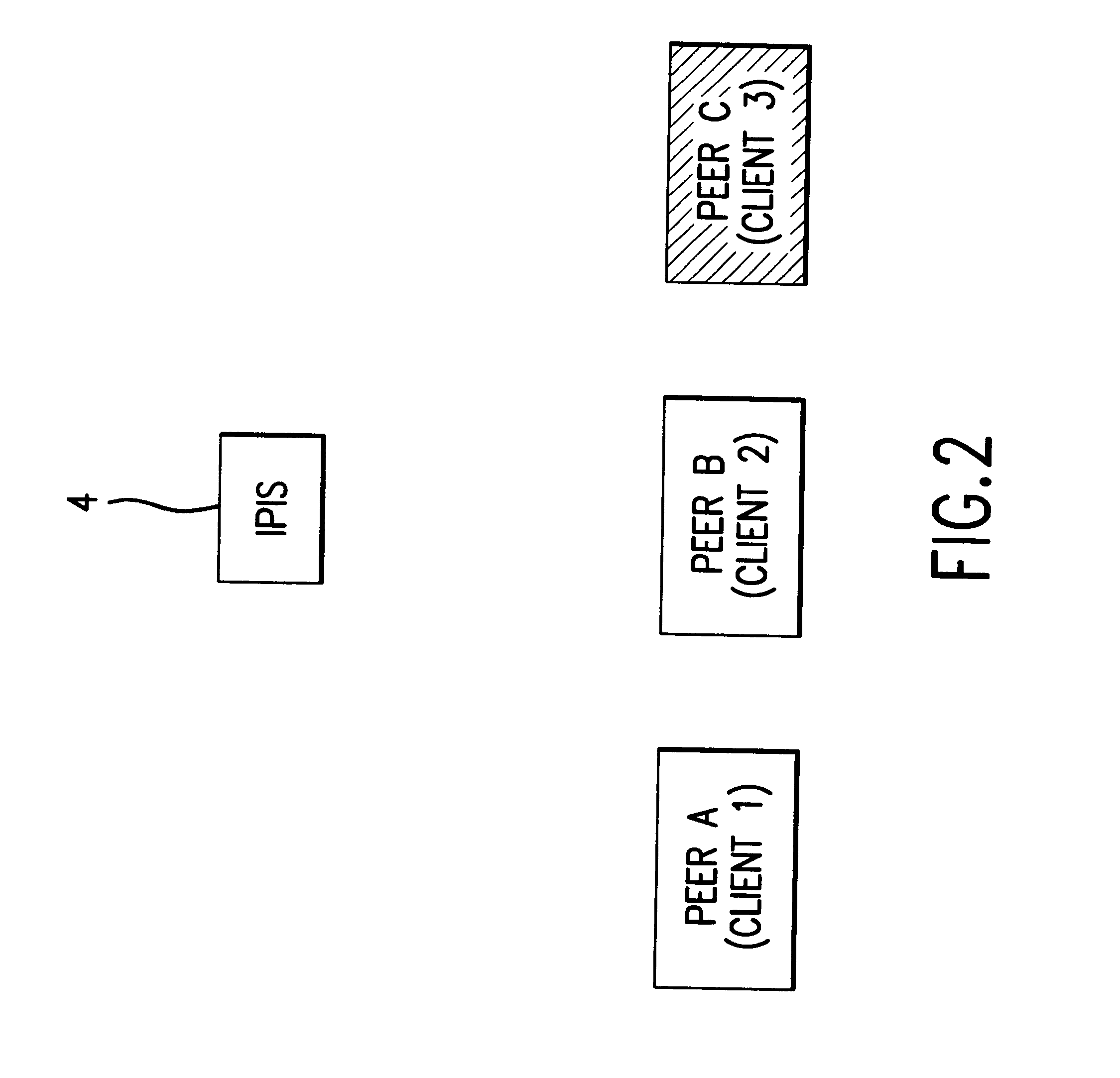
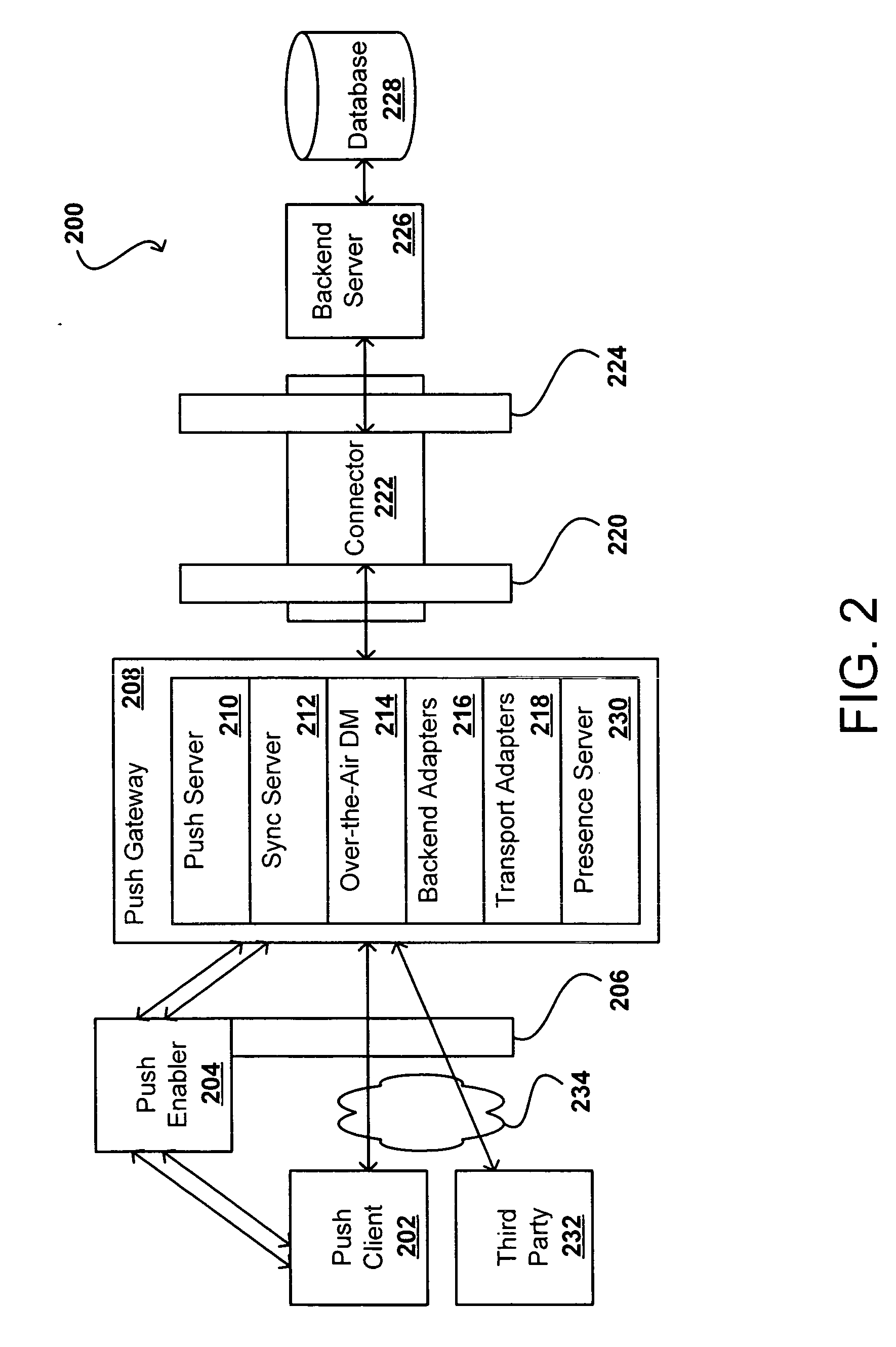
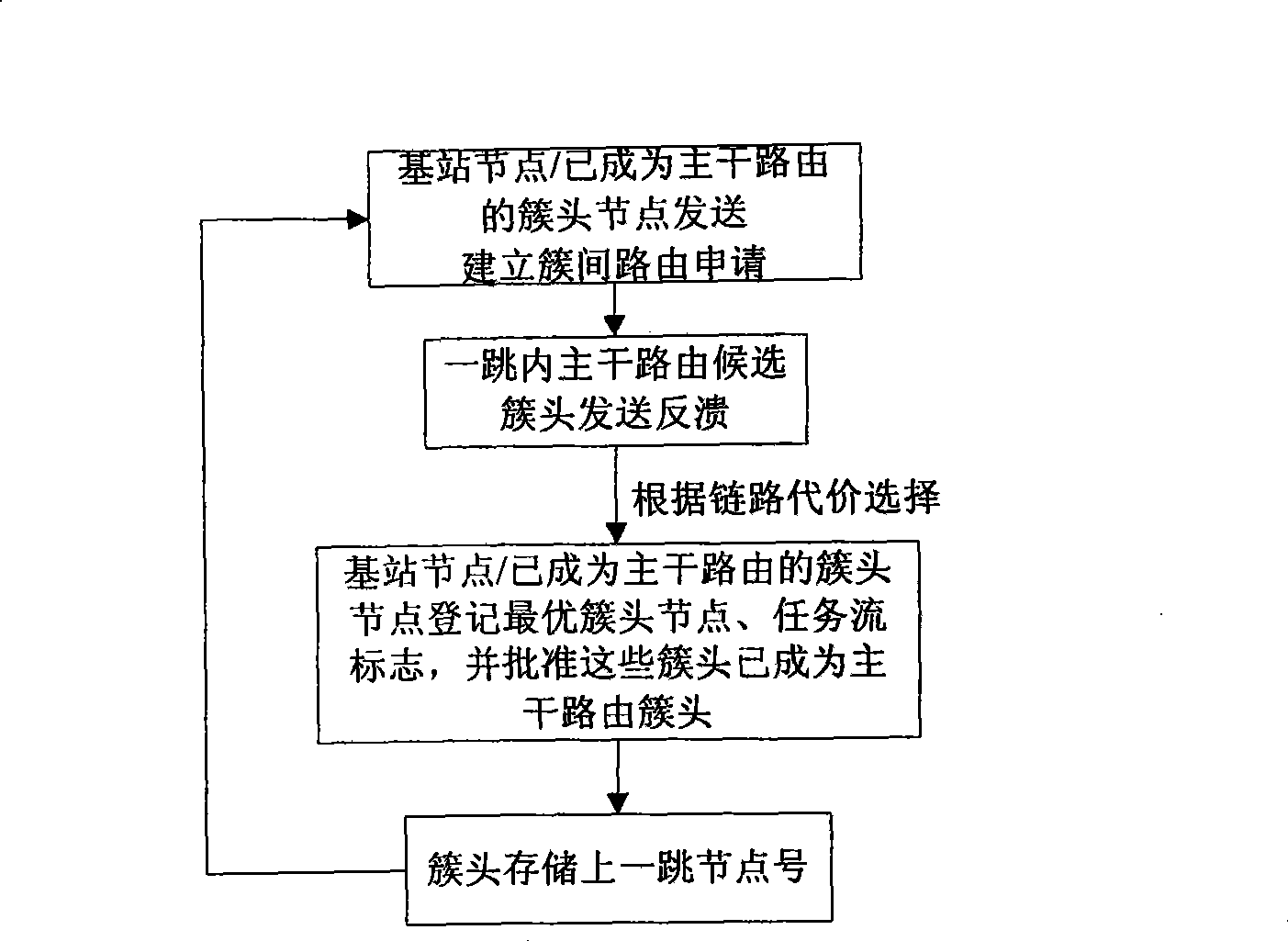
Method and system for validating and distributing network presence information for peers of interest
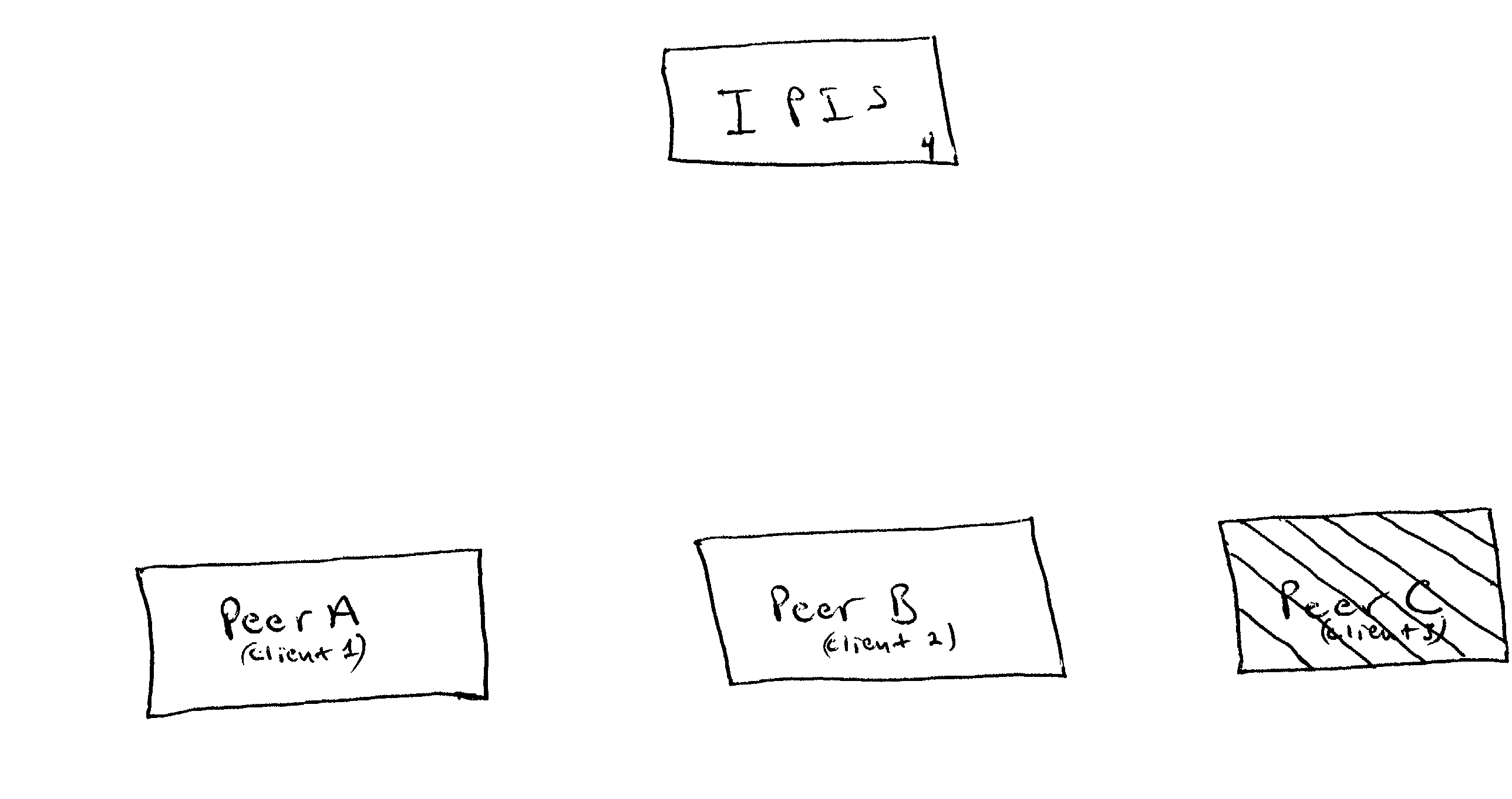
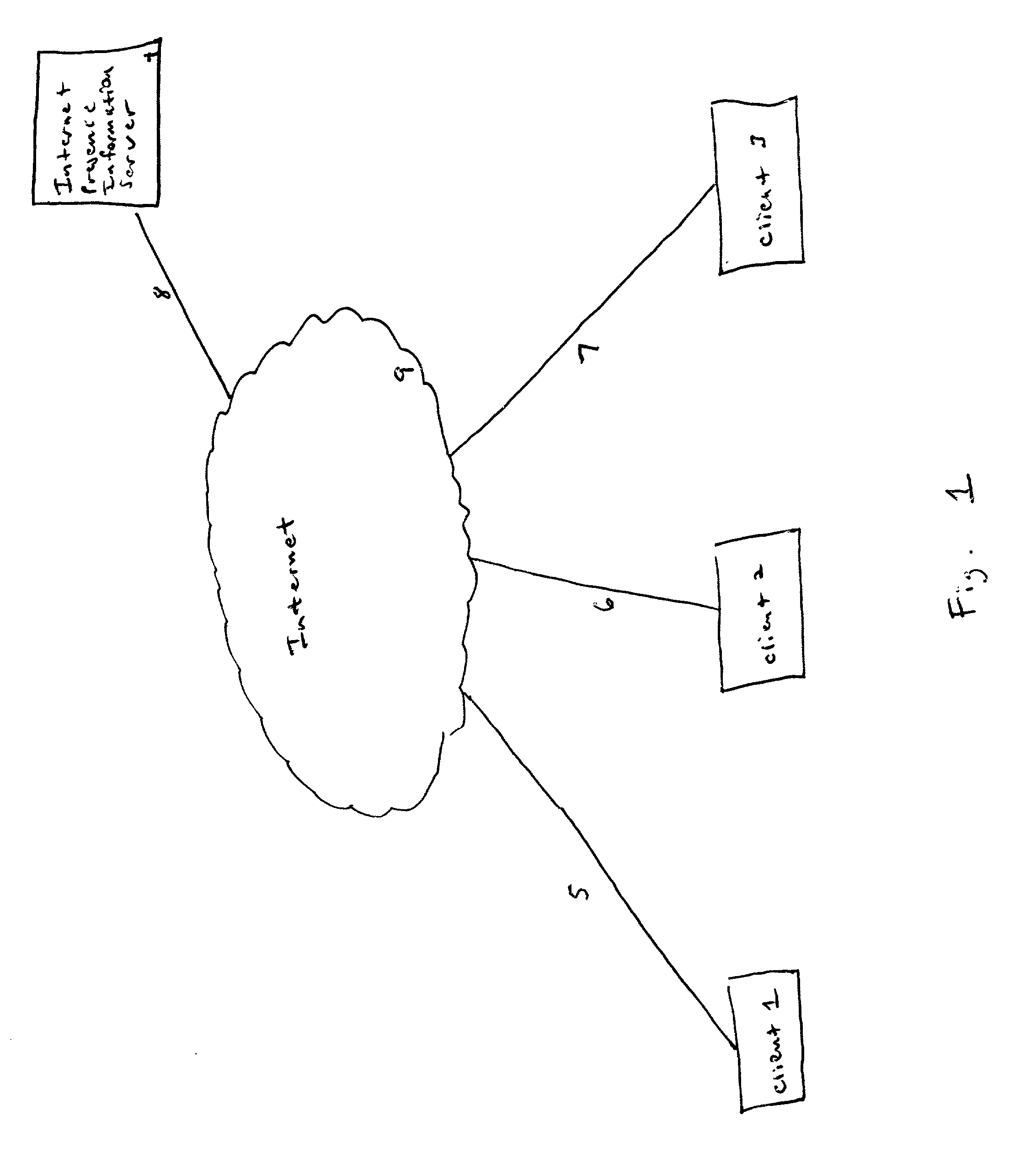
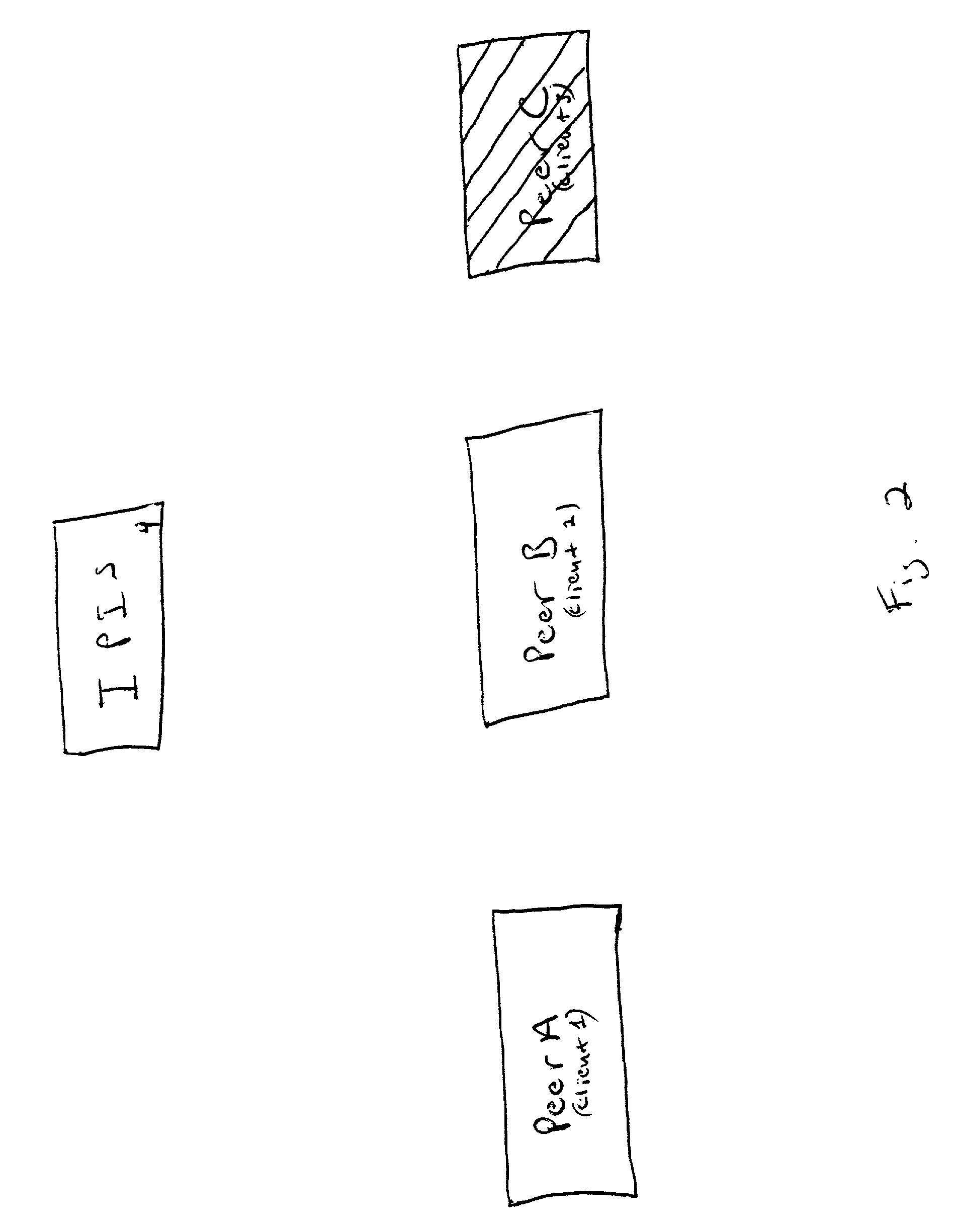
A method for distributing and maintaining network presence information is presented. According to an embodiment of the present invention, a user logs onto the Internet and transmits to an Internet Presence Information Server (IPIS) his / her presence information, a list of peers (individual network users) whose network presence are of interest to the user, and a request for a list of peers interested in the user's network presence. The IPIS then responds to the user with both a list including the last known Internet Protocol (IP) address for each peer the user is interested in and a list of peers interested in the user's Internet presence. No further communication between the user and IPIS is required after the IPIS responds to the user with these two lists. The user then attempts to directly contact the peers on the first list received from the IPIS by confirming and authenticating the received IP addresses. According to policy, the user directly contacts the peers on the second list received from the IPIS to inform those peers the user is currently signed on-line. Finally, the user periodically "pings" (directly contacts) the confirmed and authenticated IP addresses from the first list received from the IPIS to determine when those peers sign off-line.
Owner:INTEL CORP
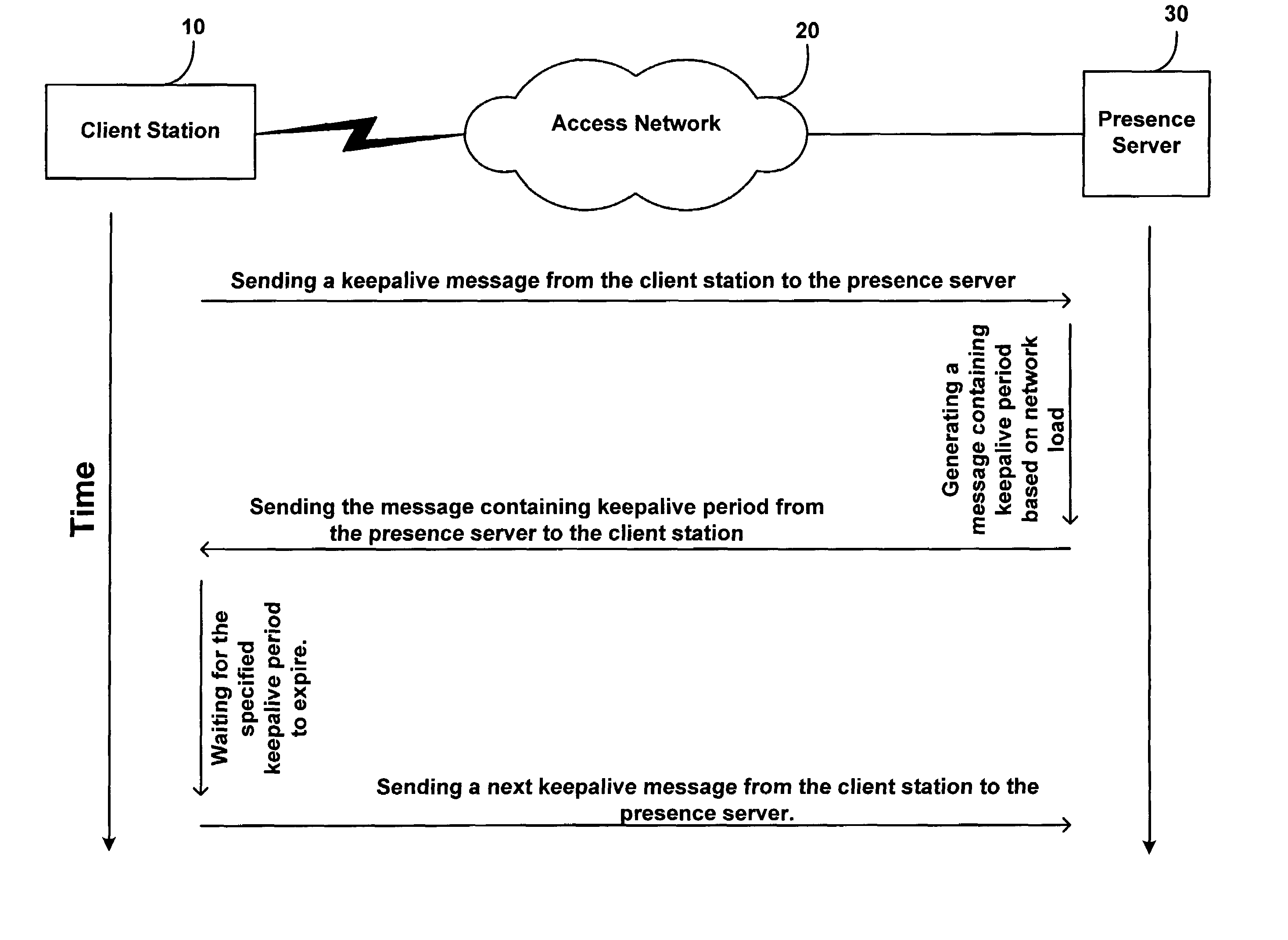
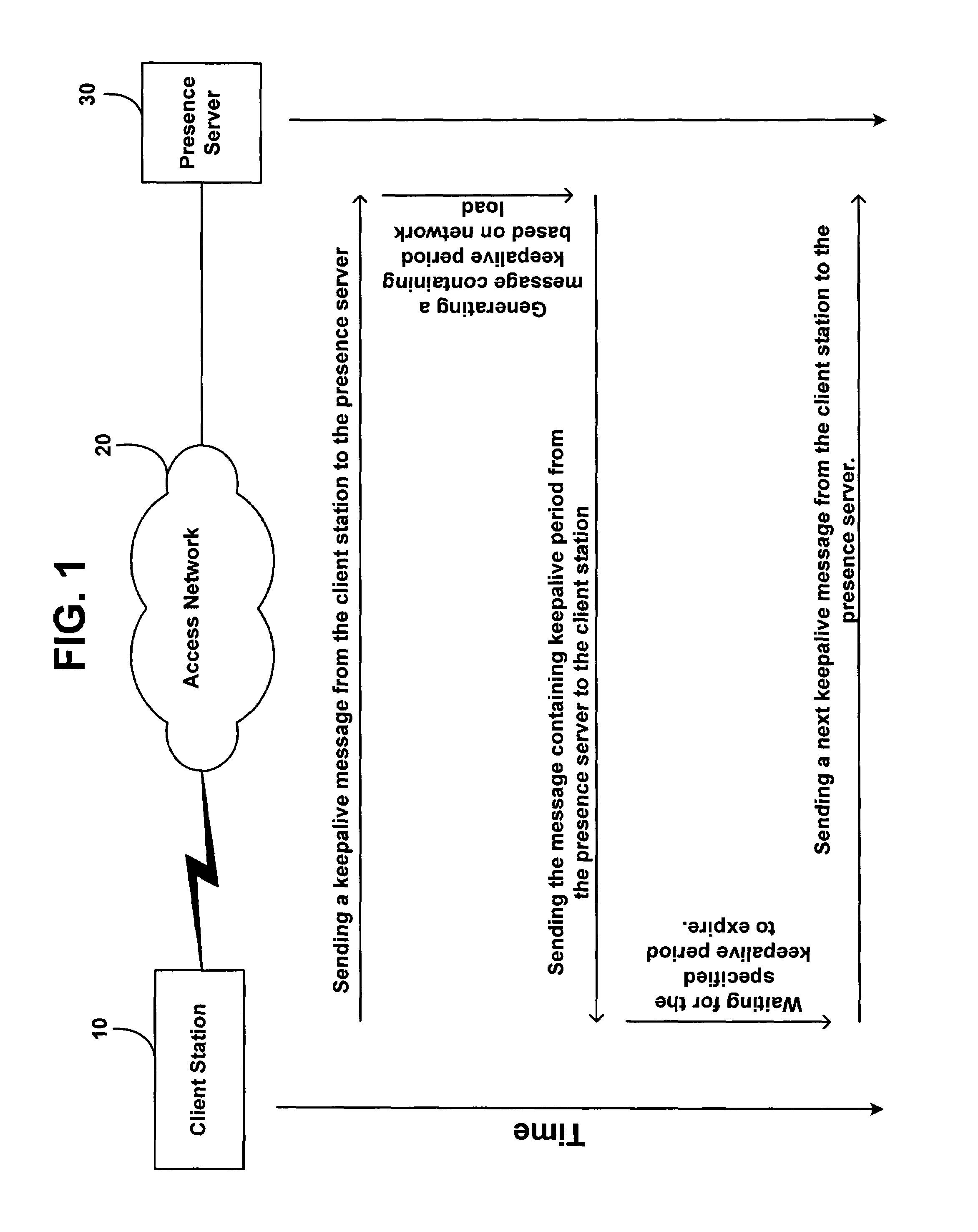
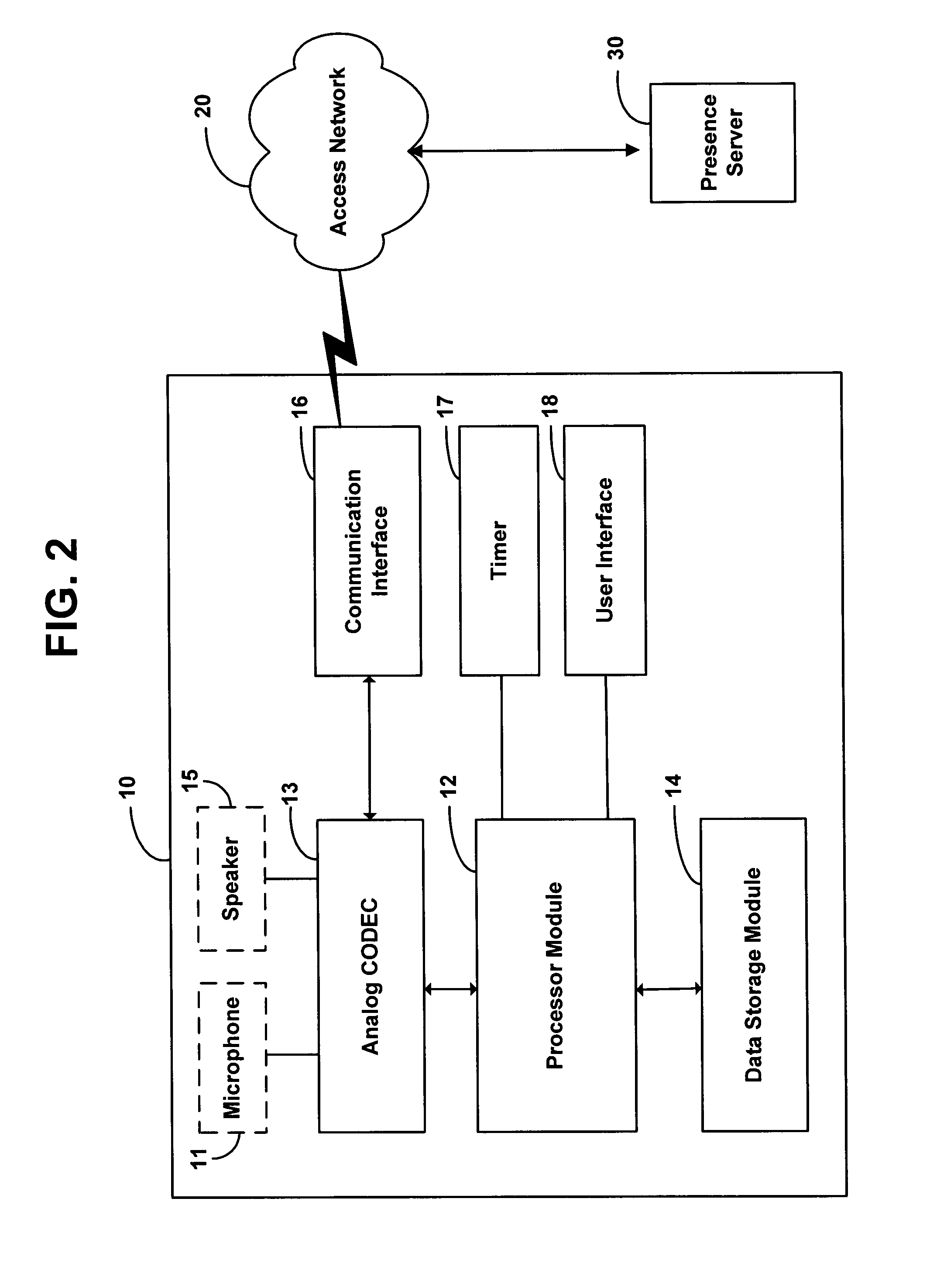
Method and system for updating network presence records at a rate dependent on network load
ActiveUS7634558B1Available bandwidthSimple methodMultiple digital computer combinationsTransmissionActive messageRate dependent
A method is disclosed for determining how often a client station in a network should send keepalive messages. Based on a measure of network load, a presence server determines a keepalive period, which is a time interval in which a client station needs to send a keepalive message, and the presence server reports this keepalive period to the client station. The client station responsively sends a keepalive message to the presence server within the determined keepalive period.
