An expansion security authentication method based on 802.1X protocol
A security authentication and protocol technology, used in user identity/authority verification, digital transmission systems, data exchange networks, etc., to solve problems such as software insecurity, theft of authentication information, and the inability of unknown viruses to do anything.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
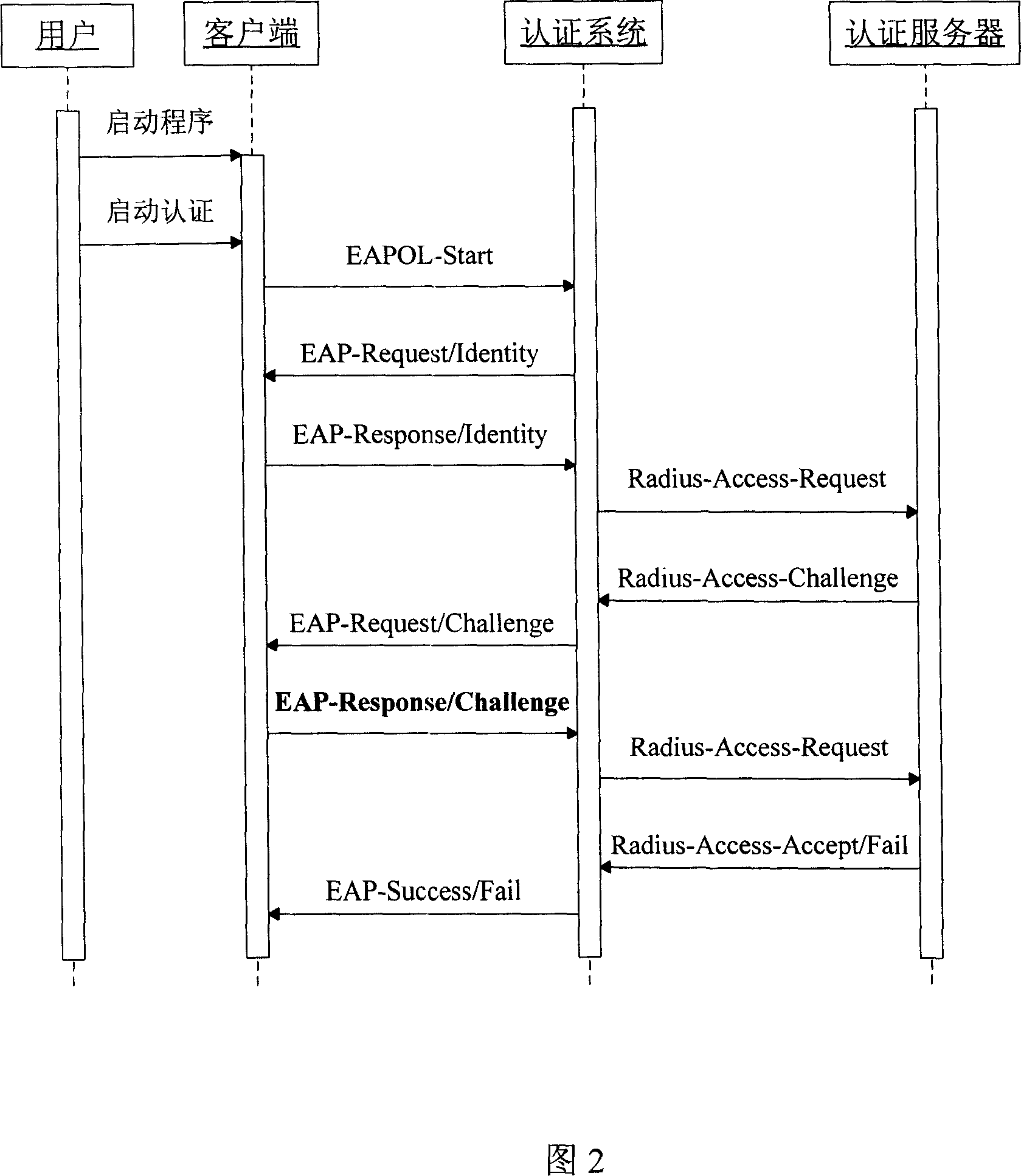
[0033] Figure 2 shows the most commonly used client and authentication system in the authentication phase of the protocol process.