Owner:SPRINT SPECTRUM LLC
Push e-mail inferred network presence
ActiveUS20080040441A1Multiple digital computer combinationsData switching networksThird partyService provision
The presence of a user or device on a network is inferred without requiring permission or exposure from a service provider or network operator. If updates for a user have been pending past a specified amount of time, the user can be inferred to not be present. If the user has requested updates within that specified time, the user can be inferred to be present. If presence cannot be inferred from past activity, a wake-up event can be sent to the user. The wake-up event can be piggy-backed on an existing protocol in order to have easy access to the user. If the user is present on the network, the user will respond to the wake-up event and the user's presence can be determined. If the user does not respond, it can be inferred that the user is not present. This presence can be provided to a third party.
Owner:ORACLE INT CORP
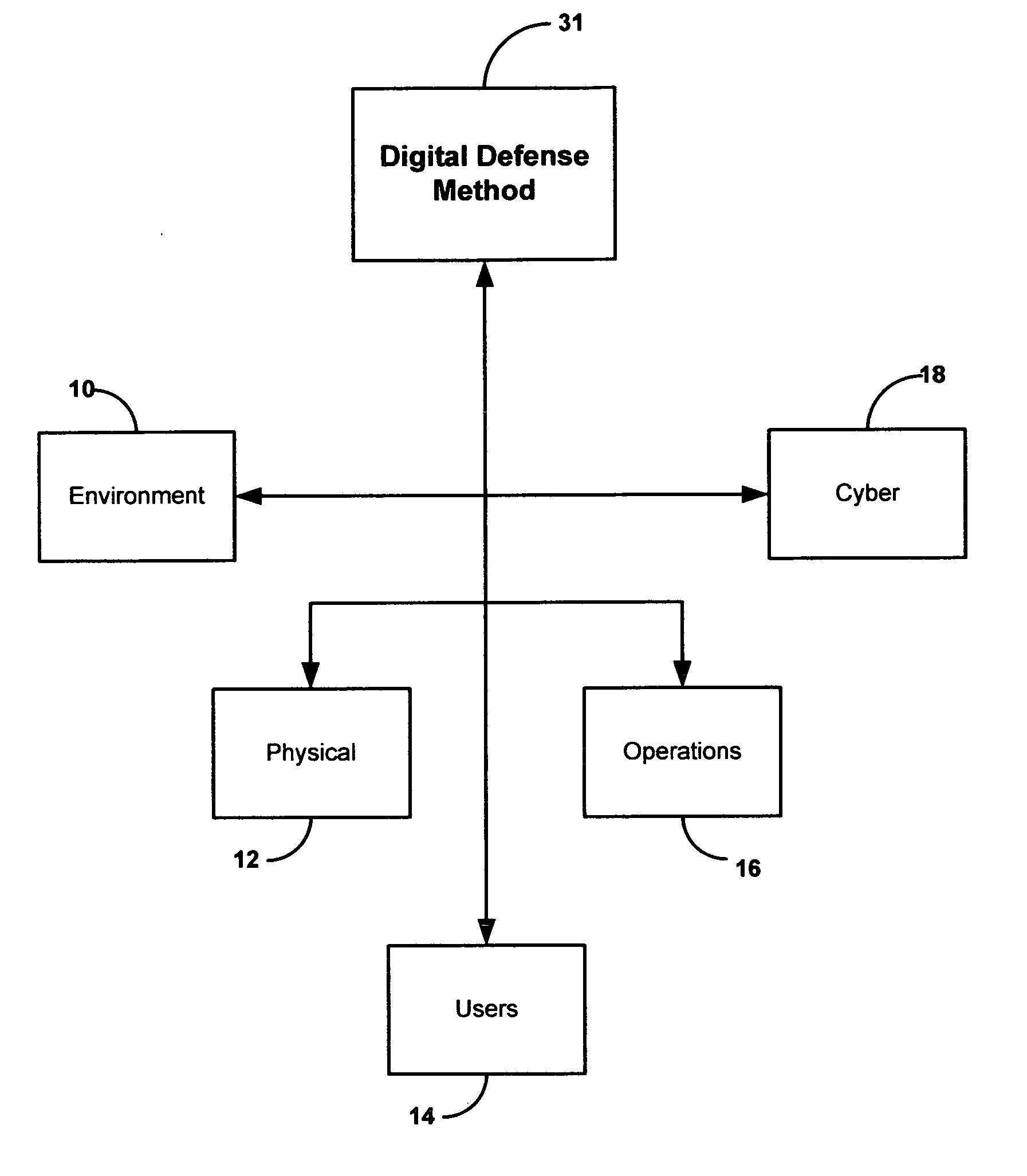
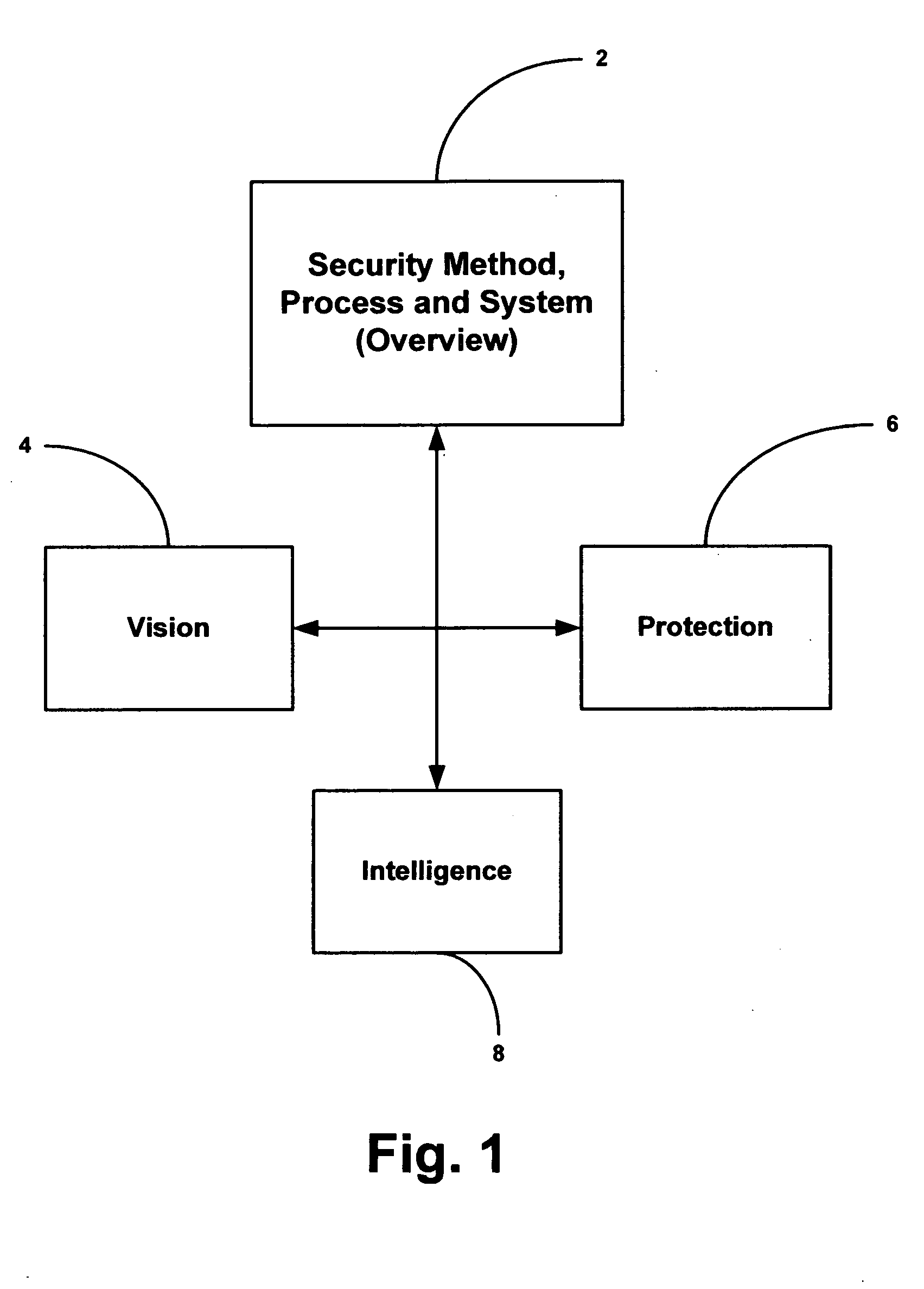
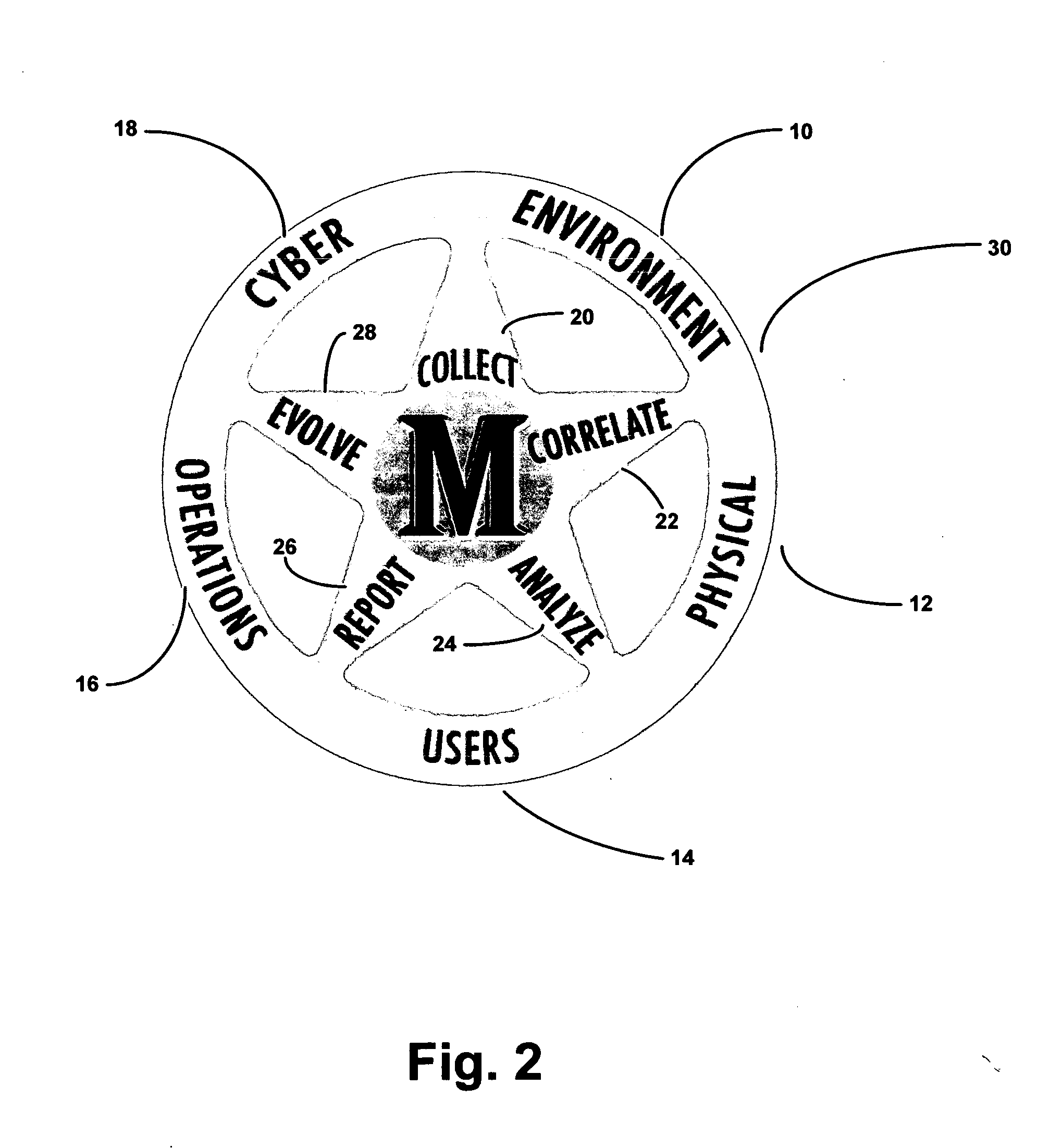
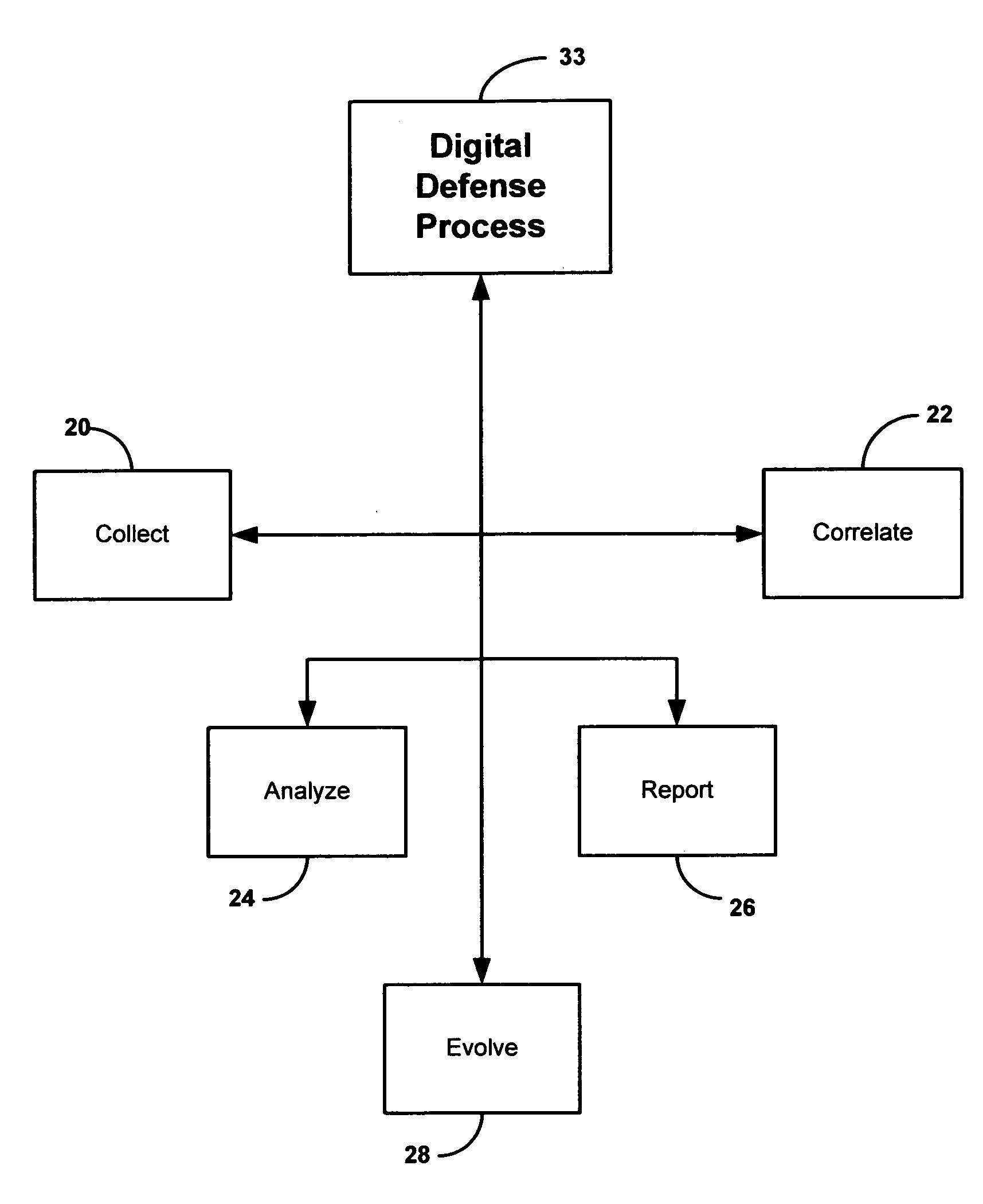
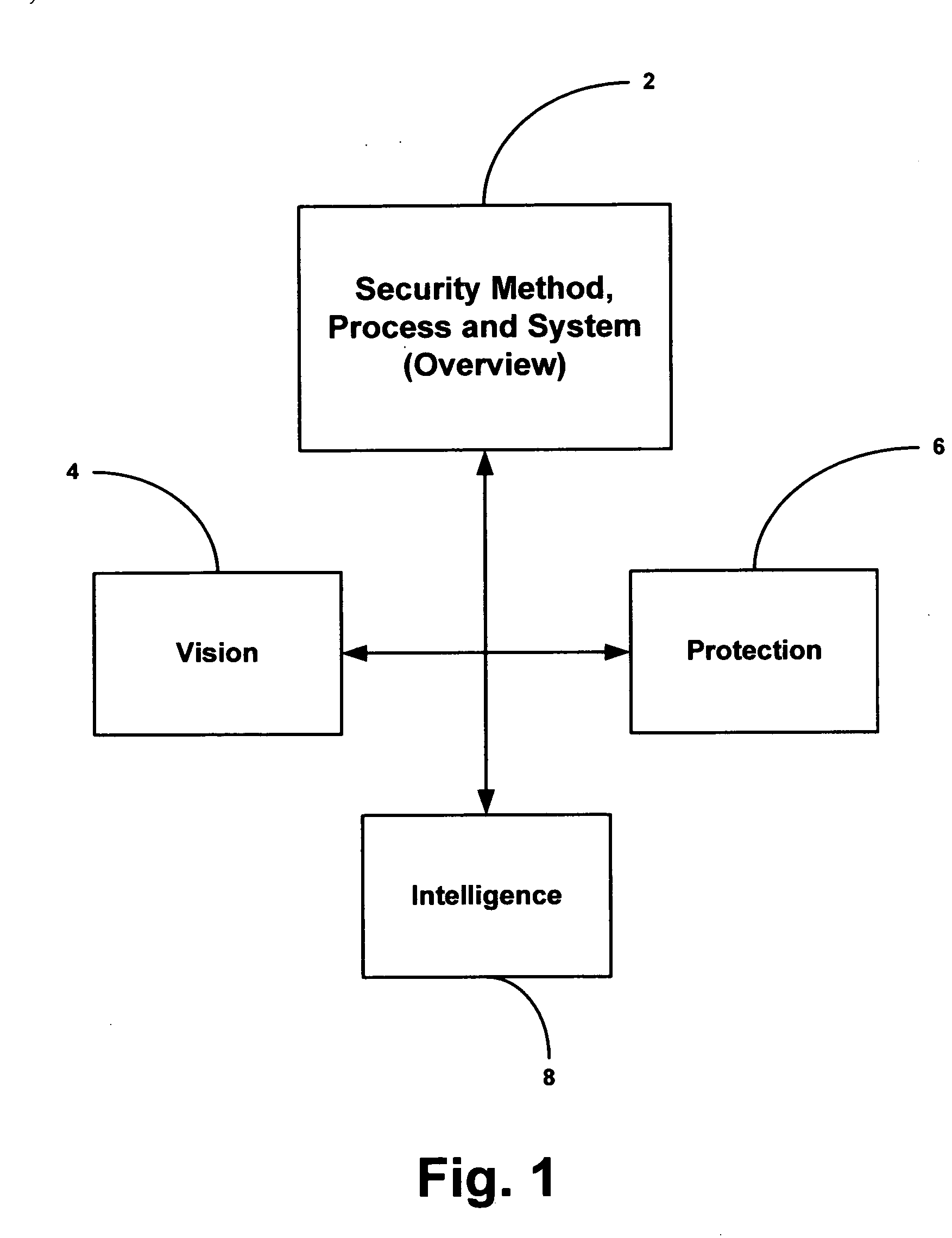
Security system and method including individual applications
InactiveUS20070180522A1Great advantageReduce downtimeMemory loss protectionUser identity/authority verificationEnvironmental issueAnalysis data
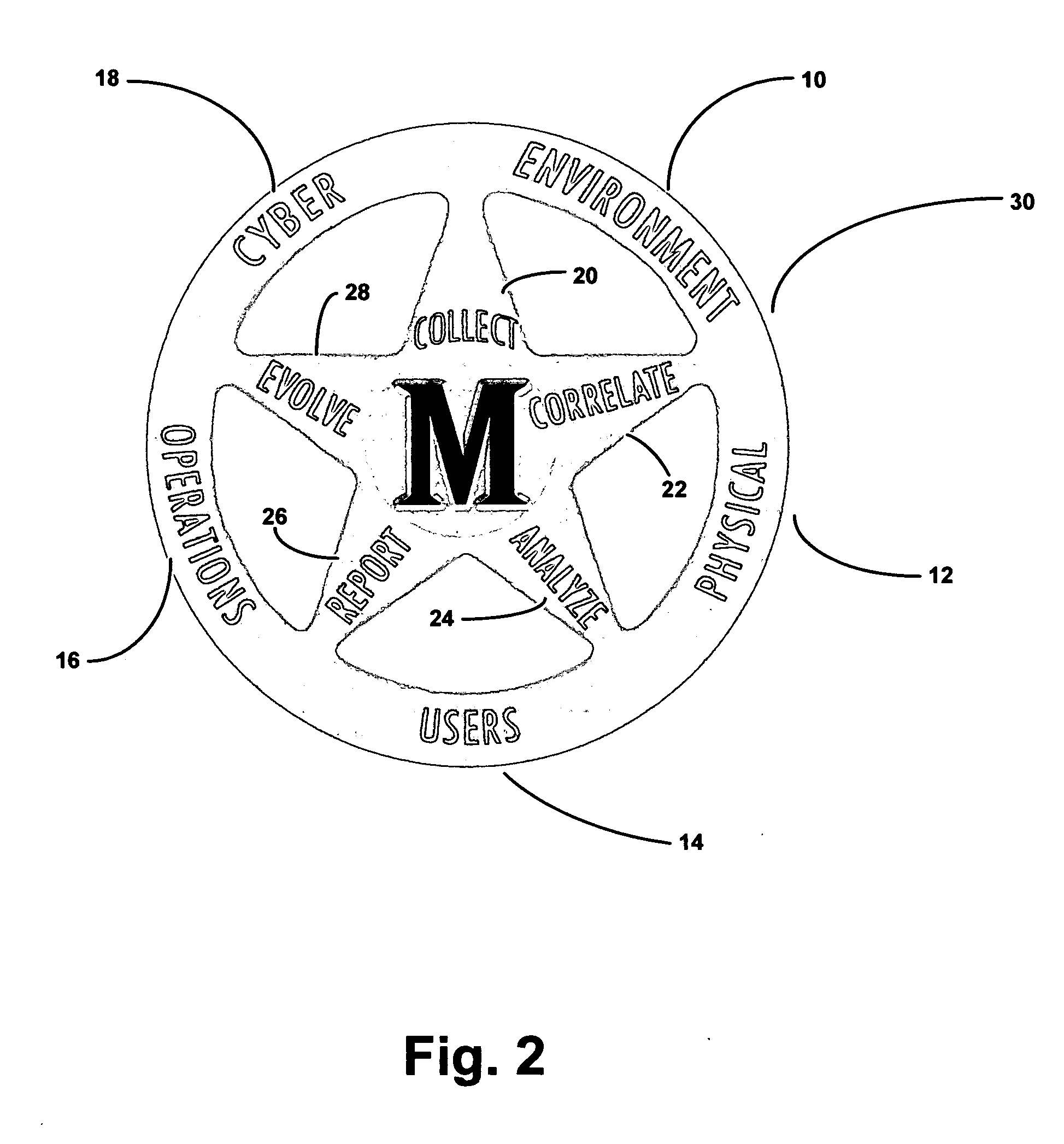
A method and system for providing security to organizations having data and information, involving a vision specific to the organization by gathering information and determining current and future plans and needs, a scenario for protection from invasive activities including cyber-space and physical invasion, and intelligence to assist in determining protection. Also included are present and needed environmental concerns and threats, present and needed physical components, present and needed education and training for end users with access to the information, operations by examination, monitoring and detailing present and needed processes, and cyber presence including one or more computers, functions, locations, configurations, and trust relationships. Also considered are the importance of proprietary information, off-site back-ups, access-level restrictions to data, log books and preventions to minimize down-time of systems due to maintenance or attack. Also involved are collecting data, correlating the data, analyzing the data, providing reports, and evolving the method based upon information gathered. A number of different application are also provided.
Owner:BAGNALL ROBERT J
Method for distributing and maintaining network presence information
InactiveUS20020035594A1Multiple digital computer combinationsData switching networksIp addressNetizen
A method for distributing and maintaining network presence information is presented. According to an embodiment of the present invention, a user logs onto the Internet and transmits to an Internet Presence Information Server (IPIS) his / her presence information, a list of peers (individual network users) whose network presence are of interest to the user, and a request for a list of peers interested in the user's network presence. The IPIS then responds to the user with both a list including the last known Internet Protocol (IP) address for each peer the user is interested in and a list of peers interested in the user's Internet presence. No further communication between the user and IPIS is required after the IPIS responds to the user with these two lists. The user then attempts to directly contact the peers on the first list received from the IPIS by confirming and authenticating the received IP addresses. According to policy, the user directly contacts the peers on the second list received from the IPIS to inform those peers the user is currently signed on-line. Finally, the user periodically "pings" (directly contacts) the confirmed and authenticated IP addresses from the first list received from the IPIS to determine when those peers sign off-line.
Owner:INTEL CORP
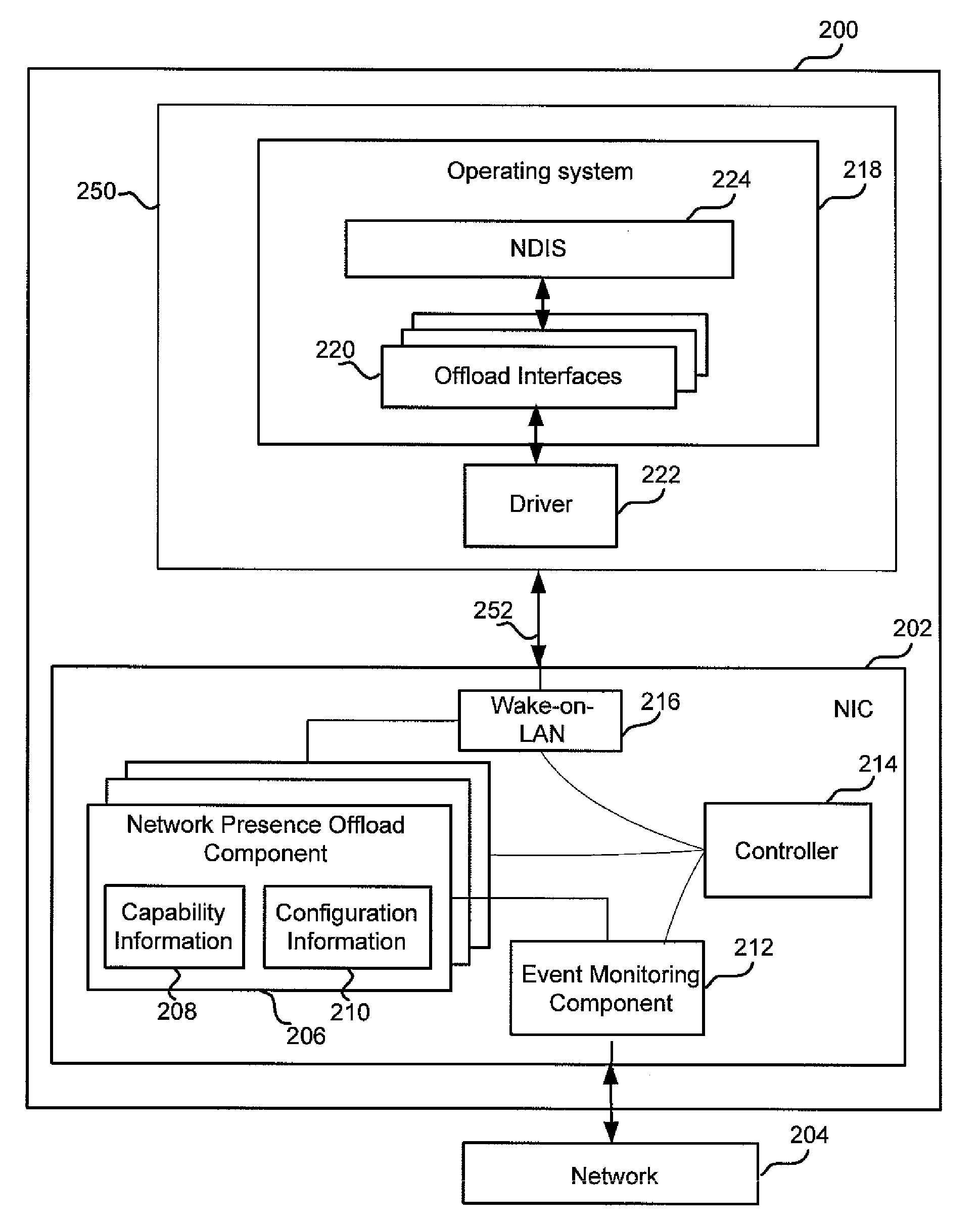
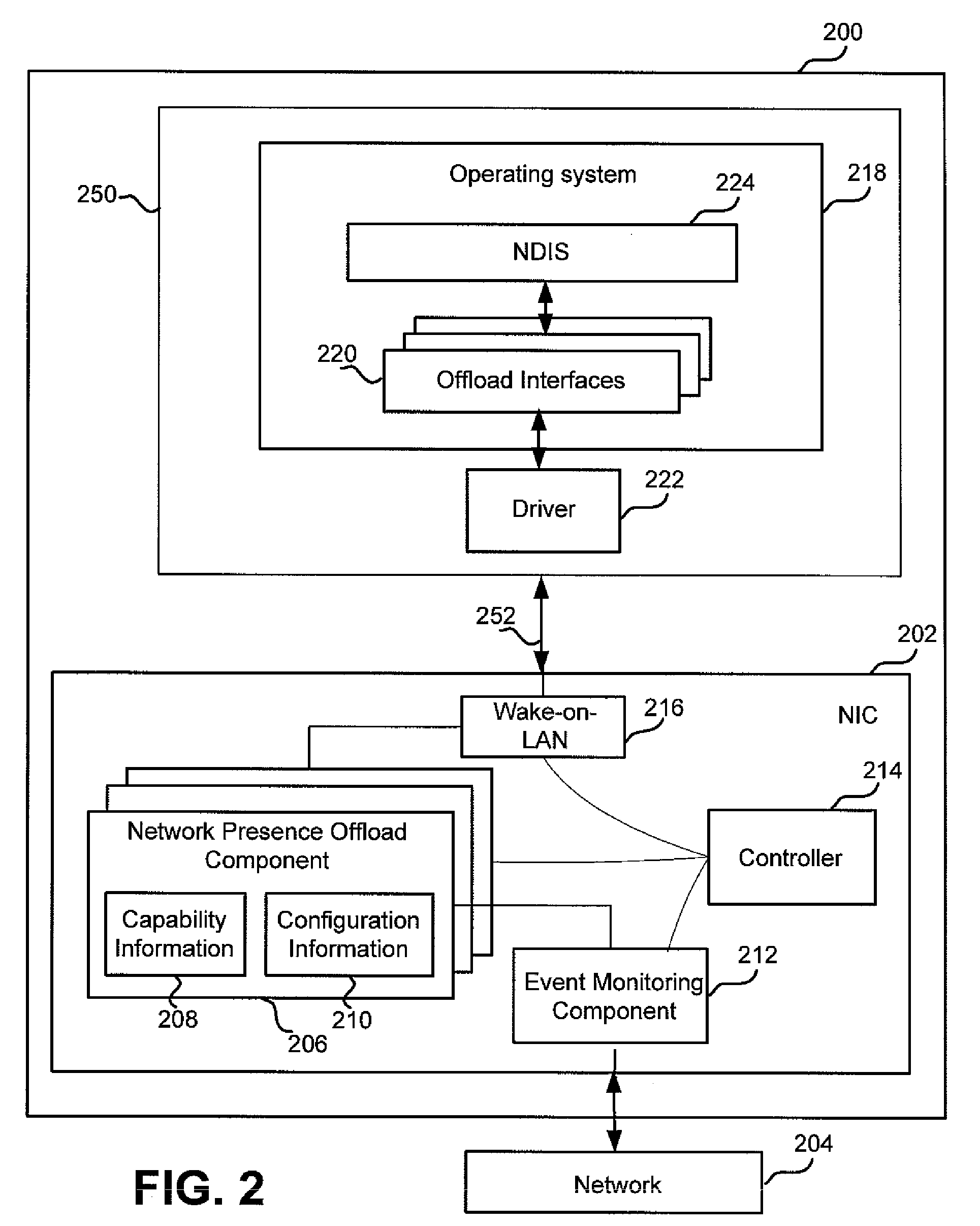
Network presence offloads to network interface
ActiveUS20100174808A1Good power savingSave powerEnergy efficient ICTDigital data processing detailsNetworking protocolSecurity information
A computing device that has a network interface that performs a subset of possible networking functions while the computing device is in a sleep mode. The subset of functions may be simply implemented on the network interface, yet to substantially reduce the frequency with which the computing device has to wake up to perform networking functions. The subset of functions may be selected to maintain a network presence of the computing device while the device is in sleep mode, and may include responding to requests for MAC information, sending keep-alive messages or exchanging security information that, in accordance with network protocols, has a limited lifetime that would otherwise expire while the computing device is in sleep mode.
Owner:MICROSOFT TECH LICENSING LLC
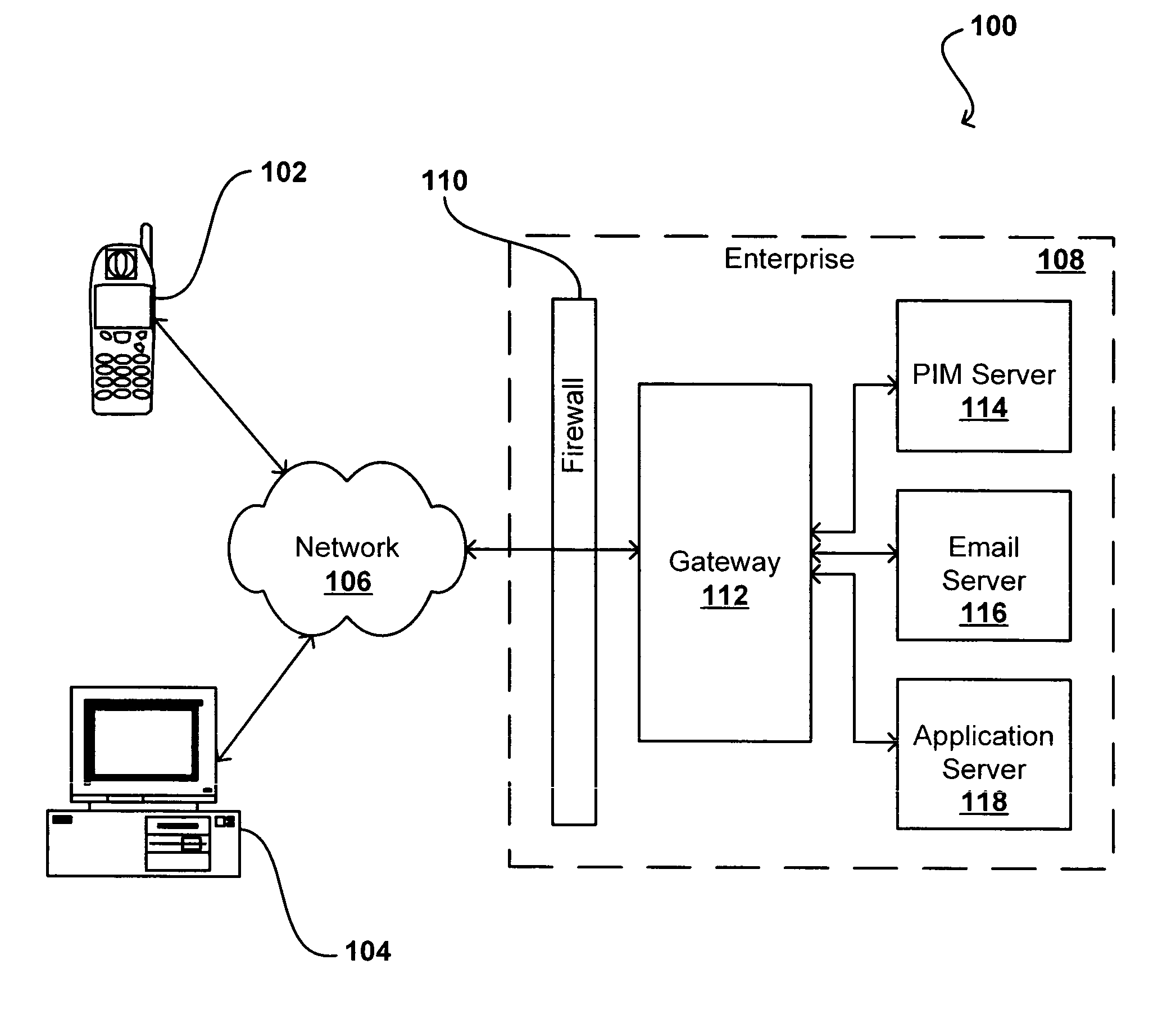
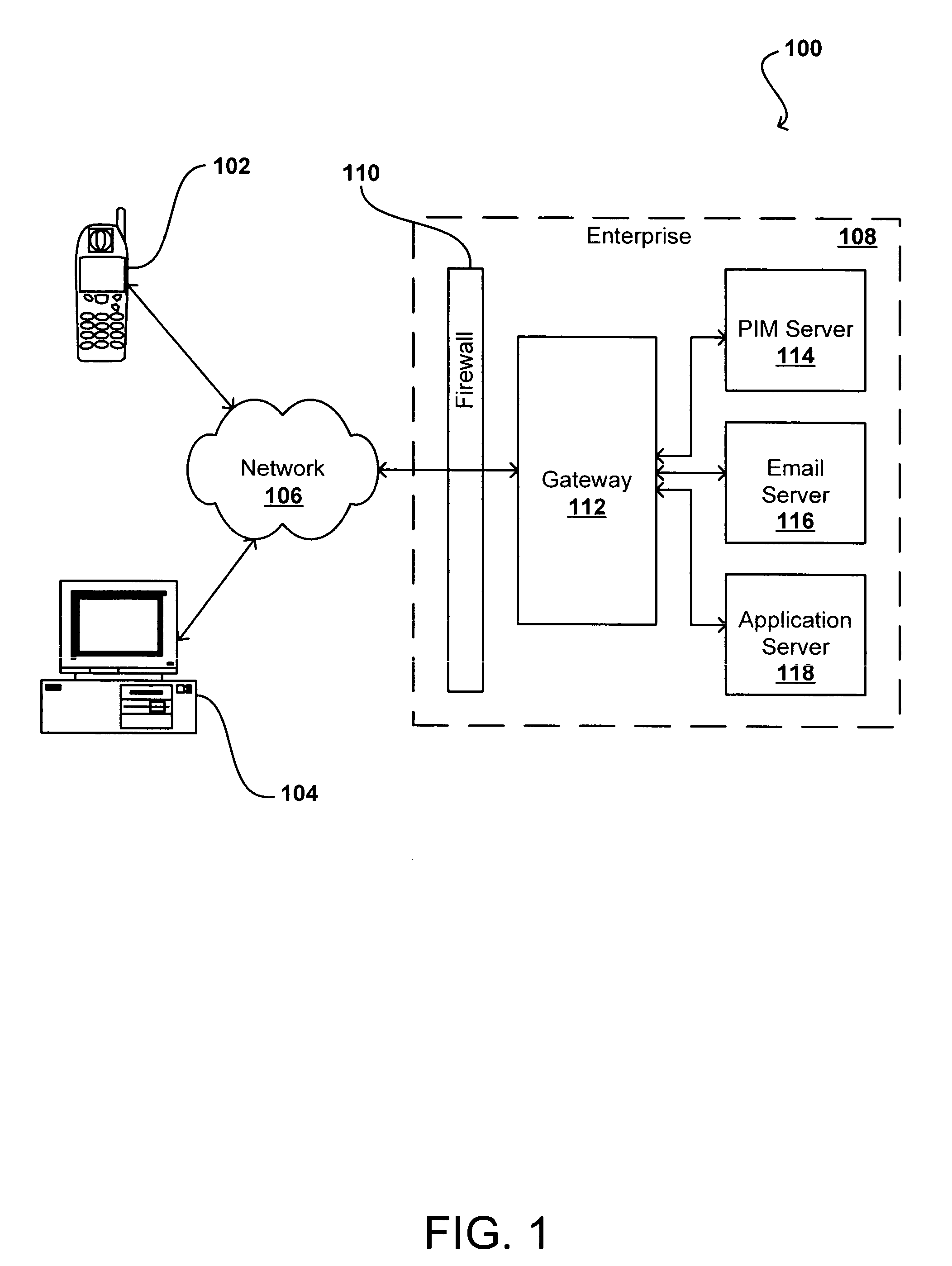
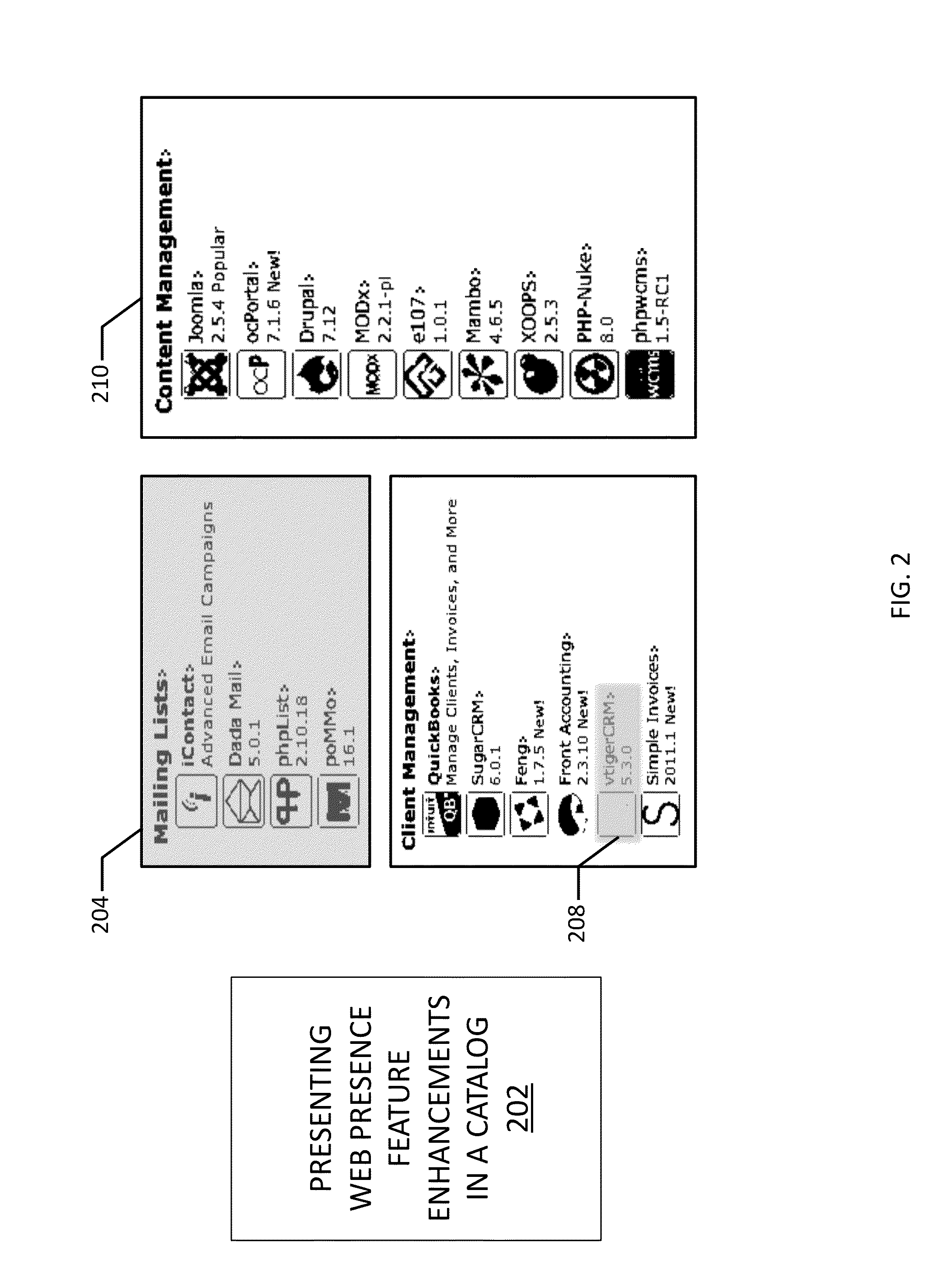
Automatic web presence feature deployment
InactiveUS20130204746A1Easy to install automaticallyEasy to collectBuying/selling/leasing transactionsResourcesApp storeMultimedia
An app store provides a searchable catalog of selectable elements representing programs that provide capabilities for enabling the online presence of a customer, and automatically installs such programs and enables such web presence-enabling capabilities upon selection by the customer of the selectable element.
Owner:ENDURANCE INTERNATIONAL GROUP
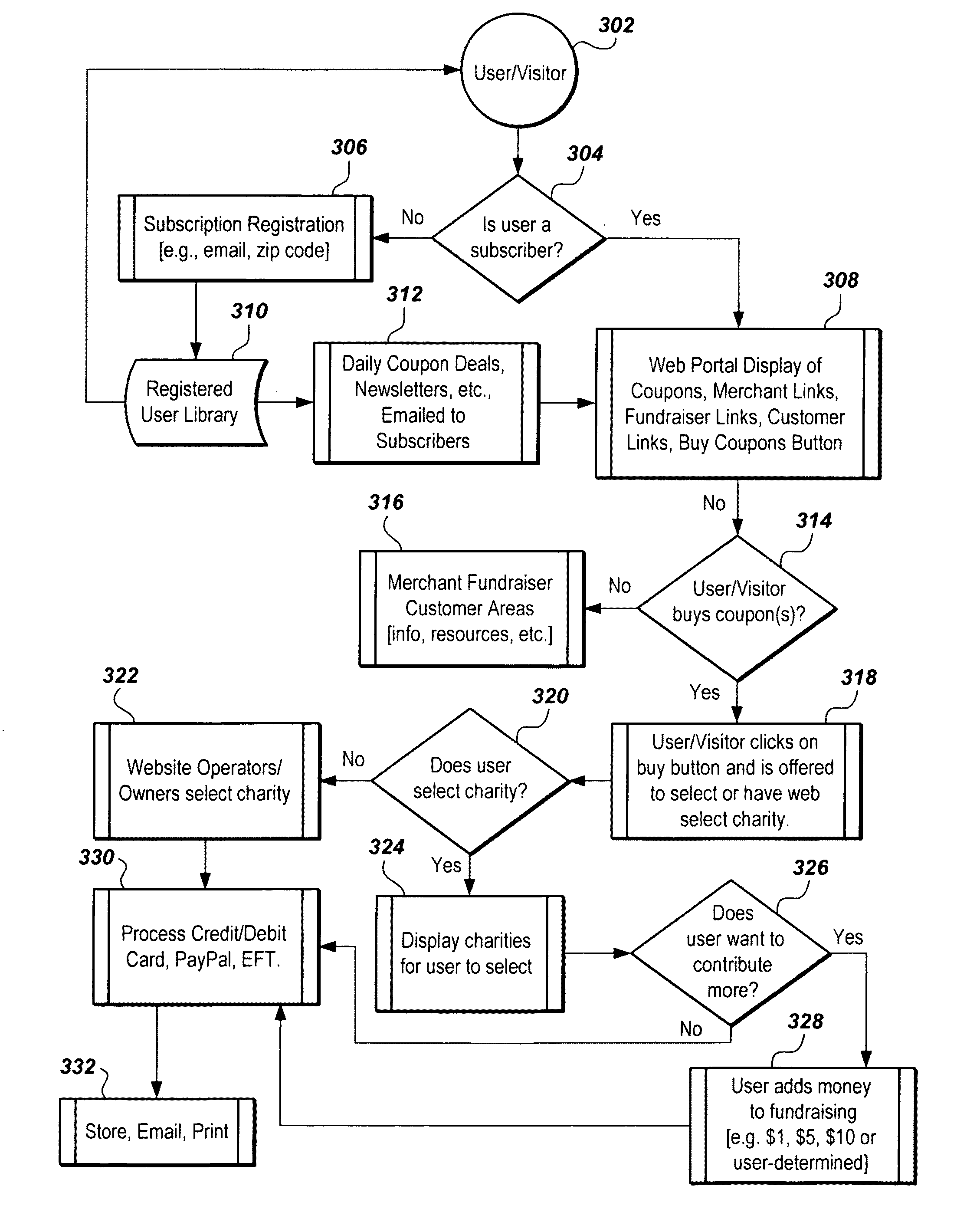
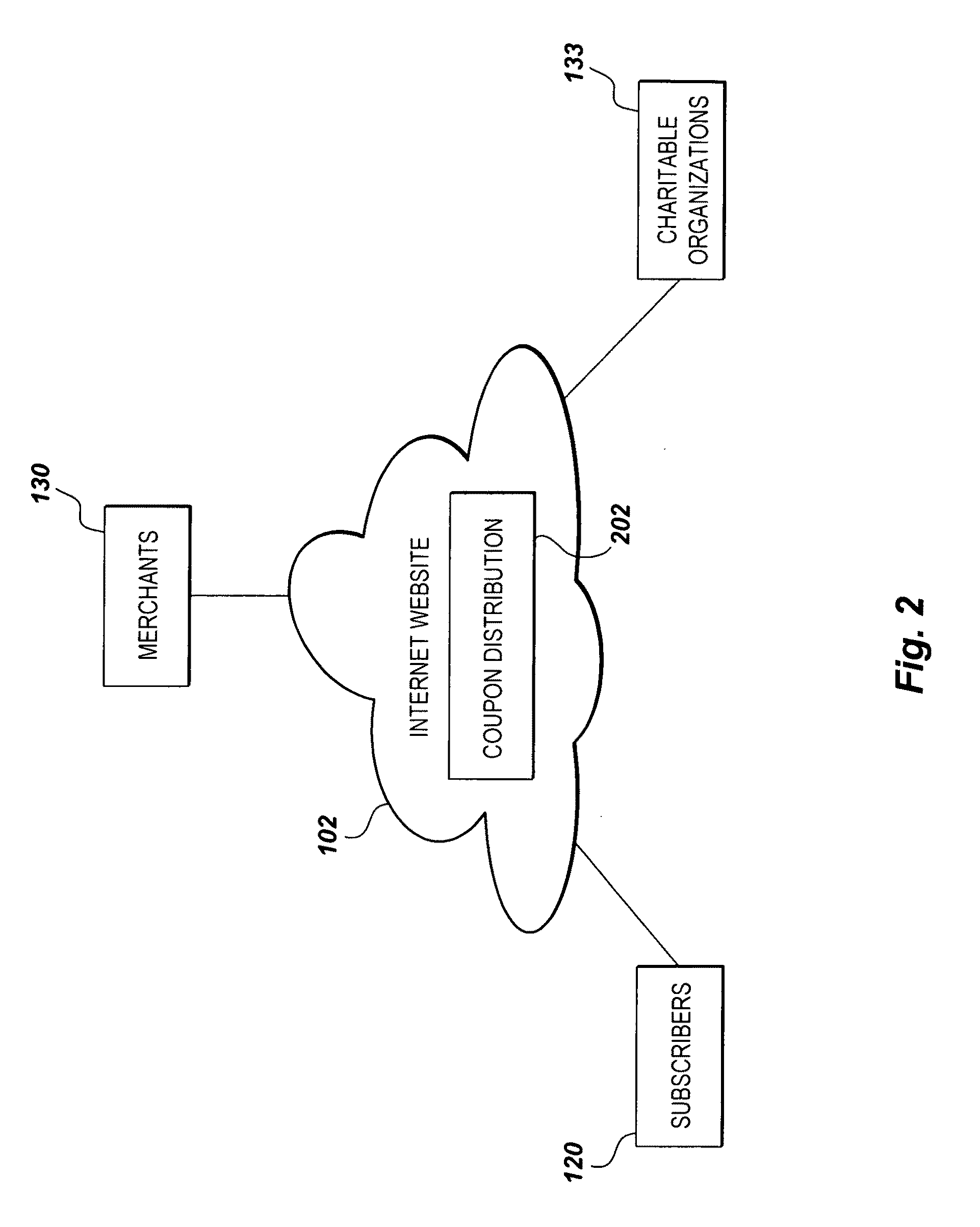
Online coupon distribution system and method
InactiveUS20110276373A1Readily apparentMultiple digital computer combinationsPayment architectureCost effectivenessDistribution system
The online coupon distribution system and method distributes discount coupons through a website. The website is designed and constructed to include a “trifold” process that blends discount coupon purchasing with cost effective advertising and charitable contributions into a powerful web presence. The process is called cooperative couponing. The system sells coupons and allocates generated revenue among merchants, a website principal, and a designated charity. The website identifies local merchants in a geographic area. Coupons are electronically distributed on a daily basis. The website features target goal coupons, two subsidiary coupons providing discounts, and five additional weekly merchant coupons strategically placed on the website. The website permits website users to designate a charitable contribution to a charity of their choice based on their coupon purchase.
Owner:JUSZCZAK NICHOLAS MR +1
Method and system for online sales and purchase
InactiveUS20060149653A1Level decision making processCost timeFinanceBuying/selling/leasing transactionsInternet basedData science
Internet-based commercial network connects multiple qualified participant buyers and sellers. Items are made available for defined periods of time, referred to as an event (139). Event terms and conditions include item types, price, quantity, volume or units, discount, shipping terms (138). Reiterative offer and counteroffers permit negotiation of terms for an event. Participants may view anonymous competitive quotes for comparison and analysis. Pooled purchases and auctions are envisioned. Participants may create web presences and are subject to restrictions on access (141) and purchase (142) authority. Central system maintains participant data.
Owner:DAVIS ORENL +4
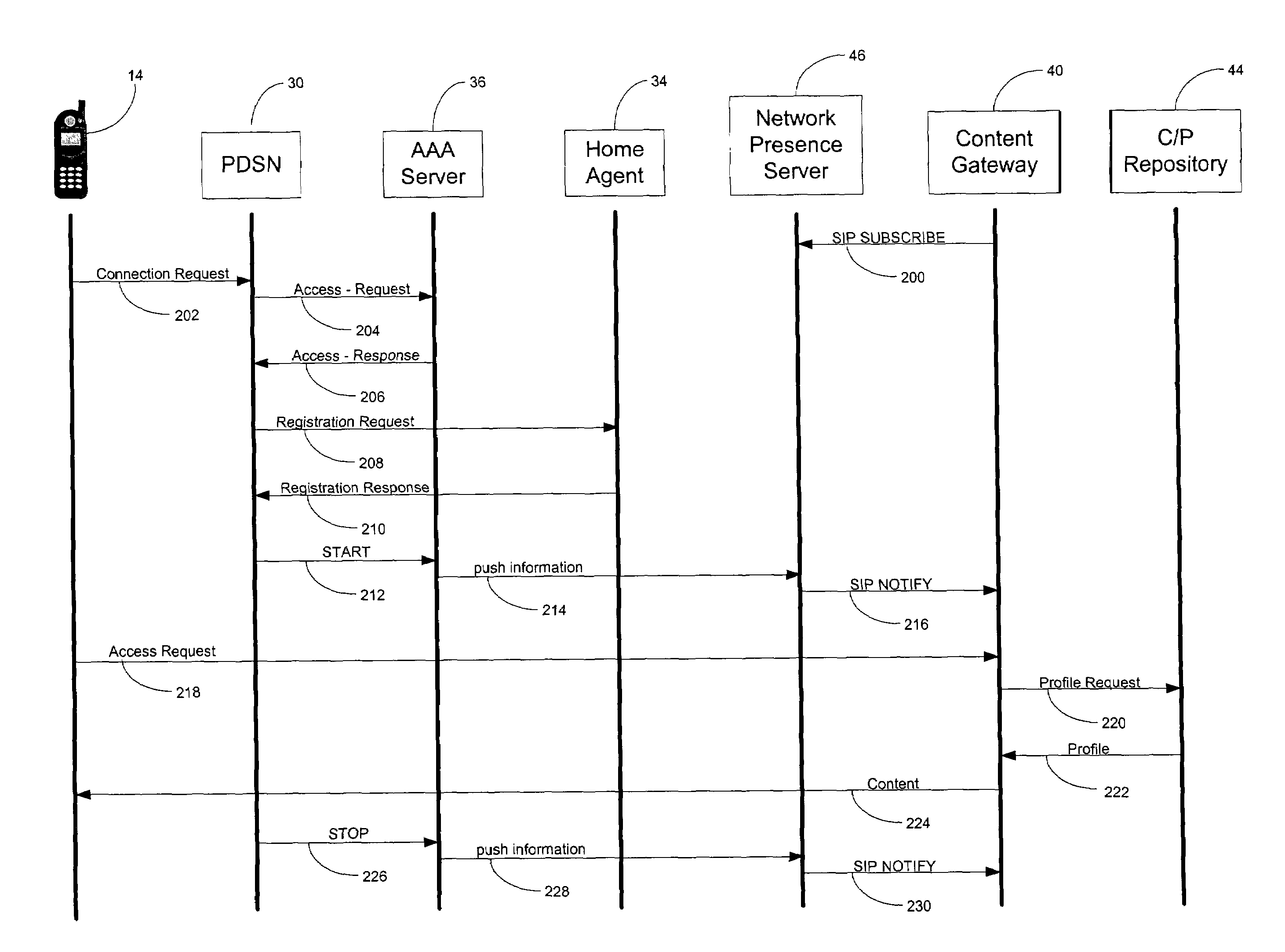
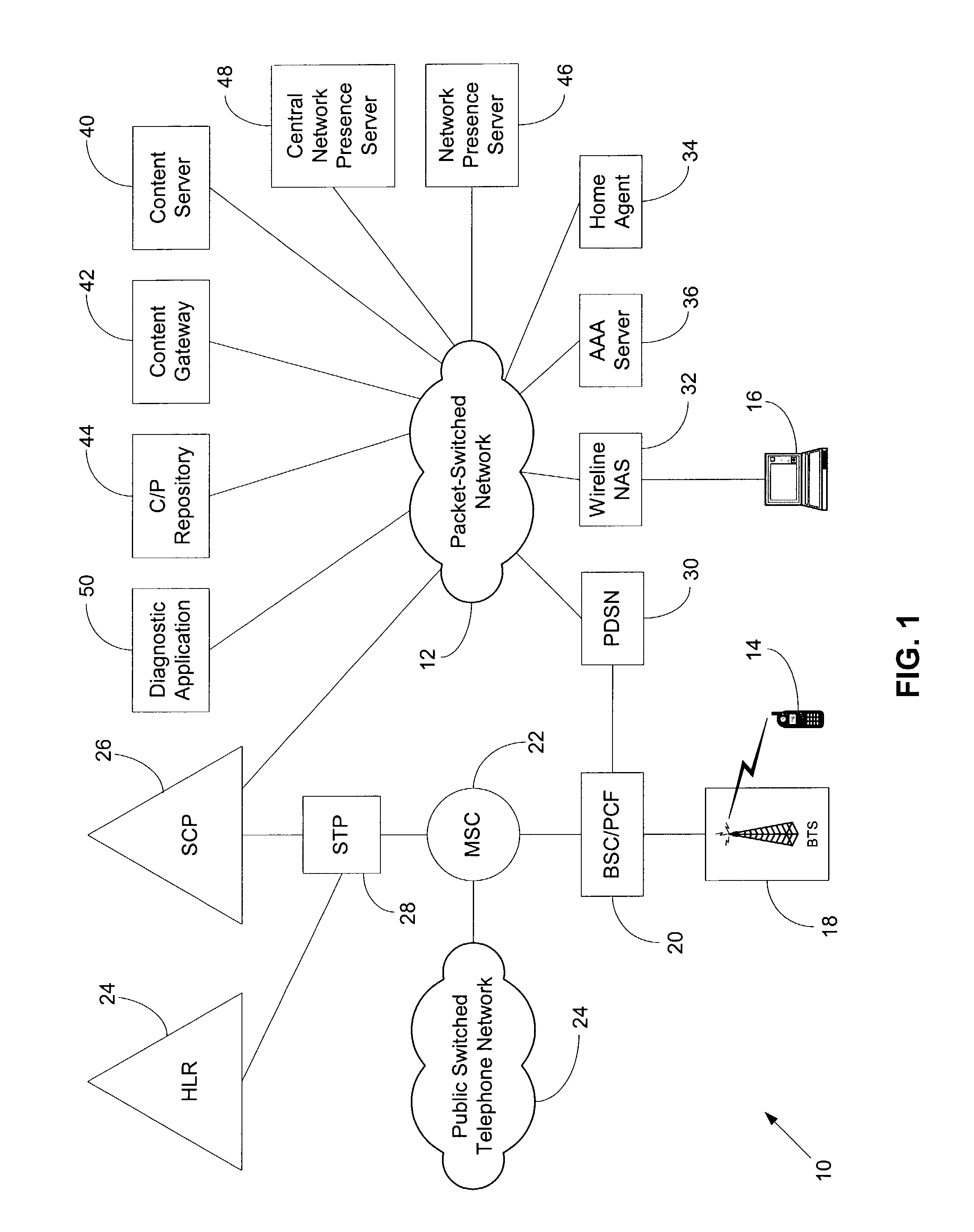
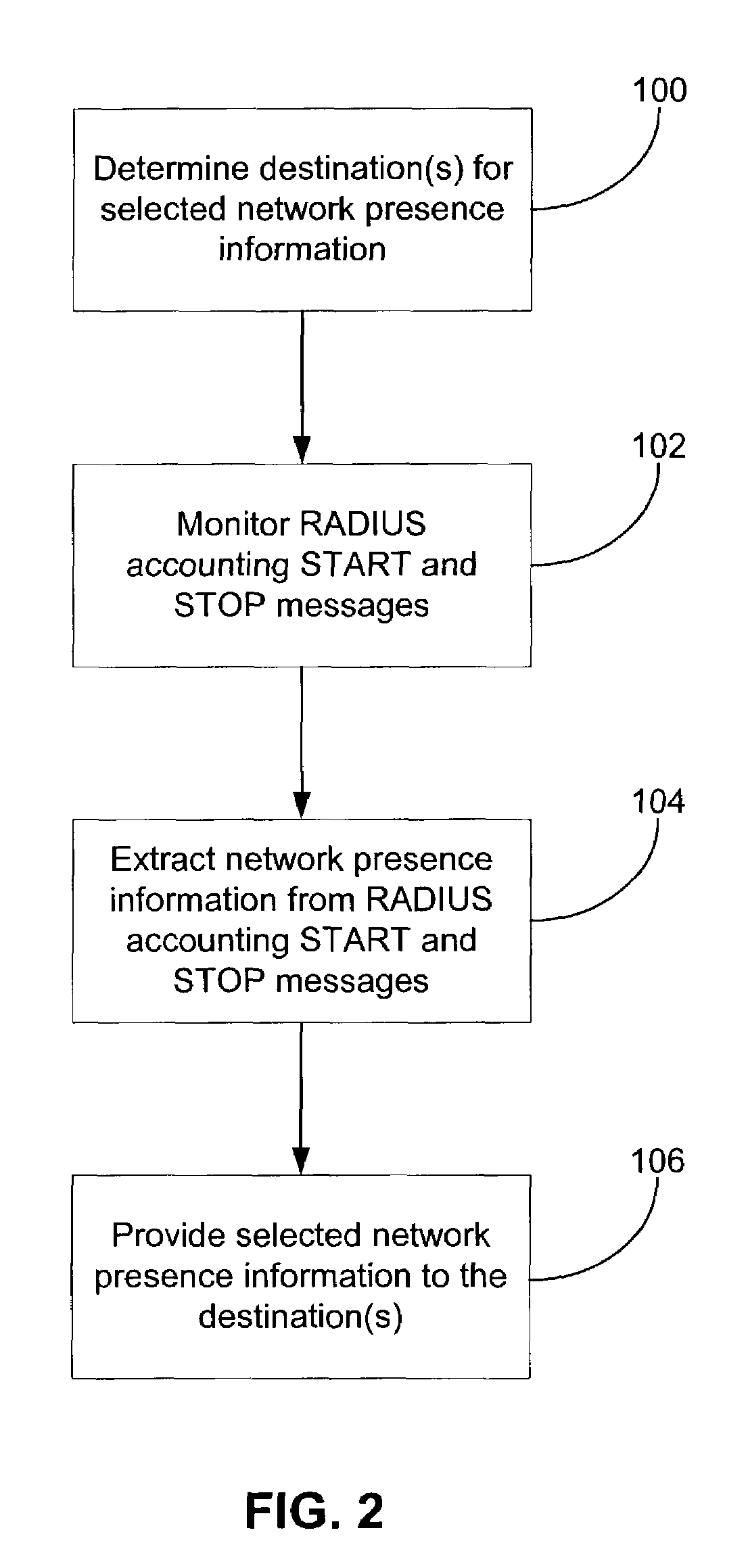
Method and system for network presence notification
ActiveUS7545762B1Assess restrictionData switching by path configurationNetwork access serverPacket data serving node
In a packet-switched network, a subscribing application subscribes to a network presence server to receive selected network presence information. The network presence server obtains the selected network presence information, at least in part, from status messages that a network access server, such as a packet data serving node (PDSN), sends, for example, to an accounting server. The network presence server then provides the selected network presence information to the subscribing application. The selected network presence information may include an identification of a particular customer that has just initiated or terminated a data session and the network address the particular customer is or was using.
Owner:SPRINT SPECTRUM LLC
Security system and method
InactiveUS20070180525A1Provide securityAvoid and minimize down-timeMemory loss protectionError detection/correctionEnvironmental issueAnalysis data
A method and system for providing security to organizations having data and information, involving a vision specific to the organization by gathering information and determining current and future plans and needs, a scenario for protection from invasive activities including cyber-space and physical invasion, and intelligence to assist in determining protection. Also included are present and needed environmental concerns and threats, present and needed physical components, present and needed education and training for end users with access to the information, operations by examination, monitoring and detailing present and needed processes, and cyber presence including one or more computers, functions, locations, configurations, and trust relationships. Also considered are the importance of proprietary information, off-site back-ups, access-level restrictions to data, log books and preventions to minimize down-time of systems due to maintenance or attack. Also involved are collecting data, correlating the data, analyzing the data, providing reports, and evolving the method based upon information gathered.