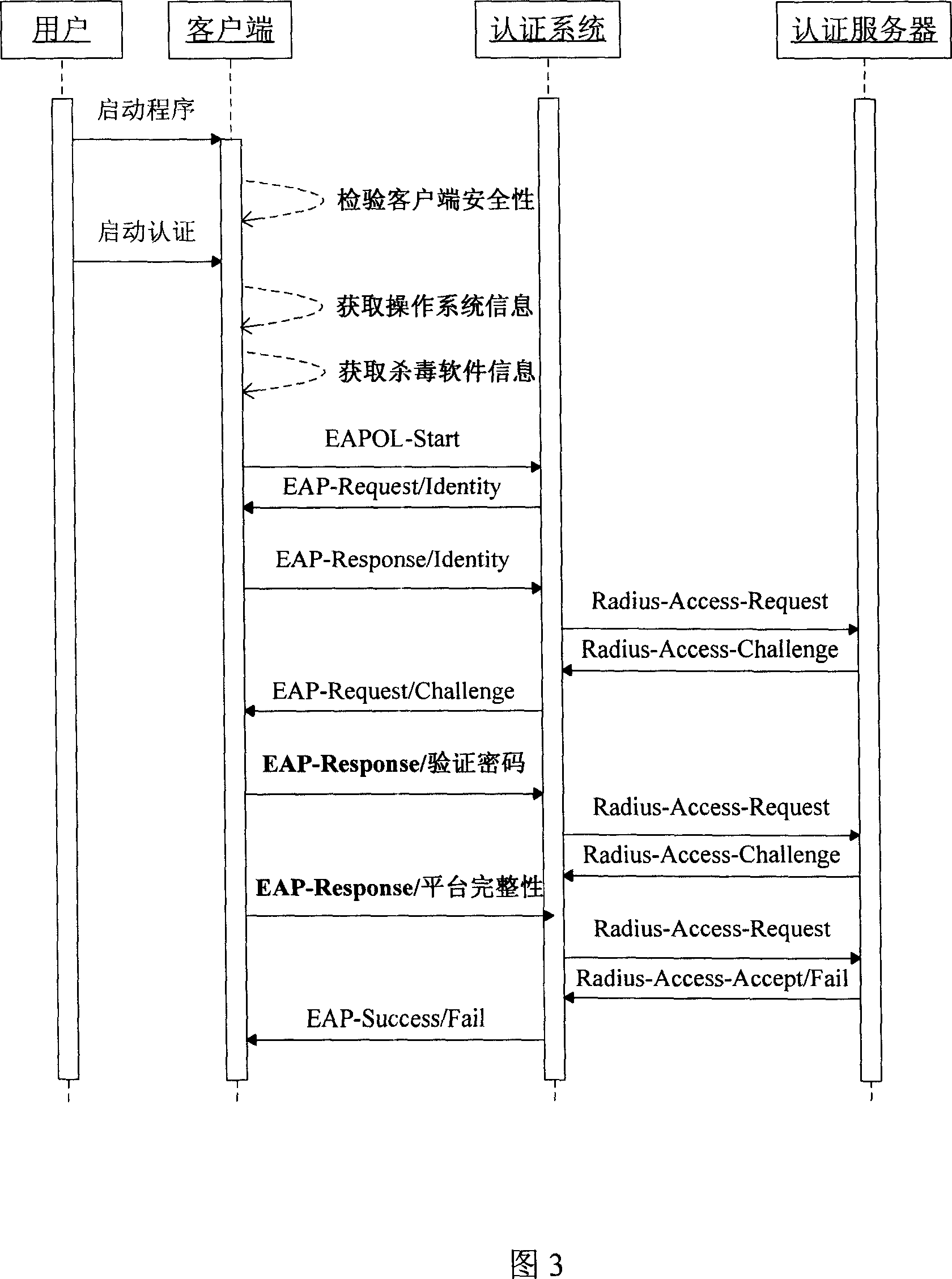
[0034] As shown in Fig. 3, the safety authentication method expanded on this basis of the present invention. The main implementation steps are as follows:
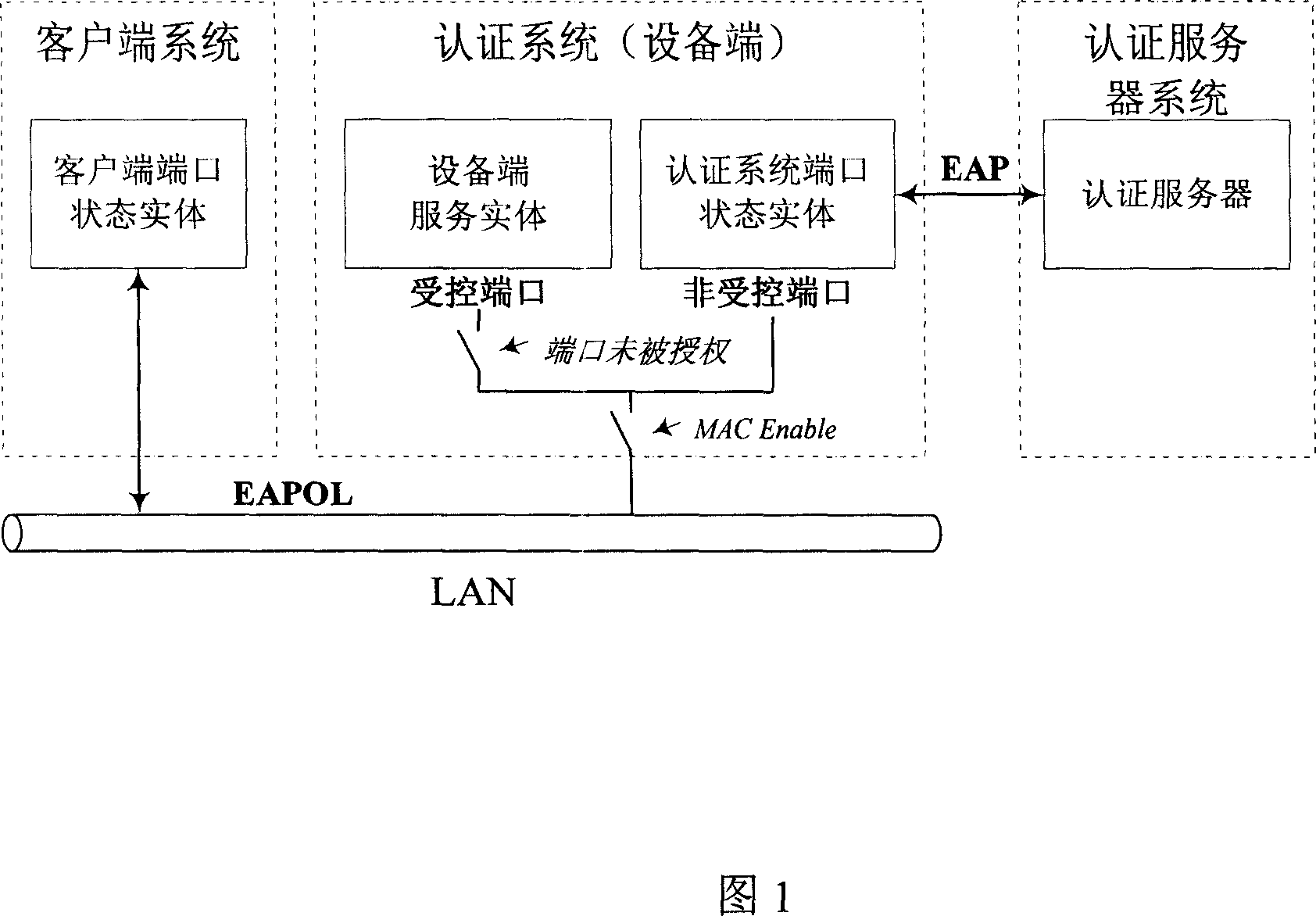
[0035] First, before the user is authenticated, the controlled port of the authentication system is closed, and the user cannot access the network. However, the uncontrolled port is always open, but only EAPOL authentication packets are allowed to pass.
[0036] In the initial stage, the client program needs to first check the security of the program itself, including whether the client program has been modified and the correctness of calling the DLL file.
[0037] After the user issues an authentication command, the client program continues to obtain information about the user's operating system. Different operating systems require the corresponding client software to obtain its information. The i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com