Owner:BAGNALL ROBERT J
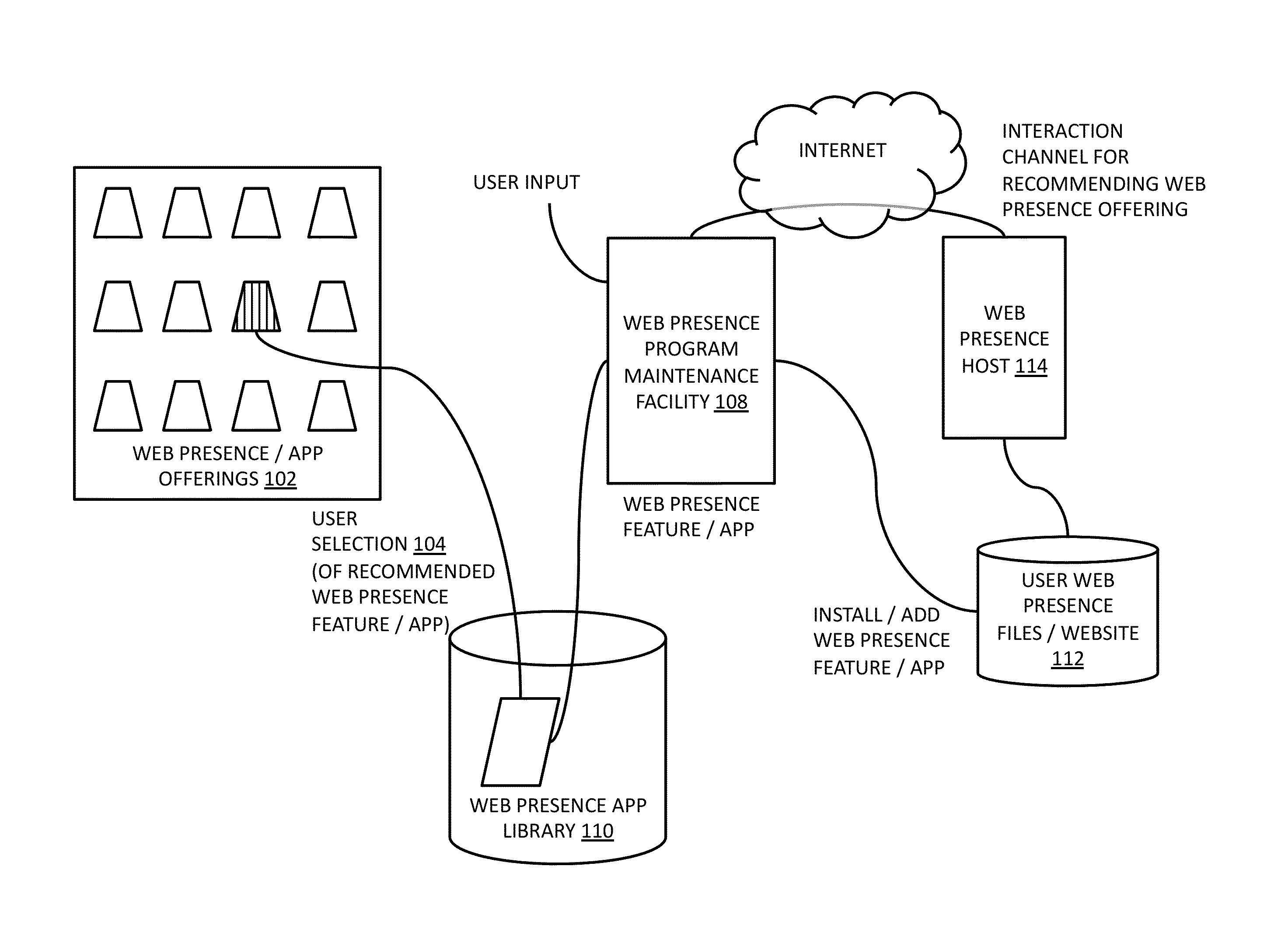
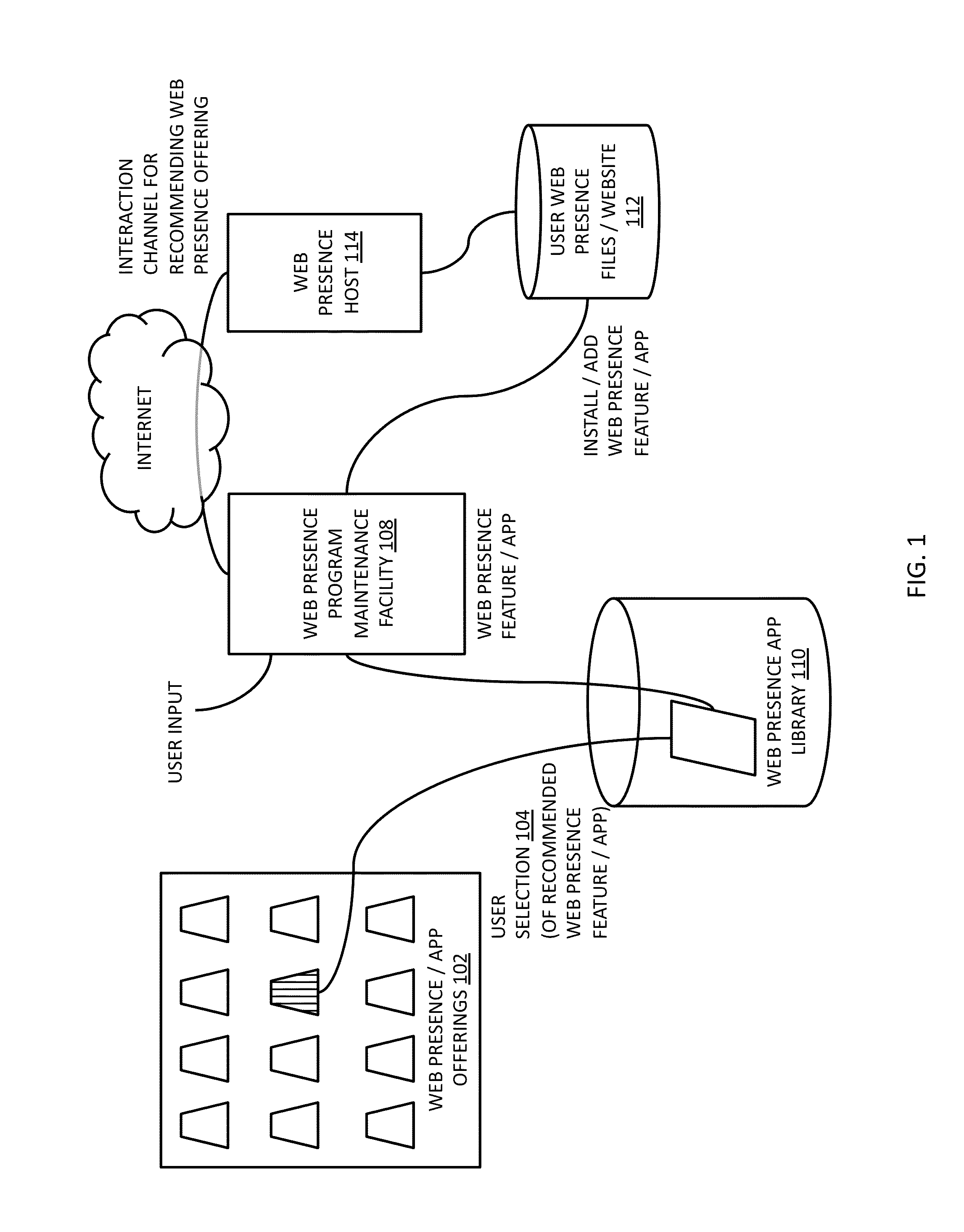
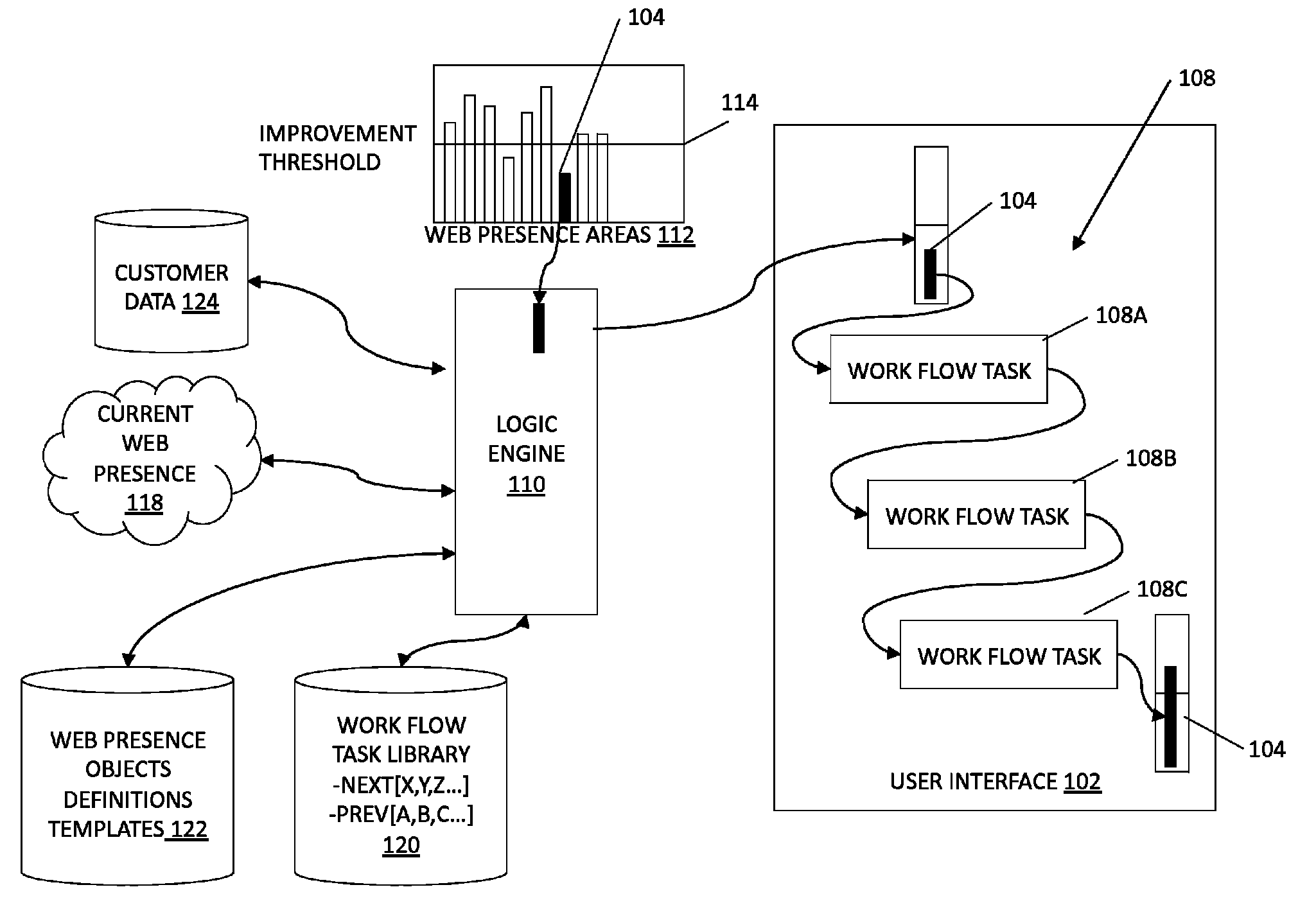
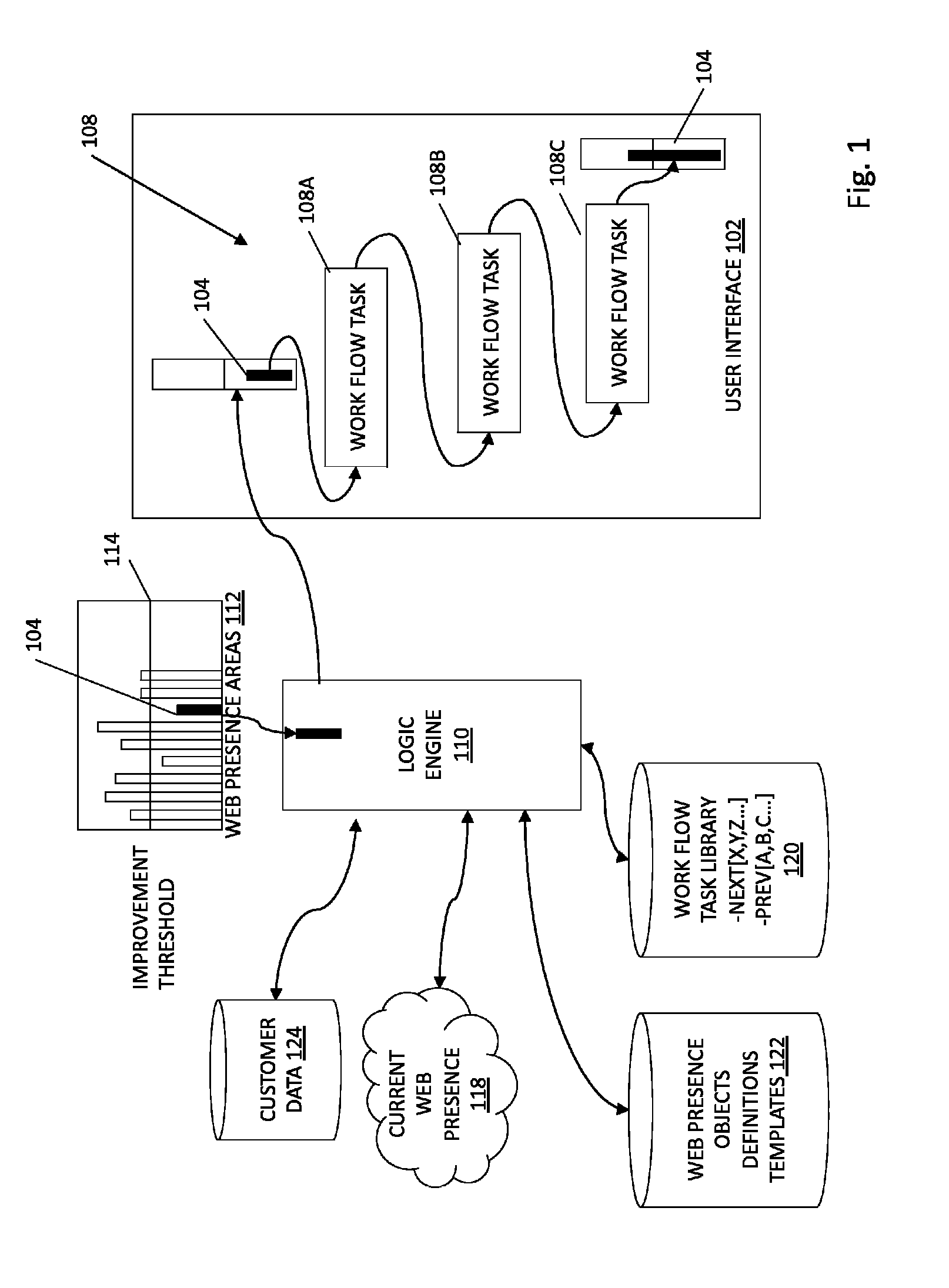
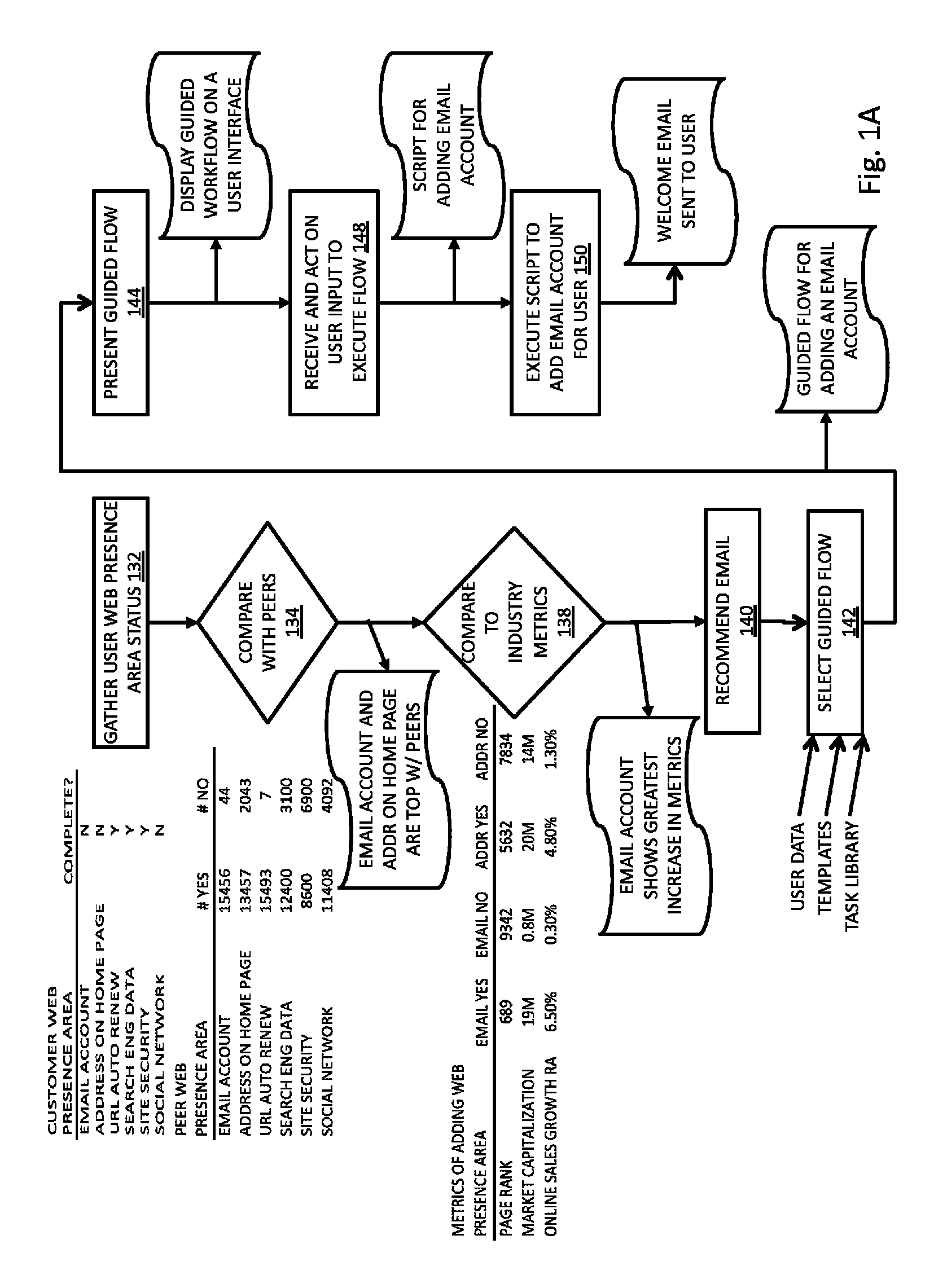
Guided workflows for establishing a web presence
ActiveUS20130204966A1Minimal timeMinimal knowledgeWeb data indexingMultiple digital computer combinationsUser interfaceKnowledge base
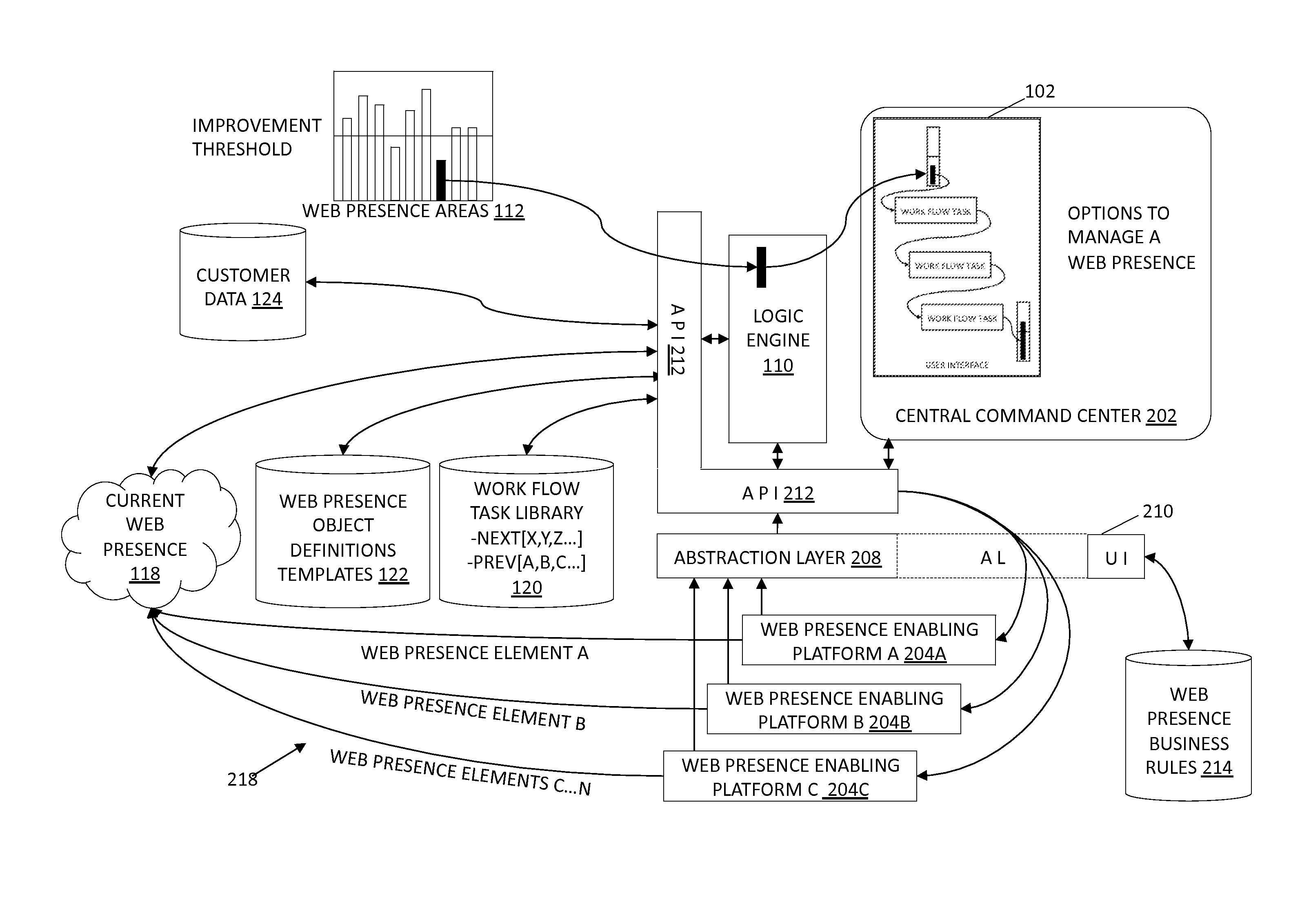
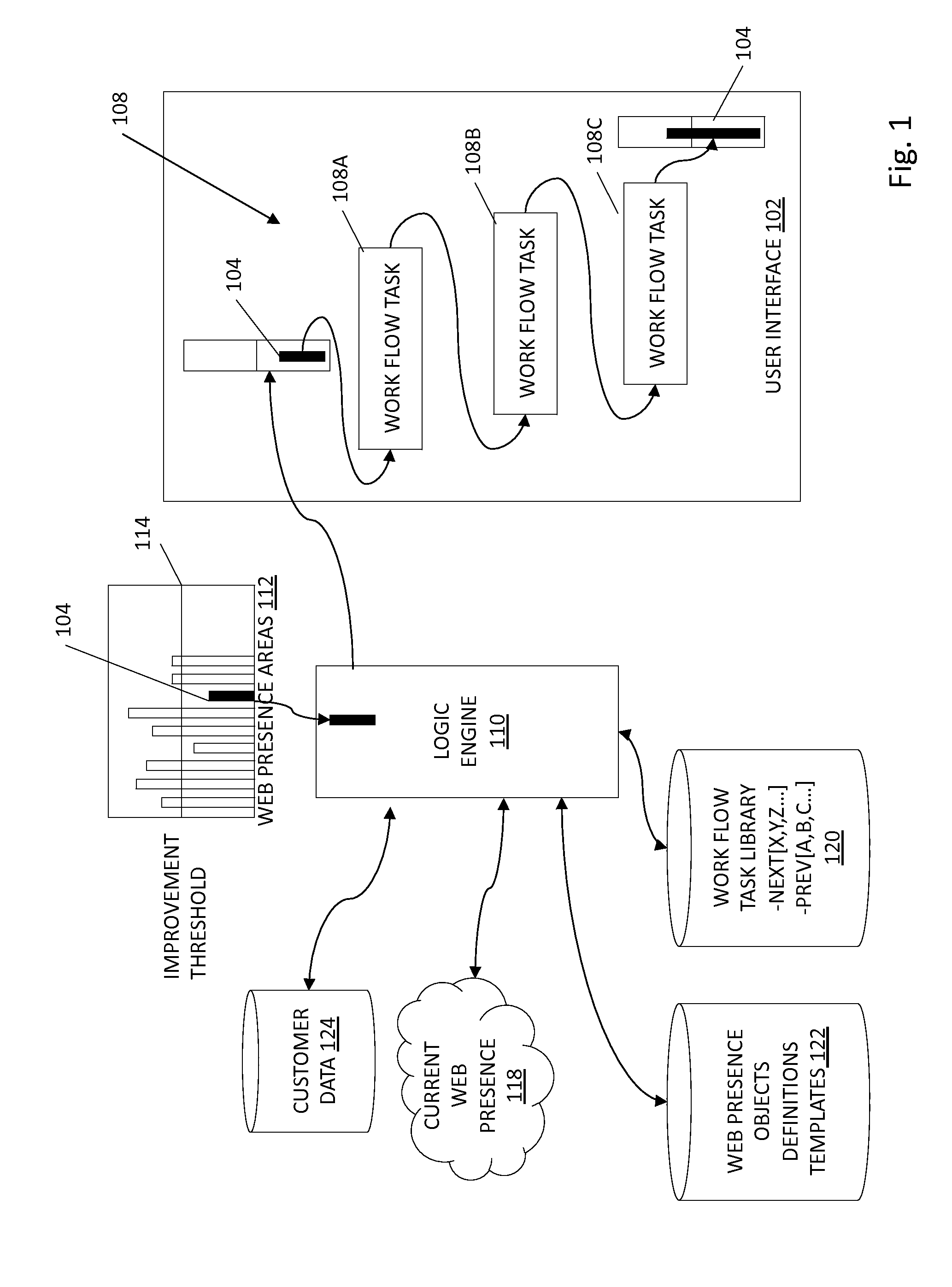
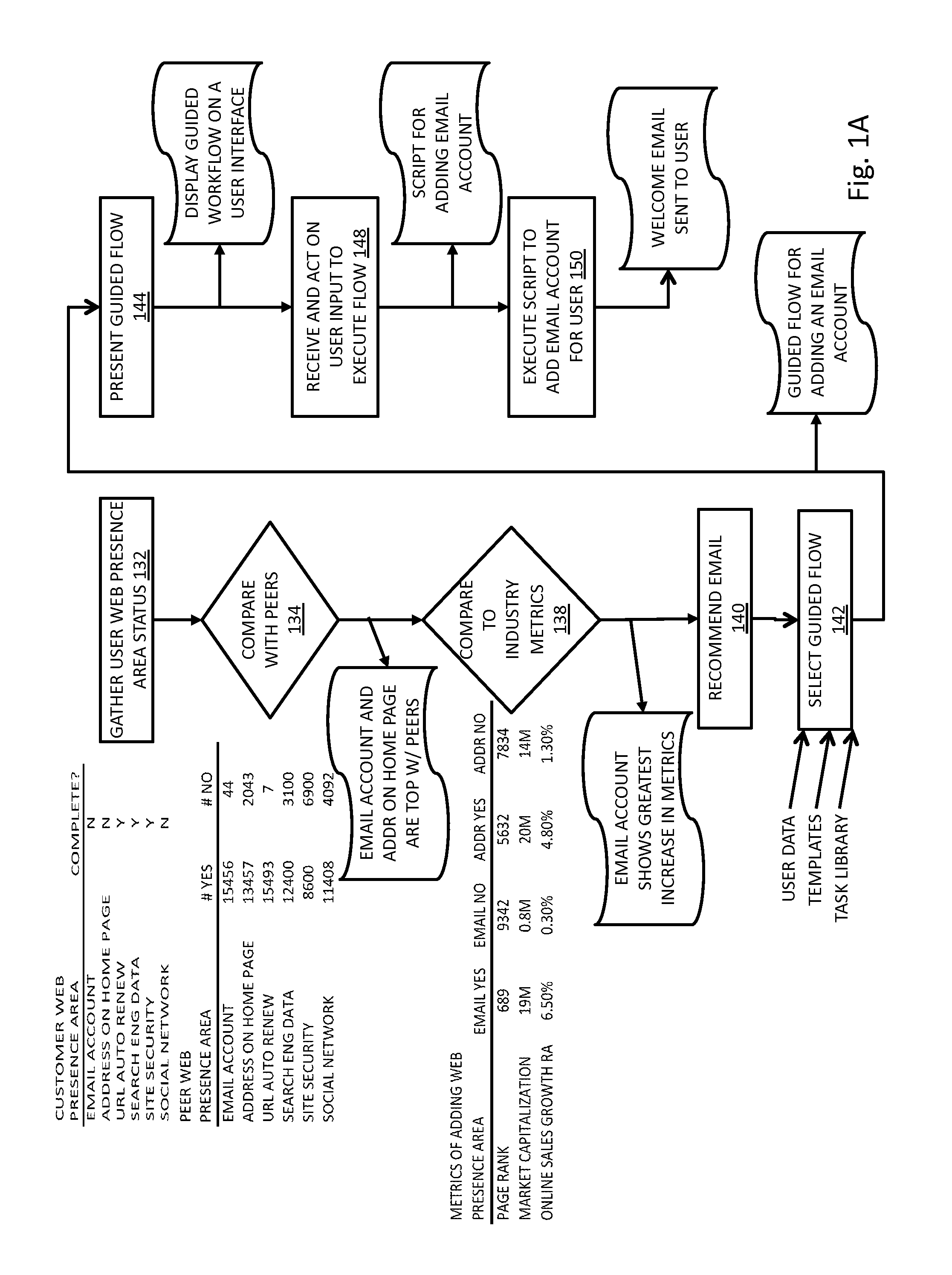
Methods and systems related to guided workflows for establishing a web presence include a customer user interface with a guided workflow layer based on a knowledge base about the customer, wherein the customer interface allows a customer to manage a customer's web presence based on operation of a logic engine that accesses information about what a customer has done and who the customer is (e.g. type of business), wherein the user interface presents a guided workflow of tasks associated with a recommended area of improvement for the customer.
Owner:NEWFOLD DIGITAL INC
File processing using mapping between web presences
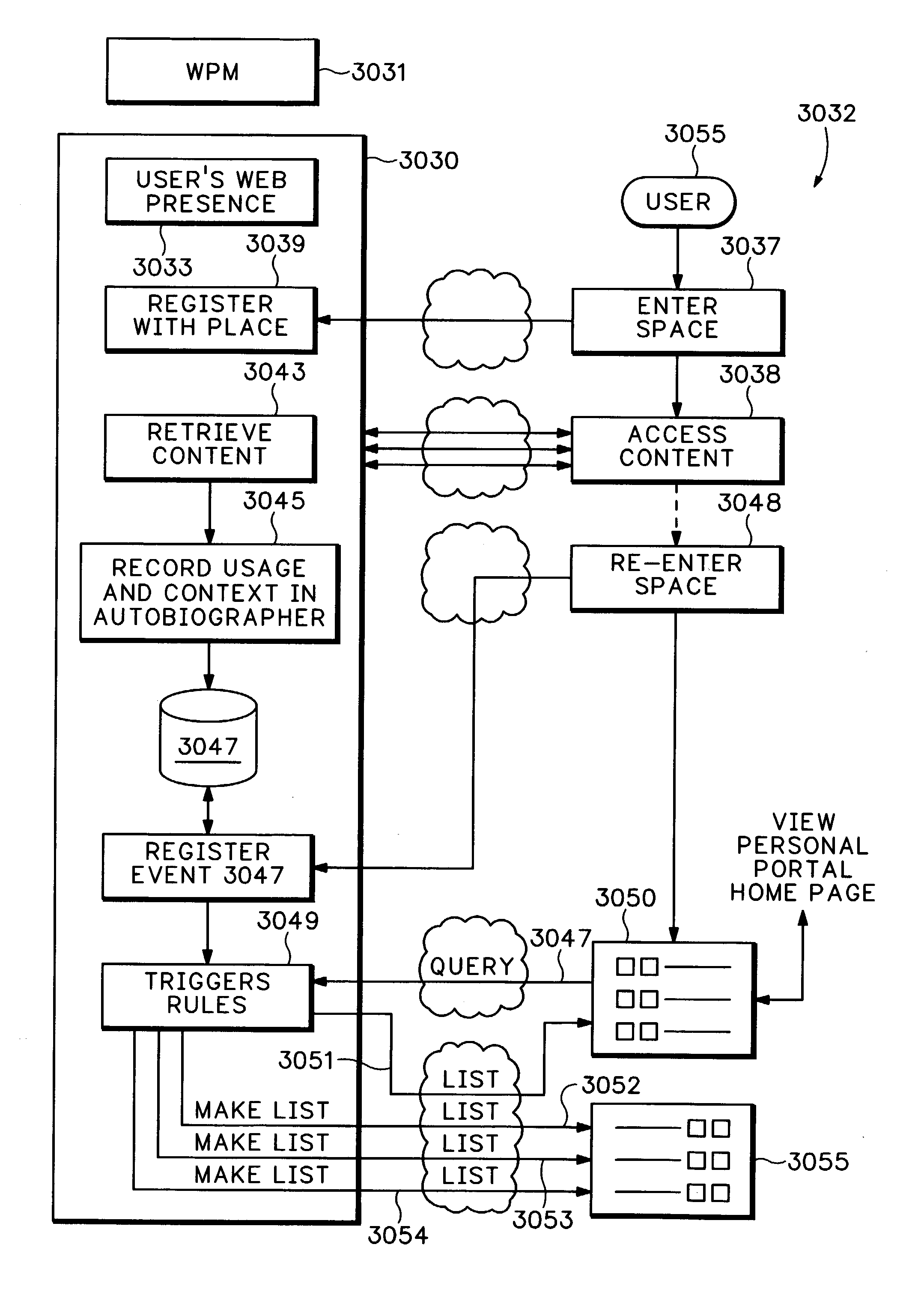
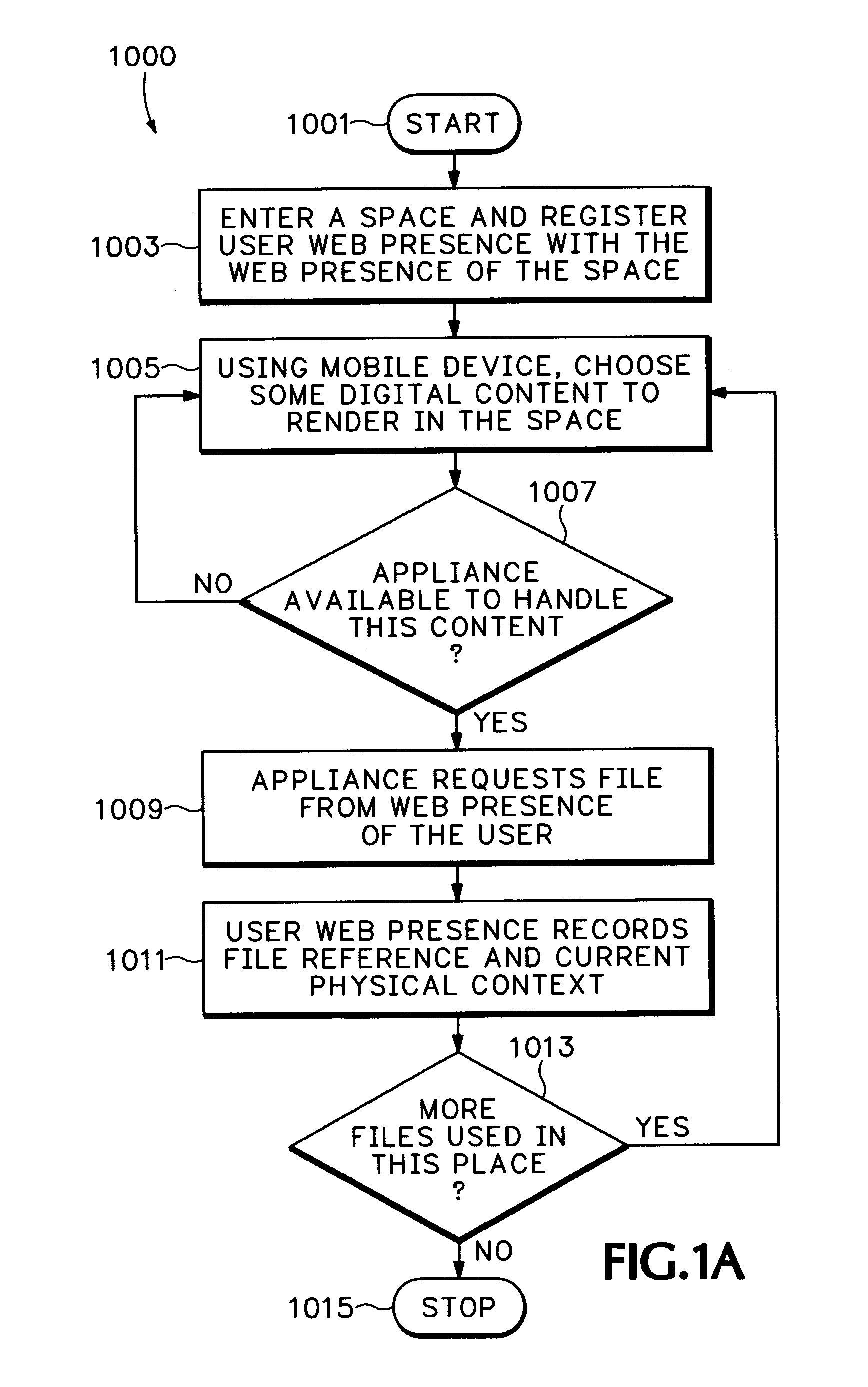
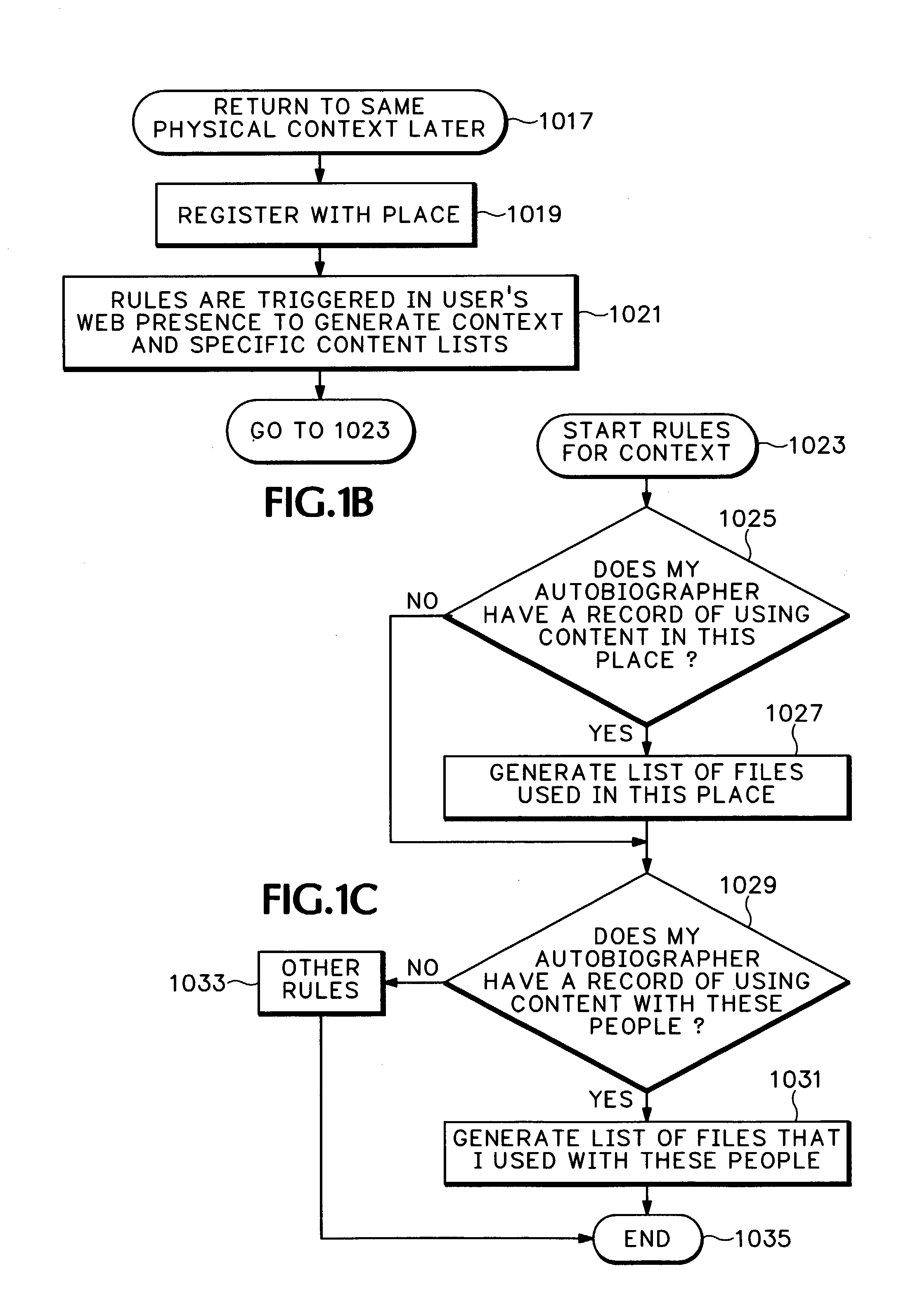
InactiveUS7233990B1Easy to understandMultiple digital computer combinationsOffice automationDocument handlingPhysical context
Using a web presence manager infrastructure (see Appendix), actions, appliance events, and presences are continuously and automatically captured and stored as historical metadata for each physical context managed. The metadata is mapped interactively for all users. Personal content for each user, such as digital file usage, is indexed in association with each physical context. Users personal content from autobiographical web presence manager past events is displayed upon each registration of the user's presence in a current physical context with content recall directly related to the current physical context. Personal content mapping to available services is also provided.
Owner:HEWLETT PACKARD DEV CO LP
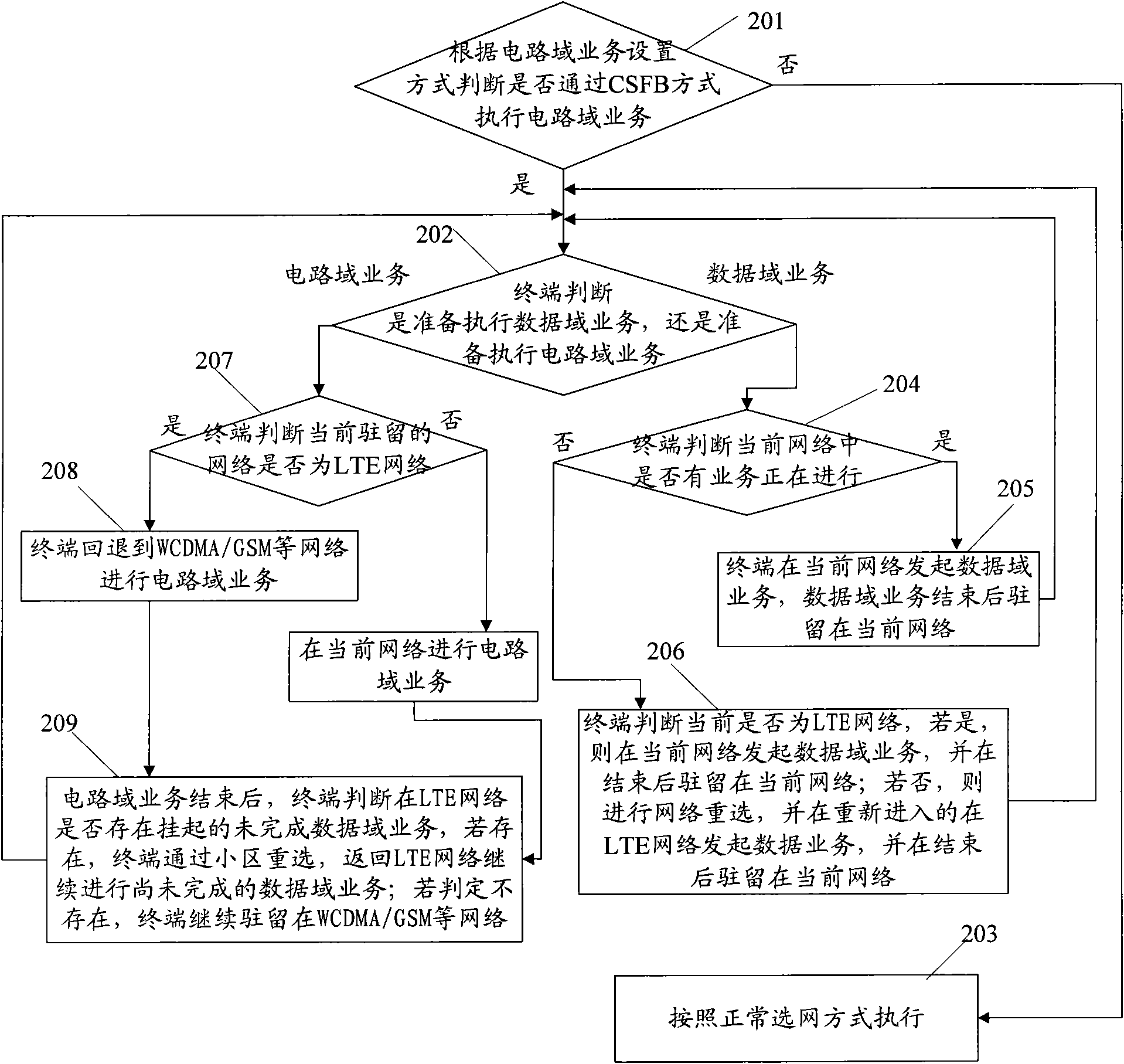
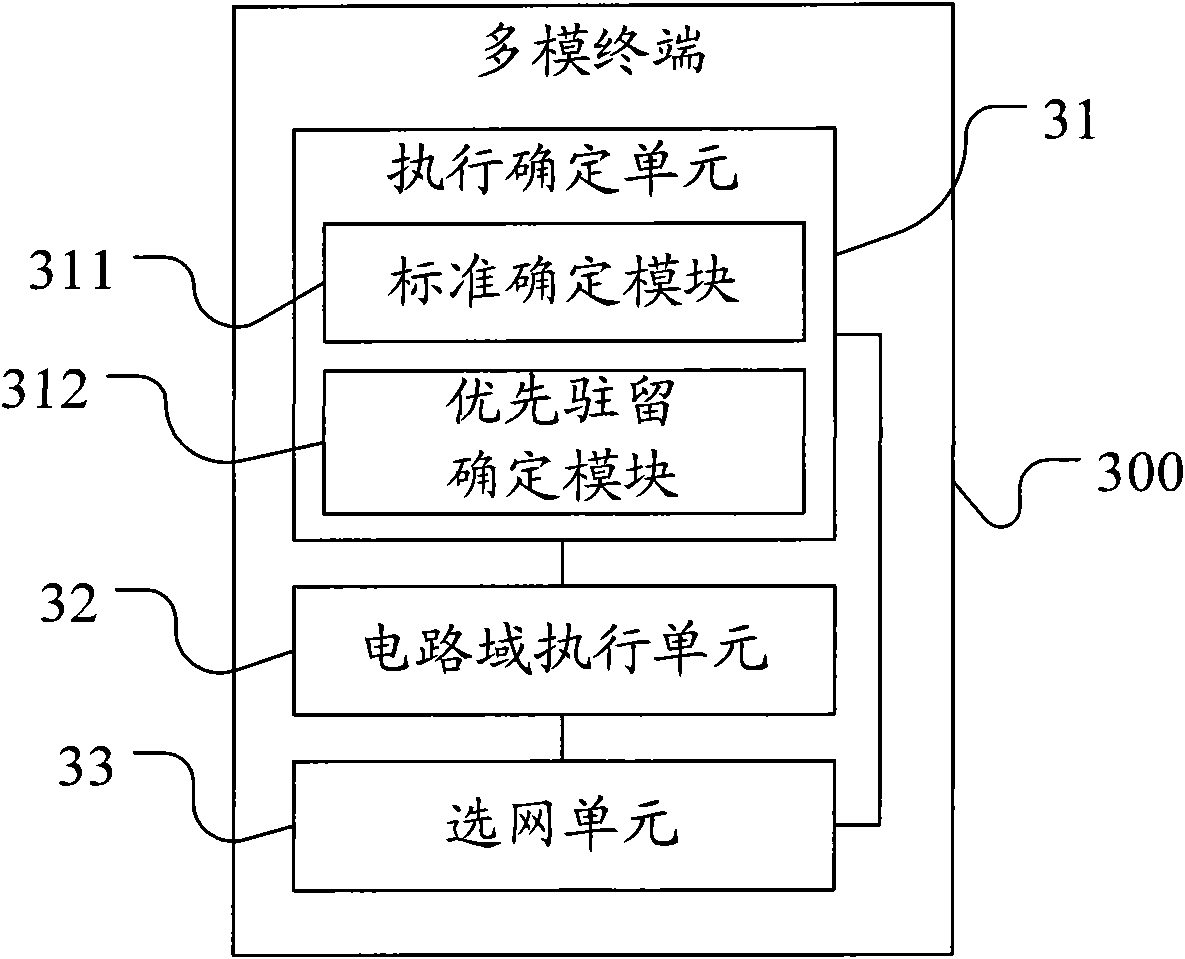
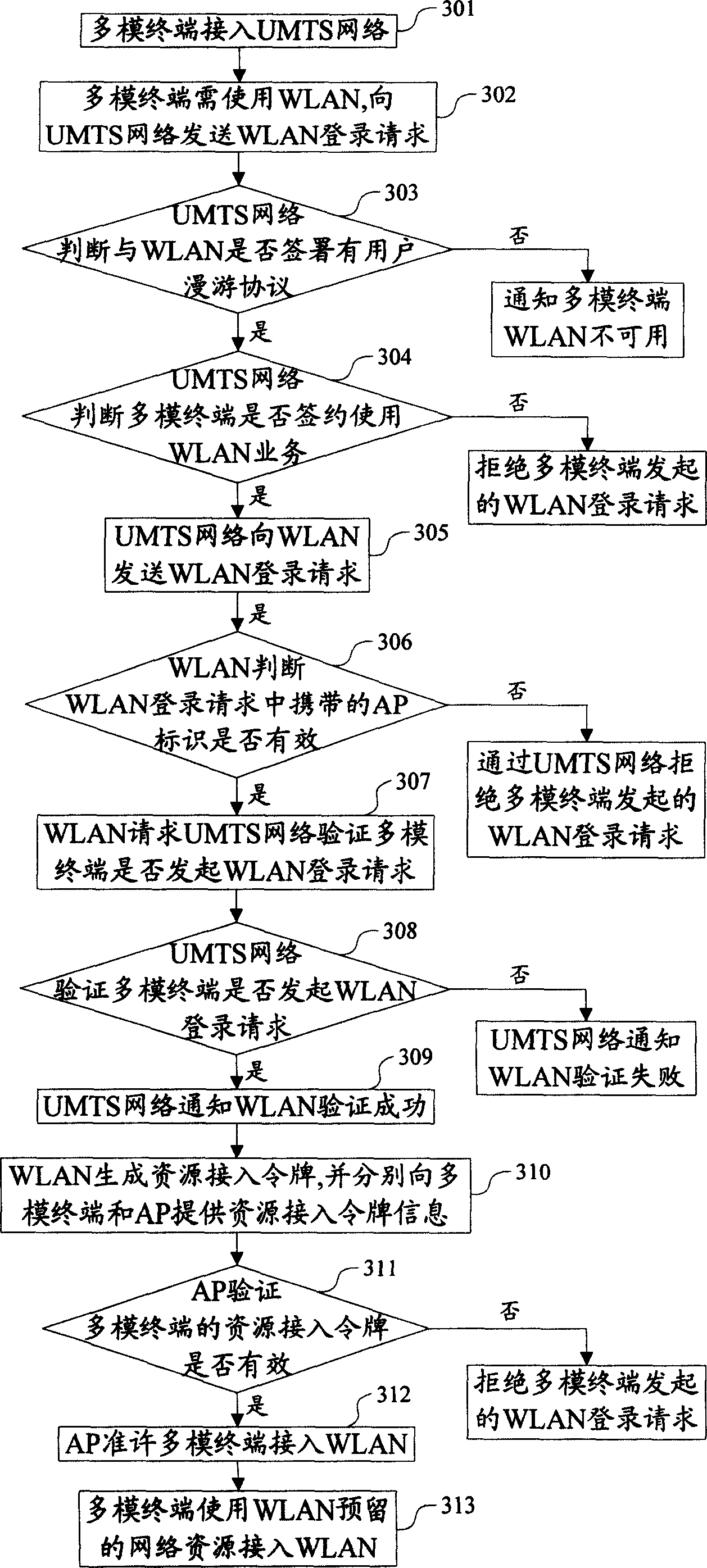
Executing method of multimode terminal network selection and multimode terminal
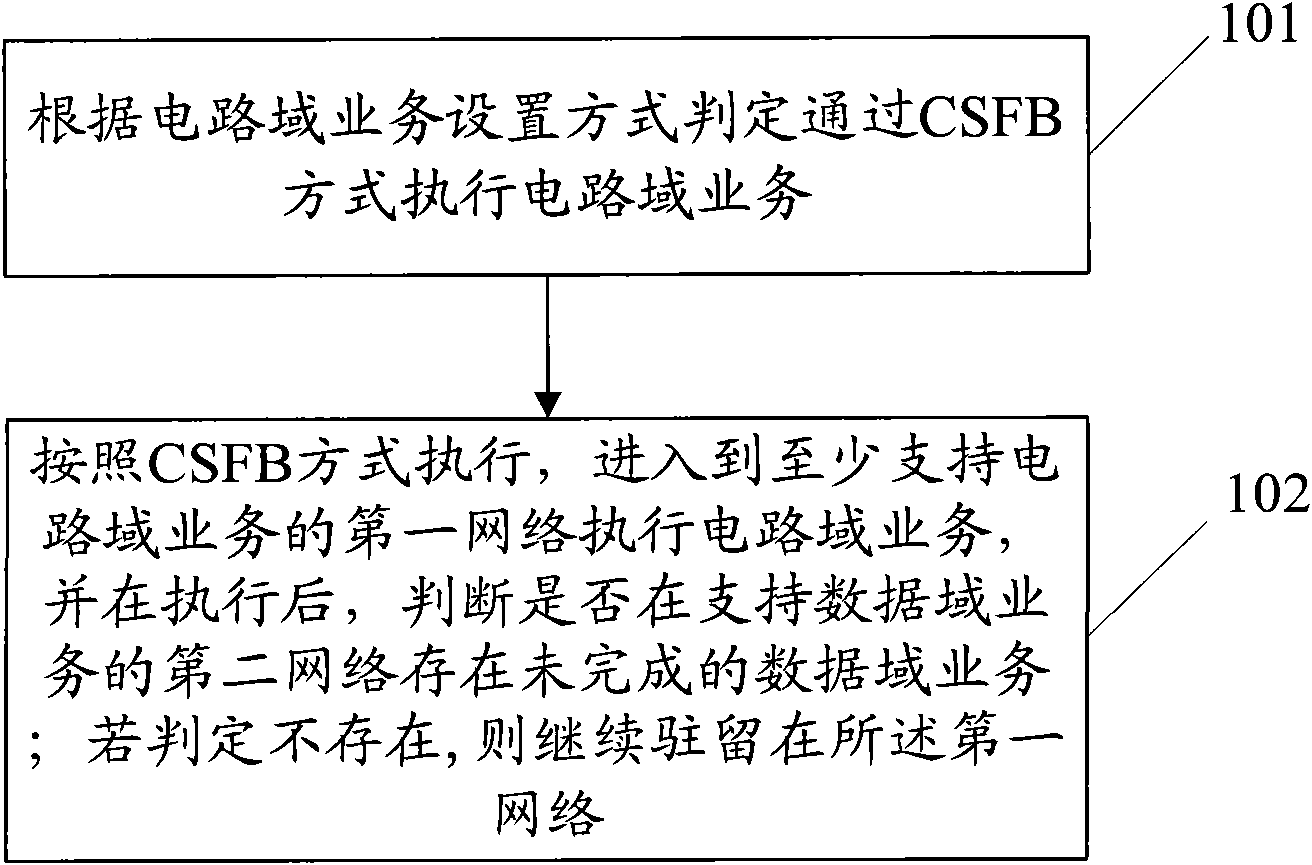
InactiveCN101835246AImprove experienceReduce switchingAssess restrictionData domainDistributed computing
The embodiment of the invention discloses an executing method of multimode terminal network selection and a multimode terminal, relating to the technical field of communication and solving the technical problem that the multimode terminal is frequently switched when a CSFB mode is adopted in the prior art. The method comprises the steps of: judging whether a circuit domain service is executed by the CSFB mode according to a circuit domain switch setting mode; if so, entering a first network executing circuit switch service, and judging whether a hung-up uncompleted data domain service exists in a second network after the circuit domain service is completely executed, wherein the first network at least supports the circuit domain service, and the second network supports the data domain service; and if the hung-up uncompleted data domain service exists in the second network, continuing to remain the first network. The embodiment of the invention is mainly applied to the terminal.
Owner:HUAWEI DEVICE CO LTD
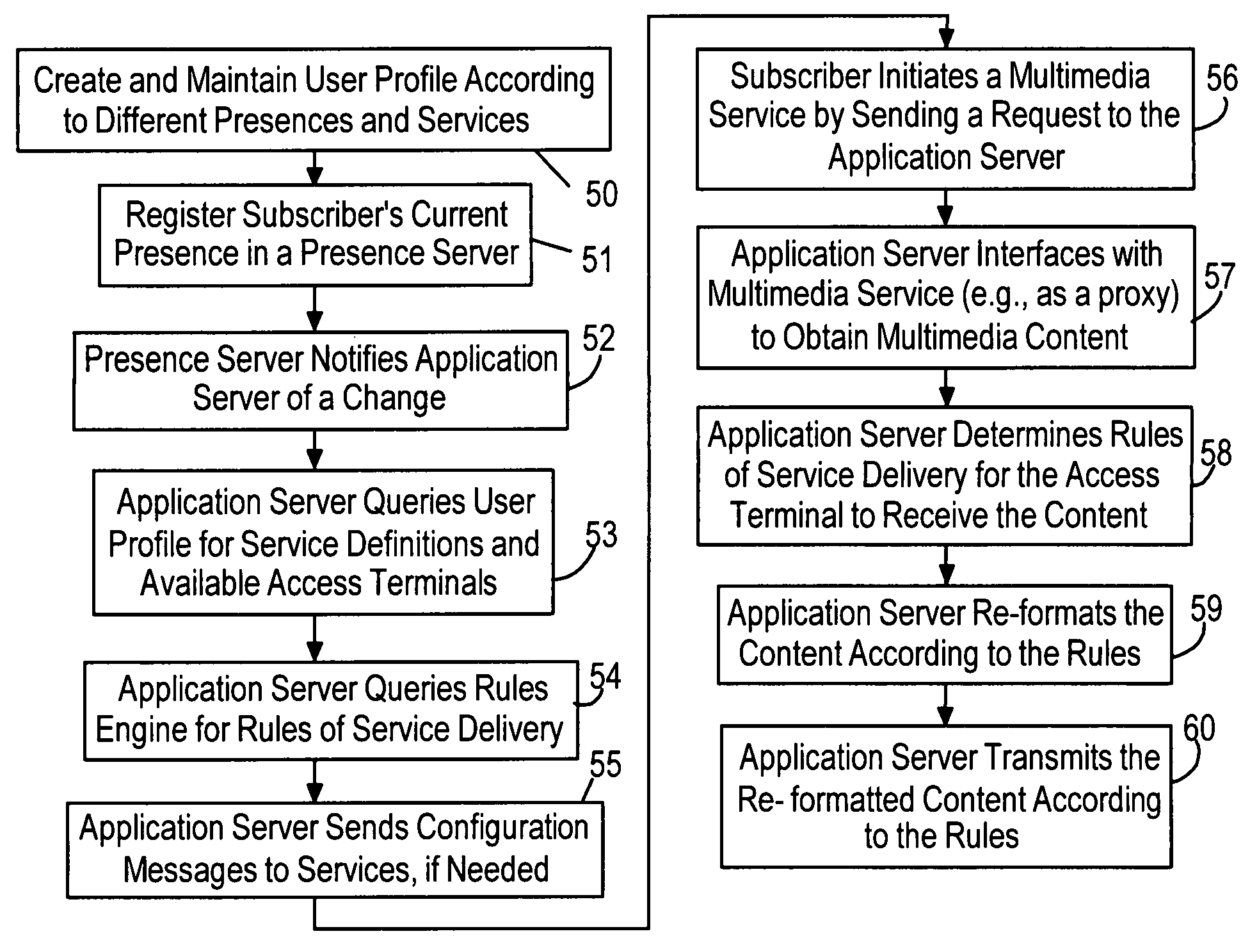
Persona management for mobile enabling services
ActiveUS8126439B1Eliminate needSpecial service for subscribersWireless commuication servicesApplication serverRole management
Multimedia services are provided to a subscriber within a domain of a communication network, wherein the subscriber utilizes one or more predetermined access terminals to access the multimedia services according to a network presence configuration of the subscriber. Each access terminal has respective multimedia capabilities, and the domain includes an application server for accessing the multimedia services. A user profile is established for the subscriber relating respective presence identifiers to a respective user service definition, wherein each user service definition specifies a set of the predetermined access terminals and respective multimedia services to be available for a respective network presence configuration. A current presence identifier of the subscriber is registered. The application server accesses the user profile to determine a user service definition corresponding to the current presence identifier. The subscriber initiates one of the multimedia services by sending a request to the application server from one of the access terminals in the set of predetermined access terminals. The application server interfaces with the multimedia service to obtain multimedia content from the initiated multimedia service. The application server then determines rules of service delivery according to the set of predetermined access terminals. The application server re-formats received multimedia content according to the rules of service delivery for the set of predetermined access terminals. The application server transmits re-formatted multimedia content to the corresponding access terminals.
Owner:T MOBILE INNOVATIONS LLC
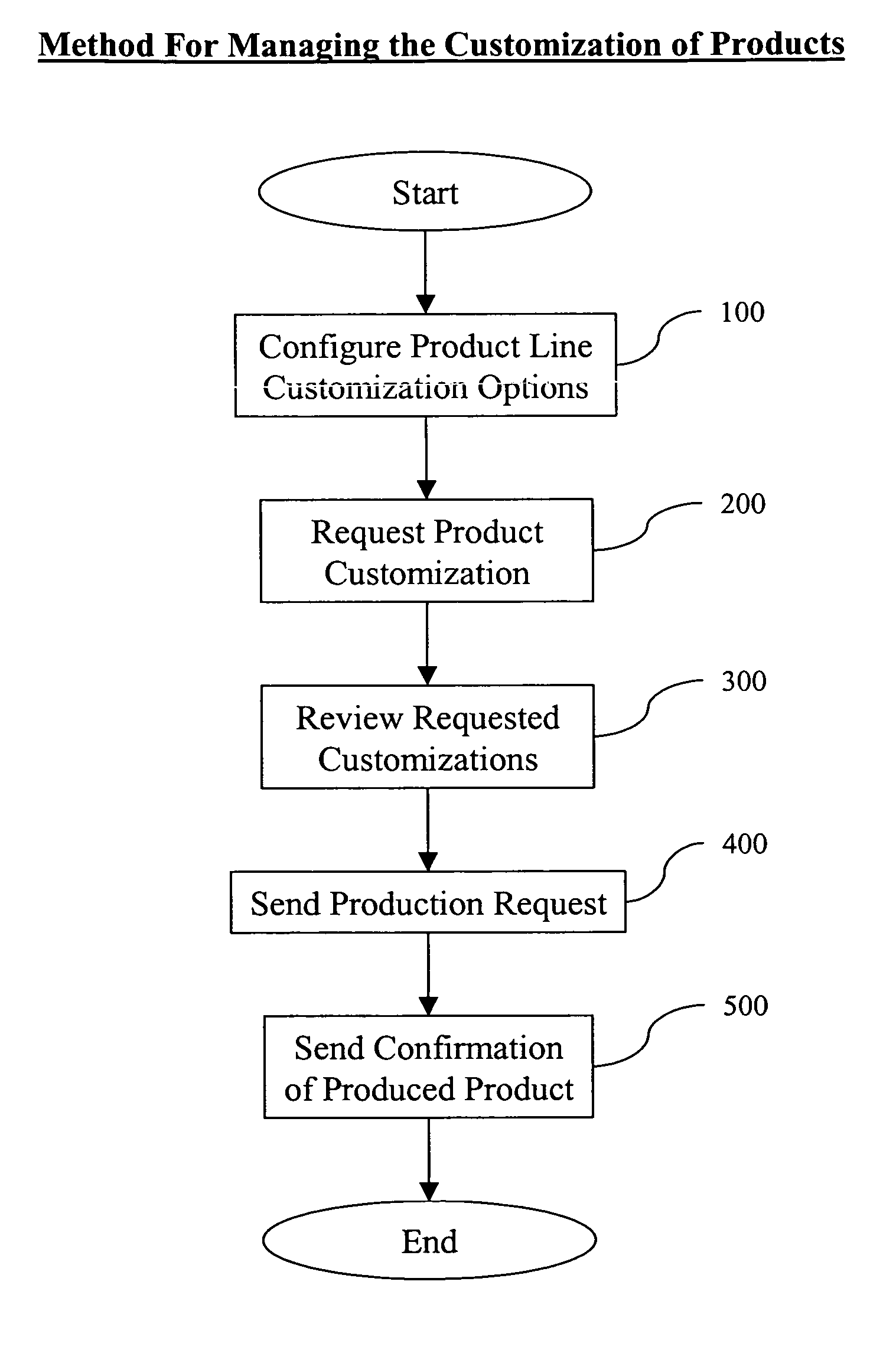
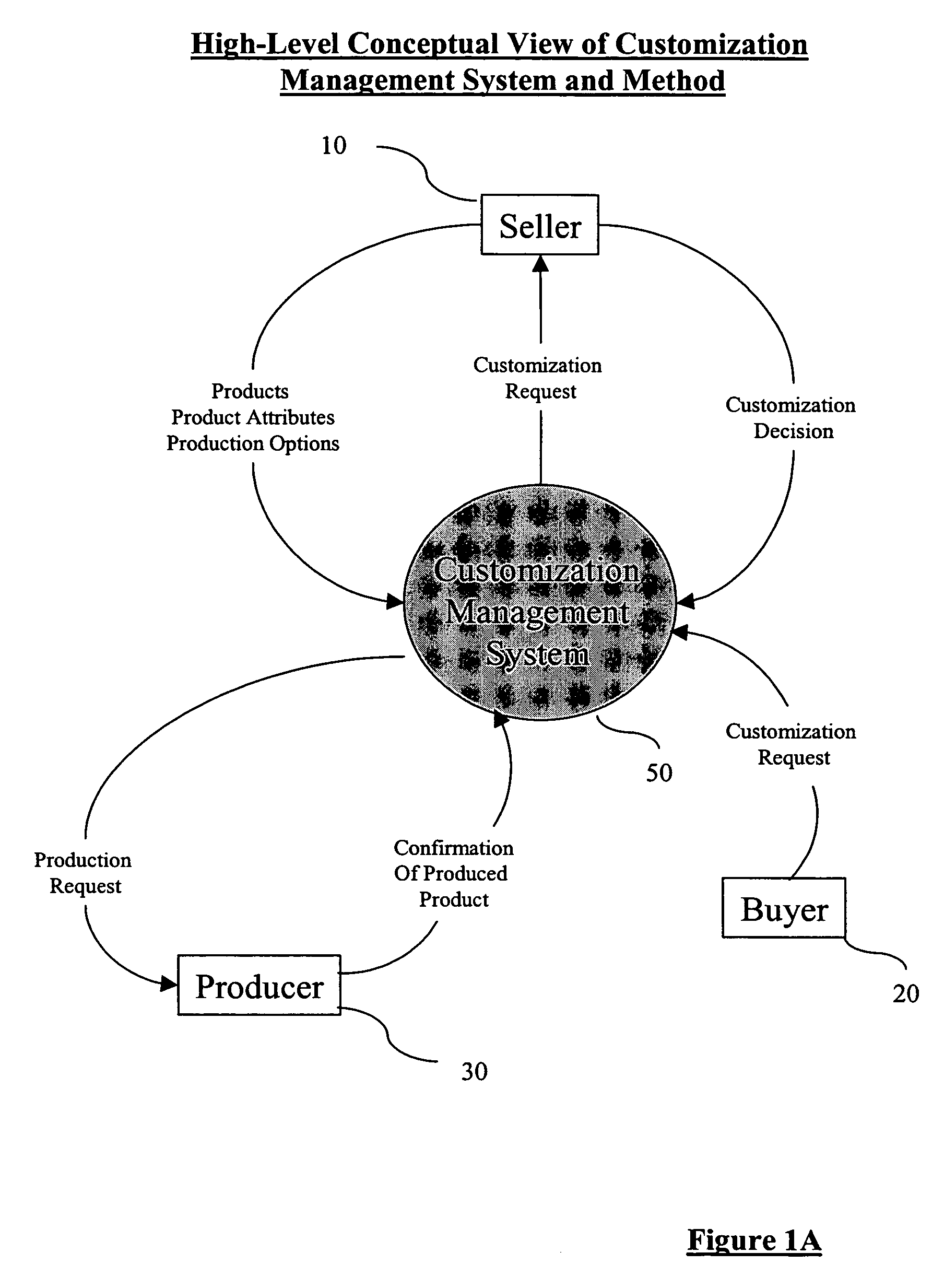
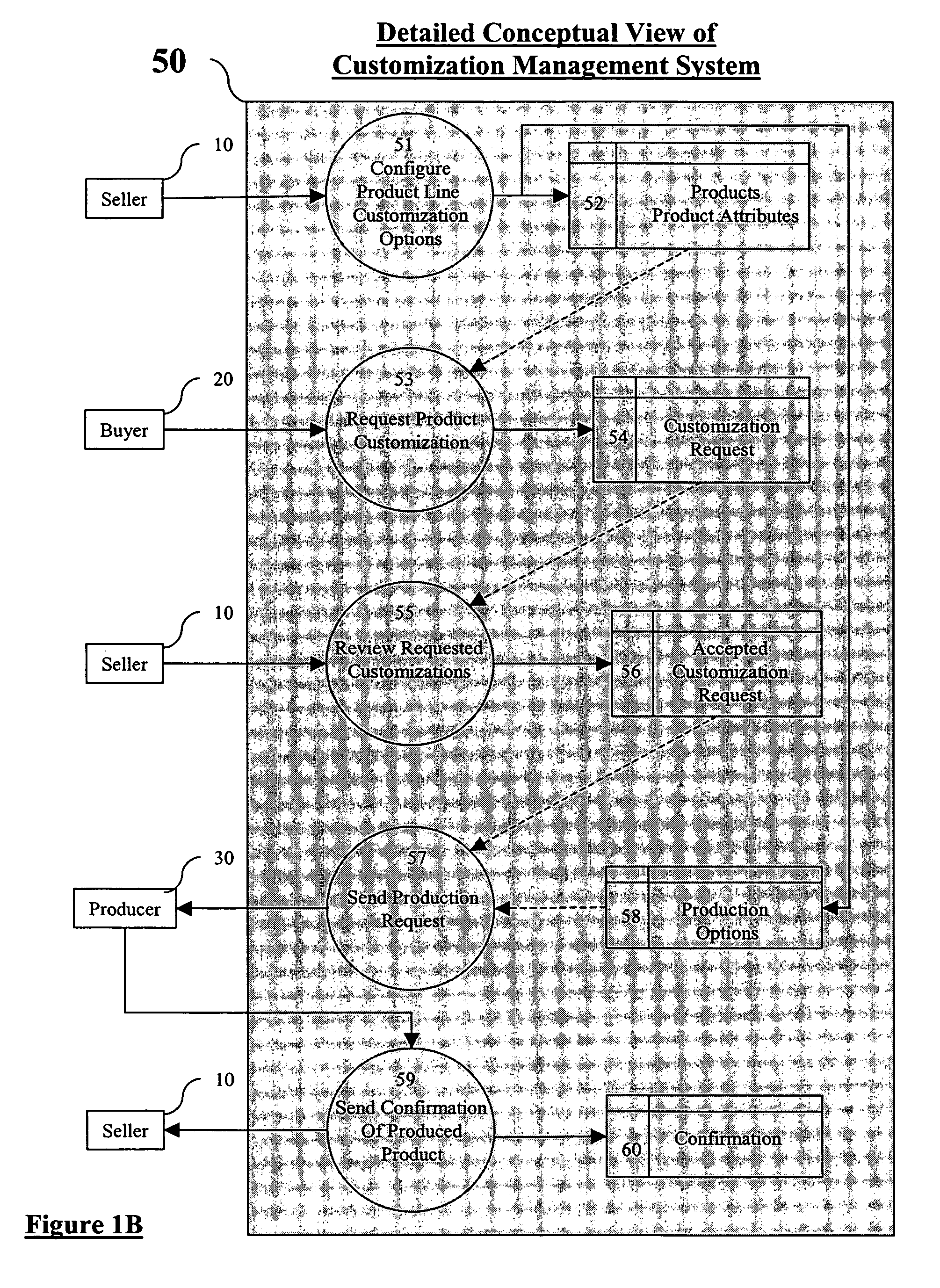
System and method for managing product customization
Systems and methods for managing the customization of products can be implemented to facilitate the cooperative efforts of sellers, buyers, and producers of customizable products through a common, loosely coupled, remote system. This system may be implemented via a web-based software system as a hosted solution or as an easily integrated solution to the existing web presence of the seller.
Owner:DIMPLE DOUGH
Browse type service perception analysis method
The invention relates to a browse type service perception analysis method and belongs to the mobile communication field. With the browse type service perception analysis method adopted, massive user browse type service perception data acquired from a terminal side can be effectively utilized to analyze, position and delimit causes in the whole-network level for poor browse type service perception of users, and therefore, related parameters, algorithms, protocols and the like of a network can be optimized, so that the ability of the mobile network to carry browse type services can be improved, and references can be provided for the improvement of the browse type service perception of the users. According to the browse type service perception analysis method, causes for poor browse type service perception are analyzed according to terminal data acquired in actual mobile networks, namely, a plurality of 3G networks of regional and municipal telecommunications companies, and serious problems such as excessively long DNS resolution time and long time delay of the first packet of the Sina website exist in a certain network; and the problems are confirmed by the optimization departments of the telecommunications companies, and the optimization departments of the telecommunications companies carry out corresponding network adjustment, for example, optimize DNS servers and increase local Sina CDN servers, and subsequent tests also verify that the problems are solved, and indexes are improved.
Owner:BEIJING UNION UNIVERSITY
System and method for communications management with a network presence icon
InactiveUS6510452B1Data processing applicationsMultiple digital computer combinationsCommunications managementTelecommunications
Owner:RPX CLEARINGHOUSE
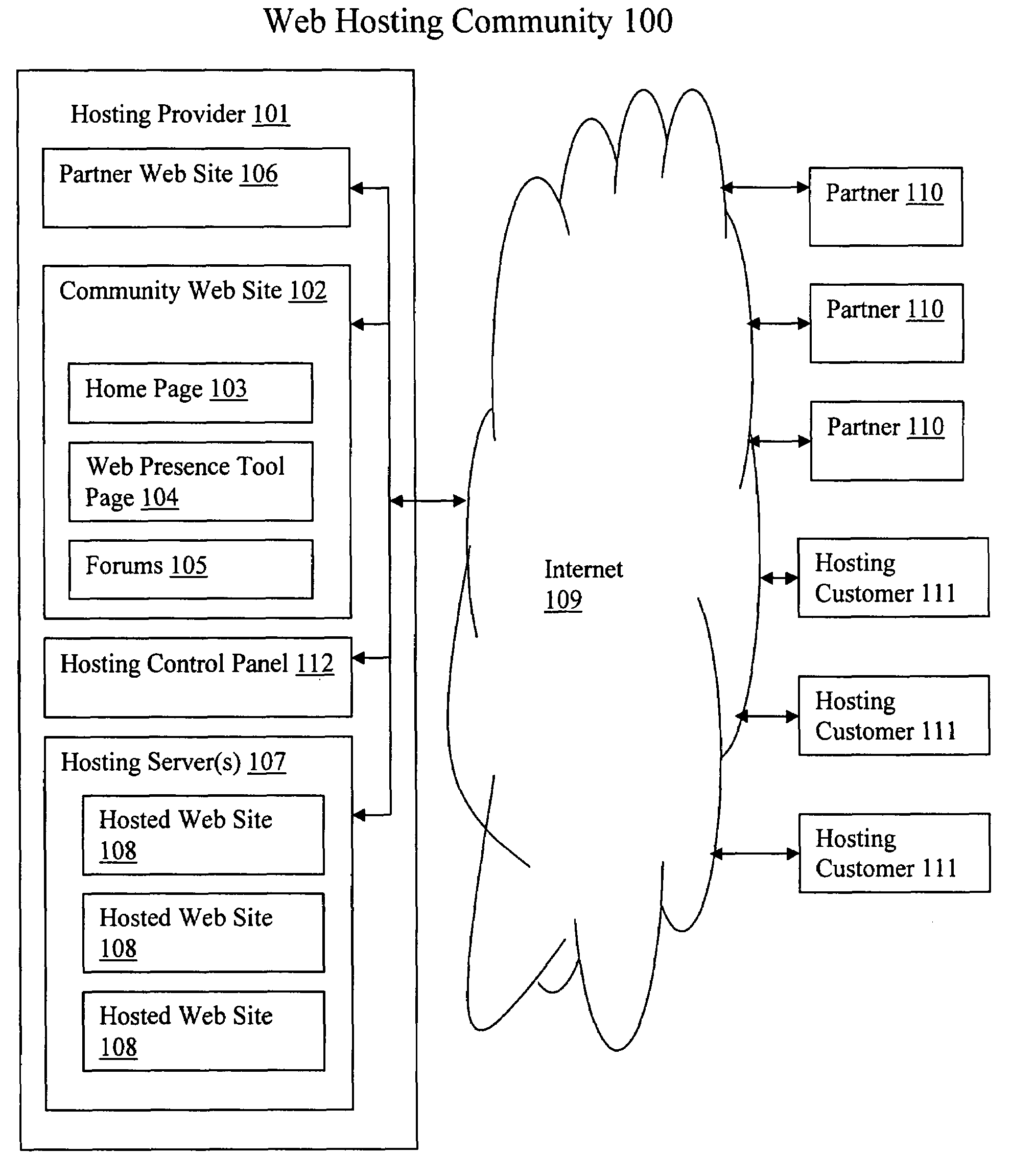
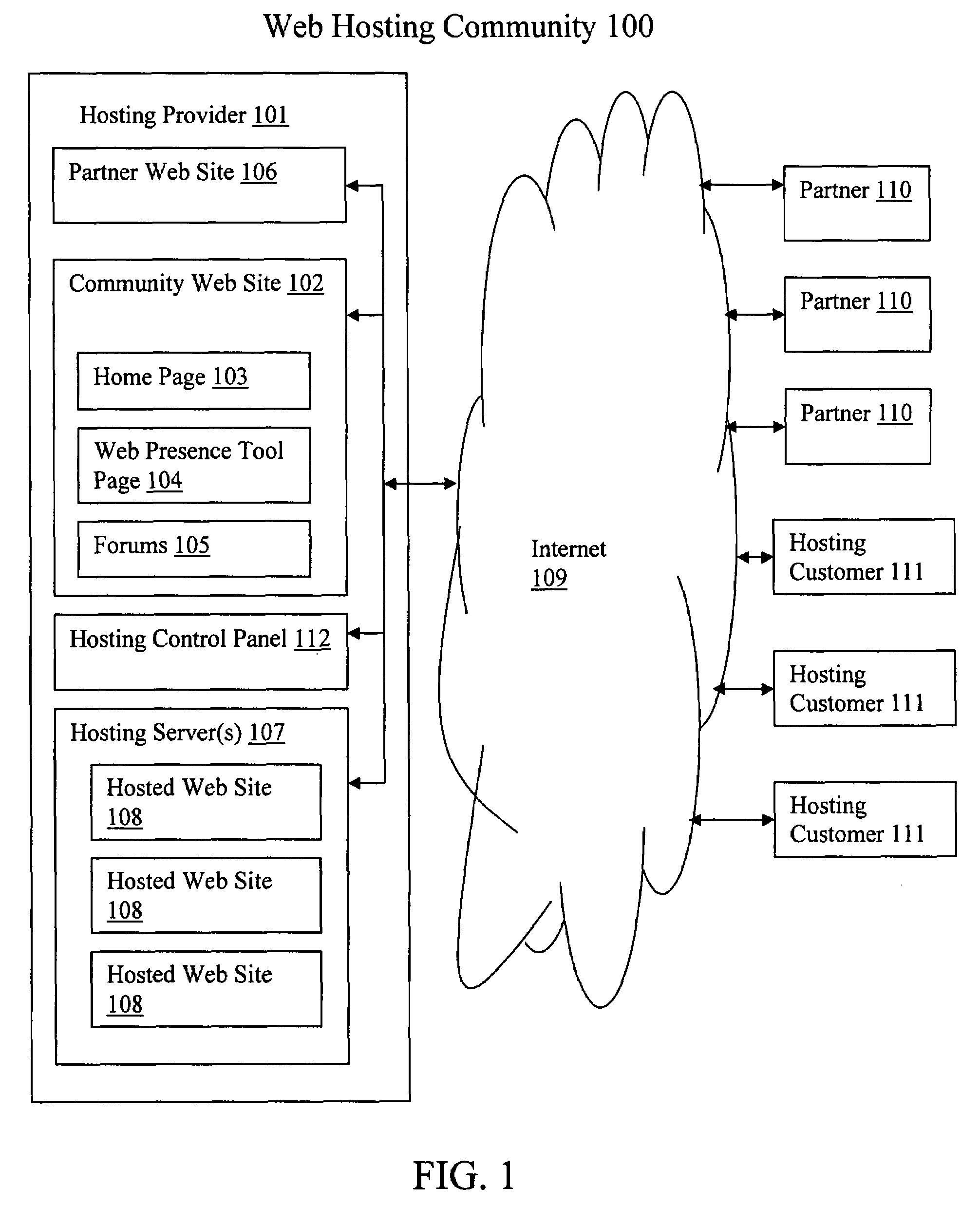
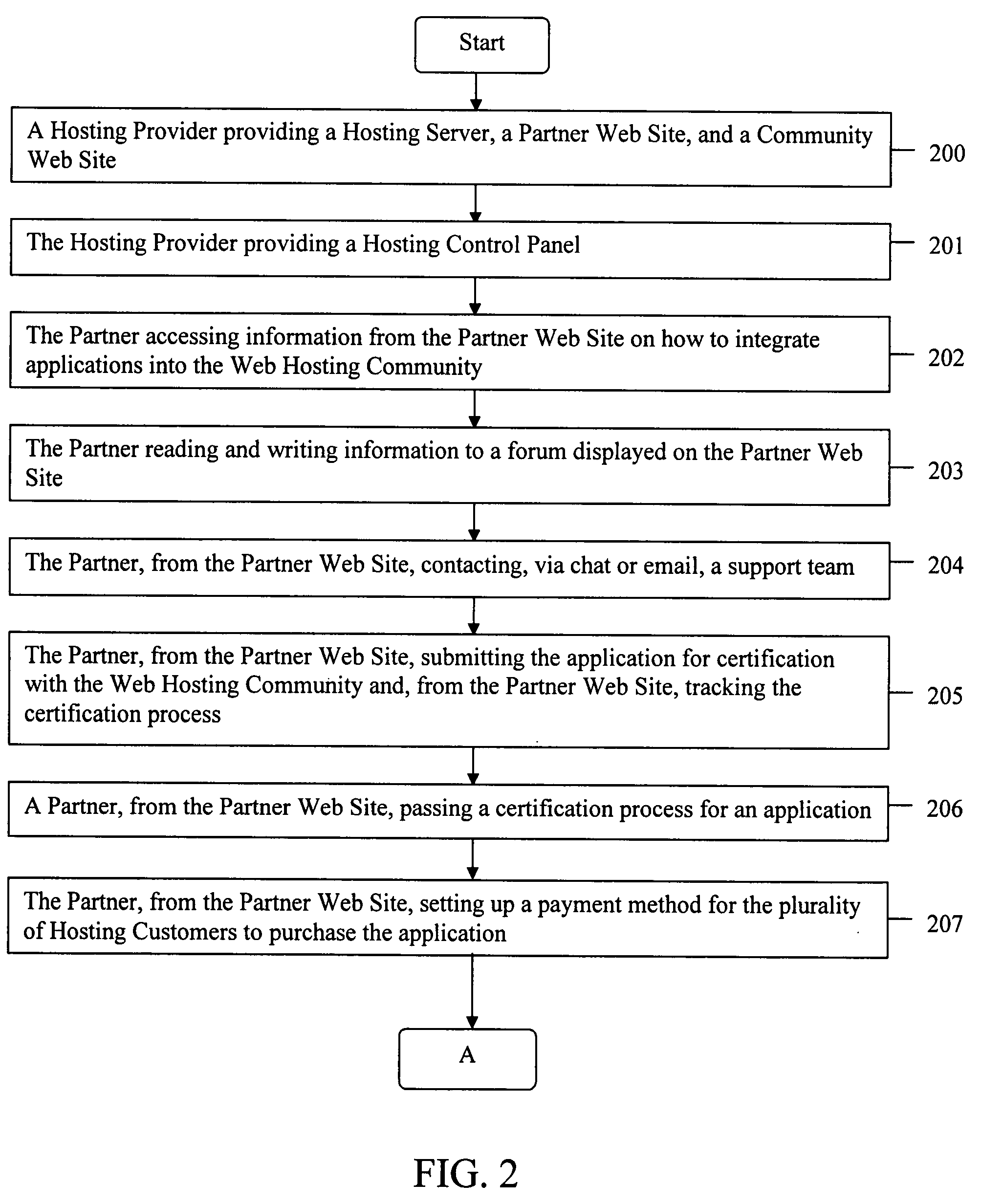
Community web site for creating and maintaining a web hosting community
ActiveUS20080201421A1User identity/authority verificationMultiple digital computer combinationsWeb siteHome page
An example embodiment of a Community Web Site includes a Home Page, a Web Presence Tool Page, and a Product and Community Forum which is created and maintained by a Hosting Provider. The Home Page may be made accessible to Hosting Customers and Partners and is an ideal location for placement of ads since all members of the Web Hosting Community are funneled through this Web page. The Web Presence Tool Page may display information generated by a Partner regarding the Partner's application which may be viewed by the Hosting Customers. The Product and Community Forum may allow the Hosting Customers to share information regarding all the applications with other Hosting Customers.
Owner:GO DADDY OPERATING
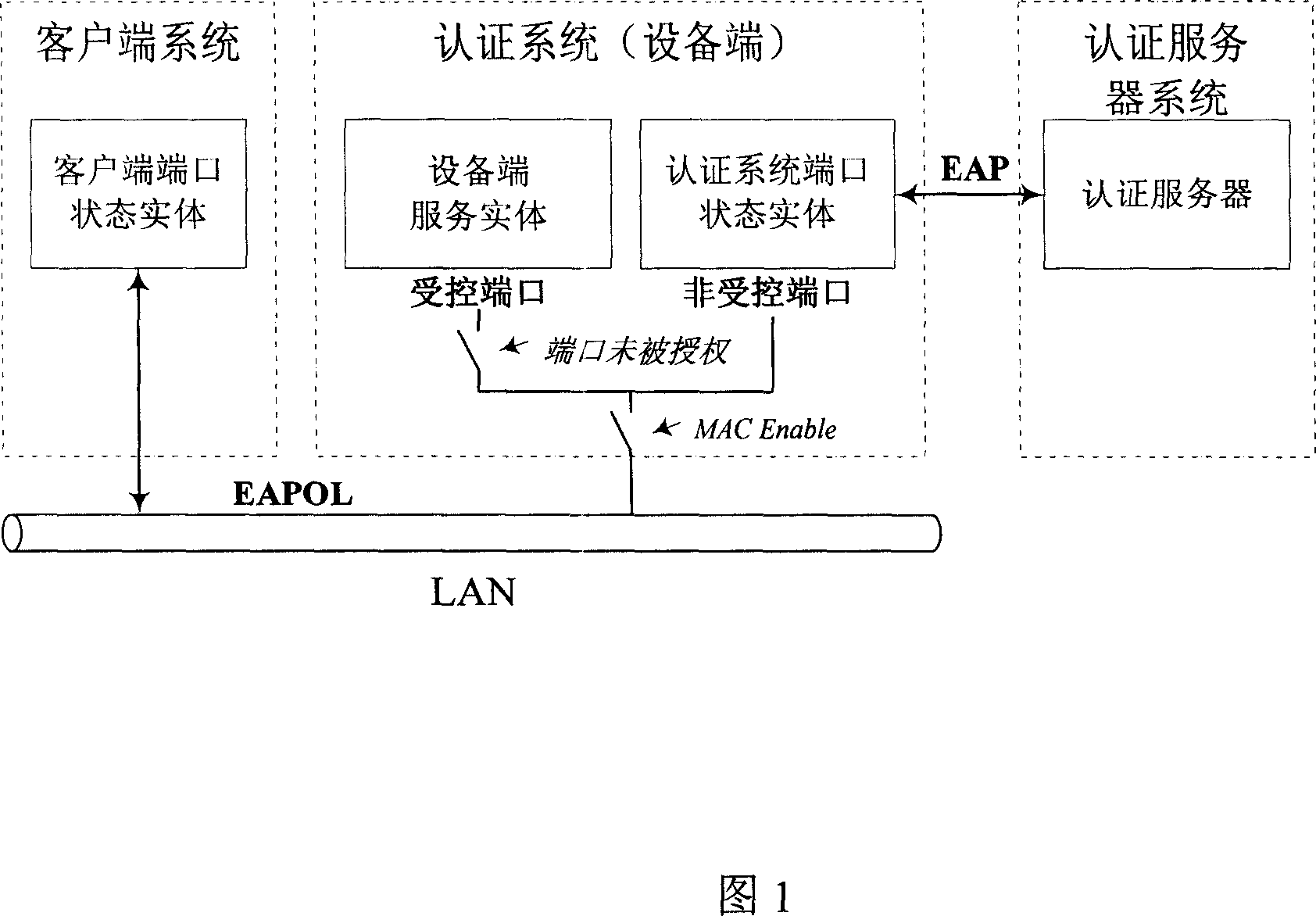
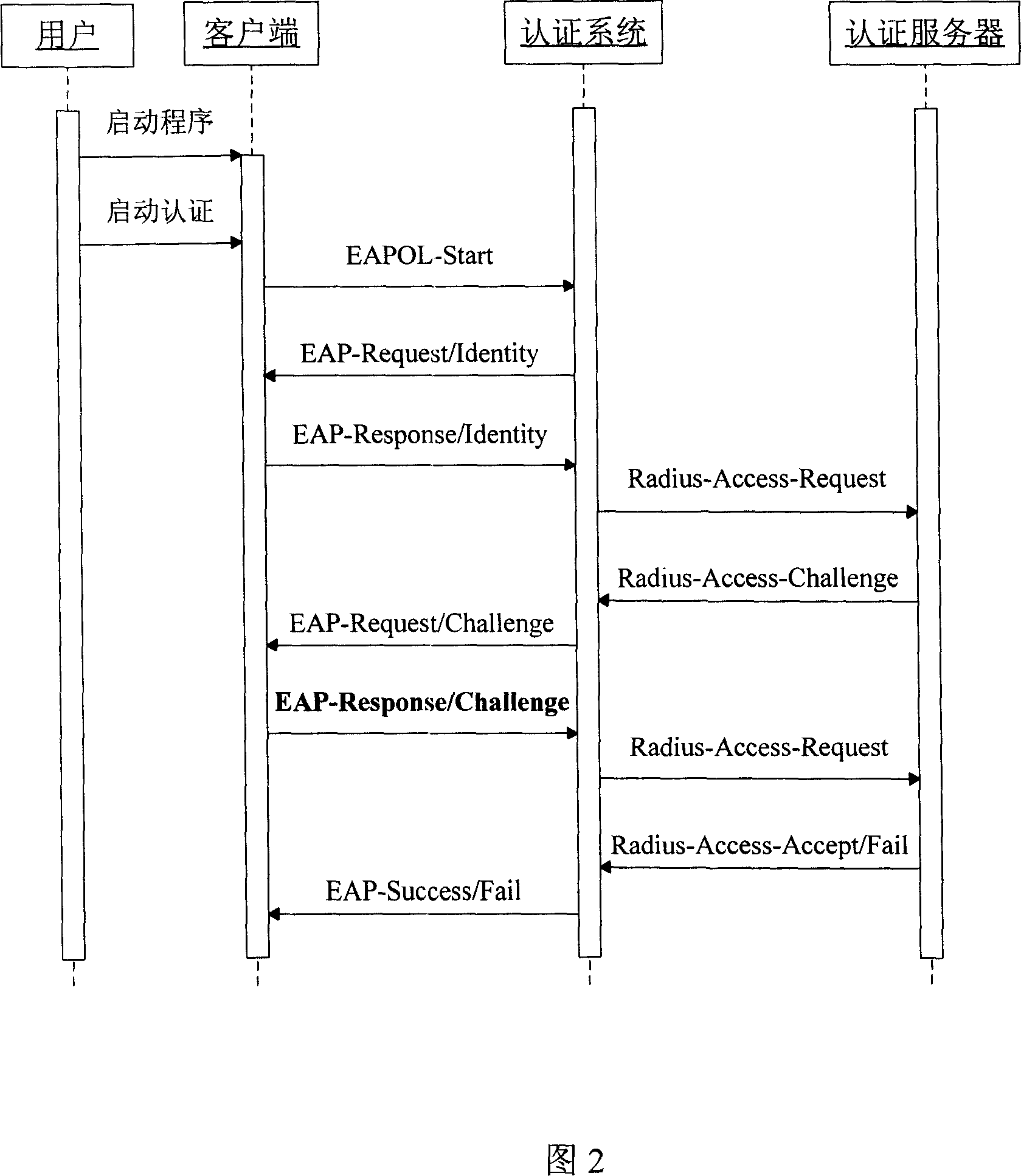
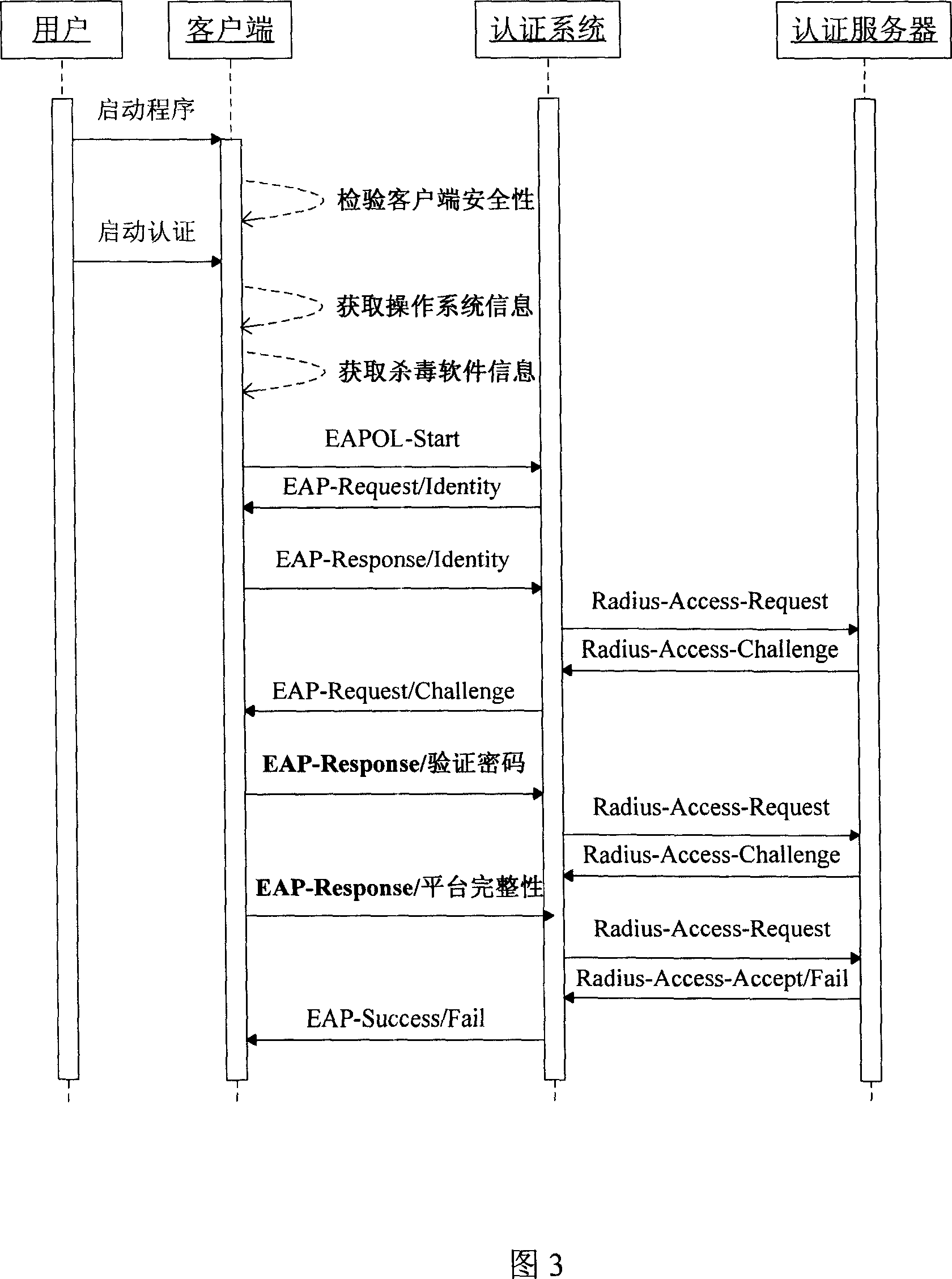
An expansion security authentication method based on 802.1X protocol
InactiveCN1997026AUser identity/authority verificationData switching by path configurationOperational systemSecurity authentication
This invention relates to one extensive safety identification method based on 802. 1X and its method, which adopts identification and monitor idea to need to measure the operation system, virus killing software, customer end identification program and uses the measurement result as identification message with only customer end system meet standard through user codes testing for legal user; if not updating the system.
Owner:BEIJING UNIV OF TECH
Video backup method and system based on security and protection home gateway
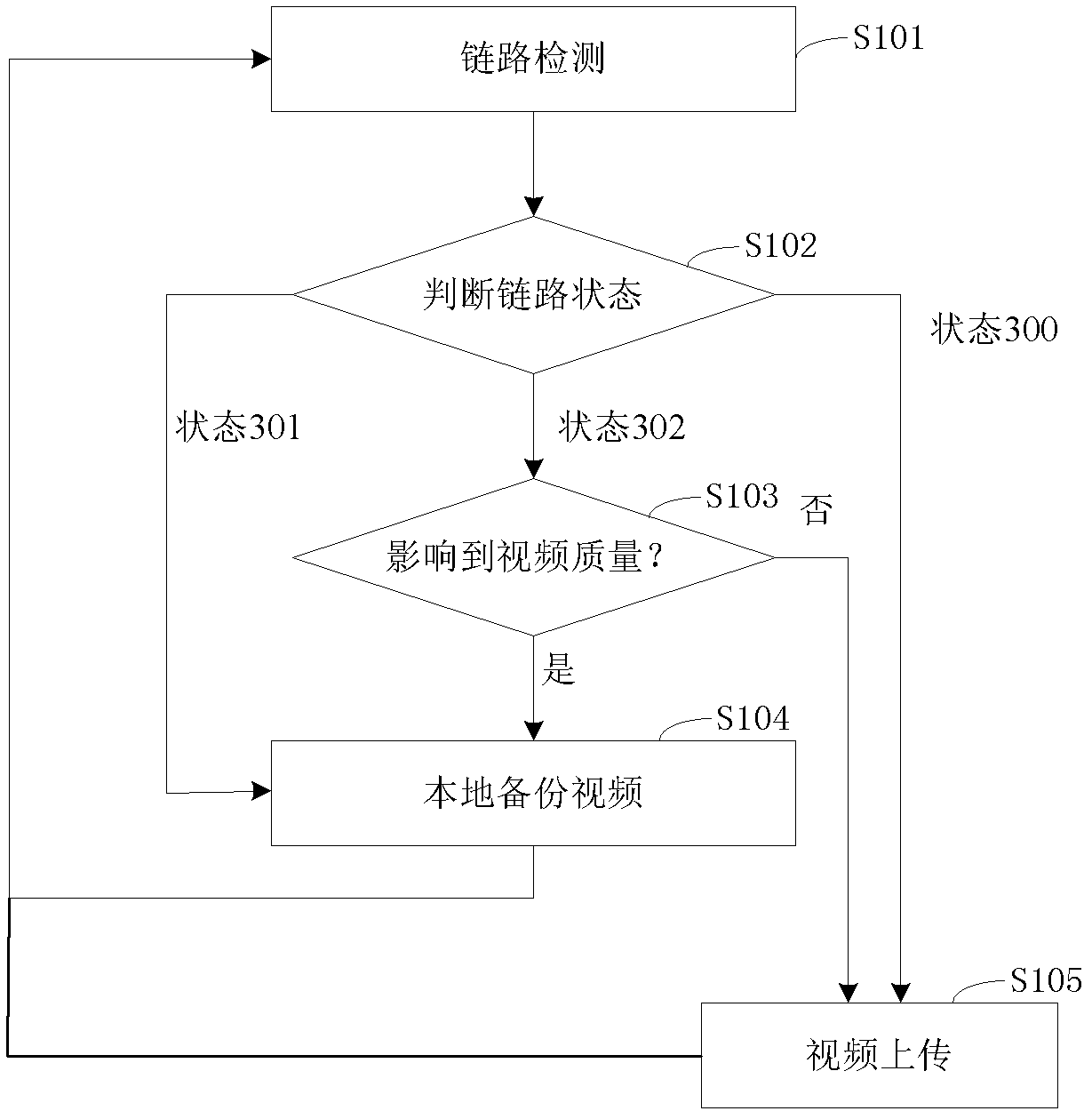
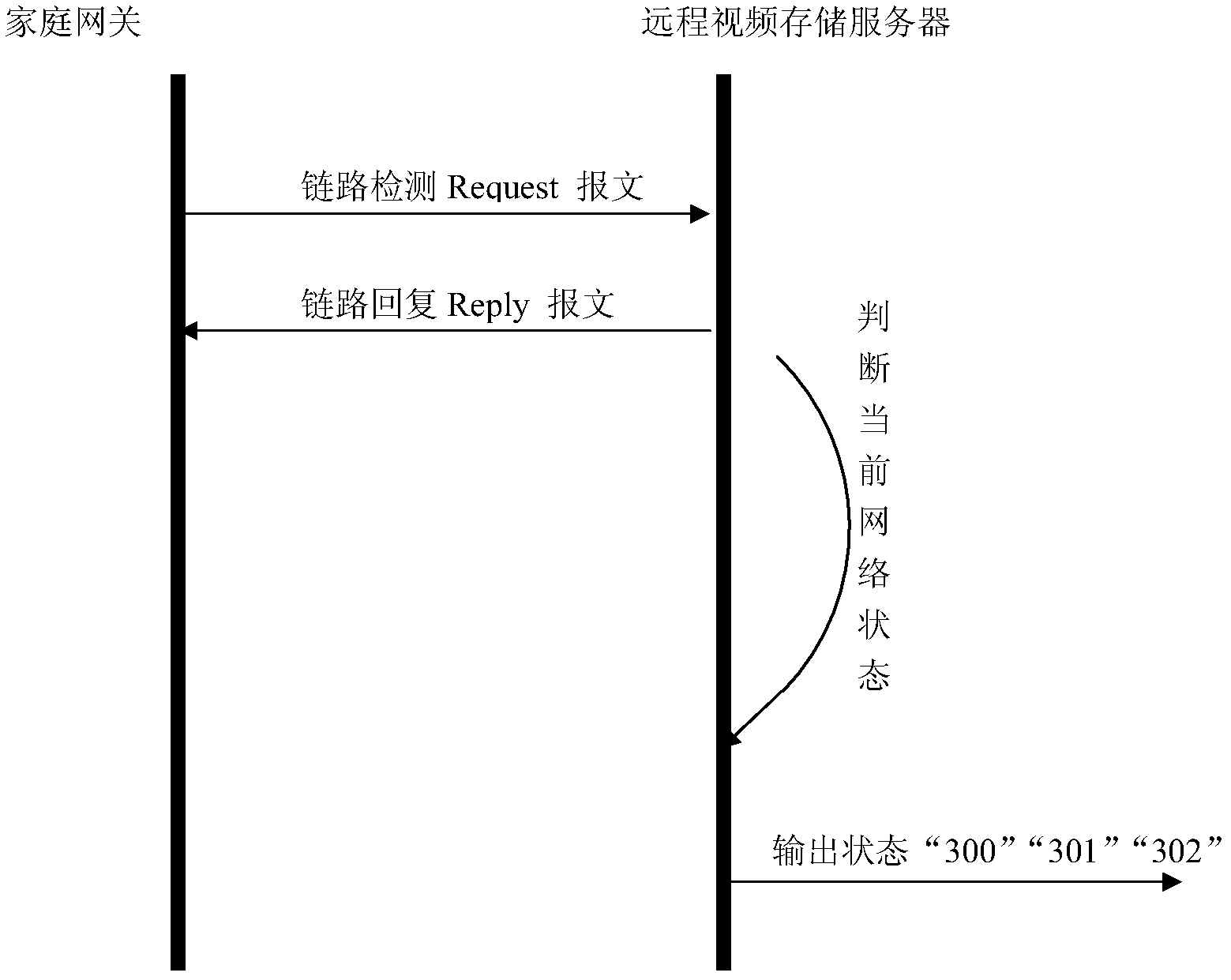
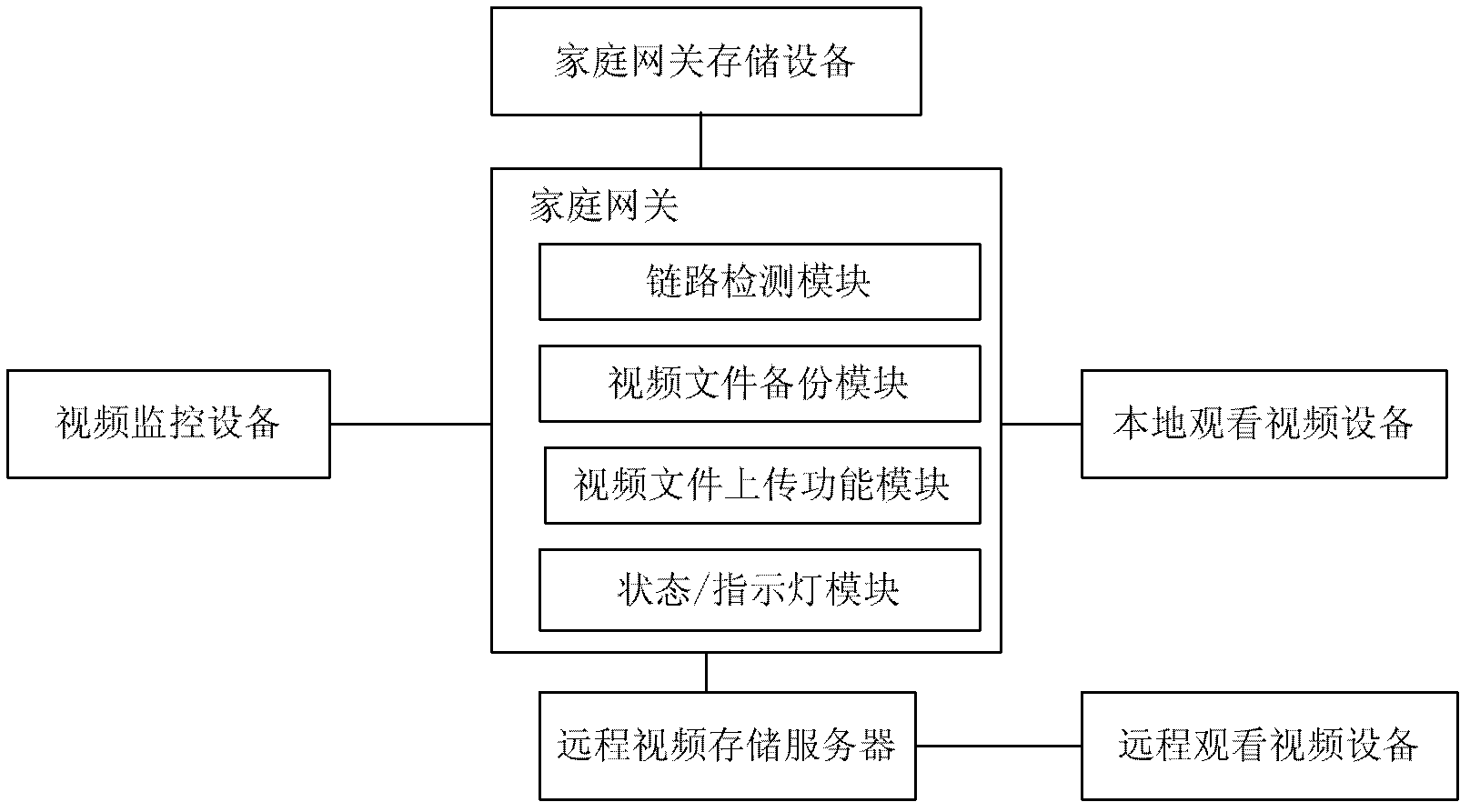
InactiveCN103024326AIntegrity guaranteedAvoid lossTelevision system detailsColor television detailsVideo storageData loss
The invention discloses a video backup method and system based on a security and protection home gateway. The video backup method comprises the following steps that: the home gateway of a network video system periodically sends a link detection report to a server and judges whether a current network state is normal or not according to a link reply report responded by the server; if the current network state is normal, the home gateway uploads current video data of the network video system to the server; and if the current network state is abnormal, the home gateway stores the current video data of the network video system to a local storage space of the home gateway. The video backup method and system provided by the invention solve the problem that a home gateway monitoring video cannot be stored into a long-distance video storage server when the long-distance video storage server or a network is abnormal in the prior art through a local data backup mechanism when the network is abnormal, so that the integrity of video data can be effectively ensured, and the risk of losing the video data can be reduced.
Owner:ZTE CORP
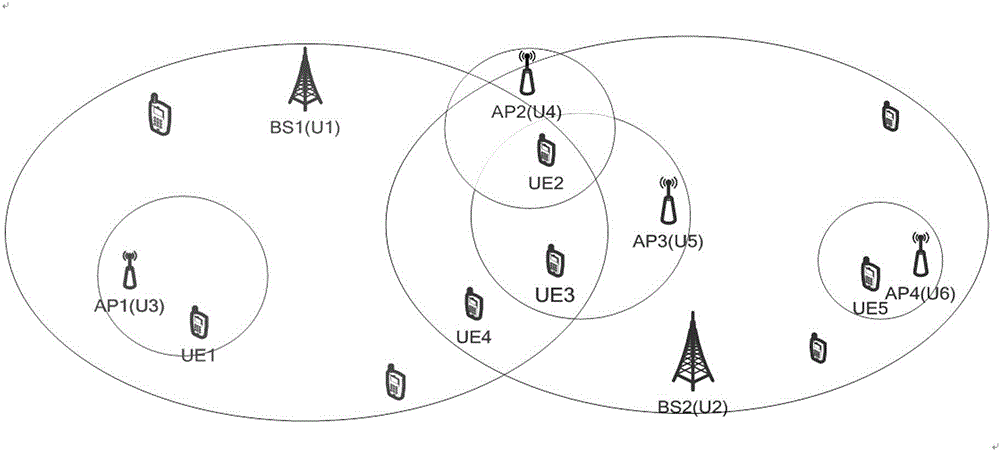
Load balancing method based on forced switching in heterogeneous wireless network system
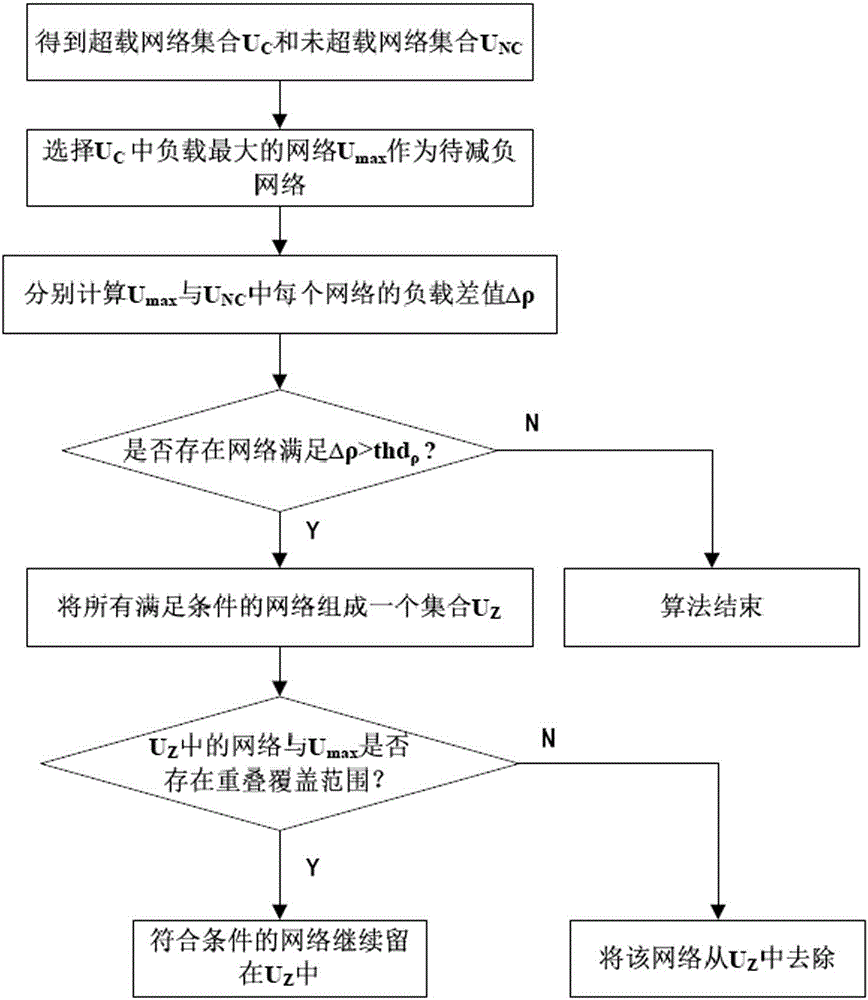
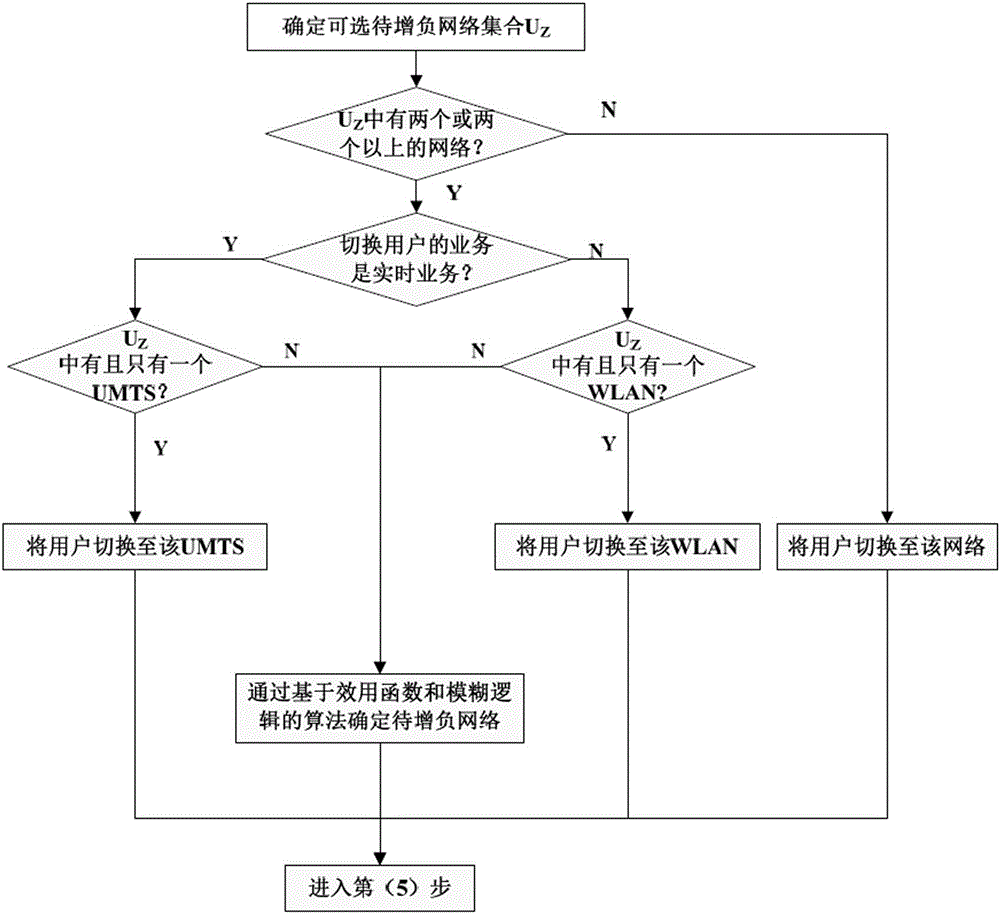
ActiveCN105188091AImprove service qualitySatisfied with the serviceNetwork traffic/resource managementResource utilizationHeterogeneous wireless network
The invention relates to a load balancing method based on forced switching in a heterogeneous wireless network system. The method comprises a) determining whether the load is greater than the threshold; b) determining the network set waiting for load increasing because the difference value of load is greater than a preset threshold value and an overlapping coverage area exists in the network waiting for load decreasing and in the heterogeneous wireless network; c) utilizing a user selection strategy for comprehensively considering the business rate, the fairness, the QoS profit and the network wireless resource utilization rate to select a target switching user; d) switching the target terminal, determining the network waiting for load increasing through a network selection algorithm based on a utility function and fuzzy logic, and switching the target; and e) determining whether the load is balanced. The load balancing method can automatically search out a suitable network waiting for load increasing and switch the target user when an overload network exists, and the user is switched to the network waiting for load increasing to realize load decreasing of the overload network, so that well running of each wireless network can be guaranteed and satisfying service can be always supplied to the user.
Owner:SHANDONG UNIV OF FINANCE & ECONOMICS
Wireless multimedia sensor network routing method for guaranteeing QoS
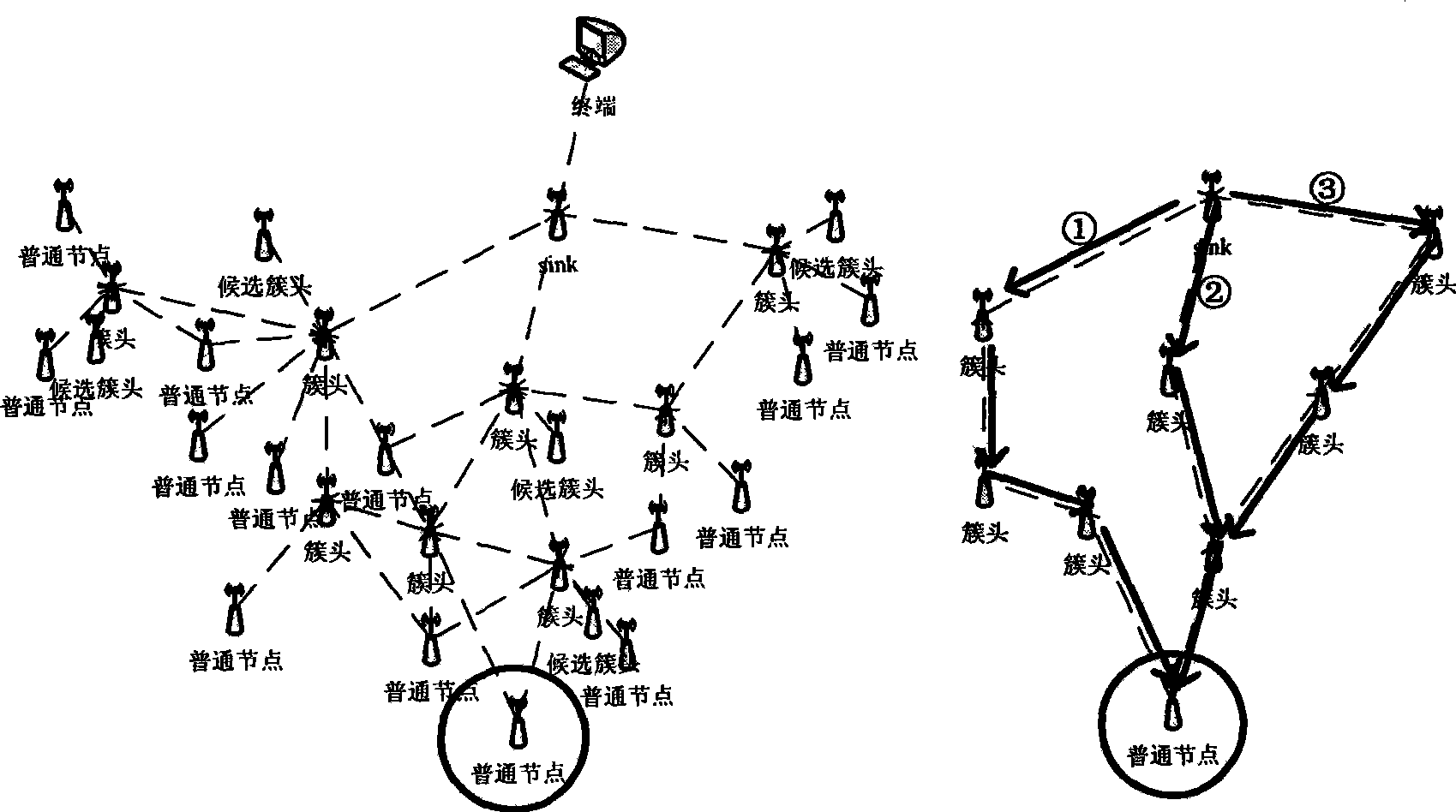
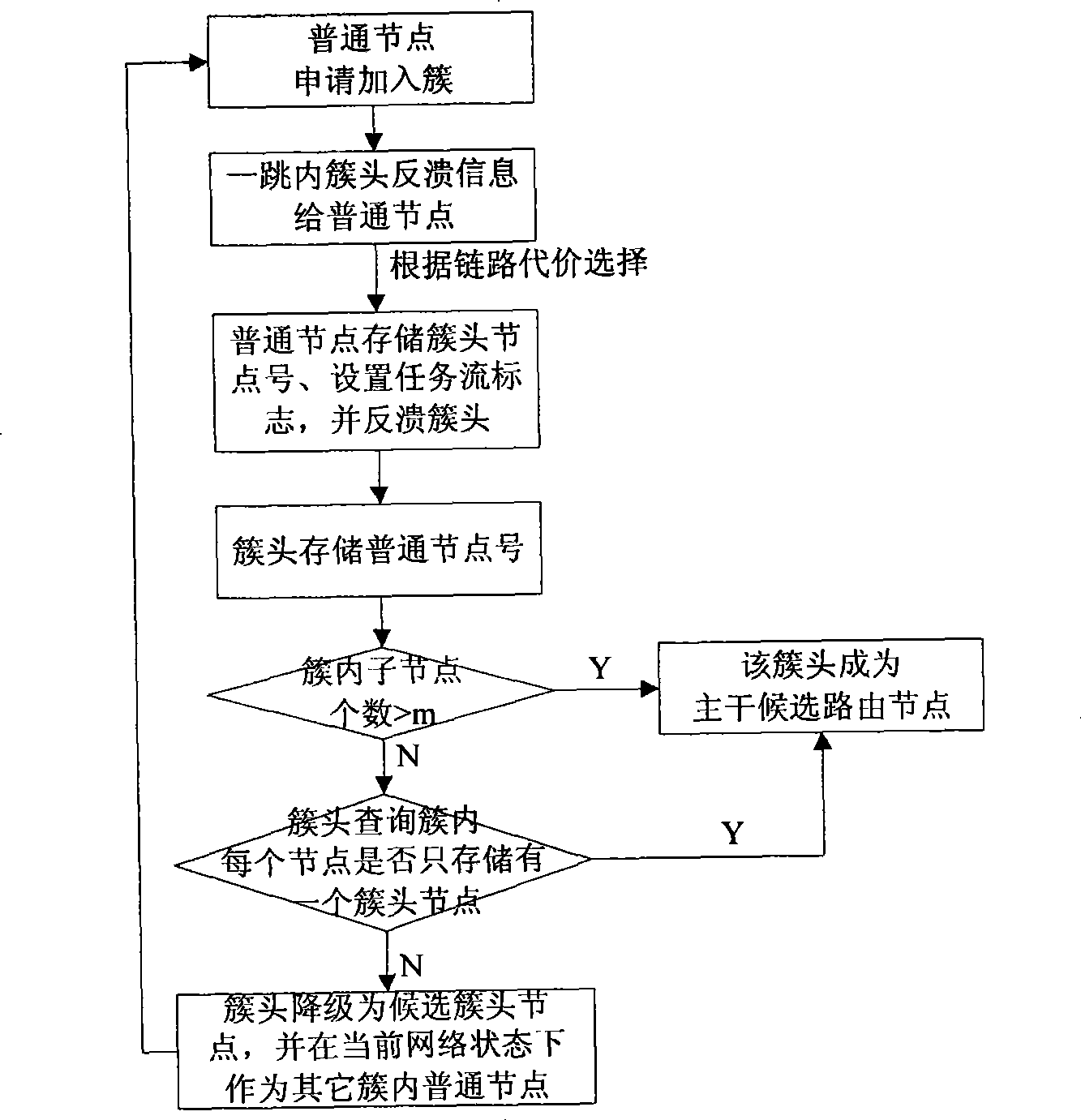
InactiveCN101483902ATroubleshoot routing issues for transmissionsEasy to deployNetwork topologiesTransmissionBalancing networkQuality of service
The invention relates to a multimedia sensor network routing scheme guaranteeing service quality, which refers to a wireless multimedia sensor network routing method, and is mainly used for solving the transmission problem of the data of a plurality of task flows existing in a wireless multimedia sensor network. The wireless multimedia sensor network routing scheme realizing guaranteeing the service quality is mainly characterized in that according to the own characteristics of a node, a role played in a routing path is automatically applied; according to cost on a link path, an optimal node is selected to establish a plurality of routing paths with different task flows; and when network topology changes, then routing path is dynamically renewed. By using the method of the invention, when the network is under a situation that a plurality of multimedia task flows are transmitted and applied, the multimedia task flows are real-timely and effectively transmitted, and the aim of reducing network congestion rate, increasing network huff, fully playing the function of each node in the network, balancing network energy consumption, effectively utilizing the resources of the whole network, and improving the survival period of the whole network is achieved.
Owner:NANJING UNIV OF POSTS & TELECOMM
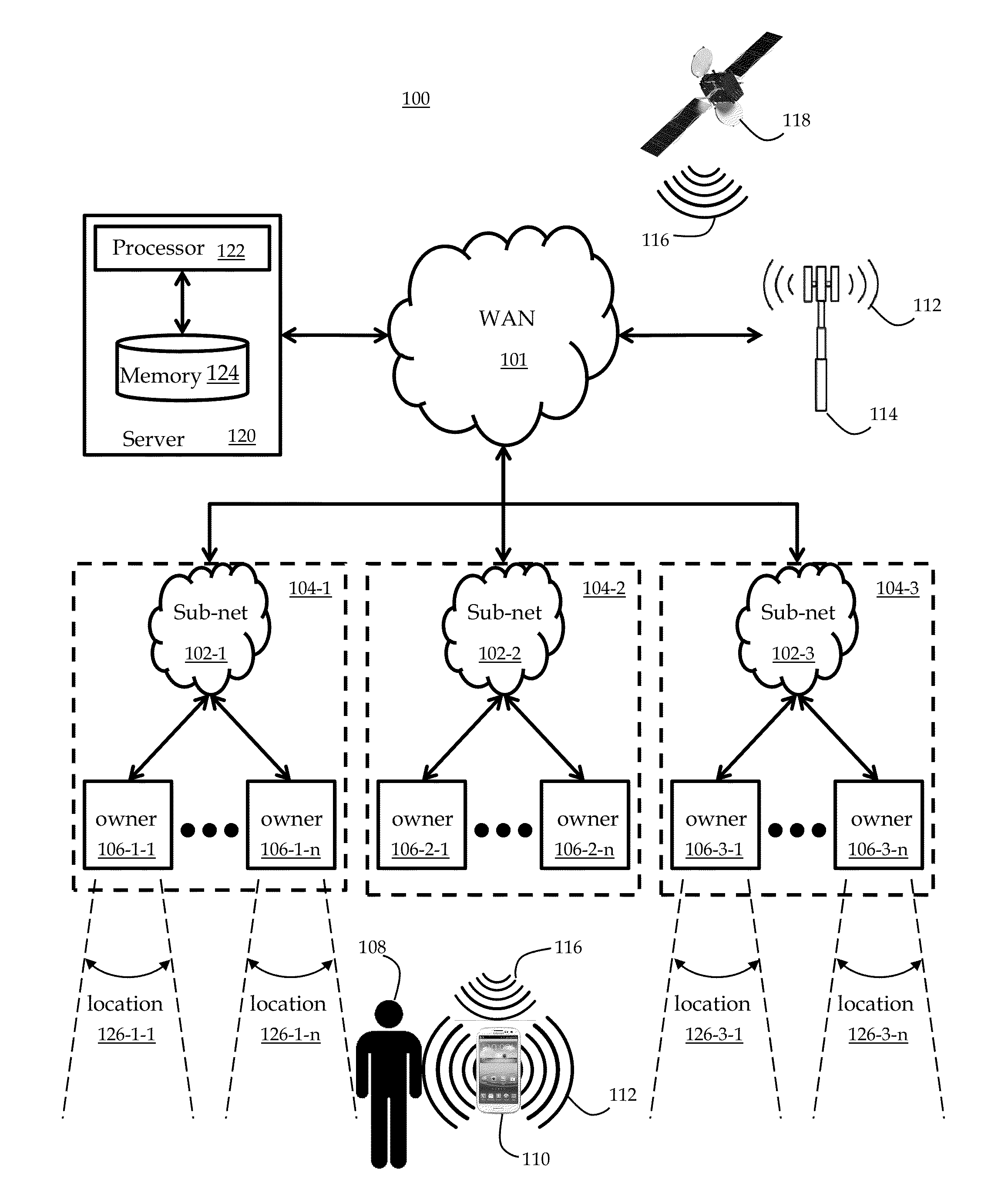
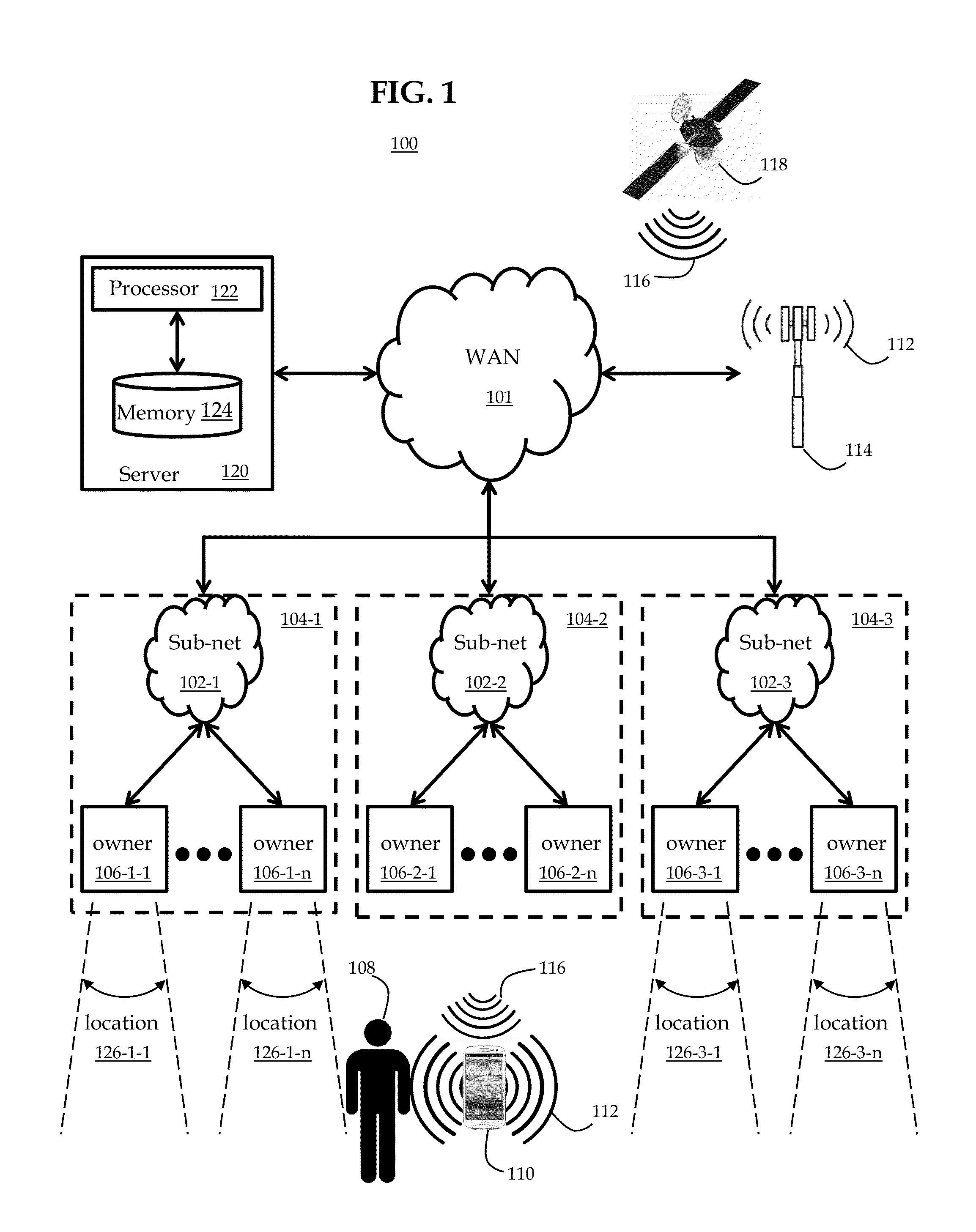
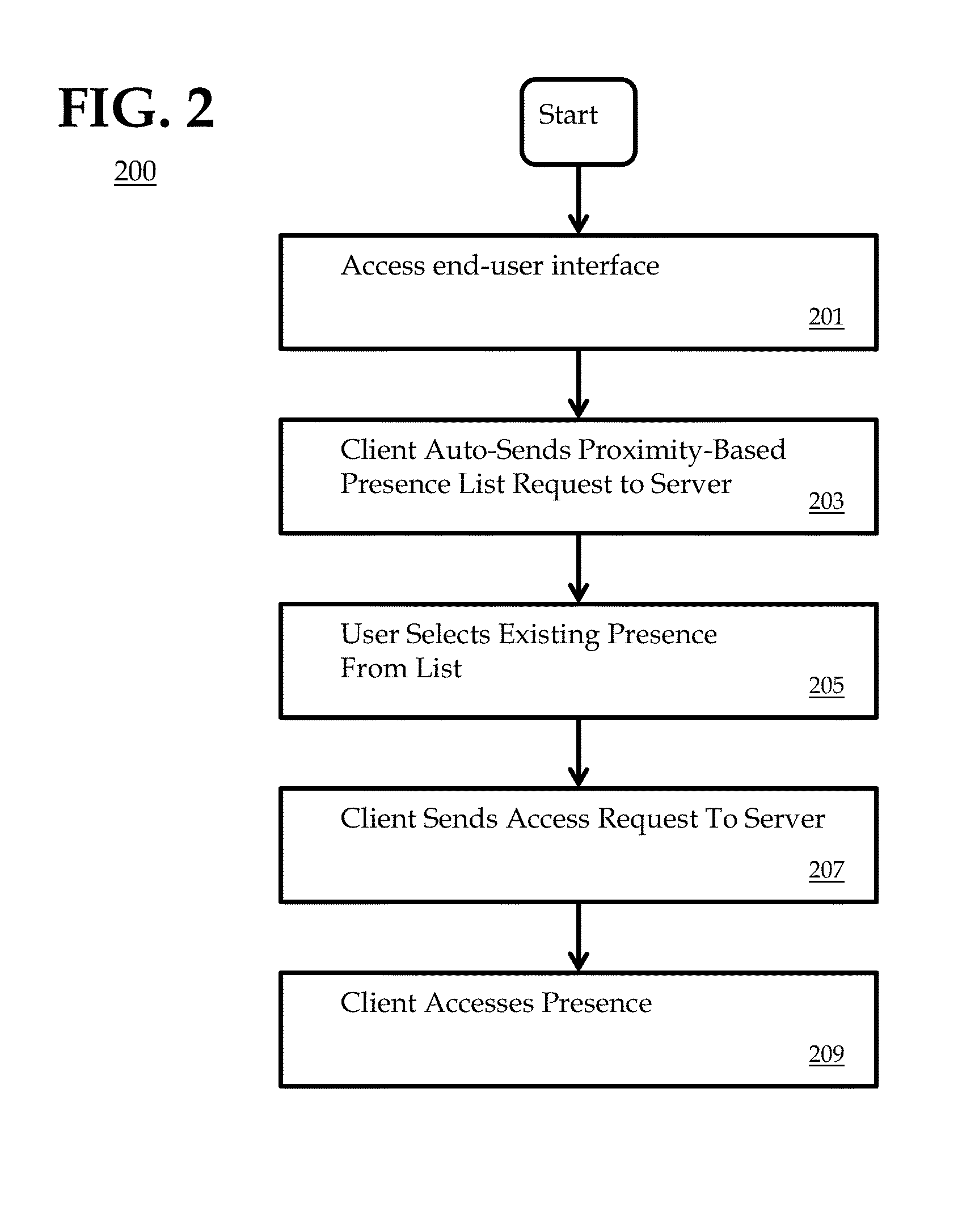
System and method for web presence for one or more geographical locations
InactiveUS20130151950A1Control moreEnhanced informationDigital data information retrievalNatural language data processingWeb presenceGeolocation
System and method to provide a discovery-augmented web presence for one or more geographical locations. Embodiments may provide open access to geographical location-based web presence content, allowing the presence content to be created by users based on location verification and user anti-spam qualification. Embodiments enable a legitimate location owner or representative to claim and manage at least a portion of the user-created presence content, thus providing improved transparency and accuracy in location-related content.
Owner:PHOTOPON
Identification method for multi-mode terminal roaming among heterogenous inserting technology networks
ActiveCN1889781AImprove securityAvoid Malicious Billing FraudAssess restrictionRadio/inductive link selection arrangementsTelecommunicationsEnd user
Owner:DATANG MOBILE COMM EQUIP CO LTD
Guided workflows for establishing a web presence
ActiveUS9277022B2Minimal effortMinimal knowledgeWeb data indexingMultiple digital computer combinationsUser interfaceKnowledge base
Methods and systems related to guided workflows for establishing a web presence include a customer user interface with a guided workflow layer based on a knowledge base about the customer, wherein the customer interface allows a customer to manage a customer's web presence based on operation of a logic engine that accesses information about what a customer has done and who the customer is (e.g. type of business), wherein the user interface presents a guided workflow of tasks associated with a recommended area of improvement for the customer.
Owner:NEWFOLD DIGITAL INC
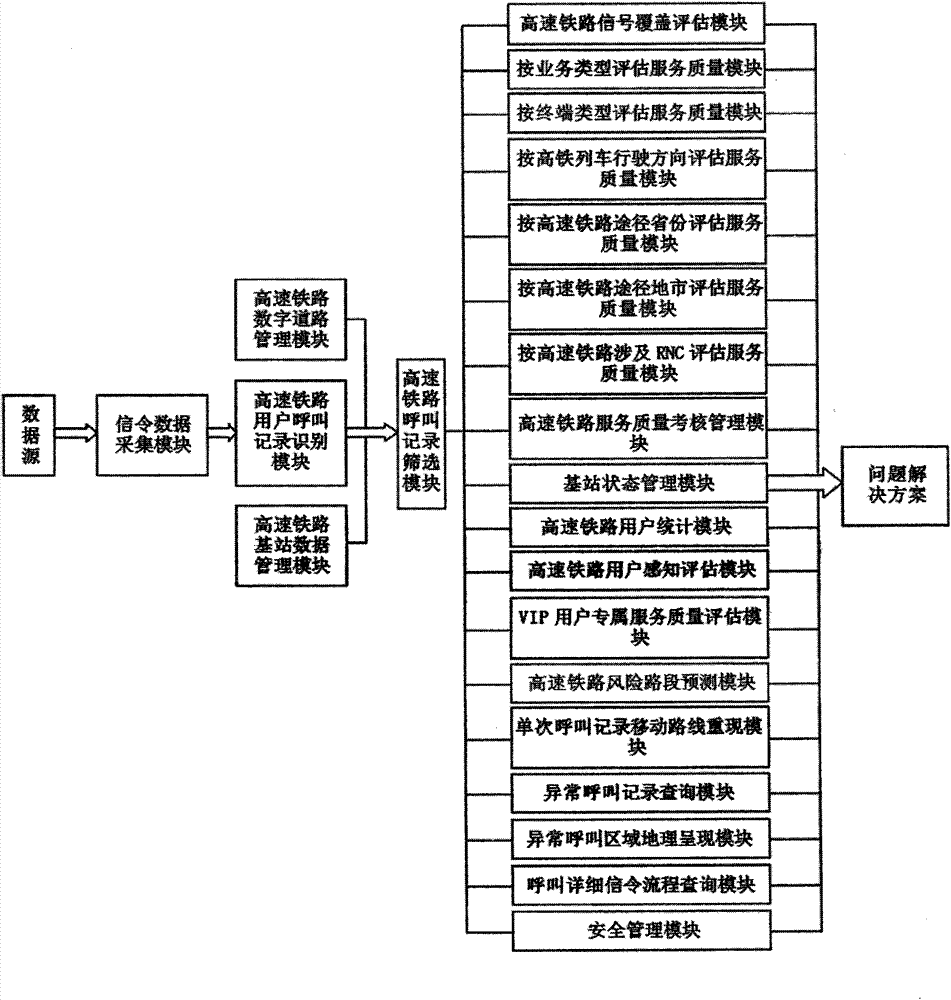
Optimization analysis method for high-speed railway mobile user perception and high-speed railway mobile user perception system
ActiveCN104768169ARealize unified assessment and assessmentRaise attentionWireless communicationTelecommunicationsUser perception
The invention relates to an optimization analysis method for high-speed railway mobile user perception and a high-speed railway mobile user perception system. The system comprises 23 functional modules and can locate users in a high-speed railway carriage through algorithms such as high-speed railway service cells, the traveling track and so on, and high-speed railway coverage quality conditions are shown on a geographical map in a rasterization way, thereby helping operators to perform global real-time monitoring on the high-speed railways nationwide. Special optimization can be made for a certain high-speed railway. The system assesses the service condition of the network, the service state of a high-speed railway base station, and perception of users especially VIP users when users on the high-speed railway travel at a high speed, finds the problems of the network and predicts the risky section of the high-speed railway. According to the assessment result of the system, optimizing staff of the operator perform targeted optimization and adjustment, so as to improve the perception of mobile users traveling by the high-speed railway.
Owner:北京洛神科技有限公司
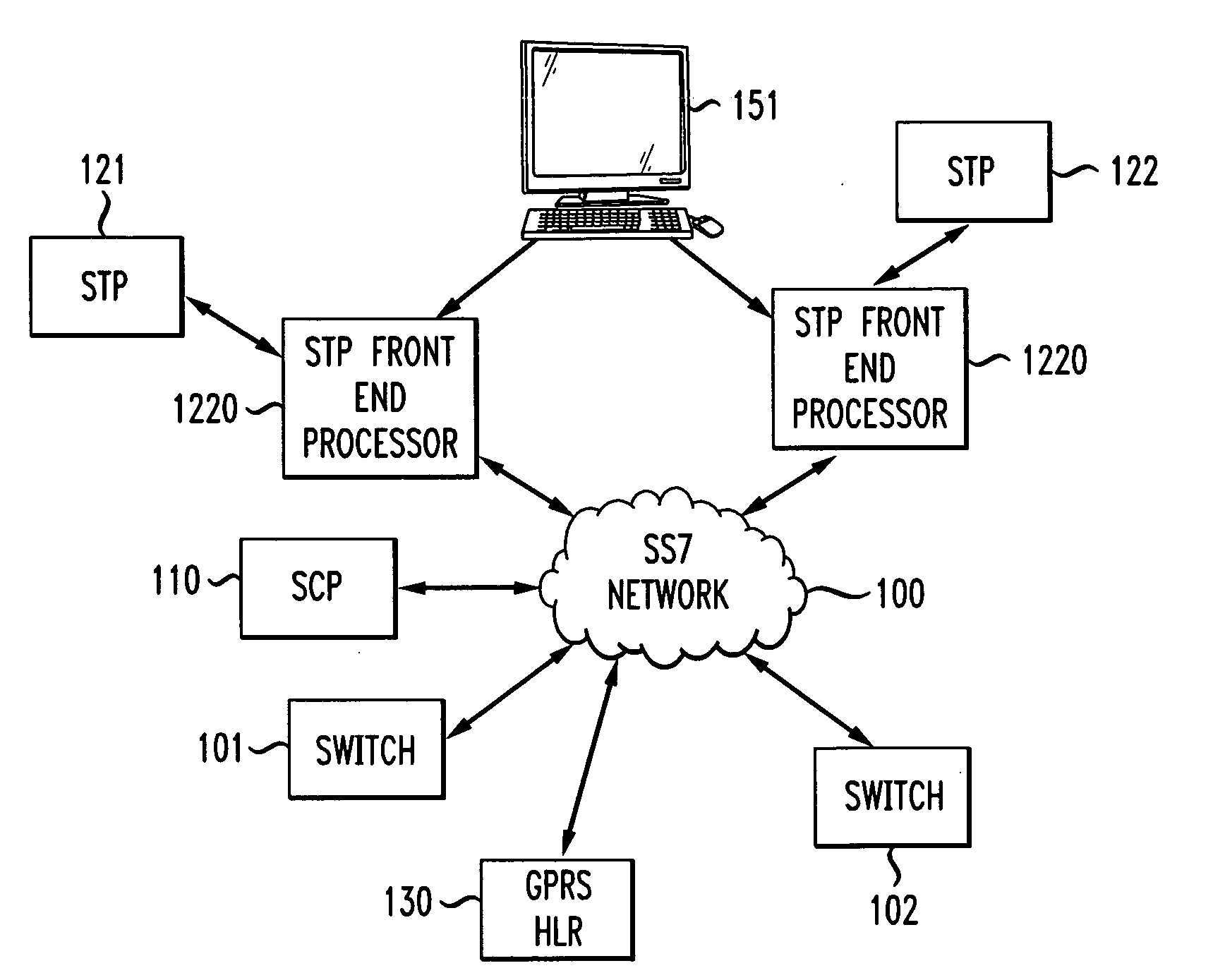
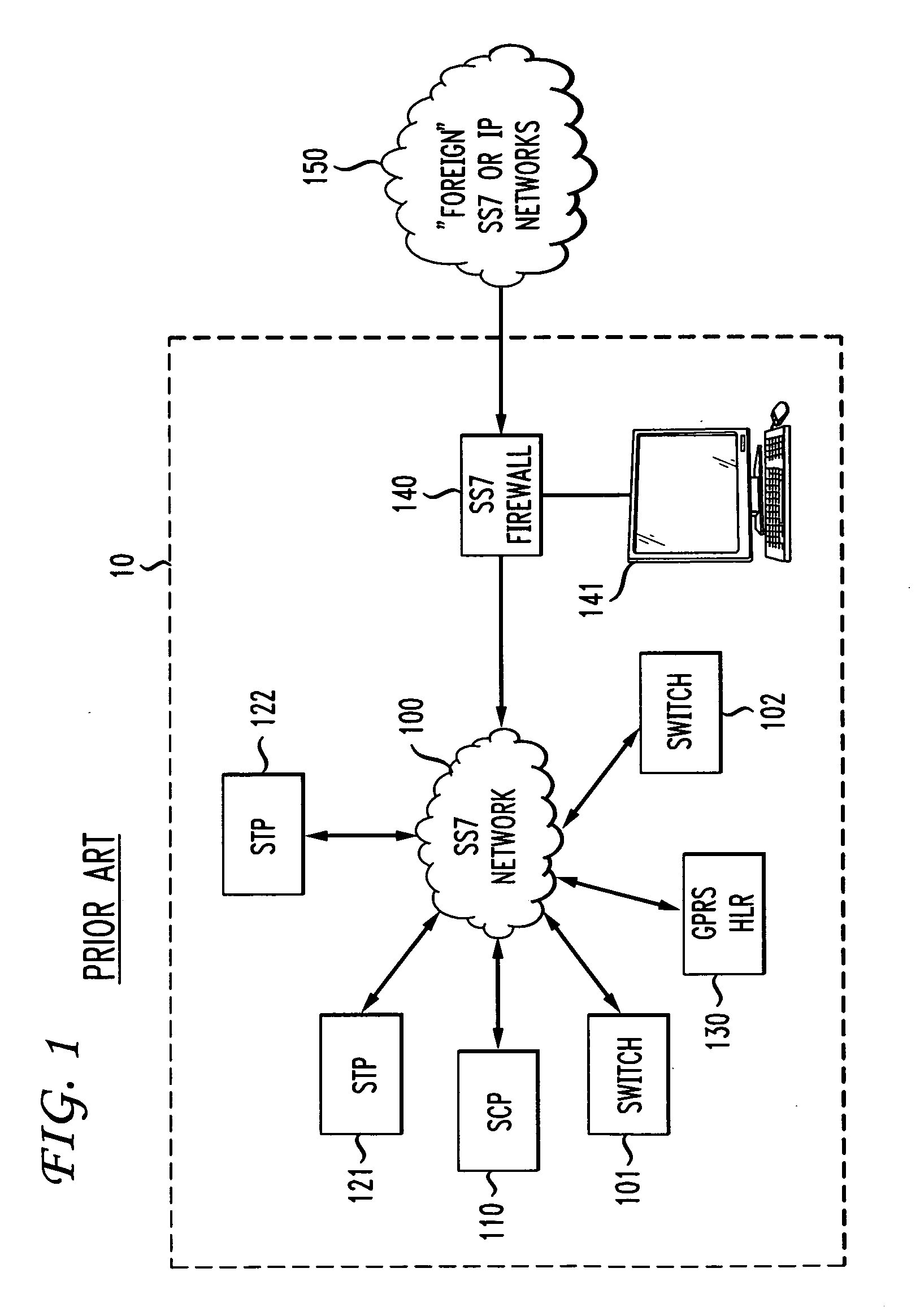
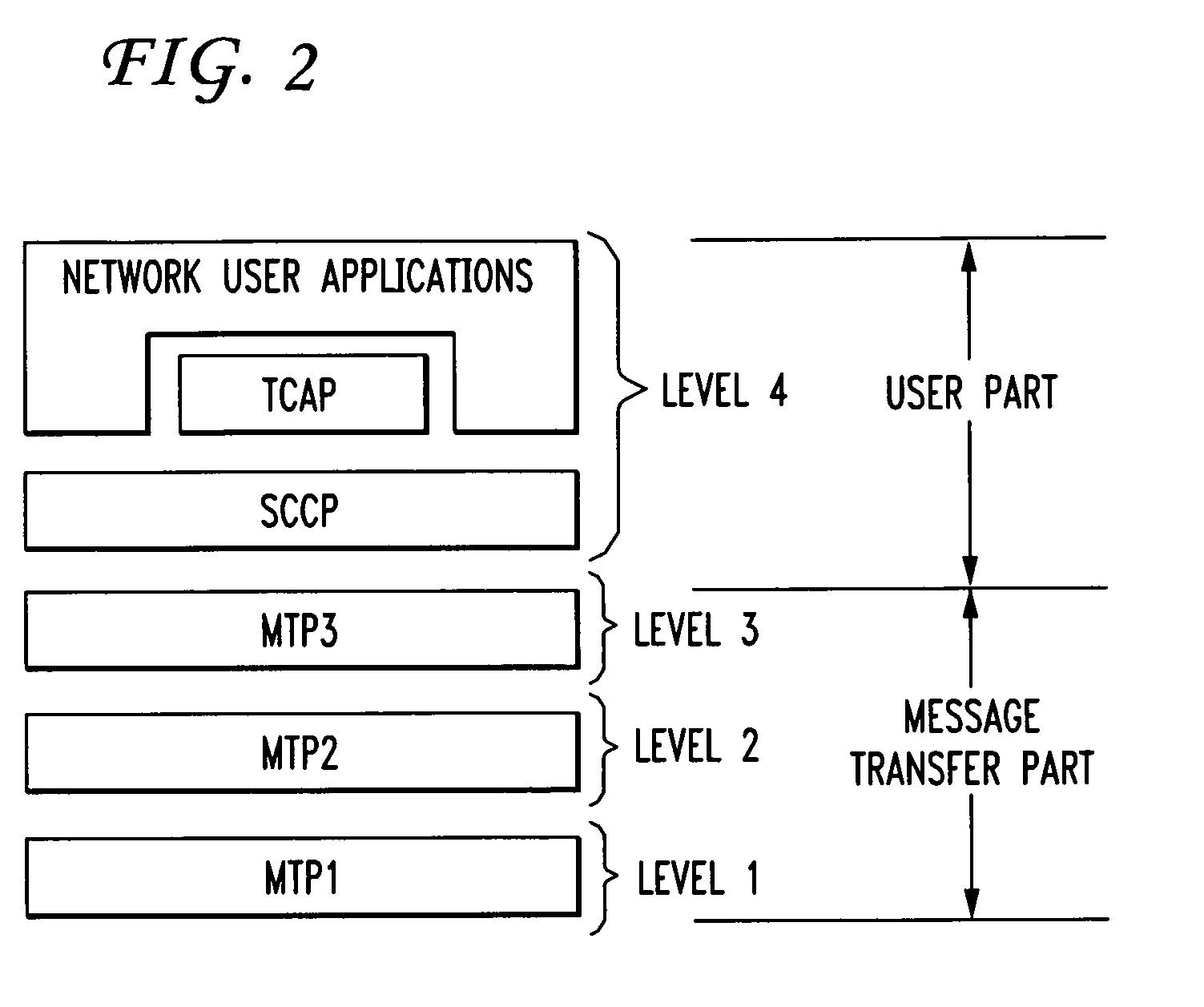
Signal transfer point front end processor
InactiveUS20110041176A1Improve the level ofInterconnection arrangementsDigital data processing detailsSecurity ruleProtocol stack
In an SS7 network, each of a plurality of Signal Transfer Points is fronted by a front-end processor (STP-FEP) that has a network presence. The STP-FEP implements at least the MTP2 layer of the SS7 protocol stack and implements security rules at the MTP2 and MTP3 layers.
Owner:AT&T MOBILITY II LLC
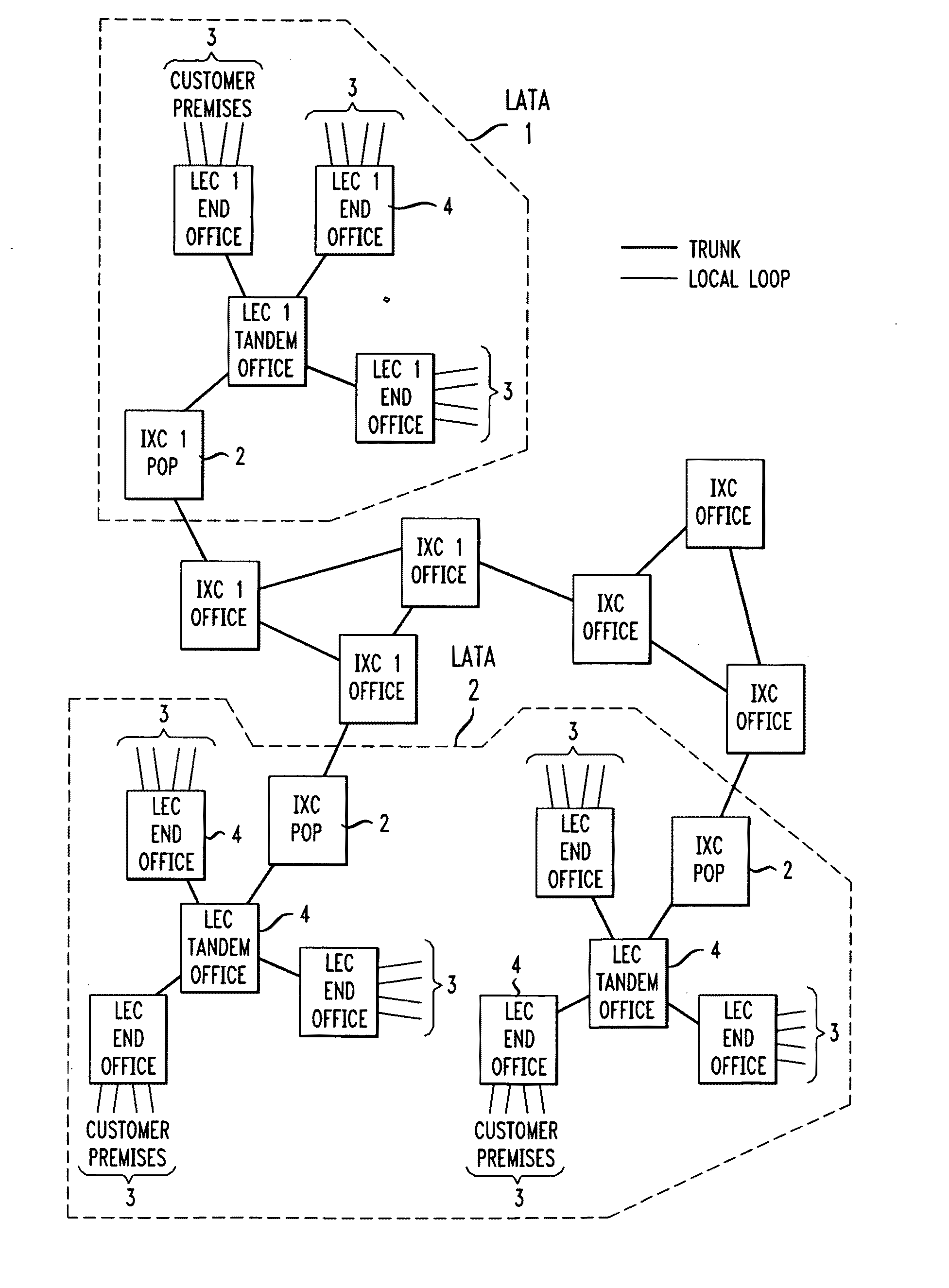
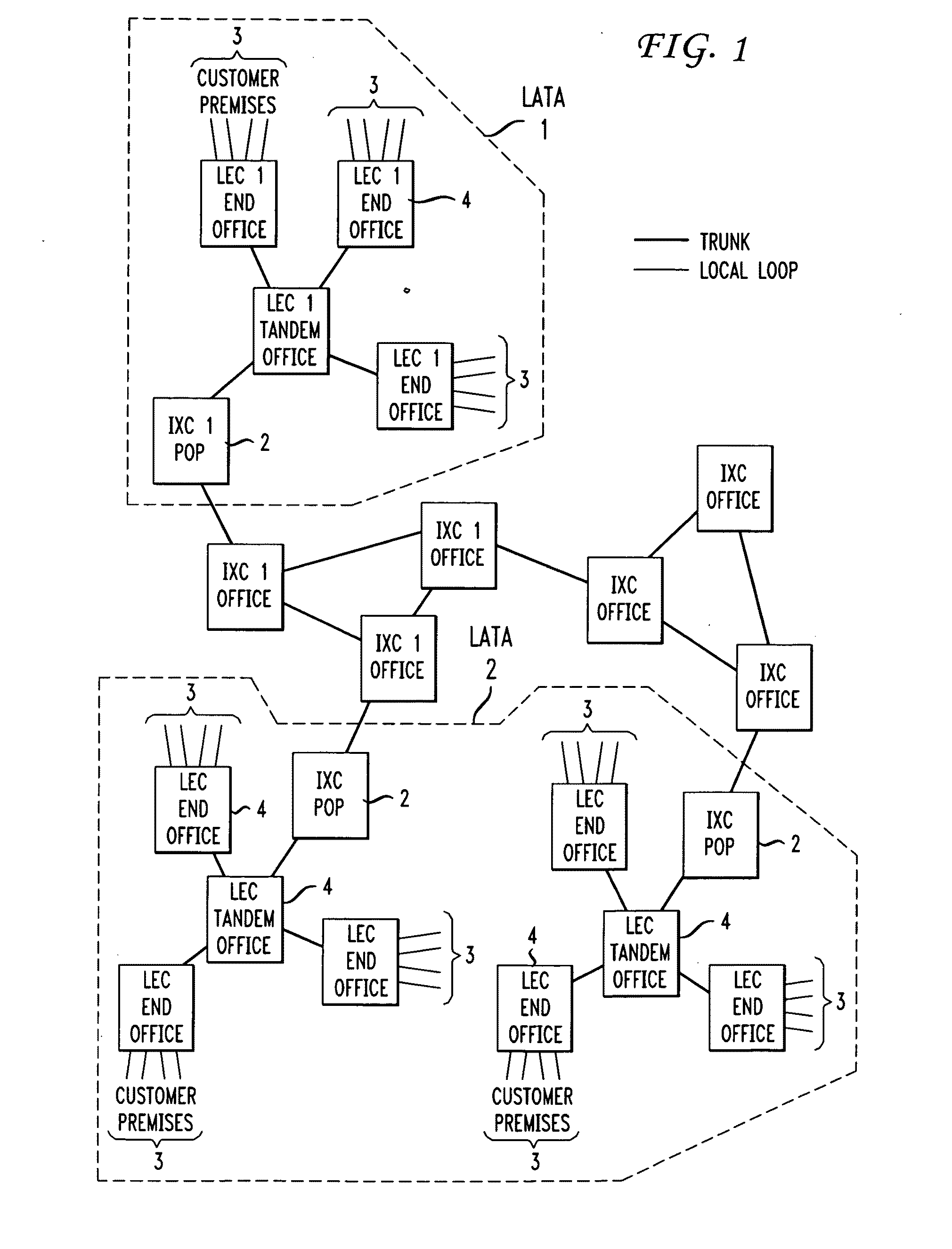
Method for optimizing network "Point of Presence" locations
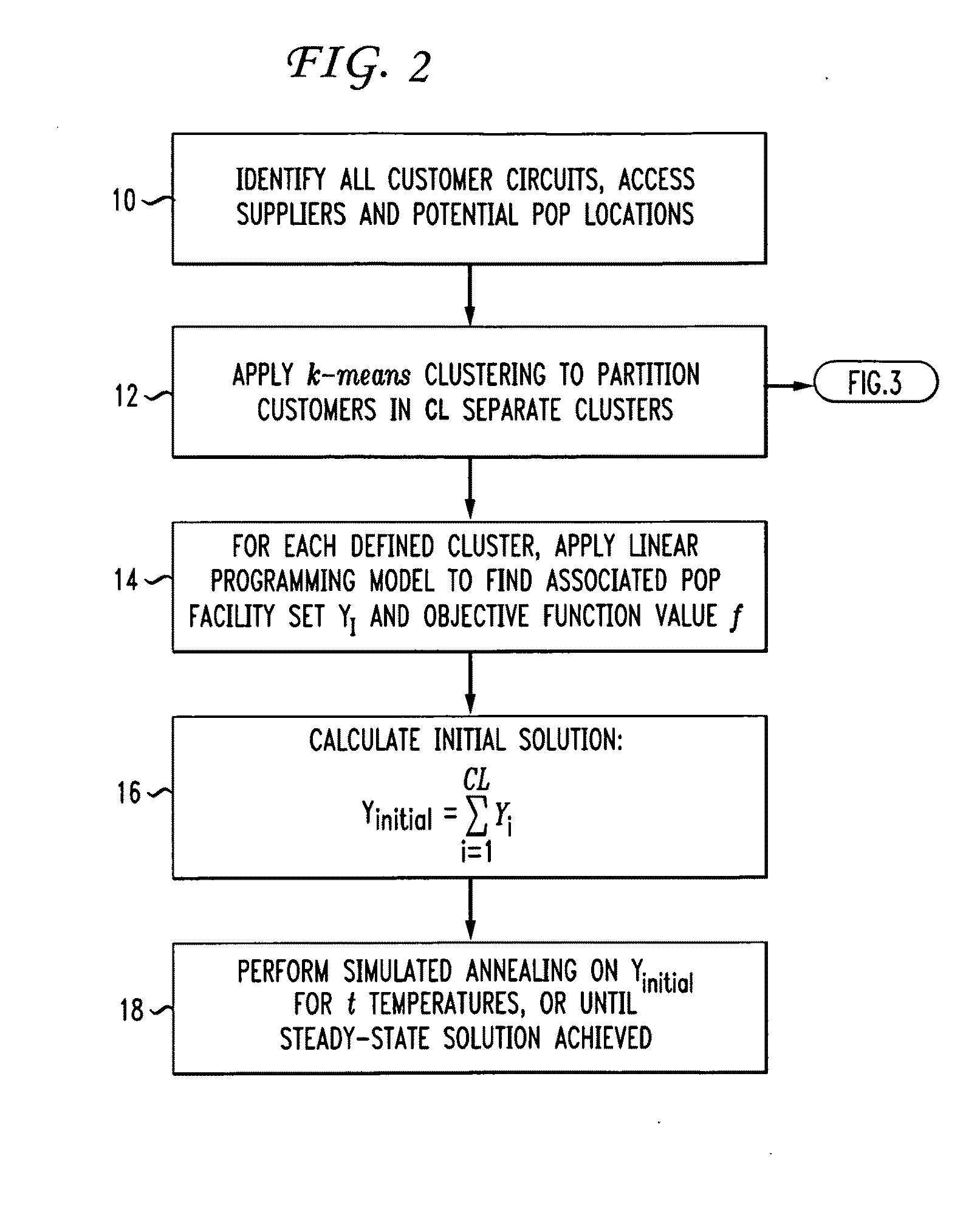
A methodology for optimizing the placement of network “Points of Presence” (POPs) across the carrier's entire network (i.e., a “global” solution”) utilizes carefully constructed customer clustering and simulated annealing methodology to create a cost-efficient solution. The customer base is first partitioned into a plurality of clusters such that the customers within each cluster are closer to its centroid than the centroid of any other cluster (e.g., applying the k-means clustering algorithm or any other suitable method of partitioning the customer base). A linear algorithm process is used to minimize the costs associated with the number of placement of POPs within each cluster. A simulated annealing (SA) process is then used to iterate the entire set of potential POP locations until a compact, steady-state solution is achieved (or, alternatively, until a given number of iterations has been performed). In a preferred embodiment, a number of iterations are performed at each “temperature” in the simulating annealing process to further improve the result (this iterative process referred to in the art as “intensification”).
Owner:AT&T LABS
Method of phantom lines in multiple hops for building simulation of phantom line from end to end
InactiveCN1874302AImprove performanceEasy transitionNetworks interconnectionBuilding simulationInterconnection
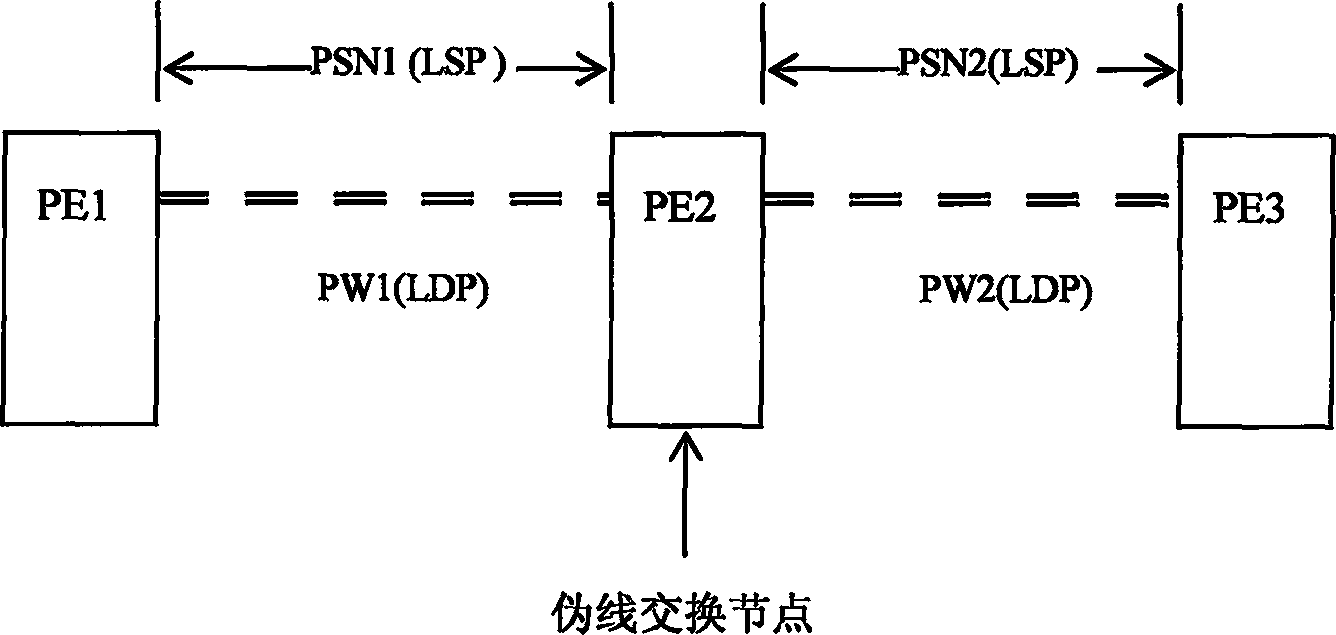
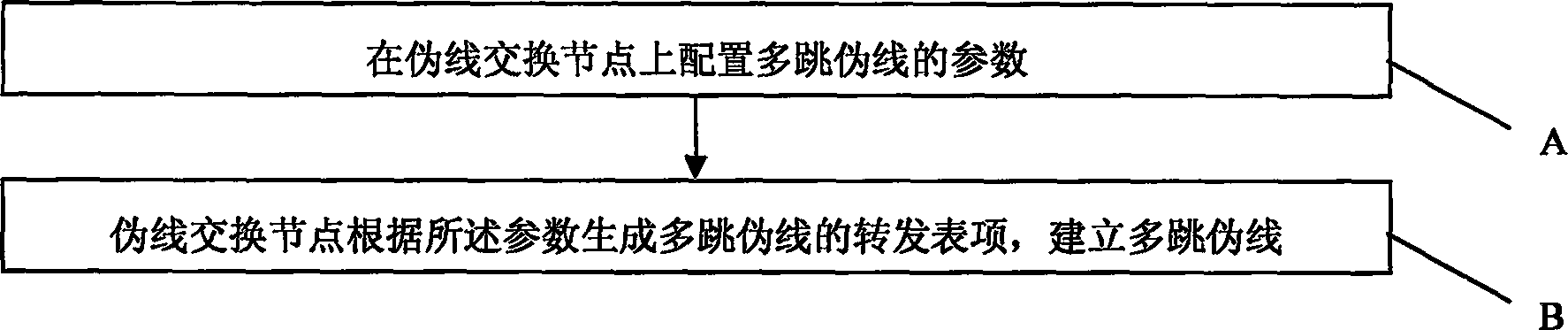
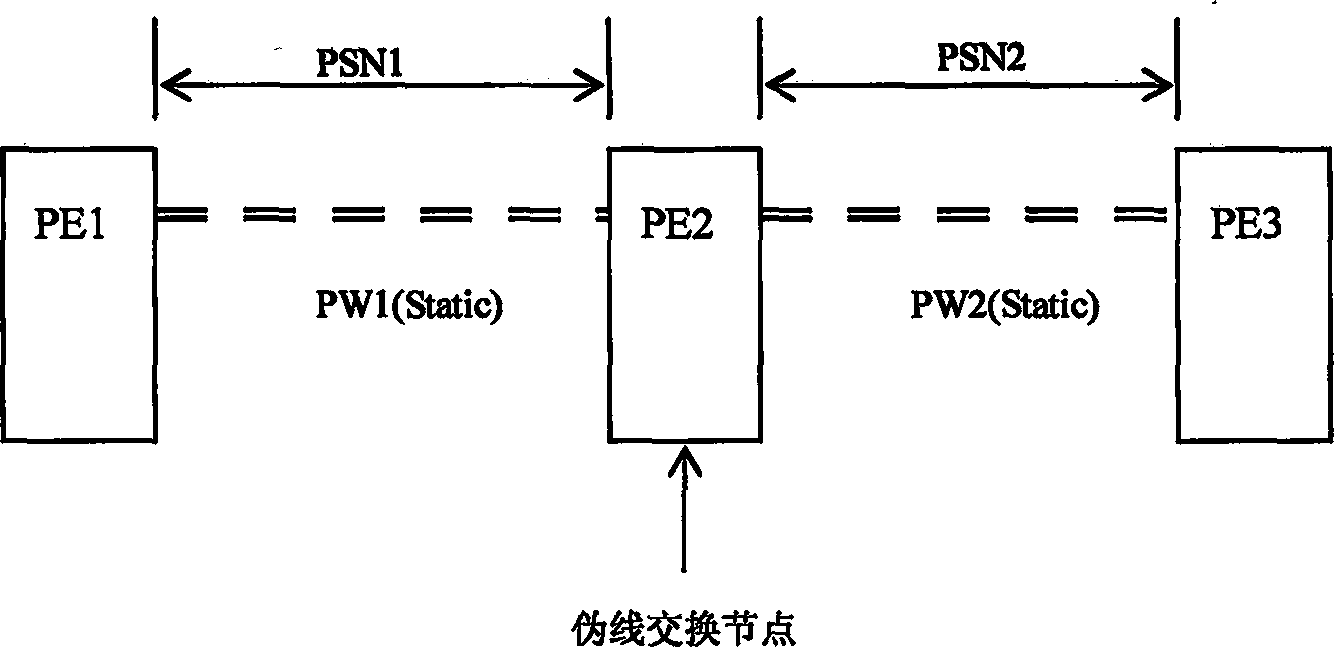
The method comprises: a) setting multi-jump PW (pseudo wire) parameters on the PW switch node; b) in term of the switching list item of multi-jump PW generated by said parameters, the PW switch node establishes the multi-jump PW; meanwhile the PW switch node can also establish multi-jump PW in term of switching list item generated by the information obtained from dynamical protocol. In the PWE3 services, the invention can ensure interconnection of the multi-jump PWE3 services in case of not running dynamical signaling LDP; beside, when the oscillation occurs in network, a great amount of signaling messages will not be produced.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com